freeradius3 - mschap: FAILED: No NT-Password
-
Saw the link in the recent news letter to the article about setting up 2FA via freeradius... I get the following error when attempting to connect an actual wifi client (Unifi AP):
Login incorrect (mschap: FAILED: No NT-Password. Cannot perform authentication): [iphone] (from client AP port 0 via TLS tunnel)My freeradius setup authenticates non-2FA users.
- I can successfully authenticate using 2FA via the Diagnostic > Authentication only
- I've read this thread, applied changes but no effect.
- I tried re-installing the package, but the existing settings weren't purged as part of the operation - would appreciate help for how to be able to start from scratch.
Pertinent:
- freeradius3: 0.15.10
- pfsense: 23.05.1-RELEASE (amd64)
-
Hmm, what exactly are you trying to log into there?
It works as expected in the local auth test?
-
iphone > Unifi AP > pfense/freeradius
stephenw10 said in freeradius3 - mschap: FAILED: No NT-Password:
It works as expected in the local auth test?
Yes, I believe that's what my first bullet states
-
@vLANity said in freeradius3 - mschap: FAILED: No NT-Password:
Yes, I believe that's what my first bullet states
Ah, so it does!

Ok, so you are using this for 802.1x auth to the access point rather than OpenVPN as shown in the article? Did you try using it for OpenVPN?
Yeah reading through that other thread it sure seems the same. You are running a newer pfSense version. I wonder if the those older EAP types were deprecated.
Do you see the same failure from any client type?
-
@stephenw10 said in freeradius3 - mschap: FAILED: No NT-Password:
...you are using this for 802.1x auth to the access point rather than OpenVPN as shown in the article? Did you try using it for OpenVPN?
Correct; I have no need for OpenVPN at this time.
Yeah reading through that other thread it sure seems the same. You are running a newer pfSense version. I wonder if the those older EAP types were deprecated.
True; my concern is that my freeradius setup has seen so many alterations which may have rendered the fix in the reference thread useless. Hence why I was asking how to purge in order to setup from stock (as demonstrated in the original article)...
Do you see the same failure from any client type?
I tried various types, various combinations. I'm unclear on what you mean by "client", the terminology is overused so wanna make sure I know you're referring to the freeradius client vs iphone/etc. I haven't tested with tablet, but anticipate same as iphone.
-
Sorry I meant Windows, MacOS, Linux, iOS etc. The other user reported Windows failed entirely whereas MacOS eventually succeeded. Implying it tried more EAP types and eventually tried one that worked. Also that it started out with the least secure types....
-
Only iOS clients to date, using what I understand to be the various insecure EAP types. Which again, I suspect there could be an issue with a legacy configuration change I've made that I'm unaware of that is impacting testing...
No plans for Win/Mac/Android.
-
It would be a good test though since we know it worked after some tries in MacOS in earlier versions.
-
Can not test what I do not have
-
@vLANity Here is what mine is set to no issues connecting IOS devices:-
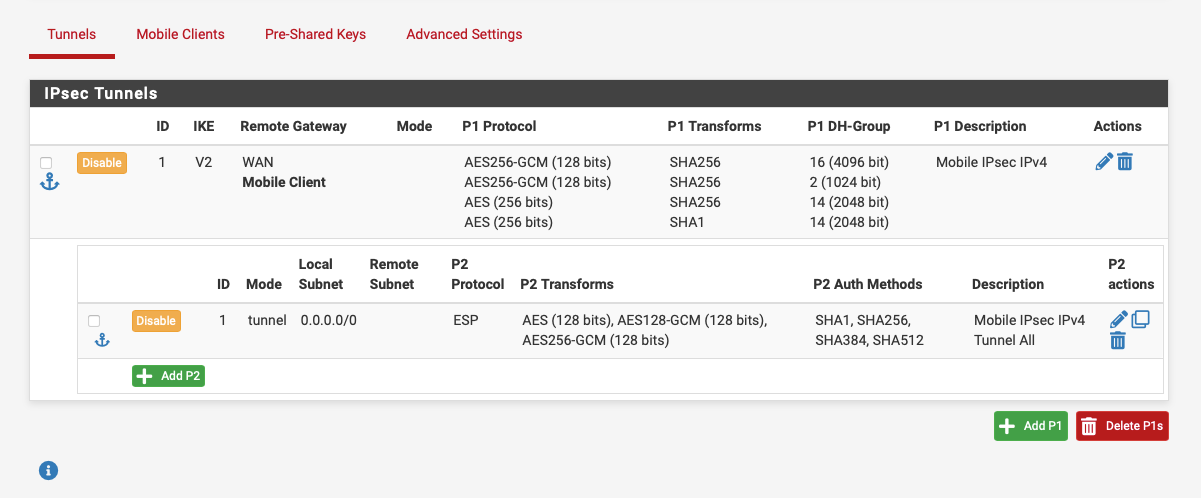
It also works fine with my Mac Pro, but that's at home so kinda pointless :)
-
@NogBadTheBad Thanks? I added IPsec as was previously not using...
Still - no change re: original issue:
- iOS device over wifi (Unifi AP) using 2FA: can NOT authenticate
- Diagnostic > Authentication: The same user authenticates using 2FA
- Log reports as listed in thread title