ISP change and now pfsense unable to resolve DNS names
-
I have my ISP router and PFsense firewall communicate over the 192.168.110.0/24 network and i have a local Lan of 192.168.0.1/24 with the pfsense firewall having the ip of 192.168.0.1 on the lan and 192.168.110.1 on the wan.
I changed ISP and setup the new ISPs router to 192.168.110.2 and all works as expected on some devices but i was unable to access the internet from other devices. I found the issue was that any device not using with google DNS server set as static were unable to resolve domain names. Most devices on my network use DHCP and are given the pfsense as DNS server as that will filter out adverts with pfblockerng and allow local lookups. I restarted unbound and pfblockerng on the pfsense but issue still remains I also restarted the pfsense server and the issue still remains.
I changed the DHCP setting in pfsense to use googles DNS but this means I am not no longer able to resolve local DNS names and see ads everywhere.
Nothing was changed on the pfsense side so I have no idea what could be the cause or even how to debug this and never had the issue before when i changed ISP or router.
I am still able to resolve local names with pfsense just not remote domains.
Pfsense info:
2.7.0-RELEASE (amd64)
built on Wed Jun 28 03:53:34 UTC 2023
FreeBSD 14.0-CURRENTThe system is on the latest version.
Version information updated at Fri Sep 8 8:16:09 UTC 2023Doing a DNS lookup on the pfsense i can see i get a fail from the local host but it is able to resolve domains using google DNS. From the main pfsense page i can see the dns servers listed are:
127.0.0.1
8.8.8.8
8.8.4.4I assume the localhost address is normal to be there.
Anyone have any idea where to even start to figure out where the issue is.
Appreciate any help or advise
-
I figured it out on the ISP router when i go into export mode there is a secure DNS option if i disable this all works as expected again
-
Still, this is pretty strange ( imho : alarming ) :
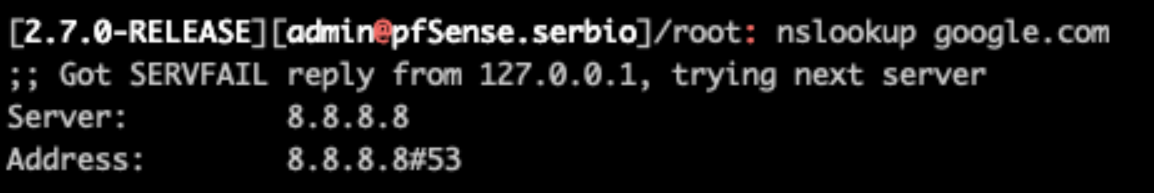
On your pfSense, no one answers on 127.0.0.1, that's not 'normal' at all.
You told pfSense that these are there :
@swansense said in ISP change and now pfsense unable to resolve DNS names:
Doing a DNS lookup on the pfsense i can see i get a fail from the local host but it is able to resolve domains using google DNS. From the main pfsense page i can see the dns servers listed are:
127.0.0.1
8.8.8.8
8.8.4.4is unbound running ?
While you are at the command line :
ps ax | grep 'unbound'and
sockstat | grep '53'will tell you what you need to know.
These : 8.8.8.8 and 8.8.4.4 are not needed, except if you want to forward to them / have to hand them over your DNS traffic.
@swansense said in ISP change and now pfsense unable to resolve DNS names:
on the ISP router when i go into export mode there is a secure DNS option
This router can do what it has to do. By default, pfSense isn't using it's DNS facilities anyway.
It does its own DNSSEC ( as long as you, again, are not forwarding)if possible.The Netgate default pfSense DNS settings work out of the box. No need to add or modify anything.
-
@Gertjan said in ISP change and now pfsense unable to resolve DNS names:
Still, this is pretty strange ( imho : alarming ) :

On your pfSense, no one answers on 127.0.0.1, that's not 'normal' at all.
You told pfSense that these are there :
@swansense said in ISP change and now pfsense unable to resolve DNS names:
Doing a DNS lookup on the pfsense i can see i get a fail from the local host but it is able to resolve domains using google DNS. From the main pfsense page i can see the dns servers listed are:
127.0.0.1
8.8.8.8
8.8.4.4is unbound running ?
While you are at the command line :
ps ax | grep 'unbound'and
sockstat | grep '53'will tell you what you need to know.
These : 8.8.8.8 and 8.8.4.4 are not needed, except if you want to forward to them / have to hand them over your DNS traffic.
@swansense said in ISP change and now pfsense unable to resolve DNS names:
on the ISP router when i go into export mode there is a secure DNS option
This router can do what it has to do. By default, pfSense isn't using it's DNS facilities anyway.
It does its own DNSSEC ( as long as you, again, are not forwarding)if possible.The Netgate default pfSense DNS settings work out of the box. No need to add or modify anything.
so i shouldnt have google DNS servers added in pfsense? I have pfsense set up to resolve not forward.
-
It's time you know what "resolving" is ;)
For example (hundreds of good video's exist) : How DNS Works - Computerphile.
It all starts with the famous "13" : Root name server - these are always there, have a known UPv4 and Ipv6.
For example, when unbound starts, it has the 13(+13) IP addresses build in.When you wanted to know : what is the IP(v4) address of "www.youtube.com" unbound start to send a request to one of (the fastest) root server with this question : "give me an address of a TLD DNS server, the one that handles dot com (.com)". Many exist, so the root server will give you one.
Unbound obtained the addresses of this dot com DNS server (which only knows about dot com domains).
It will ask : "do you have the list of domain name servers" of "youtube.com". "The list", because there are always at least two of them, sometimes far more.
To one of these domain name server, unbound will ask : do you have the A (IPv4) (or AAAA if IPv6) of "www.youtube.com".
(Youtube's) domain name server will hand over the IP.
unbound now will hand over this IP to the device (your PC on the LAN, the one that asked for "www.youtube.com".
It will also keep this answer in it's local DNS cache, so an answer can be given right away without doing the entire process mentioned above.
Nice side effects : the a address of the TLD that can resolve dot com addresses is also kept, so the next time www.google.com is needed, no need to go to a root server again : unbound can question the TLD direcly, as it has kept the IP also.
Same thing for the domain name servers : you want an A record (Ipv4 address) and then the MX ? and then the AAAA ? unbond has already the domain name server's address of that host name.Now, the PC, for example a browser, can connect to the IP.
This is what "DNS" is.
Nothing less, nothing more.Now consider, for example : 8.8.8.8. 8.8.8.8 is a resolver like unbound ( !! ) so it does the same work as what unbound does. when you forward with unbound will delegate the resolving task to 8.8.8.8, and wait until it gets answer back.
I leave it up to you to understand why you would this to happen like this.
When you install pfSEnse, there is no "8.8.8.8" or "1.1.1.1" setting anywhere.
Know you know why : it isn't needed. If it was, Netgate would have set these right "out of the box". -
thank you
Was not aware that pfsense had root servers IPs built in and did not need DNS servers like google setup. -
@swansense said in ISP change and now pfsense unable to resolve DNS names:
Was not aware that pfsense had root servers
Not pfSense.
Any of these ( Having a Yes in the Recursive column ) https://en.wikipedia.org/wiki/Comparison_of_DNS_server_software are resolvers.
For most OSs these are just application of packages you include / install and use.
The most known is 'bind'.
The better ones do also DNSSEC.

