pfSense on Proxmox with WireGuard
-
Hi there,
Since a few weeks I'm playing around with a Protectli hardware device, Proxmox on it and pfSense. Working great!
I am having a 1.2gbs connection and getting almost full speed, even when I'm behind a WireGuard VPN.
The reason I'm having my router virtualized is because I can and I like to play around and learn.My question: Until I installed a VPN tunnel with WireGuard, I was able to switch between host (Proxmox) and router (pfSense) on both their LAN IP adresses.
Proxmox 192.168.178.36 (My "WAN" side, IP obtained from DHCP)
pfSense 192.168.1.1Now since everything is behind the VPN I cannot anymore.
The reason must probably lie in the firewall rules, but I don't know what to change so I can access the Proxmox GUI again.
Any thoughts on how to fix this?
I'm here to learn so a heading in the good direction is also very welcome! Thanks in advance.
-
@j0hsm1tty
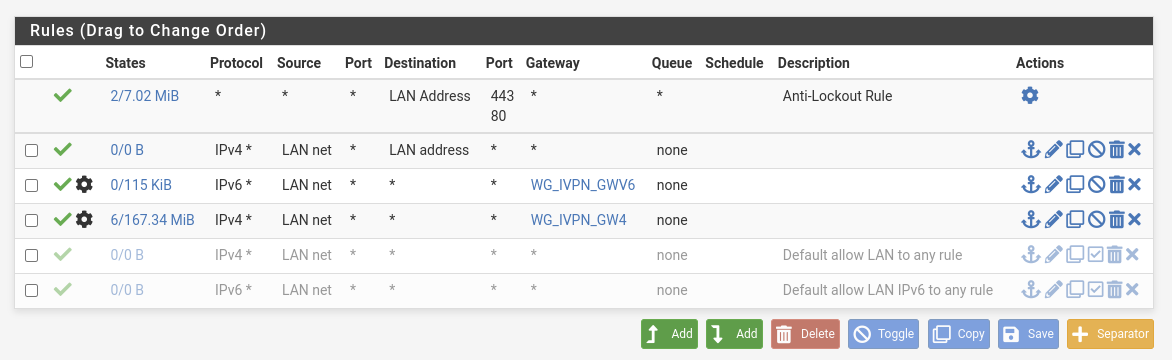
Your WG rules policy routes any traffic to the VPN gateway apart from the LAN address. So traffic to Proxmox IP is not allowed.You have to put a pass rule with destination = Proxmox above of the WG rules to get access.
However, as your network may grow in the future do it on the smart way yet:
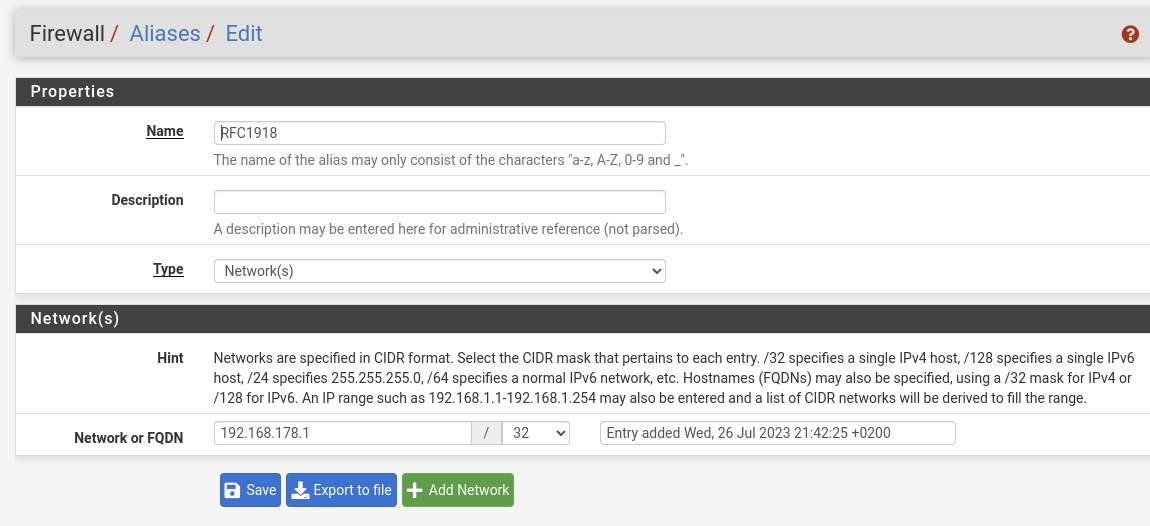
Create an Firewall > Aliases of type networks and add all private networks to it. Call it RFC1918.
