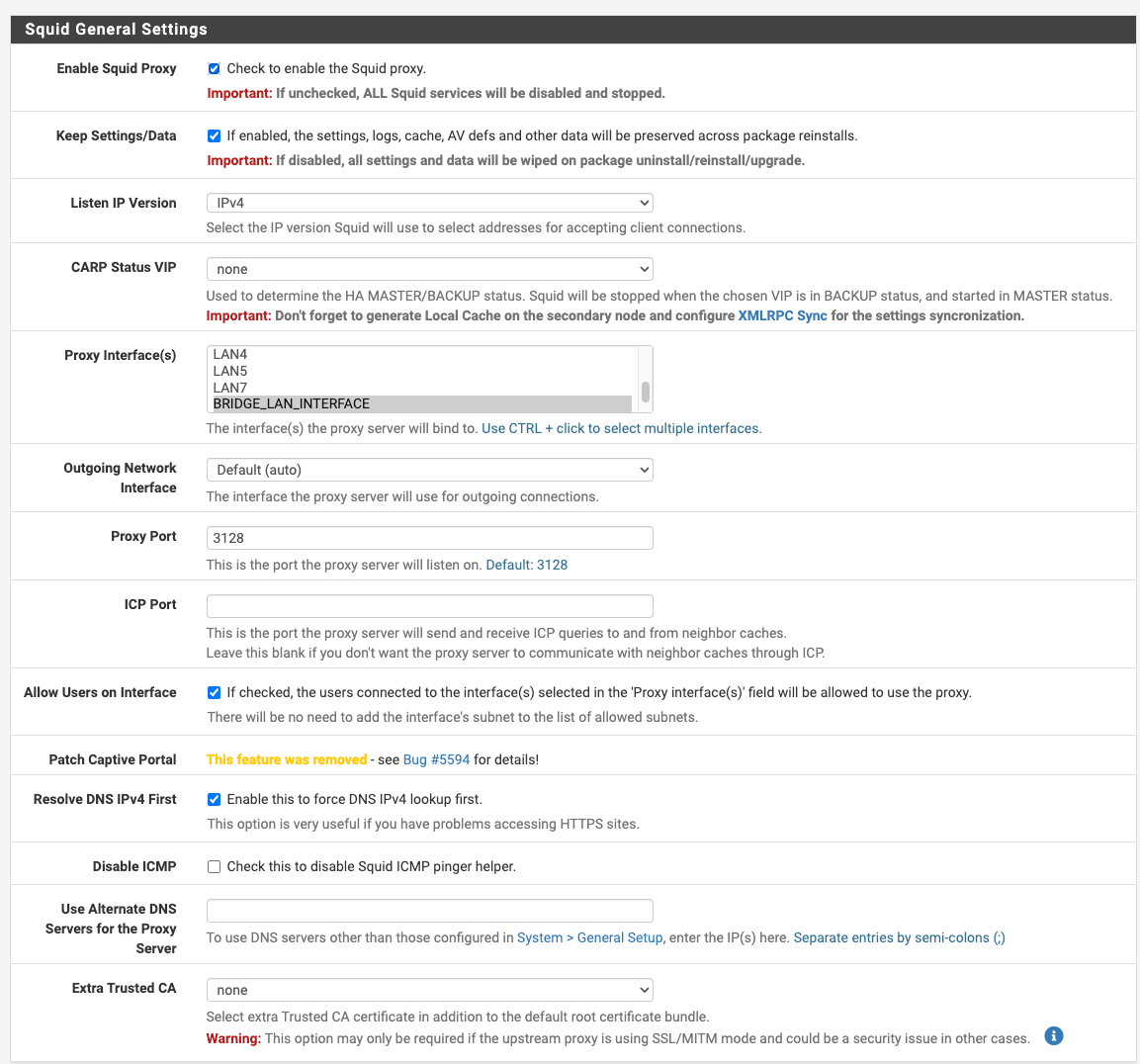
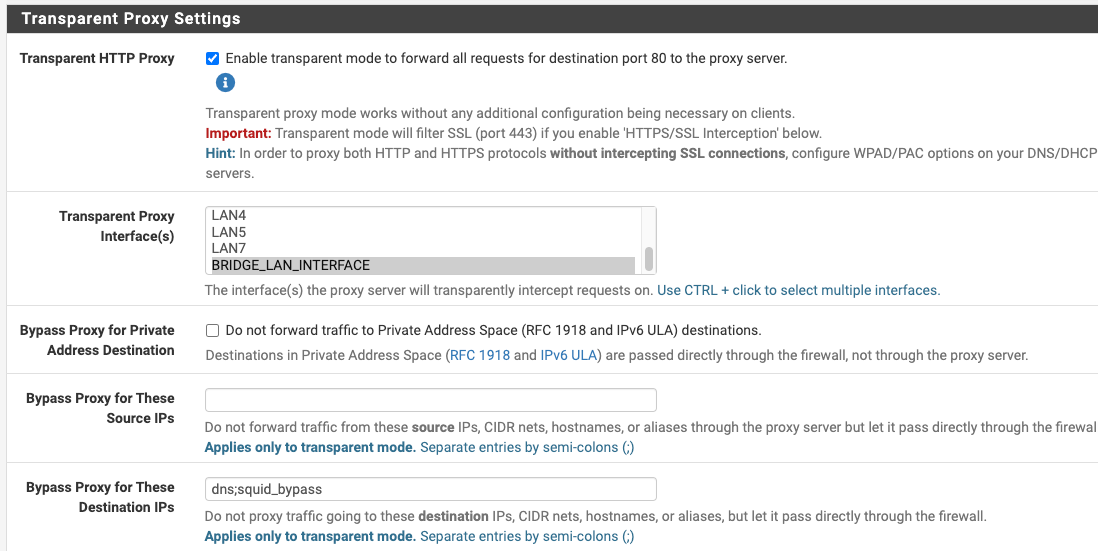
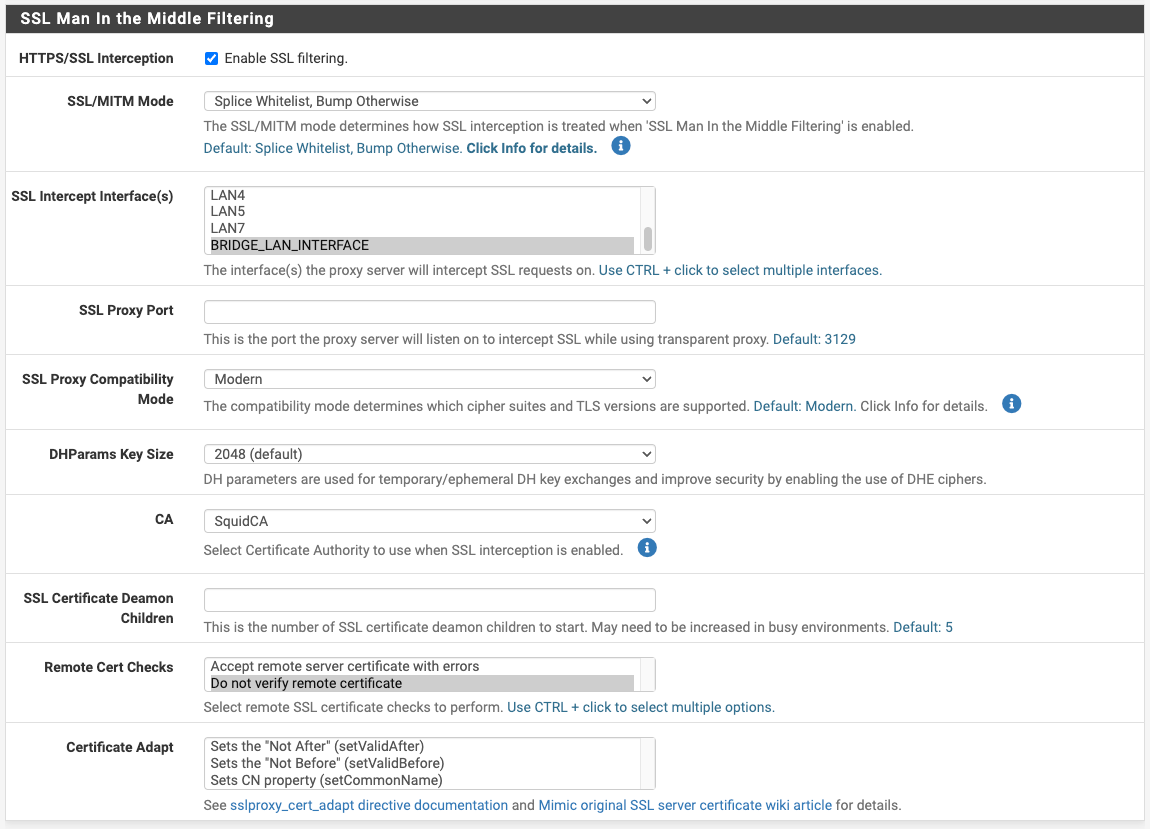
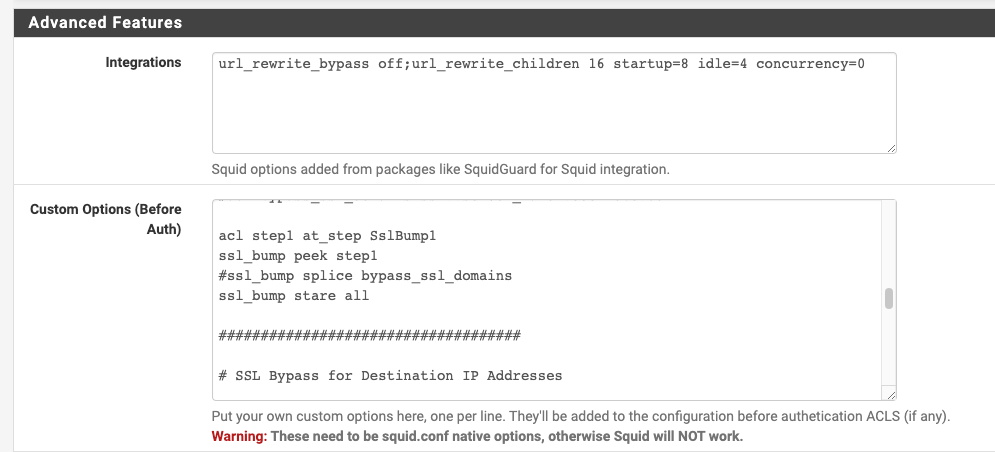
Squid Proxy "Bypass Proxy for These Destination IPs" Not Working?? Transparent HTTP Proxy Mode + HTTPS/SSL Interception
-
@dkzsys if you use Squid or Squidguard you can utilize regular expressions.
Some examples from my always splice file:
^((alt[0-9]-mtalk.)|(mtalk.)|(mtalk-(staging|dev).))google.com
^(((clients)[0-9])|accounts).google.(com|us)
^.*(outlook.)(office365|office).com
^(disney.(content|connections)).edge.bamgrid.com
Test and create them with a regular expressions tester online if needed.
-
@JonathanLee my understanding is that for the regex domain to work, squid will need to be set to explicit mode, or transparent mode with peek and splice config; and it doesn't work for transparent mode with Splice All. Happy to be corrected.
