Module resolving ipv6 when no ipv6 on the network
-
I have the Tailscale module installed and launched, however it cannot contact its control servers because it's attempting to use an IPv6 address. The greater network only has link-local IPv6 addresses and no gateway so it is failing. I've tried using DNS Resolver and Forwarder to no success, I can't coax it into using any of the IPv4 addresses that are returned by nslookup or diagnostics.
What am I missing?

-
@gesundheit40 hmmm - I would log into the tailscale site and look at your admin console do you happen to have disableIPv4 set to true in your access controls?
-
@johnpoz Sadly the module can't get far enough to know it's part of my tailnet. The module is trying to reach the control server on the ipv6 address which is impossible because I don't have any ipv6 infrastructure. I assume this is because modules run directly on the OS which will always prefer IPv6?
-
@gesundheit40 I am by no means an expert when it comes to tailscale.. But you could check the admin console on the tailscale site be it pfsense can connect to it or not..
Just go to https://tailscale.com/ and login.
The only thing off the top of my head that "might" be able to cause that is your settings on tailscale site. Its just a guess, pretty sure you would of had to have messed with that.. But should only take you like 10 seconds to check it..
What version of the package are you using on what version of pfsense? I show
pfSense-pkg-Tailscale 0.1.4 pfSense package Tailscale
tailscale 1.44.0 Mesh VPN that makes it easy to connect your devicesI am on 23.05.1
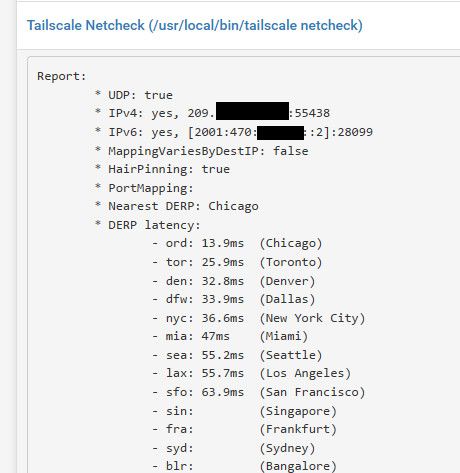
Your only showing the status section - what does your netcheck section say? Example
-
@johnpoz said in Module resolving ipv6 when no ipv6 on the network:
@gesundheit40 I am by no means an expert when it comes to tailscale.. But you could check the admin console on the tailscale site be it pfsense can connect to it or not..
Just go to https://tailscale.com/ and login.
The only thing off the top of my head that "might" be able to cause that is your settings on tailscale site. Its just a guess, pretty sure you would of had to have messed with that.. But should only take you like 10 seconds to check it..
Yup, just verified. We have many other devices that are communicating over IPv4 successfully.
What version of the package are you using on what version of pfsense? I show
pfSense-pkg-Tailscale 0.1.4 pfSense package Tailscale
tailscale 1.44.0 Mesh VPN that makes it easy to connect your devicesI am on 23.05.1
Latest from this morning, so 1.44.0.