Then replace the "LAN address" destination in your second rule with this alias.
This assumes that you don't need to access private networks over the WG. Meas that you only use it for internet access.With this alias you can also access other local (private) networks from LAN network in case you add any in the future.
-
Thanks for helping me in the right direction!
I noticed when I made changes in the firewall rules my browser on the client side kept loading longer, so something has changed. But I still can't acces the Proxmox GUI.
A little more research made me find out that one of the gateways has a problem. I'm not sure if this came due to some firewall rules, OR that the firewall rules are in place and the gateway setting are not right.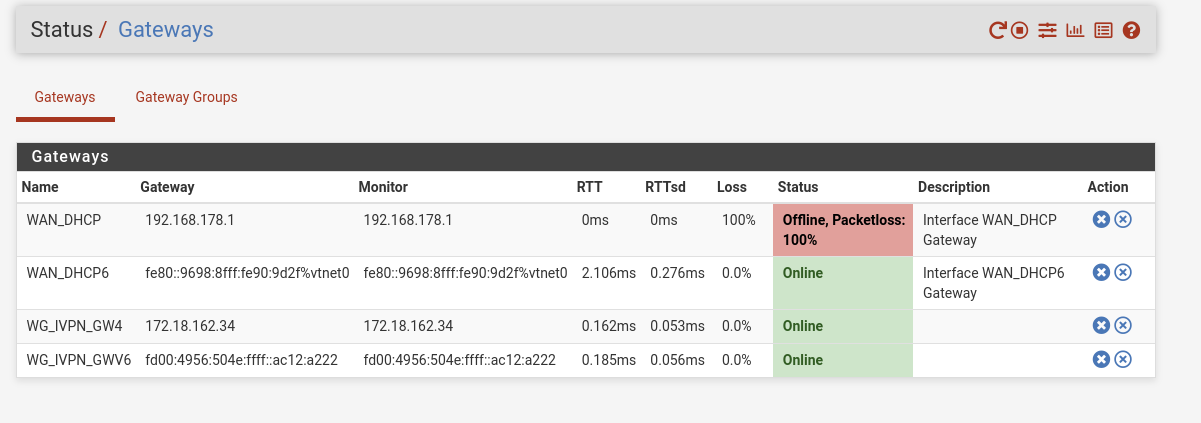
I did made the firewall rule like you said, with the whole IP range in an alias.
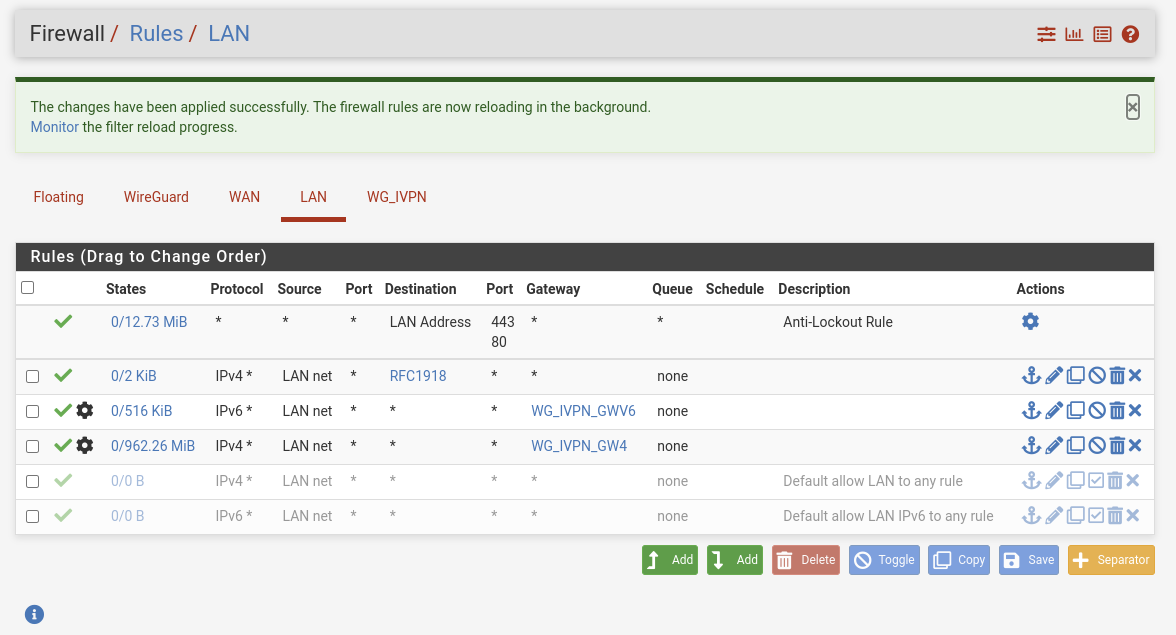
And hereby the specific rule. From my LAN side.
