CE Update Frequency
-
@neiltiffin you can't have it both ways. First you complain that there were no releases between 2.6 and 2.7. (* as mentioned see System Patches). Then you question why you can't download a version older than 2.6. Pick a lane.
-
@neiltiffin FWIW there was no intermediate version to be a 2.6.1. 22.09 then 22.11 was skipped due to the OS change, 23.01 still had a lot of bugs/patches due to the PHP version change, and they fixed a few things in/with 23.05.1 when they released 2.7.
-
@neiltiffin I agree with everyone here, being insulting isn't the way to go in general and what you said was pretty rude regardless of who it was directed at.
But secondly, do some looking around at pfsense vulnerabilities, there aren't many, no all products need updates the way Microsoft does them because not all are swiss cheese. Smaller issues are also usually addressed via System Patches or package updates depending on what the issue applies to.
If you do some googling about it though there aren't really a lot of known security issues or POC exploits for it even historically speaking.
-
@SteveITS said in CE Update Frequency:
@neiltiffin System Patches is version specific, and they issue a package update for new patches. Or they are usually posted in forum or from Redmine entries. Typically used for PHP code or non binary files.
https://docs.netgate.com/pfsense/en/latest/development/system-patches.html
Thanks, that was non-obvious. I manage a number of Linux systems security updates are applied by doing a system update/upgrade. It seems rather annoying that there is no notification that I should be applying a System Patch. I can't even tell if there are any that are applicable. I sure hope the experience is better with the pfSense Plus.
So I went see if there are any System Patches on 2.6 CE and guess what? It does not work.
pfSense-pkg-System_Patches installation failed!
WARNING: Current pkg repository has a new PHP major
version. pfSense should be upgraded before
installing any new package.Look, It does not seem like anything posted here is changing my opinion. Version specific updates is a system problem that was solved decades ago, but it seems like the pfSense developers just don't get it and everyone here seems ok with that.
2.7 is too new and my experience with new major upgrades is that an upgrade will take me a day to get things working again, there are multiple forum entries with problems and no responses. Did I mention that my hardware is a Netgate appliance.
-
@neiltiffin said in CE Update Frequency:
If you would read the forum or doc , instead of "whining & nagging" , you would discover that pfSense is automatically switching update source to latest Branch , when it becomes available (here 2.7). As it is expecting you to upgrade to latest.There are a kazillion posts, about : DON'T upgrade packets before upgrading pfSense , when an upgrade is available.
If you want to stay on "previuous" update branch, you have to "manually" switch back to previous.
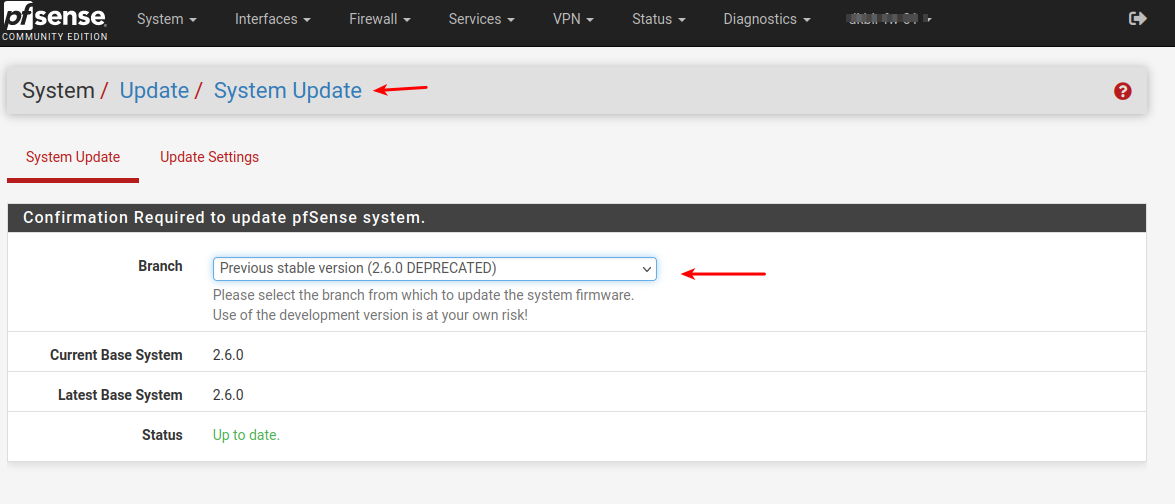
Then your system would also stop showing there is an update , and that you are on latest.
And if you didn't FSCK up your packages/system already, by trying (succeding) to install 2.7 packets on a 2.6 system
You should be able to install 2.6 (Previous) packets now.Did I mention that my hardware is a Netgate appliance.
So you could even have gotten Netgate to help out, instead of bashing them ...
SIGH ....
/Bingo
-
@planedrop said in CE Update Frequency:
@neiltiffin I agree with everyone here, being insulting isn't the way to go in general and what you said was pretty rude regardless of who it was directed at.
