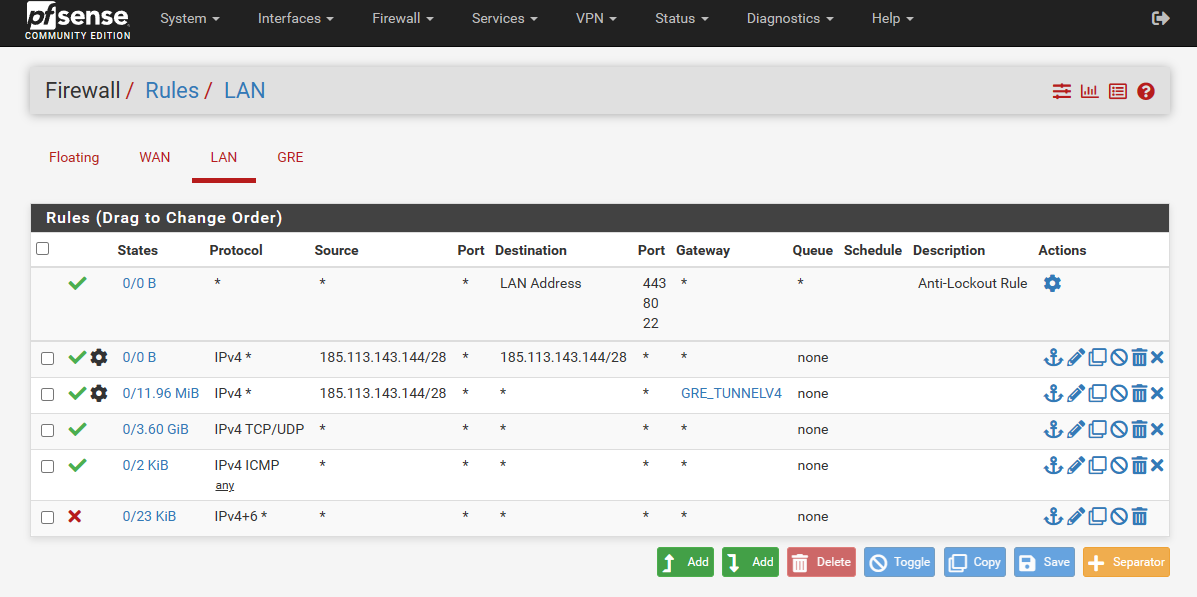
Routing tunel Gre
-
Hi
I have a gre tunnel between two pfsesne.
I have a machine with the ip 185.113.143.148 pinging continuously at 8.8.4.4 locally.
Traffic passes through the tunnel and the remote pfsense wan interface receives the response from 8.8.4.4.The problem is that traffic received from 8.8.4.4 is not passing from the wan to the gre tunnel on the remote pfsense.
I tried with that firewall rule and without success.
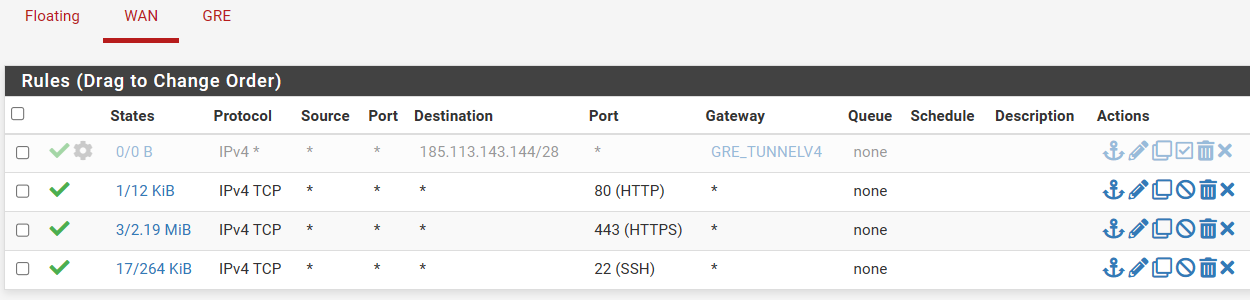
I tried with a static route and also without success.
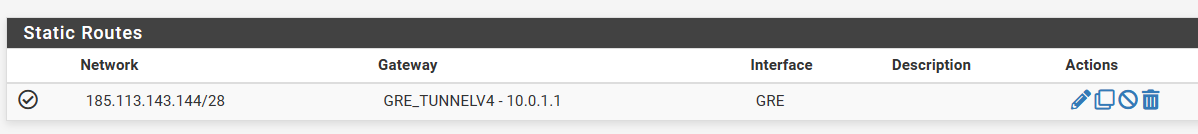
Can anyone help me understand what I'm doing wrong?