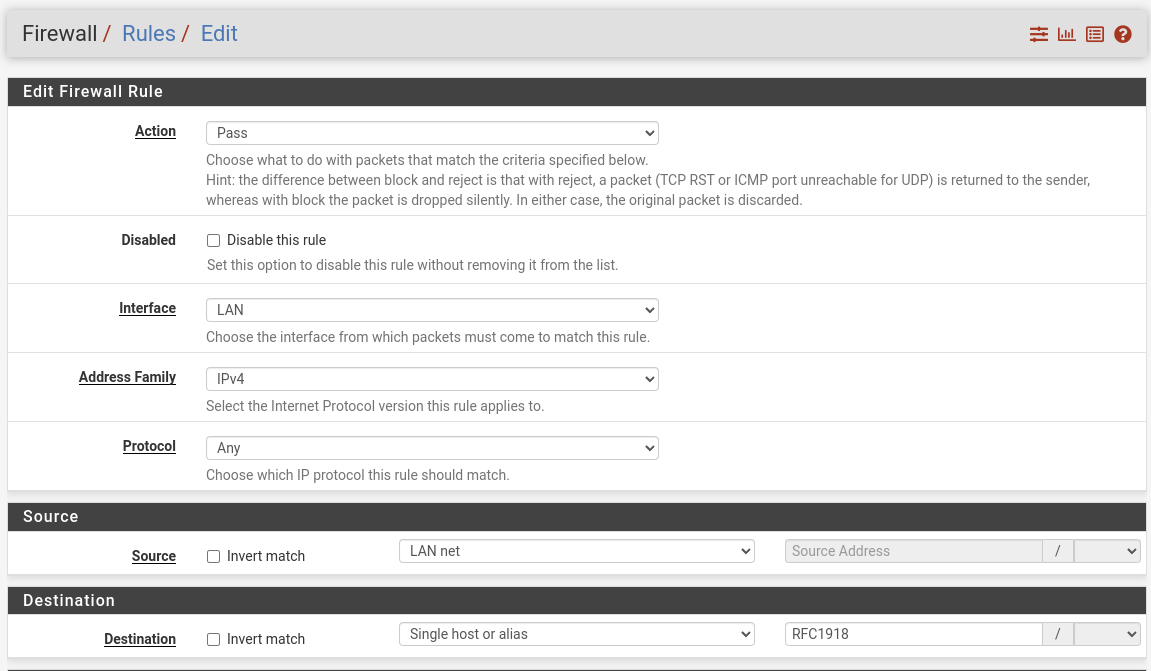
Could it have something to do with a outgoing gateway? (WireGuard VPN?)
Hoping you can help me out.
Thanks in advance! -
@j0hsm1tty
The gateway offline state just means that the gateway is not responding to the monitoring pings.
Anyway, monitoring the local router doesn't give a good review about the internet connection. You should consider to monitor an IP in the internet, which is responding top pings, e.g. 8.8.8.8.
You can set the in System > Routing > Gateways > Edit the concerned gateway.Your RFC1918 alias contents only the routers IP? This makes no sense. It's not the router you want access, but Proxmox as I got you.
And the suggestion with the alias aimed to include all RFC 1918 networks to it like this:
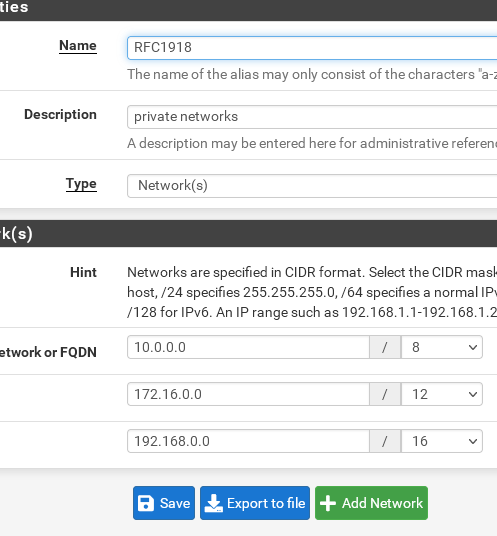
Could it have something to do with a outgoing gateway? (WireGuard VPN?)
