VLAN parent Interface LAN no routing from VLAN to LAN
-
Hi,
I am in a migration from Sophos UTM to pfsense and so far I have everything up and running except one little thing where cant get a solution even after googling and reading for hours.
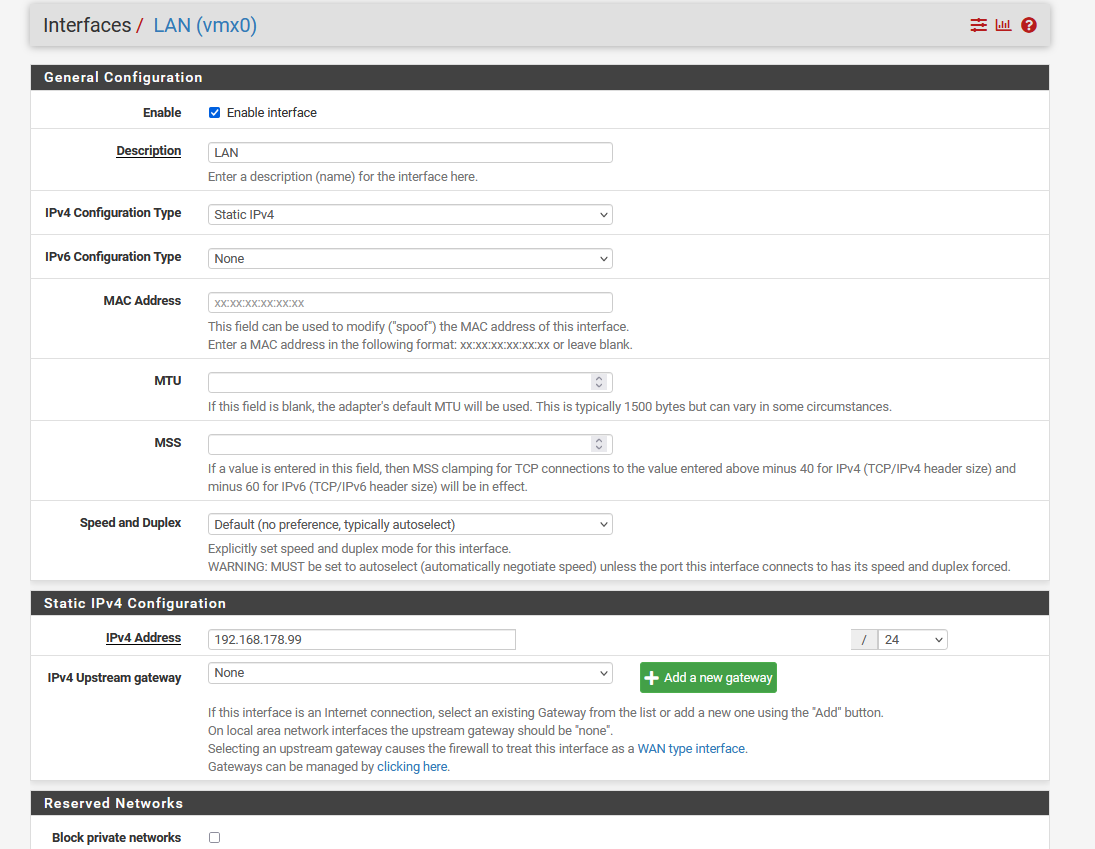
My pfsense has two NICs. One for WAN and one for LAN.