Thanks
-
Check the states at both ends while the ping is running. Make sure you see states on the GRE interfaces at each end and the NAT state on WAN at the end it leaves.
Check the firewall logs at each end for blocked traffic.
-
Thanks
I already managed to solve this problem I think it was from the states. Now another problem has arisen in the local pfsense, I wanted the traffic in the local network to communicate without leaving the network, only when access to the internet is necessary to go out through the tunnel, I tried to do the following but it is not working very well, it seems that something thing loops and I get lossy sometimes. If the rule is only to forward the traffic through the tunnel, the machines cannot communicate within the network. -
Traffic between hosts inside that /28 never goes through the firewall so that pass rule you've added does nothing. You can see there are no states or bytes shown on the rule.
-
When I remove this rule the following appears to me.
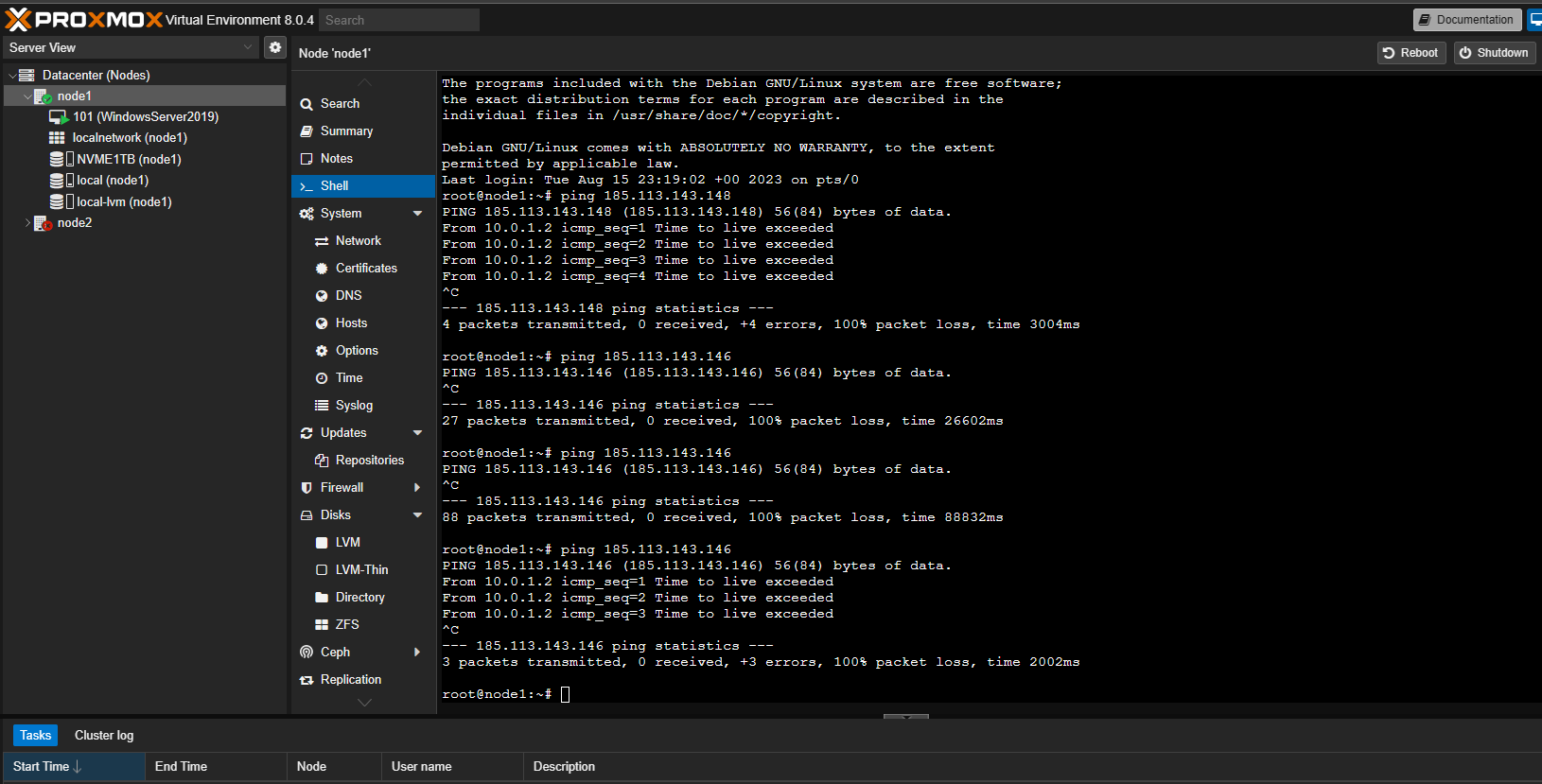
If I add the rule the ping works.