No, the Proxmox IP is within the WAN subnet. So pfSense doesn't send packets destined to it to any gateway.
I suspect that your outbound NAT is in automatic mode. Natting the traffic is even necessary, otherwise Proxmox would send responses to the upstream gateway, since it doesn't know the network behind pfSense.
-
Thank you. I changed the private networks as you suggested. I kept the firewall rules for the LAN network the same.
Maybe I made a mess of the outbound NAT, but these are my settings.
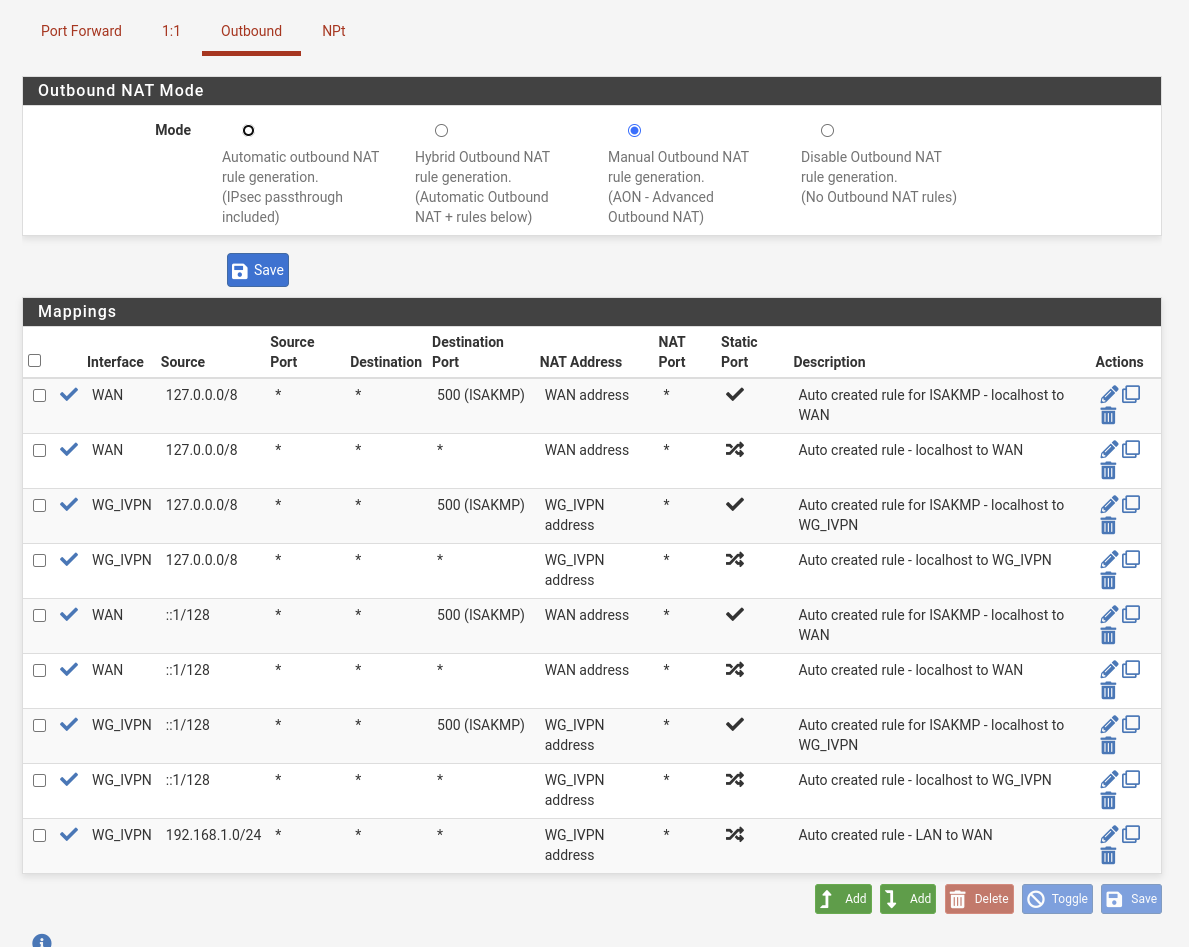
Do I need to make an extra line for outbound traffic for my internal network?
