Uni-directional traffic with NAT IP via IPSec VPN
-
Hi! All How to configure Uni-directional traffic with NAT IP via IPSec VPN
Scenario is defined in image.
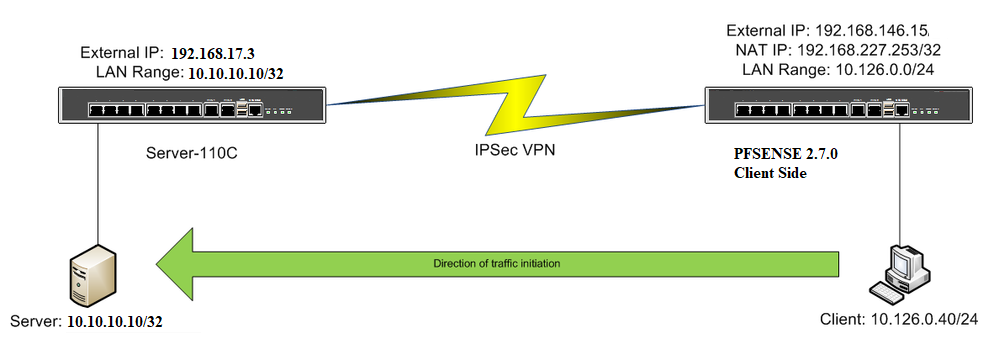
-
@mralvi22244
Unidirectional access can easily be achieved by allowing nothing on IPSec at the right side.However, I'm wondering what you want to achieve with NAT. Do you want to masquerade the right sides access through the VPN with that IP?
-
@viragomann
Hi!
It is requirement of service provider. They provide me (Your Source/Natted/Tunnel IP address will be 192.168.227.253/32 "Route Base VPN" Primary Link)
When I configure Natted in IPSec P2 Local Subnet 192.168.227.253 and Remote Subnat 10.10.10.10/32.
In Routing GW 10.10.10.10 appearing. -
@mralvi22244
So in your phase 2 you have to select "Network" at Local Network and enter 10.126.0.0/24.At NAT/BINAT translation select "Address" and enter 192.168.227.253 for doing the NAT to this single address.
At Remote Network also select "Address" and enter 10.10.10.10.
-
@viragomann
Dear
It is possible in P2 VTI option. I have configured same scenario in Fortinate Through IPSec with Routing, which is working fine. But my production environment is configured with PFsense. -
@mralvi22244 said in Uni-directional traffic with NAT IP via IPSec VPN:
It is possible in P2 VTI option.
Not that I'm aware of.
-
@viragomann
Please provide some guideline for VTI process. -
@mralvi22244
NAT is not supported for VTI IPSec at this time. -
@viragomann
So how will I process NAT in VTI, is there any way
NATted IP with routing protocol working in FN. Should I change Device or It will working in IPSec tunnel protocol with NAT/BINT 1:1. -
@mralvi22244
I would try it with policy based tunnel as suggested.I'm not familiar with VTI, but as I understand it, in this case you have to state 192.168.227.253 as your local address and 10.10.10.10 as remote.
Then assign an interface to the concerned IPSec instance, enable it, no IP settings.
Then you should be able to apply an outbound NAT rule to it.If the outbound NAT is still in automatic mode, enable hybrid mode first. Then add a rule:
interface: that you have created before
source: 10.126.0.0/24
destination: 10.10.10.10/32
translation: interface address -
@viragomann
Dear this suggestion is for VTI or policy base -
@mralvi22244
As I wrote, the above with BINAT in IPSec is meant for policy-based tunnel.The last one is how I think, it has to be configured with VTI.
However, I'm unsure if it will work with the stated local / remote addresses, 192.168.227.253 / 10.10.10.10. Accordingly to the pfSense docs both addresses have be within a (transit) network. But yours obviously aren't. Don't think, that IPSec can do PPP.
But these are the data you stated.