But secondly, do some looking around at pfsense vulnerabilities, there aren't many, no all products need updates the way Microsoft does them because not all are swiss cheese. Smaller issues are also usually addressed via System Patches or package updates depending on what the issue applies to.
If you do some googling about it though there aren't really a lot of known security issues or POC exploits for it even historically speaking.
Yep did that and found 2 major ones that apply to pfSense 2.6: CVE-2023-27100 (related to SSH) rated 9.8 out of 10, and CVE-2022-23993 rated 6.1. Now CVE-2022-23993 does not apply to me. CVE-2023-27100 does apply and not issuing a .x update is in my opinion not very responsible although the report is very new and I assume that Netgate's solution is to update to 2.7.
Secondly, most of the time security vulnerabilities are not published until after a fix has been issued. So yes, there is at least one major vulnerability that went un-resolved in pfSense 2.6.
FreeBSD lists 13 security vulnerabilities acknowledgments that were fixed in FreeBSD 12.4 that phSense skipped. Not sure how many apply to pfSense.
However there are at least 8 reported CVE vulnerabilities in FreeBSD 13.0. I wonder how may have been fixed on pfSense 2.7? Maybe we have to wait another 1.5 years for these fixes? Are they fixed in pfSense Plus in a more timely manner?
None of this gives me the feeling that Netgate is supporting pfSense CE in a way that I expect, which is issuing security updates in a reasonable time. Functionality is a different story, but firewall software needs to be secure and especially today when vulnerabilities are found daily.
-
@bingo600 said in CE Update Frequency:
@neiltiffin said in CE Update Frequency:
If you would read the forum or doc , instead of "whining & nagging" , you would discover that pfSense is automatically switching update source to latest Branch , when it becomes available (here 2.7). As it is expecting you to upgrade to latest.SIGH ....
/Bingo
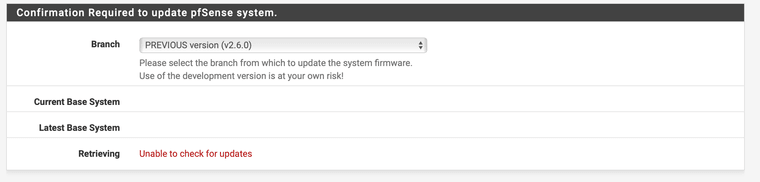
The reason to use a UI is so that it does not allow one to "shoot yourself in the foot". Guess that does not work either?
-
@neiltiffin
Refresh Main Page a few times ???Should show this
And the Unable to check for update should go away
Edit: Don't bother answering ... You are now "Officially" on my Forum Block List
/Bingo
-
You seem very hostile to folks trying to help. You insulted a company from the very beginning, complained about the lack of security updates, whined about how you can’t get older versions of code with security vulnerabilities, admitted that you have a Netgate device so you continue to fund the company that you think is “brain dead”.
I don’t get you. You’re a contradiction.
I guess that’s what trolls do on the internet - cause controversy but don’t you think your time would be better utilized doing something else? You’re that bored you rather be a forum troll? Why? -
@neiltiffin if you have a Netgate unit and want faster updates just run Plus. 3x per year is the target there.
Don’t install packages for the wrong version; see my sig.
https://redmine.pfsense.org/issues/10464
https://docs.netgate.com/pfsense/en/latest/troubleshooting/upgrades.html#upgrade-not-offered-library-errorsSystem Patches is relatively new, the last year or two. Might have been after 2.6.
-
@SteveITS said in CE Update Frequency:
@neiltiffin if you have a Netgate unit and want faster updates just run Plus. 3x per year is the target there.
Nah, I'll switch first. I originally used Netgate and pfSense because it was open source. I understand the need for support. I originally bought a Netgate appliance and paid yearly for the "gold" whatever it was. I would not mind paying $100 to $200 per year for security. But I no longer support proprietary code running on my key edge devices. If I wanted that I would just as easily go purchase a Juniper or Cisco firewall.
Don’t install packages for the wrong version; see my sig.
https://redmine.pfsense.org/issues/10464
https://docs.netgate.com/pfsense/en/latest/troubleshooting/upgrades.html#upgrade-not-offered-library-errorsSystem Patches is relatively new, the last year or two. Might have been after 2.6.
Yeah, thanks for the help.
My problem with System Patches, now that I am aware of them, is that I cannot find any source of notifications about them being published. I looked at GitHub and read the documentation at https://docs.netgate.com/pfsense/en/latest/development/system-patches.html.
Did I miss something? Or is the only way to know is to go into the firewalls patches UI and see if there is anything not applied?
-
@neiltiffin There will be a package update when new patches are added. Often they come from patches from Redmine reports or linked in forum posts.
Jim has posted pinned threads in https://forum.netgate.com/category/16/pfsense-packages for updates.
-
@michmoor said in CE Update Frequency:
You seem very hostile to folks trying to help. You insulted a company from the very beginning, complained about the lack of security updates, whined about how you can’t get older versions of code with security vulnerabilities, admitted that you have a Netgate device so you continue to fund the company that you think is “brain dead”.