Your only showing the status section - what does your netcheck section say? Example

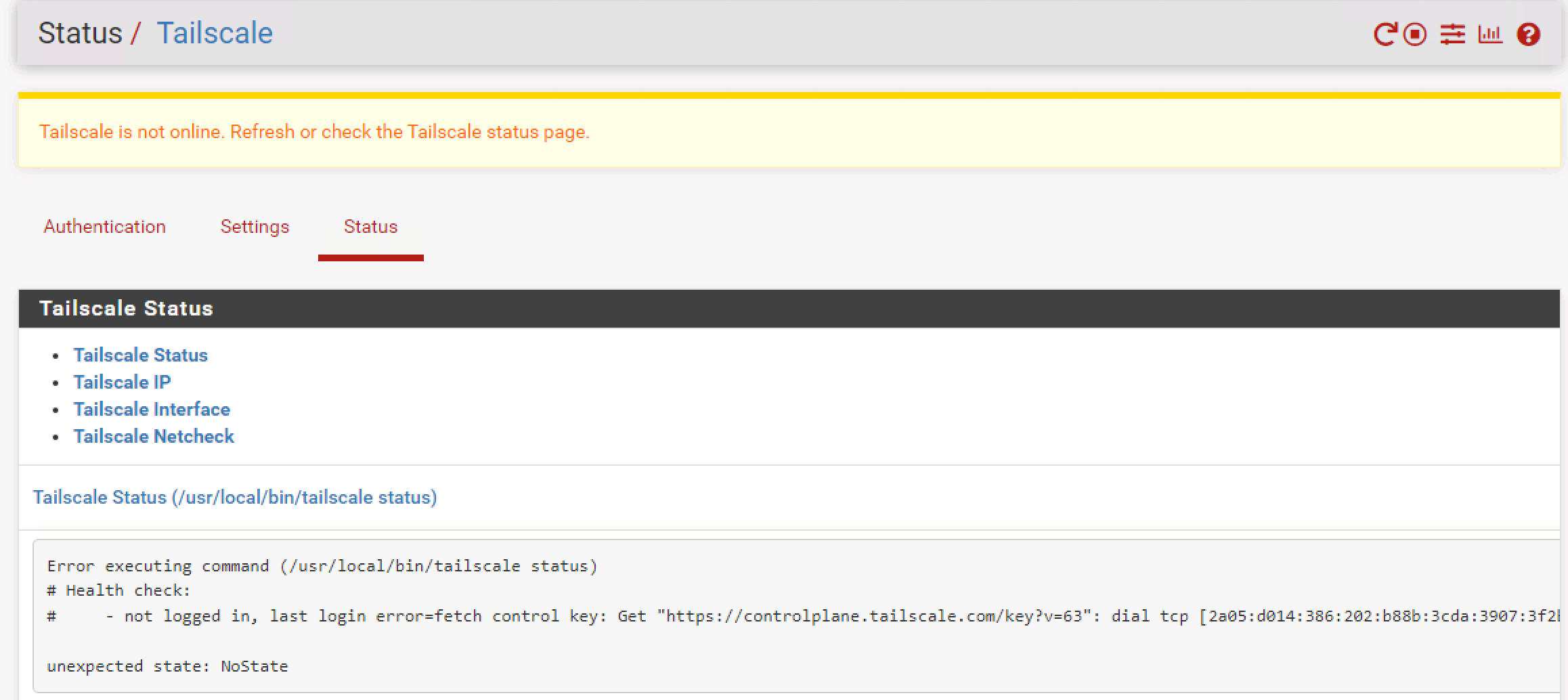
I don't have the exact output (for reasons you'll see below) but it was along the lines of "tailscale not connected". Which makes sense because it can't communicate with the coordination server because it is using a DNS response that won't ever work. I can also confirm that it has never used the auth key that I generated for it, therefore can confirm it did not reach the server.
I rebooted to try to clear things out and now I've lost remote connection to it and I don't have hands there to help at the moment. This means that it somehow forgot my interface configuration? At this point I'm going to have to do a much deeper dive into what is wrong with this unit (Sadly this is my first experience with pfsense so not looking good). Thank you for trying to help.
-
I am having a similar issue as gesundheit40 ; my tailscale instance on my router won't resolve an ipv4 address for control tailscale site
On all my other devices tailscale netdata command returns values for ipv4 and ipv6.