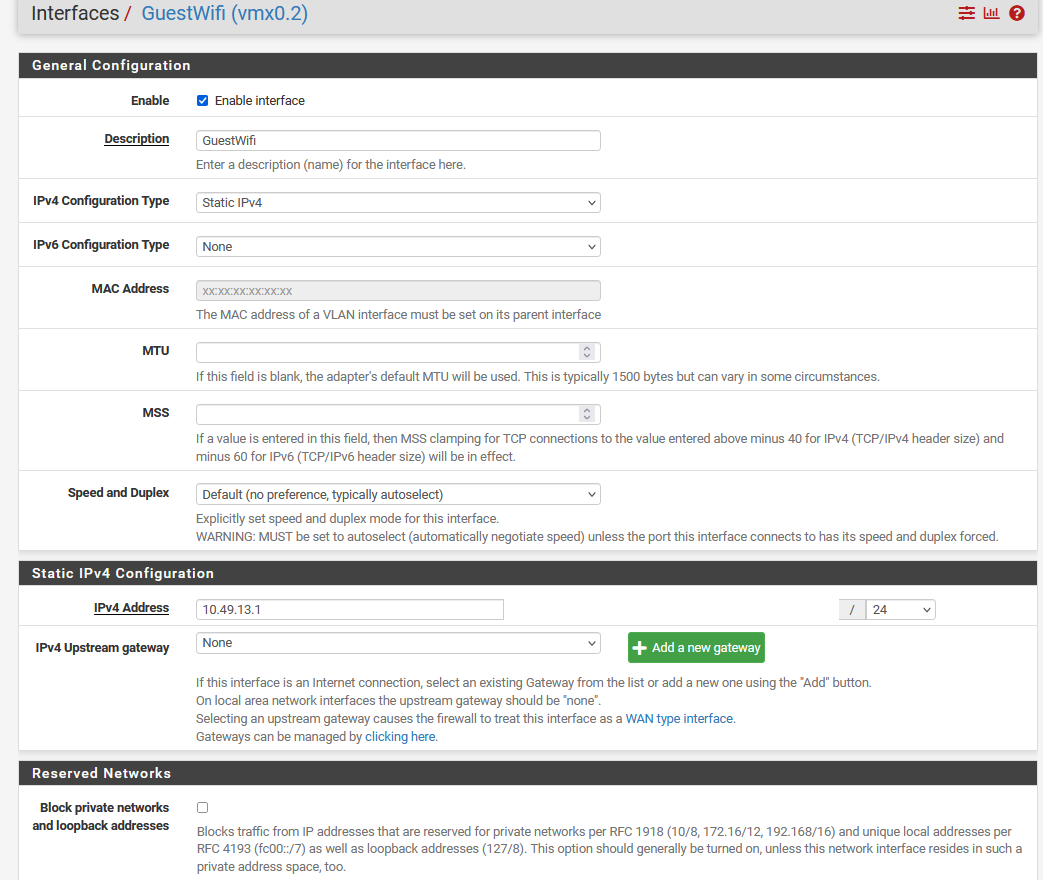
On LAN I also added 1 VLAN to seperate my GuestWifi from my LAN.GuestWifi is working fine. Clients in their do receive the correct IP Addresses from pfsense DHCP Server and they are also able to access Internet.
The only thing that isnt working is, that I cant reach any device from one subnet to another.
So e.g. a GuestWifi Client with IP 10.49.13.10 is unable to reach a webserver on 192.168.178.10.I assigned IPs to every interface and only the WAN Interface has a Gateway defined.
I also changed all the firewall rules to "any any" without success.I cant even see in the firewall log, that the GuestWifi Client is trying to reach a Client in the LAN Segment.
If I ping from GuestWifi Client to Gateway Addresses in both VLAN and LAN I do get a reply and also this traffic is logged in Firewall Log.
But as I said, I am unable to get another Client from one subnet to another.I made a little simple drawing. Green represents traffic that works, red one which does not work.
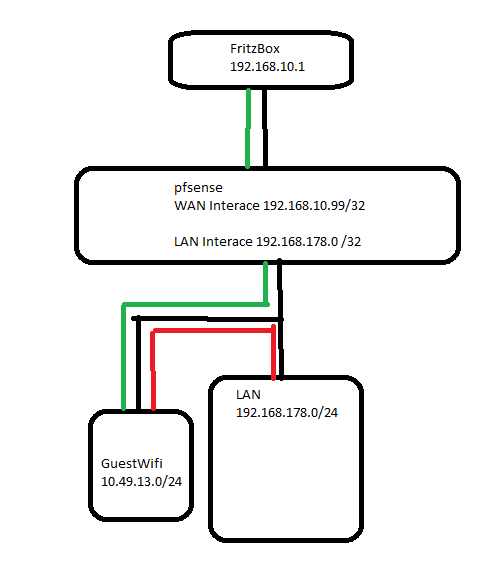
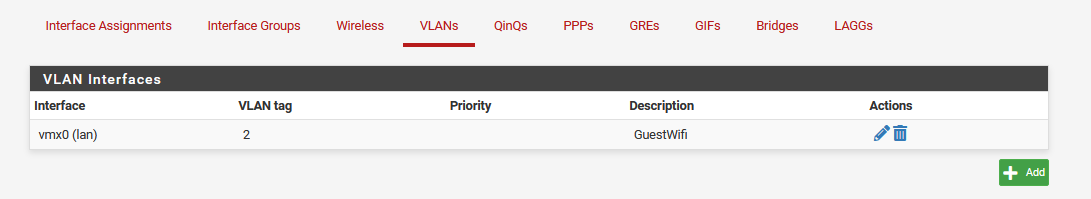
I now read a lot and found some articles stating, that having VLAN on "LAN Interface" problems could accur regarding routing.