-
@dkzsys it should work if the domains are using .something else in it. Yes that is mostly used with SSL intercept
-
@dkzsys said in Squid Proxy "Bypass Proxy for These Destination IPs" Not Working?? Transparent HTTP Proxy Mode + HTTPS/SSL Interception:
- FW Blocking to WAN is no longer 100% effective, to the FQDNs on and off the source bypass list. For example, blocked clients can still search on google.com, play chess on chess.com, etc. See screenshot for the fw block rule below. I will have to reset fw states to block all outgoing traffic to WAN from those clients. @periko - can I get your input on this pls - any other options to effectively block client to WAN without fw state reset?
I just found out that I can use "pfctl -k" to reset fw sessions for specific client IPs via terminal. Since I am using CLI to toggle the blocking rules, it actually worked out well for me as a workaround - simply adding the extra command in the block rule CLI snippet.
-
@dkzsys said in Squid Proxy "Bypass Proxy for These Destination IPs" Not Working?? Transparent HTTP Proxy Mode + HTTPS/SSL Interception:
I just found out that I can use "pfctl -k" to reset fw sessions for specific client IPs via terminal. Since I am using CLI to toggle the blocking rules, it actually worked out well for me as a workaround - simply adding the extra command in the block rule CLI snippet.
Unfortunately killing the state for the client still doesn't block their traffic to WAN with the block rule enabled... Looking for an alternative workaround.
-
@dkzsys try this
client_persistent_connections on
client_persistent_connections off"Squid uses persistent connections (when allowed). You can use
this option to disable persistent connections with clients."http://www.squid-cache.org/Doc/config/client_persistent_connections/