-
@jakedn
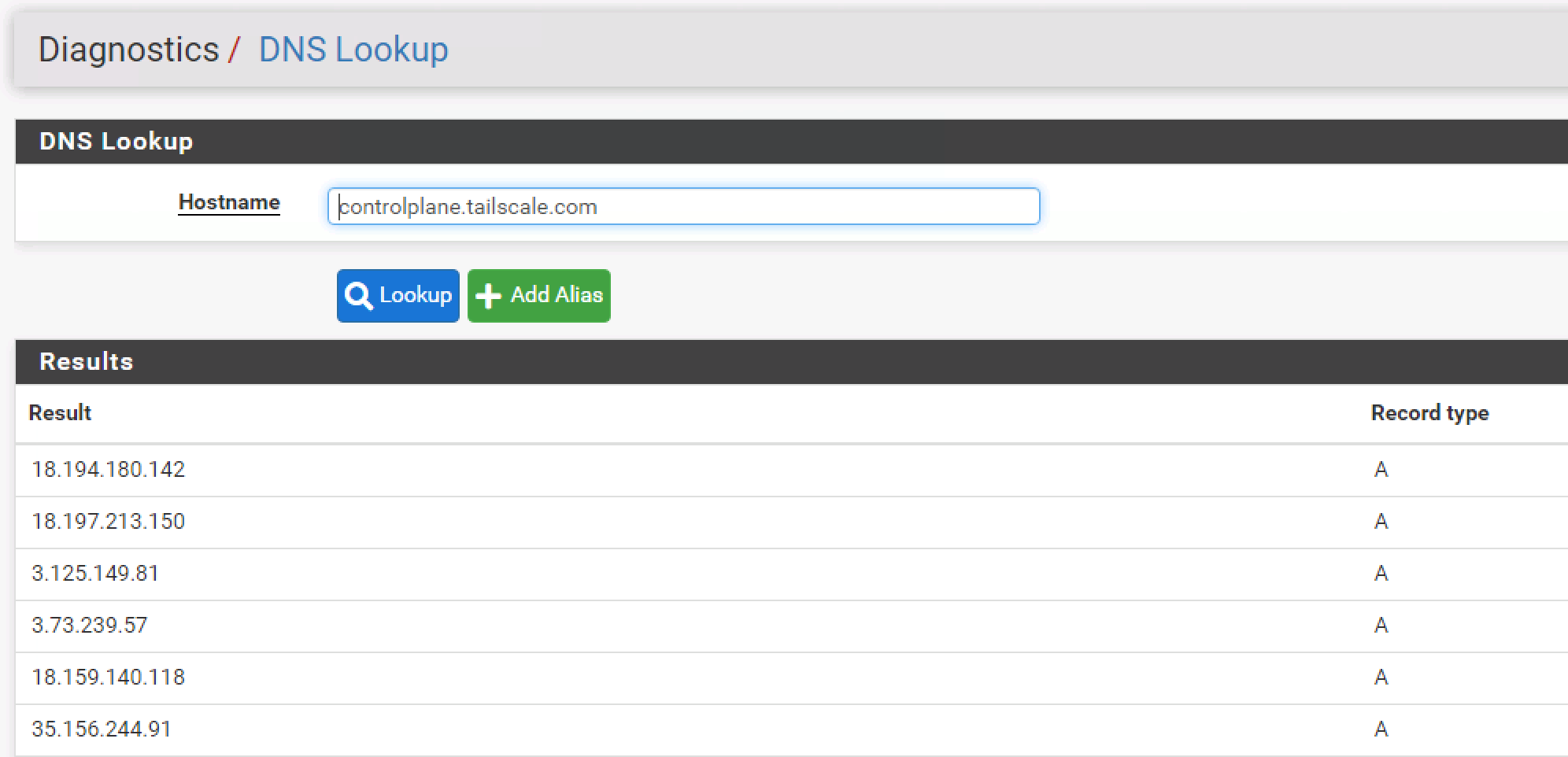
I am not sure why I am unable to post my whole comment as it gets marked as spam.On my netgate router the tailscale netcheck comes back with no result for IPv4. its result is the string (no addr found)
Things i have tried:
- Under advanced/network setting select the "prefer ipv4 to ipv6" option. This did not work.
- creating a manual dns entry for the control site with one of their ipv4 addresses.
-
@jakedn so from my understanding these are the fqdn that are required for tailscale to work. Not sure if all are needed, but would validate you can resolve them.