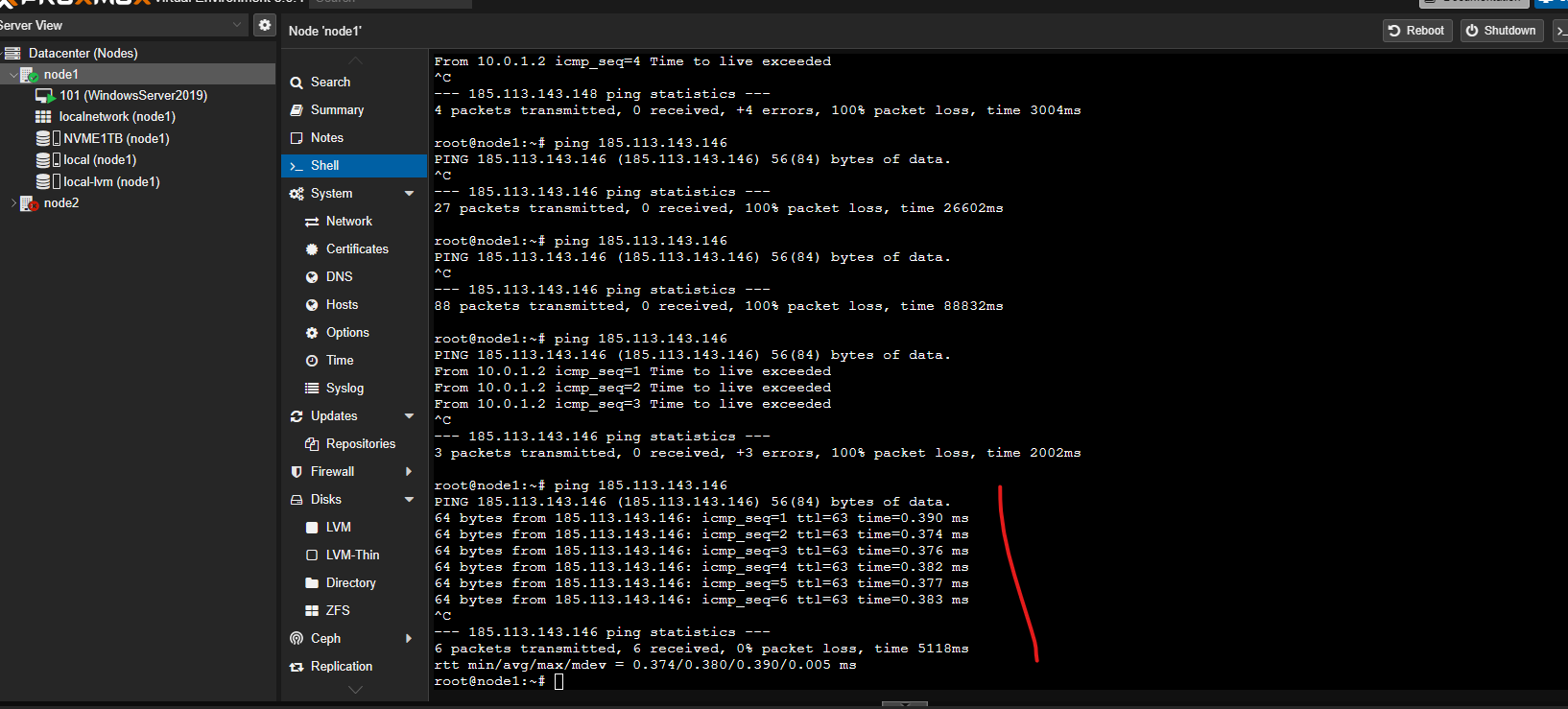
It's a bit weird
-
Hmm, you have something bridged? What are those IPs? If is the pfSense LAN address you might hit it.
-
Thanks,
I had misplaced the ip`s in the proxmox by putting the mask /32 instead of /24 so obviously they weren't communicating because they were on different networks.
Compliments
-
Ah, that would do it!