Redirecting DNS to local Adguard Home DNS server
-
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html
Is there a way to adapt this if your DNS is a local DNS server other than pfsense? I tried using the rule but it won't work because the reply packets from Adguard have a source IP of its IP address which is expected because the reply traffic does not go back to the router because they DNS server and the clients are on the same subnet, so asymmetrical routing is happening. Maybe create an outbound NAT rule for when the redirect happens so the source IP address of the forward packet gets changed to the LAN interface or something?
-
I tested the outbound NAT approach and it did work. The problem with that is that Adguard won't see the real source IP of the queries which defeats the purpose of me using it in the first place.
-
@kevindd992002 said in Redirecting DNS to local Adguard Home DNS server:
Is there a way to adapt this if your DNS is a local DNS server other than pfsense?
So, the rest of your message is difficult to understand but, what's lacked in pfSense DNS that you need this adguard home server?
Is pfSense configured for DNS or is this adguard? What do you have here: System > General Setup > DNS settings, see below...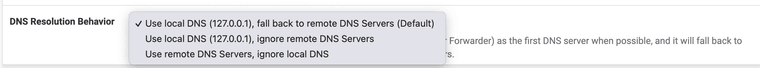
If you select remote and ignore local DNS...provide the IP of this adguard home server despite it's LAN IP, I believe it should work as it's not local to "pfSense."
-
@NollipfSense said in Redirecting DNS to local Adguard Home DNS server:
@kevindd992002 said in Redirecting DNS to local Adguard Home DNS server:
Is there a way to adapt this if your DNS is a local DNS server other than pfsense?
So, the rest of your message is difficult to understand but, what's lacked in pfSense DNS that you need this adguard home server?
Is pfSense configured for DNS or is this adguard? What do you have here: System > General Setup > DNS settings, see below...
If you select remote and ignore local DNS...provide the IP of this adguard home server despite it's LAN IP, I believe it should work as it's not local to "pfSense."
Sorry about that. I tried to explain as best I could. I want to separate DNS from pfsense. I've been using AGH for a while now. It has better monitoring than pfsense and it can do DOH. But that's a different topic altogether. I know people prefer pfblockerNG in pfsense for ad blocking or even pihole. I prefer AGH.
pfsense's unbound/DNS Resolver is configured for itself only. I have the default there:
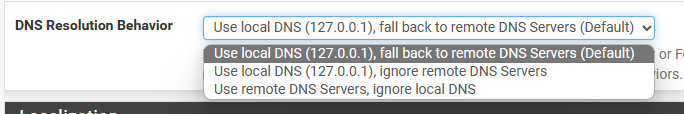
How would changing that work though? One of the LAN interfaces of pfsense is still local (same subnet) to that of the AGH server. Without some sort of SNAT/outbound NAT, the reply packet from the AGH server will be all layer 2 and will not be returned to pfsense, so no translating back of source IP for the reply packet (which is expected when the forward packet is DNAT'ted).
-
@kevindd992002 I think the dns-redirect rule should work with AGH for dns without a problem, but not for local DoT or Doh. You should not use those and block them.
-
@Bob-Dig said in Redirecting DNS to local Adguard Home DNS server:
@kevindd992002 I think the dns-redirect rule should work with AGH for dns without a problem, but not for local DoT or Doh. You should not use those and block them.
It doesn't though, for the reasons I stated above. Picture this:
- Client (192.168.10.x:{random source port}) tries to use 8.8.8.8:53 as a DNS server.
- The forward packet gets sent to the default gateway, which is pfsense.
- The forward packet (with destination socket of 8.8.8.8:53) gets DNAT'ted to 192.168.10.10:53 (my AGH server).
- The forward packet is received by the AGH server.
- AGH replies with a reply packet with these addresses:
- source: 192.168.10.10:53
- destination: 192.168.10.x:{the same random source port in #1)
- This reply packet is now all layer 2 since the source and destination are now on the same subnet, so it won't route back through pfsense.
- The client rejects this reply packet because the source IP IS DIFFERENT from the destination IP in the original forward packet that came from it.
This is somewhat similar to asymmetrical routing. The forward packets got DNAT'ted by pfsense but the reply packet did not route back to pfsense so there is no way for the source IP of the reply packet to be translated by pfsense to 8.8.8.8:53 so that the client won't reject the packet. I'm 100% sure this is what's causing the timeouts because I've already tested it. Creating an SNAT rule so the source IP of the forward packet (after being DNAT'ted) gets translated by pfsense to the interface IP fixes this problem but with the downside of having all forward packets having the same source IP (pfsense interface IP) as seen by AGH.
@NollipfSense I hope this explains my original post better.
-
@kevindd992002 What happens if you put your AGH in a different (V)LAN?
-
@Bob-Dig it works without any issues, as expected. I have clients in other VLANs that access the AGH server in VLAN 10 (192.168.10.0/24). Since these clients are on another VLAN, the reply packets from AGH go back the correct route (pfsense) and the translation happens properly.
-
@kevindd992002 said in Redirecting DNS to local Adguard Home DNS server:
I hope this explains my original post better.
Yes, I understand your objective and seems you found a solution using vLAN...
-
@NollipfSense nope, I haven't really found a solution yet. I did not create a new VLAN just for my AGH server. I have multiple VLANs and the clients in all those VLANs are pointed to the AGH server in VLAN 10 as their DNS server. The clients that are affected are the VLAN 10 clients. The clients in other VLANs work fine.
-
@kevindd992002 Maybe you can find some useful information here:
https://forum.netgate.com/topic/182369/pi-hole/20?page=1 -
@MoonKnight perfect! The discussion there is exactly what I needed. I'll reply there.
-
@kevindd992002 said in Redirecting DNS to local Adguard Home DNS server:
I did not create a new VLAN just for my AGH server.
Why not, where is the problem? If you want dns-redirect everywhere, you have to.
-
@Bob-Dig right, what I mean is I didn't really create a new VLAN now. I just happen to have other VLANs when you had me test that idea earlier. But yes, I will be revamping my home lab setup pretty soon anyway. I will create a separate server and client VLANs and put the AGH server in the server VLAN. I won't need to create a redirect for the server VLAN anyway since servers don't really use "any other DNS" and respect what's configured in their settings. I guess this is the best solution overall.