Patches update
-
@JonathanLee so you are redirecting to pfsense then?
-
@michmoor there is a built in redirecter for blocked urls that is in Squidguard. It's inside of pfSense
-
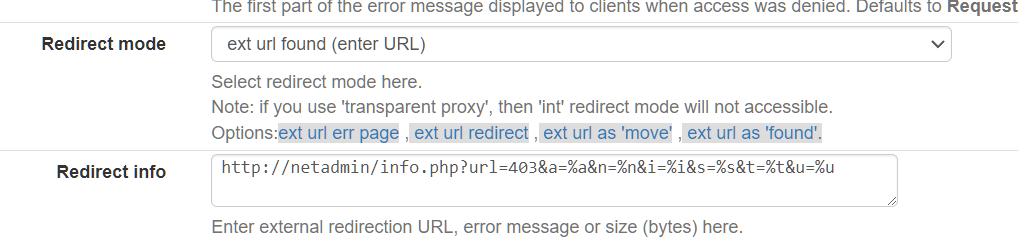
@JonathanLee Ive been using the 'ext url found (enter URL) option. I have an instance of Apache stood up
What option are you using? Im asking because if you select internal then pfsense serves the page but you need to allow access to the management port (443) which isnt a good option .
-
As far as I remember, those redirects always worked.
But they won't work for HTTPS since the domain blocked does not match the certificate presented by squidguard, thus the browser will prompt that error. -
@mcury
If you use an external redirect which is what i do then http or https blocks dont matter as its being sent to my web server which is listening on port 80.
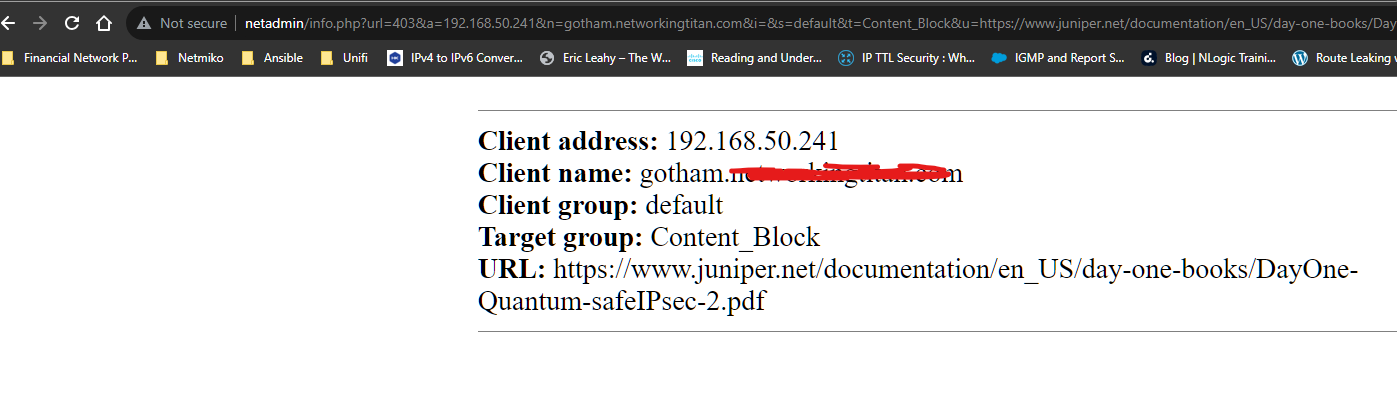
I just didnt want a dependency on something outside the pfsense box but its the only preferrable solution i can think of.So for exampleanything matching my squidguard block gets sent to http://netadmin/info.php?url=403&a=%a&n=%n&i=%i&s=%s&t=%t&u=%u
netadmin = locally hosted web server
-
@michmoor said in Patches update:
If you use an external redirect which is what i do then http or https blocks dont matter as its being sent to my web server which is listening on port 80.
I just didnt want a dependency on something outside the pfsense box but its the only preferrable solution i can think of.I don't see how a browser would allow that without showing a certificate error.
If you request a https URL, the browser is expecting the domain to match with the certificate, this is how SSL works.
Did you disable something in the browser for that to work ?Are you using bump or splice option ?
-
-
-
@mcury Yep. Sorry if that wasnt clear.
I am doing full MITM.If you rely only on the internal redirect then pfsense points back to itself on the management port (firewall.example.com:443) .
The problem of course is that in order to serve the page you must make your management port accessible to all LAN clients. That means making management accessible to all LAN clients. The only workaround is to use an external webserver that has php code on it to interrupt whats being sent to it from pfsense -
@michmoor said in Patches update:
Yep. Sorry if that wasnt clear.
I am doing full MITM.Np, I was just trying to understand :)
@michmoor said in Patches update:
If you rely only on the internal redirect then pfsense points back to itself on the management port (firewall.example.com:443) .
The problem of course is that in order to serve the page you must make your management port accessible to all LAN clients. That means making management accessible to all LAN clients. The only workaround is to use an external webserver that has php code on it to interrupt whats being sent to it from pfsenseNow I see what you meant, yes, indeed that would be a problem.. Using an external server for that solves this problem.