No, I have a hostile opinion about a company that is not performing the way I think they should. I've not insulted any individuals or anyone that was willing to help.
My Netgate device is old, make that probably 2014. I need to replace it and it looks like I am going a different direction. Until pfSense Plus I was generally happy with pfSense except for the fact that the UI upgrades easily blew up.
Not happy any more, but I guess you and others that attack the form of the message are not interested in that and the facts.
I don’t get you. You’re a contradiction.
If you don't want to hear my opinions then block me. Won't hurt my feelings.
I guess that’s what trolls do on the internet - cause controversy but don’t you think your time would be better utilized doing something else? You’re that bored you rather be a forum troll? Why?
Nope, I am a frustrated user that is wondering why Netgate has chosen to move in a direction what will lose me as a customer.
If you're not going to help, why respond at all. Oh I get it, can't refute the facts so attack the messenger.
The fact remains that any edge security devices that have not received any security updates in 1.5 years in todays environment is a problem (which I just realized regarding pfsense 2.6 to 2.7 without any intervening updates).
The fact that updates are hidden away in patches is a problem. Normal people do not consider patches something that is done on a regular basis unless one is having problems.
Not saying there are not valid reasons for each, but as a user that is not a full time firewall monitoring person these reasons are not so important for my use case.
-
@neiltiffin said in CE Update Frequency:
The fact that updates are hidden away in patches is a problem. Normal people do not consider patches something that is done on a regular basis unless one is having problems.
You're right here. The way notifications (lack thereof) of patches goes out is extremely poor. Its a step in the right direction but i agree that overall notifying admins about updates needs to be done better. Perhaps a system notification with a blog post? I dont know but anything is better than whats used now.
@neiltiffin said in CE Update Frequency:
My Netgate device is old, make that probably 2014. I need to replace it and it looks like I am going a different direction. Until pfSense Plus I was generally happy with pfSense except for the fact that the UI upgrades easily blew up.
IMO, and this is pure conjecture of course, but the community forums doesnt seem to be the place where management look to get feedback. The place for that is on redmine where you can open feature requests/bug reports/etc. Maybe the devs and management do monitor the forums and see where the pain points are. I highly suspect they dont. Like i said, redmine.
@neiltiffin said in CE Update Frequency:
The fact remains that any edge security devices that have not received any security updates in 1.5 years in todays environment is a problem (which I just realized regarding pfsense 2.6 to 2.7 without any intervening updates).
Ehhhh I am running Palo Altos at my job and we're stuck on the 9.0 track. 10.2 recently got released. Its not common to upgrade firewalls constantly unless there is a legitimate business need. Its just to disruptive. As mentioned, pfsense plus has more frequent updates so that avenue is there for everyone if they choose to upgrade to that. The way I view it is that CE is more for the home/lab , enthusiast community. You'll get updates when you get them. pfSense plus is for businesses that want/need frequent updates and exclusive features (boot environments for example).
Finally, everyone should select a firewall based on their requirements. If you need frequent updates but dont want to pay for enterprise licensing then go with OPNsense. Some people like myself like the staggered rollout of updates throughout the year. Perhaps that is Netgate's philosophy - a slow upgrade path and a focus on reliability and security.
You are still all over the place with what you want. As I and a few people have mentioned, you can't have your cake and eat it too. You want old versions of software but you complain about security? You get on here to complain into the ether and then state you are moving in a different direction--huh?
You talk about security features in FreeBSD main but i asked you in the very first post - what security vulnerability do you believe was missed and Netgate never addressed? You never answered my question which leads me to believe you either dont know of any or to lazy to research the CVEs and its impact if any on pfsense. Again, you're just all over the place. -
@neiltiffin See this is precisely the issue, it's important to actually read into the vulnerabilities before just saying CVSS 9.8 it's the end of the world.
If you knew what the actual issue was, it's basically a non issue. No one should be exposing their firewall webGUI to the public internet anyway, or any untrusted network for that matter, it should be accessed over a VPN. The whole purpose of that general best practice advise is to avoid issues like this being a problem (which BTW basically every other firewall has had similar login related CVEs that were super bad, many worse than just brute force allowance) when they do pop up. While it's important for things like this to be fixed (and it is fixed) regardless, admins still need to practice best security advise.
Additionally, all this vuln lets you do is brute force without any restrictions, but if you're following another best practice and using good strong login credentials, it shouldn't matter anyway.
I also don't understand this: "at least one major vulnerability that went un-resolved in pfsense 2.6", so what you are saying is that something got fixed but since it wasn't fixed in the version you wanted it to be fixed in it's not ok? IDK what to tell you at that point.
IDK this is all seeming like a common internet post where someone wants attention so they just complain about stuff without really knowing what they're talking about.
-
 J jimp moved this topic from Problems Installing or Upgrading pfSense Software on
J jimp moved this topic from Problems Installing or Upgrading pfSense Software on