The list of coordination servers (required for authentication, key exchange, firewall updates, and so on) is likely to change, but infrequently: login.tailscale.com controlplane.tailscale.com log.tailscale.com log.tailscale.ioSo from like pfsense can you do a trace to that controlplane one. This is how unbound would "resolve" which is how it works out of the box, vs forwarding
[23.05.1-RELEASE][admin@sg4860.local.lan]/root: dig controlplane.tailscale.com +trace ; <<>> DiG 9.18.13 <<>> controlplane.tailscale.com +trace ;; global options: +cmd . 4839 IN NS m.root-servers.net. . 4839 IN NS a.root-servers.net. . 4839 IN NS b.root-servers.net. . 4839 IN NS c.root-servers.net. . 4839 IN NS d.root-servers.net. . 4839 IN NS e.root-servers.net. . 4839 IN NS f.root-servers.net. . 4839 IN NS g.root-servers.net. . 4839 IN NS h.root-servers.net. . 4839 IN NS i.root-servers.net. . 4839 IN NS j.root-servers.net. . 4839 IN NS k.root-servers.net. . 4839 IN NS l.root-servers.net. . 4839 IN RRSIG NS 8 0 518400 20230907170000 20230825160000 11019 . sZVaZZf8BDZooQeDPFfFdsfSRr9CE7PlaT/XuqspFo/jX93oKxzt7yYw t1k/qE2HptZNHi0LU3bd5oR70CsX/unQNyqKCRJTL7mTaXPEPWfLqJz1 /lrbCeEB79Ri/oUtuivINzHuVSRsOoSanAzE7yPN9EqhjyI9qMpWJQMy 00+4r7Xd8o+HoNcsrff8a5waEzFMG7A4anh5DLW3bZ4StqBZJ7tP+zfy ex8feHVcjh1XkztMf/aaLM/M7YVF8ZV3ixZtTKlDsjMIifst8aodXbB+ ZLlyGFq9N8248blXENE2AdebydM20FrUkvjNIKCSUS2rCSi1syatqIvw U3T3Mg== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20230908050000 20230826040000 11019 . vrbVLv8h5yGWX/CMd4dzEN4C/ylaLBtoMdxThAHF+kRePg62zVkL/rJ+ u+zEzDZ8UjJMioKEpopnGJZt3sQXy4b3CLhrtRFA/S+5L1blDvrz+tKv Qa7Juu4xQfUnJdFKFpjEqW6cBDPfUV9VguGqFZabRSNOj1jj51BbLefo Tm8IeQnTyoRd8iiaCOuizNKsJgIShvxQHARj/6//xfiArp+QrtgDqa5Q 6ZJ+xzy7xcLMe46tDPHxxa23//DH4DyUkixDLnwm//u2V7NFSua/X/w0 vLUGYbyIVyKTnz38ceHt/W5TDq/FkZ0hWQNdYH13FAuAKClBpKGgaGNX 0kuArw== ;; Received 1186 bytes from 199.9.14.201#53(b.root-servers.net) in 55 ms tailscale.com. 172800 IN NS ns-197.awsdns-24.com. tailscale.com. 172800 IN NS ns-557.awsdns-05.net. tailscale.com. 172800 IN NS ns-1558.awsdns-02.co.uk. tailscale.com. 172800 IN NS ns-1359.awsdns-41.org. CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q2D6NI4I7EQH8NA30NS61O48UL8G5 NS SOA RRSIG DNSKEY NSEC3PARAM CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20230830042423 20230823031423 4459 com. UMk0GP5j78lTU8IOTmT3FeeU6oUk82fjeHyYq/QzI4LGF8WITBLhDcbk Cj0+/frShbgy/hVAos94jmvIH4Yle4EJm5Gq64CBHv6gGYPqGojYAi8N eDPMjPuibhLcEcu2w3tz+/ZTNTA4Y6I8mSv7eMDb1shB3FImuZ7KEmbk y0eqK4Fx4mwwsAppSgfw17BQkHFLnHjtkO/Ou4ifKAdZCg== EEMFUL5DGM86JTGM8F6O53PGH4JFAQ9U.com. 86400 IN NSEC3 1 1 0 - EEMG8PC7TC9DVJESUSL15590MEJNBA2G NS DS RRSIG EEMFUL5DGM86JTGM8F6O53PGH4JFAQ9U.com. 86400 IN RRSIG NSEC3 8 2 86400 20230830061003 20230823050003 4459 com. mIuXwGRreo9eEJ7uR1c1A9/ZQob+bVk1pvBj4y7zxjdF6+pLw7AV0enL gxGnjO4NsTK/zm/psP5Pykjk3ufpxCAnZ+cY5Qy83OjAosmbMUhS9bPy ej4ydsNUXto5jqTf8bV0man6mOQslzrMg1JEMkXB2CYmgLC5/IZzGygC 3imYLkcSYWHl71OtswglW7v7Ad7F3eAxTCbgd99YFqngWQ== ;; Received 