Dont know the exact reason, but I guess "tagged, untagged problems etc.".Could this be my problem?
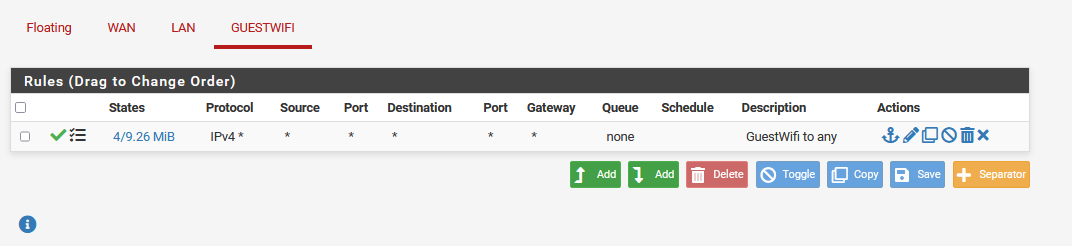
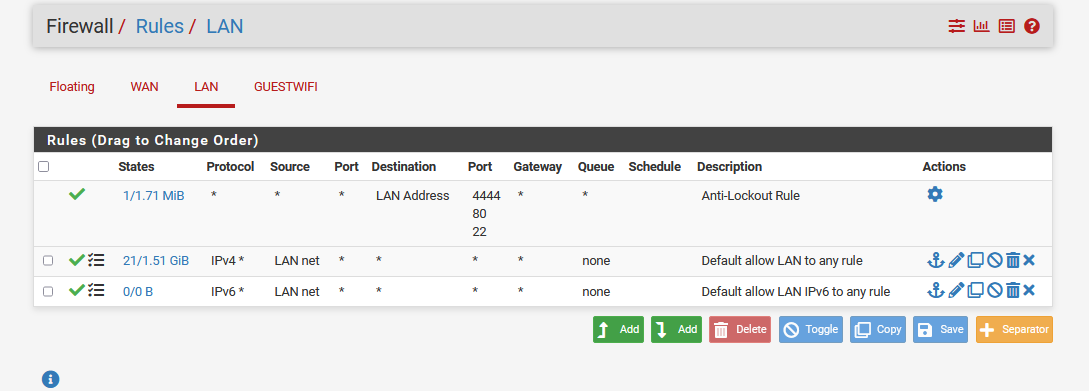
Hope someone is able to give some hints.
The pfsense is running on ESXi 6.7 and the LAN Interface that is mapped from esxi has 4095 as VLAN ID (within esxi)
Also the VLAN is tagged on the underlying HP Switch.Thanks a lot and regards
Christian -
@cpohle said in VLAN parent Interface LAN no routing from VLAN to LAN:
I now read a lot and found some articles stating, that having VLAN on "LAN Interface" problems could accur regarding routing.
Dont know the exact reason, but I guess "tagged, untagged problems etc.".But none of these problems are caused by pfSense. Mostly this is due a VLAN misconfiguration outside, so that the L2 is leaking or somewhat else.
First of all ensure that your destination device is accepting access from outside of its own subnet. By default this is not allowed and you have to configure its firewall properly.
To investigate the routing you can use Diagnostic > Packet Capture on pfSense to analyze the traffic on LAN and VLAN.
Also check the firewall log for block lines.
-
@cpohle said in VLAN parent Interface LAN no routing from VLAN to LAN:
that having VLAN on "LAN Interface" problems could accur regarding routing.
Where did you read this - do you have a link? if I took a guess to what that is about, I would say they were talking about using your lan as a transit for a downstream network. Which yes could and will cause asymmetrical routing.
But having tagged vlan isn't going to cause any problem no matter what "interface" its on in pfsense. As long as the vlan and the parent native "vlan" (untagged) are correctly isolated throughout the network.
Or maybe you were reading something that said its not good to have untagged and tagged networks on the same interface. There is some common practice in enterprise networks to not run untagged (native) vlan and then tagged networks on the same interface.
While running only tagged is one way to do it. 1 Untagged or "native" network while other vlans are tagged works just fine - comes down to more of policy of the network to try and prevent any mistakes or ability to access a network without configuration.. This can prevent possible issue where tag was not used and then have access to a network not suppose to have.
Comes down to oh forget to set a vlan on this interface, and now its in default vlan 1, and something plugged into this port is now on the default vlan which is untagged.