I'm sorry for my maybe n00b questions. -
@j0hsm1tty said in pfSense on Proxmox with WireGuard:
Maybe I made a mess of the outbound NAT,
Seems so.
Copy the last rule by ticking the copy button at the right (assuming the source is your LAN subnet) and change the interface to WAN.Basically there is no reason to switch over to manual rule generation for your set up. Just use the hybrid mode, so you keep the automatically generated rules and can add your own rules to override them.
-
I cleaned it out and added the WAN source source. Still the same.
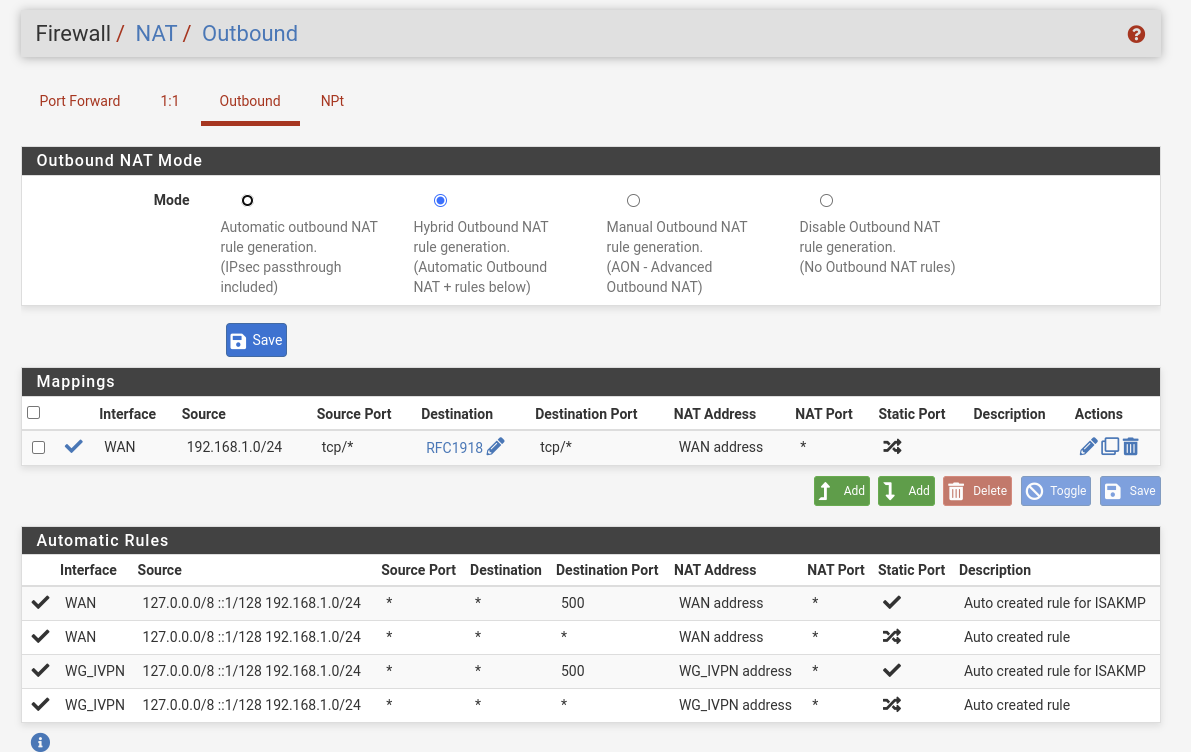
What I found out, when I clicked the specific state is this.