757 bytes from 2001:502:1ca1::30#53(e.gtld-servers.net) in 33 ms controlplane.tailscale.com. 60 IN A 3.125.149.81 controlplane.tailscale.com. 60 IN A 3.124.108.117 controlplane.tailscale.com. 60 IN A 3.78.132.46 controlplane.tailscale.com. 60 IN A 35.156.244.91 controlplane.tailscale.com. 60 IN A 3.74.105.242 controlplane.tailscale.com. 60 IN A 3.73.239.57 controlplane.tailscale.com. 60 IN A 18.159.140.118 controlplane.tailscale.com. 60 IN A 52.28.255.255 controlplane.tailscale.com. 60 IN A 3.125.194.96 controlplane.tailscale.com. 60 IN A 18.194.180.142 controlplane.tailscale.com. 60 IN A 3.69.76.60 controlplane.tailscale.com. 60 IN A 18.197.213.150 tailscale.com. 172800 IN NS ns-1359.awsdns-41.org. tailscale.com. 172800 IN NS ns-1558.awsdns-02.co.uk. tailscale.com. 172800 IN NS ns-197.awsdns-24.com. tailscale.com. 172800 IN NS ns-557.awsdns-05.net. ;; Received 384 bytes from 2600:9000:5305:4f00::1#53(ns-1359.awsdns-41.org) in 34 ms [23.05.1-RELEASE][admin@sg4860.local.lan]/root:Now does it work when say you query say 8.8.8.8 directly
[23.05.1-RELEASE][admin@sg4860.local.lan]/root: dig controlplane.tailscale.com @8.8.8.8 ; <<>> DiG 9.18.13 <<>> controlplane.tailscale.com @8.8.8.8 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 30898 ;; flags: qr rd ra; QUERY: 1, ANSWER: 12, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;controlplane.tailscale.com. IN A ;; ANSWER SECTION: controlplane.tailscale.com. 21 IN A 3.78.132.46 controlplane.tailscale.com. 21 IN A 52.28.255.255 controlplane.tailscale.com. 21 IN A 3.73.239.57 controlplane.tailscale.com. 21 IN A 3.74.105.242 controlplane.tailscale.com. 21 IN A 18.159.140.118 controlplane.tailscale.com. 21 IN A 18.194.180.142 controlplane.tailscale.com. 21 IN A 3.124.108.117 controlplane.tailscale.com. 21 IN A 3.125.149.81 controlplane.tailscale.com. 21 IN A 35.156.244.91 controlplane.tailscale.com. 21 IN A 3.125.194.96 controlplane.tailscale.com. 21 IN A 3.69.76.60 controlplane.tailscale.com. 21 IN A 18.197.213.150 ;; Query time: 18 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) (UDP) ;; WHEN: Sat Aug 26 12:36:32 CDT 2023 ;; MSG SIZE rcvd: 247 [23.05.1-RELEASE][admin@sg4860.local.lan]/root: -
@johnpoz
I can reach those fqdn with traceroute on pfsense.My specific issue is when using tailscale as an exit node (on the pfsense router), when accessing the internet with my laptop i get 0Mbps download speed and a weird 5-7Mbps upload speed. Everytime i am unable to load a website tailscale is using a direct connection over ipv6. I have tried to block ipv6 to force tailscale to go over ipv4 but this just breaks the connection over the tailscale interface.
I have tested using tailscale on a ubuntu VM that is under the pfsense router as an exit node and got better results while blocking the ipv6 protocol.
My main confusion is why the tailscale package on pfsense doesn't seem to utilize ipv4 connectivity or DERP servers in the event ipv6 direct connections do not go through.