As long as your network is setup correctly, you can run 1 untagged network/vlan on an interface along with other tagged vlans. What can not do is have more than 1 untagged vlan, and your pvid need to be setup correctly for any ports that will have untagged vlan, and tagged vlans on them.
-
@johnpoz
I don not know where I read this to be honest. If I find the link I will of course share it.Here was someone with a similar problem:
https://forum.netgate.com/topic/138670/routing-between-interfaces-lan-vlan/16I would guess that VLANs are correctly Tagged/Untagged in both esxi and the Switch as my Clients in the VLAN do receive the right IP from the DHCP Server on the PFSense. Also they are able to reach the Internet.
Only thing that isnt working is from VLAN to LAN. Hosts in my LAN are accepting connections from VLAN Subnet for sure. There is no Client Firewall active or so.
If it would be Firewall related I would expect to see something in the logs. But I dont see anything there!
Here is my route print from the pfsense GUI
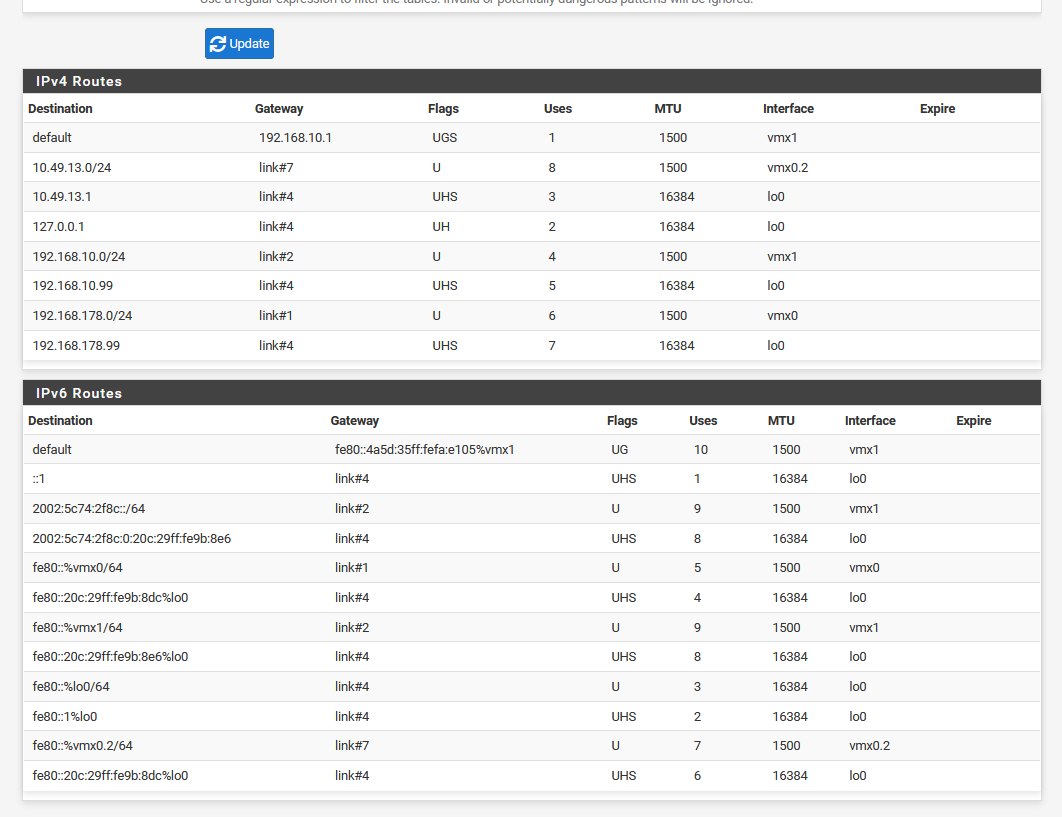
Thanks Guys!
-
@cpohle said in VLAN parent Interface LAN no routing from VLAN to LAN:
in both esxi and the Switch
So your passing all the tags to pfsense via setting a vlan ID on the esxi vswitch/port group to 4095 (VGT).. There are couple different ways to handle vlans in esxi, you can have esxi handle it by creating vswitches or port groups that are in the specific vlan. Or you can pass the tags to pfsense interface by setting 4095
its possible you got some weirdness in that configuration?
-
I captured the traffic coming from VLAN. My iPhone with IP 10.49.13.10 is trying to open http website under 192.168.178.21.
I cant find anything in the capture file regarding such traffic.