The 192.168.1.100 is my local PC, the 192.168.178.36 the Proxmox machine.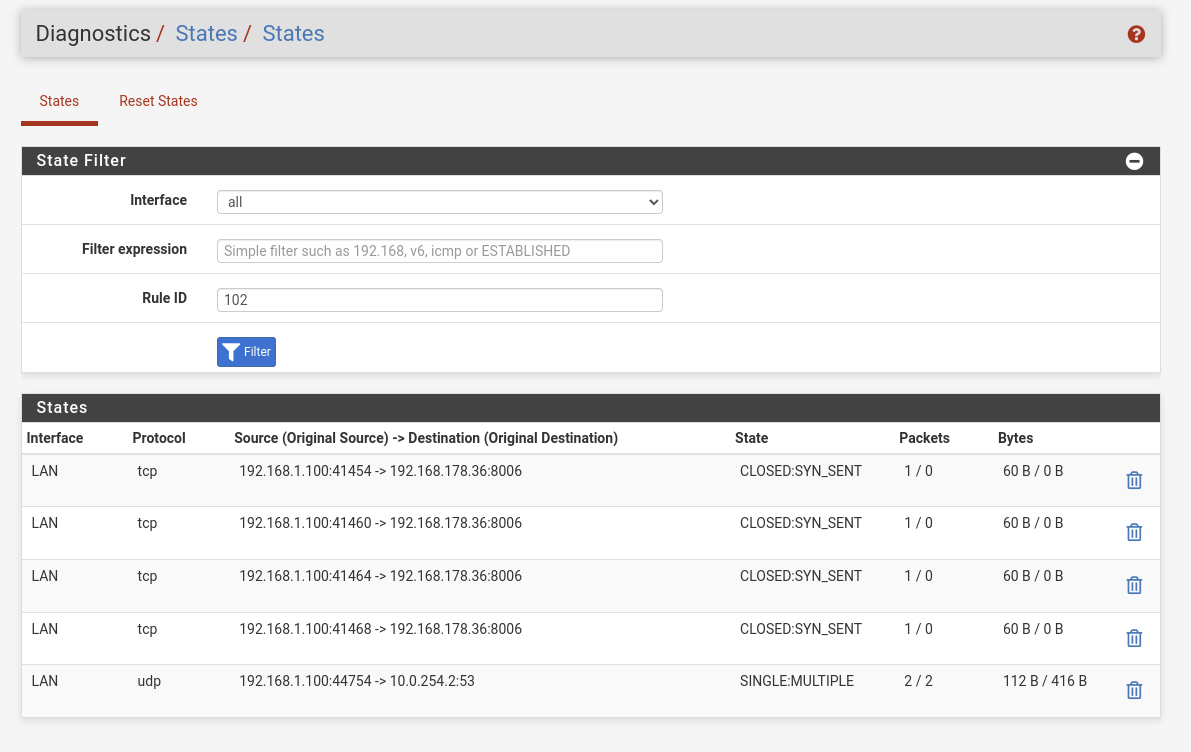
Could this have anything to do with these floating rules?
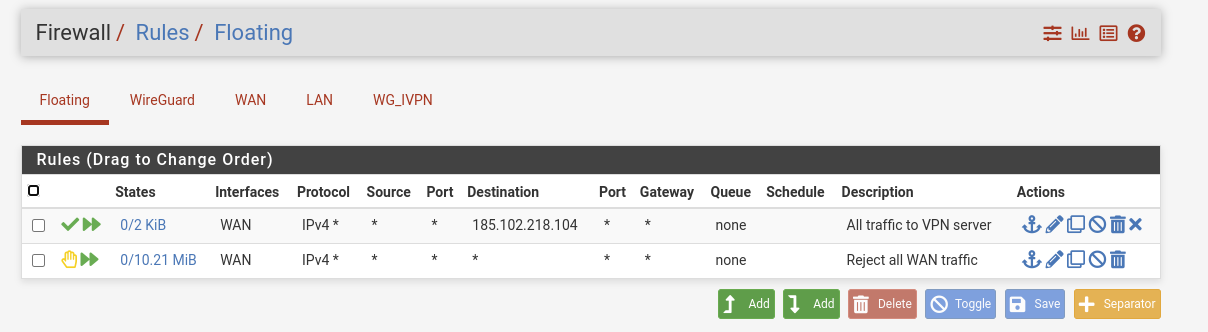
Looks like becoming a wild goose chase.
-
@j0hsm1tty
The outbound NAT should be fine now. Even the manually created rule is useless, since there is already an automatic rule for this purpose.Could this have anything to do with these floating rules?
If this reject rule is with direction out, then yes.
Also the pass rule only makes sense with direction out. -
I am really sorry Viragomann, I should have started asking with:
Could this have anything to do with these floating rules?
Because, IT WORKS!
I made these rules for a "kill switch" reason. I toggled these rules off and instantly I was able to go back to the Proxmox GUI.
Really happy with your help and your patience! Great! Thank you very much.
-
@j0hsm1tty said in pfSense on Proxmox with WireGuard:
I made these rules for a "kill switch" reason.
I see.
So you have to add an additional pass rule for the WAN subnet above of the reject rule. -
Again, very happy with your help! Up to my next learnings!