Snort Alert Disable NAT
-
I can't seem to figure out how to configure snort to not show the outside natted interface in the alerts. Let me explain what I have setup, and excuse the explanations as I try to answer questions that people are probably wanting to ask....
-
Every subnet on my network is behind a Fortigate firewall (I'm very comfortable with the FortiOS and it's super easy to manage via the GUI, CLI, and API). I've got several automation scripts in place to handle traffic. For example I have a Camera/IoT network....it's much easier to launch an Android MacroDroid shortcut on my phone to disable a policy on my Fortigate that disables Internet access for the Cameras while I cut grass, so I don't get 100 notifications. Also the Fortinet SSLVPN is super easy to configure (does contain a vulnerability but I'll touch on this in a bit). A used Fortigate 60e on eBay is around $150 so its pretty inexpensive compared to what you get.
-
The Fortigate is sitting behind the Netgate running pfSense. The gap that pfSense fills is the free IDS/IPS and GeoIP Blocking. This type of service can be thousands of dollars per year on the Fortigate so it's much cheaper to use pfSense for this since it's free.
-
In front of the pfSense is an OpenWRT router. The only reason why this is at the border is simply because it's able to do single packet inspection using the package Fwknop. Like I said earlier the Fortigate SSLVPN does contain a vulnerability; in-fact, there are always some new vulnerability that's being discovered in Fortigate appliances. It's wise not to explicitly open up service ports to the Internet, so I do single packet inspection to the edge that then dynamically does a port forward via a NAT and firewall rule.
Here is the problem.....as traffic leaves the Fortigate out to the internet, I'm not doing an outbound nat. This means the LAN side of the pfSense sees the real subnet addresses; however, when it leaves the pfSense, it does an outbound nat, which is what I want it to do, but in the alert logs, I don't want to see the natted ip.
How can I configure Snort not to show me the WAN natted ip? I still want to do this IPS on the WAN interface.
-
-
You can't. Snort sits between the physical NIC and the kernel network stack before the firewall engine. So, when you run Snort (or Suricata for that matter) on the WAN, it only sees local traffic after NAT has been applied for outbound traffic, and before NAT is undone for inbound traffic. Here are two diagrams that show how the IDS/IPS packages are plumbed into the network. This is an operating system thing and not anything the packages can alter.
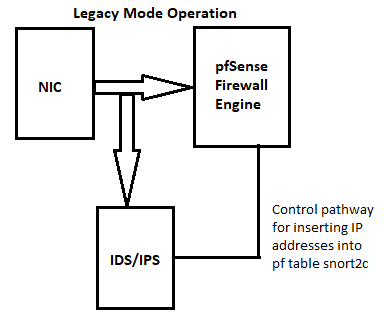
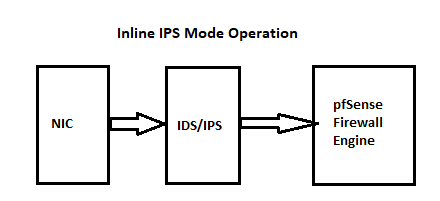
This is why I have been recommending for the last few years that users put the IDS/IPS on internal interfaces. You should do the same. There is no point in having it on the WAN. IDS/IPS is not for protecting the firewall. It's for protecting the hosts behind the firewall. If you need IDS/IPS for your firewall itself, then you really need a new firewall
 .
.Running it on the LAN would eliminate your issue of NAT hiding local IP addresses. When running on the LAN, all traffic going to or coming from local hosts would have to pass through the IDS/IPS.
And one last note. Without MITM breaking of encryption, IDS/IPS on the firewall is severely limited in what it can accomplish these days because nearly 100% of network traffic is encrypted. The IDS/IPS can't peer into any of the payloads for SSL traffic. That means zero payload inspection of HTTPS, DoT, DoH, SMTPS, IMAPS, and POP3S for starters. That's nearly all of the web traffic, potentially all of the DNS traffic (if you use DoT), and pretty much all email traffic bypassing inspection. Intrusion Detection is rapidly becoming something best done on the local destination host itself and not on intermediate network devices.