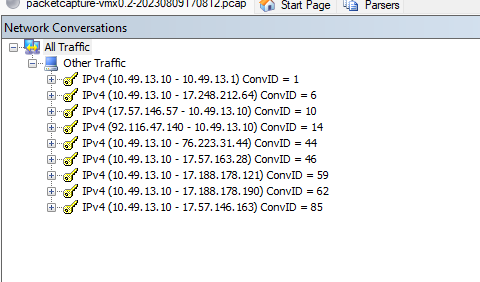
What in hell I am doing wrong? Shouldnt I see at least anything trying to connect to this target subnet 192.168.178.0/24?
-
@cpohle
Maybe a guest wifi configuration on the AP which only allows access to public destinations? -
@viragomann
Could be, I will check this again. As far as I could see, all security related features within the GuestWifi were turned off. Its Ubiquiti APs btwHere is my network config in my esxi
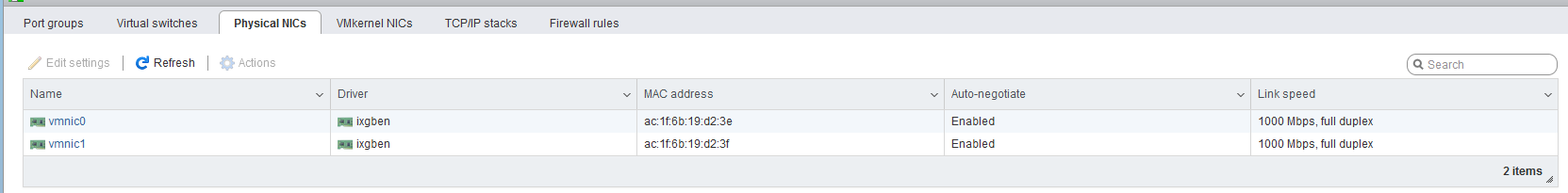
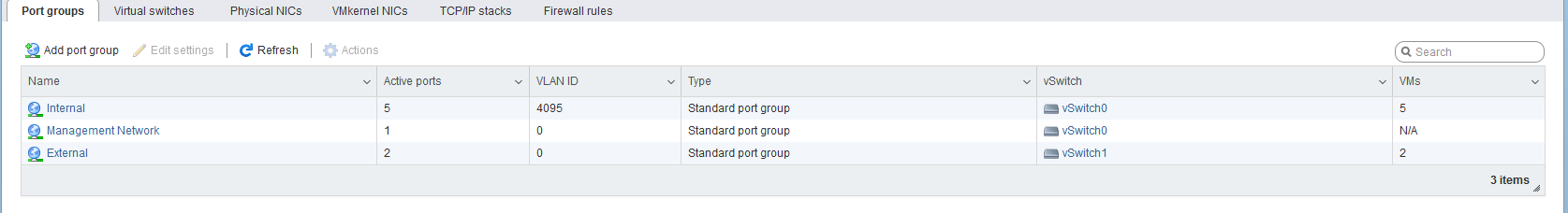
Let me know if you need other infos as well.
-
@viragomann And exactly that was the case/issue.
The VLAN contains my GuestWifi Clients. On the Unifi APs I had seperate LAN configured and in here there was "apply Guestpoliy" option enabled.
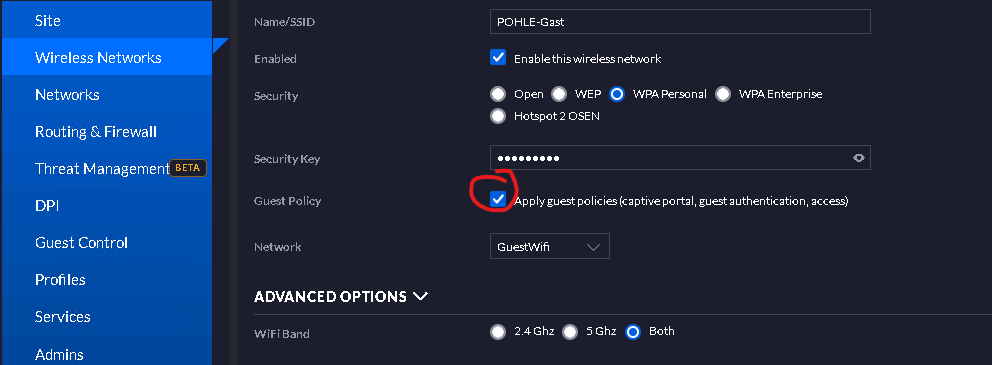
From there Ubiquiti Forum I had a description of what this feature does once enabled:
**Guest policies on VLAN will have firewall rules blocking that VLAN from all others and will apply L2 isolation.**After that checkbox was disabled I can reach the LAN Subnet just fine.
Thanks for help folks!!