nat/firewall/ha not working
-
Ok, so what NAT rules do you have there? If they are over-matching traffic from the firewall itself and NATing to the CARP VIP then only the master node will be able to connect. Even then it can cause problems for some protocols. pkg functions would not normally be one of them but...
-
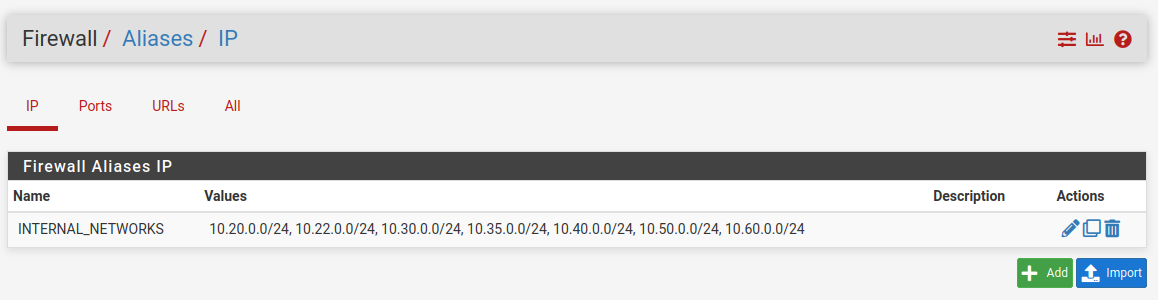
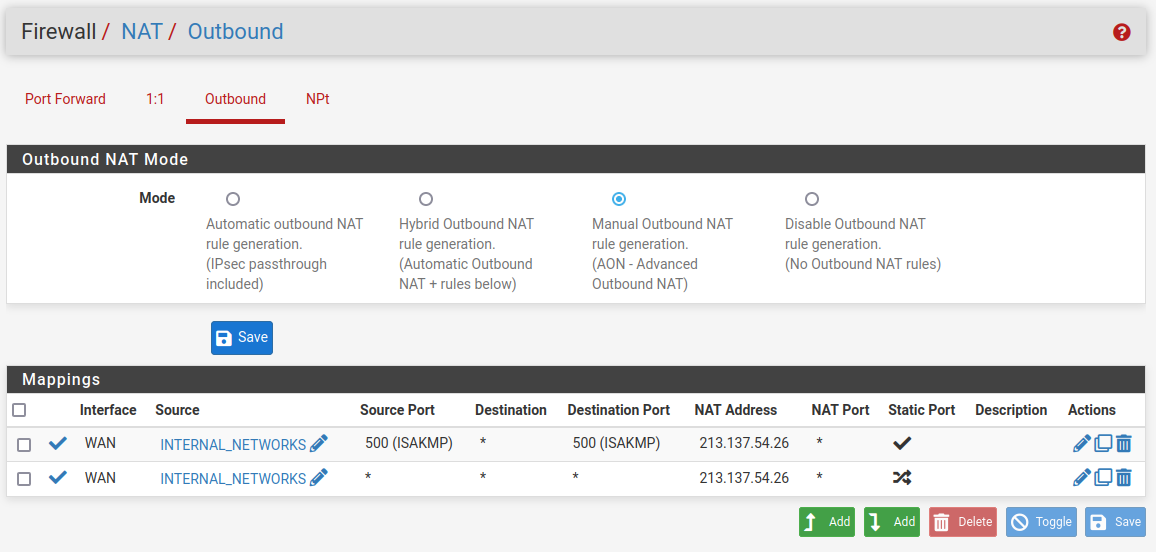
I NAT everything coming from any host port 500 (ISAKMP) to any destination port 500 (ISAKMP) with static port with the public IP (VIP), and then another rule NATting anything everything coming from any host any port to any destination any port with the public IP (VIP).
the public IP is a VIP of 10.10.0.1 (the CARP VIP), which is currently on firewall 1.
this is done because I have multiple IP addresses I route from the Cisco router to the firewalls via the CARP VIP, and would need to decide which IP address to use outbound for the specific NATted virtual machines. -
Ok, so your second rule there should not be source 'any' because that will include the firewall WAN IP which should not be NAT'd.
Either add NAT rules for each of your internal subnets as source or create an alias with that subnets in it and use that as the source in a single rule.
https://docs.netgate.com/pfsense/en/latest/recipes/high-availability.html#configure-outbound-nat-for-carpSteve
-
okay now I got a strange one at hands...
this be my alias configuration
this be my nat configuration (I verified, it got propagated to all three machines)
when trying to ping
1.1.1.1frompfsense01it works, when trying to ping from eitherpfsense02orpfsense03not only it doesn't work, trying to perform a packet capture from the same firewall it doesn't output anything, like if it doesn't even try (and of course it says I don't have network connectivity to register the firewall to pfSense+ or to update packages or whatever)...tried moving the CARP VIPs (all of them) to
pfsense02with - again - zero luck -
PS: fuck IPv4 - it doesn't work - IPv6 works fine just fine from all three machines pinging
google.com(tho only from the WAN interface, the other IP addresses are routed to the CARP VIP so I suppose it's normal it doesn't work) -
Hmm, I assume that IP you are NATing to is the CARP VIP?
On the primary node that works check the states created when it checks for updates. What source IP is it using? The CARP VIP?
We did see issues with the primary IP address on an interface moving to a VIP on it but that should be solved. Also I never saw it affect pkg operations.
-
@stephenw10 yes, but actually not really...
the configuration is like this:
10.10.0.1 is the CARP VIP of the interface
213.137.54.24/29 (to be exact 8 single /32 IPs) are virtual IPs based on the CARP VIPthis is done to more quickly move all the IPs following the CARP VIP and to minimize CARP traffic between the firewalls
@stephenw10 said in nat/firewall/ha not working:
On the primary node that works check the states created when it checks for updates
with three machines and that many interfaces there are too much states to go through to analyze
can you share the update servers' subnet? is208.123.73.212part of it? (if so, from the states it seems the source IP is10.10.0.2, the IP of the interface, so not NATted) -
Ah so the IPs from 213.137.54.24/29 are IPAliases that are on the 10.10.0.1 CARP VIP?
What is NATing the 10.10.0.X subnet then, some upstream router?
If there's nothing NATing that then the nodes would have to use IPs from the public /29 directly. But since those are on the CARP VIP only the master node can use it.
Why not use IPs from the /29 directly on the nodes?
-
 S stephenw10 referenced this topic on
S stephenw10 referenced this topic on
-
@stephenw10 said in nat/firewall/ha not working:
What is NATing the 10.10.0.X subnet then, some upstream router?
correct, the Cisco router
@stephenw10 said in nat/firewall/ha not working:
Why not use IPs from the /29 directly on the nodes?
a. to have all of them available
b. there will be no /29, I'm slowly migrating services to a single /32 -
Hmm, then there should be no problem with them using the primary IP in the 10.10.0X subnet as long as it' not the CARP VIP.
Do you not see states at all on the other nodes?