cURL vulnerability 2023
-
Hi,
maybe you already know but if not, there is probably a severe vulnerability in cURL. Details here:
Nice Sunday,
fireodo -
By the way, on curl.se site, reporting detailed information about the vulnerability, the recommendations to solve the vulnerability are:
A - Upgrade curl to version 8.4.0
B - Apply the patch to your local version
C - Do not use CURLPROXY_SOCKS5_HOSTNAME proxies with curl
D - Do not set a proxy environment variable to socks5h://It seems that points C and D are the default settings in pfSense, thereby the vulnerability may not affect pfSense.
Could somebody confirm or negate, please?
-
@Odette said in cURL vulnerability 2023:
By the way, on curl.se site, reporting detailed information about the vulnerability, the recommendations to solve the vulnerability are:
A - Upgrade curl to version 8.4.0This is the version in 23.09
B - Apply the patch to your local version
Not relevant
C - Do not use CURLPROXY_SOCKS5_HOSTNAME proxies with curl
D - Do not set a proxy environment variable to socks5h://It seems that points C and D are the default settings in pfSense, thereby the vulnerability may not affect pfSense.
Could somebody confirm or negate, please?
You are correct, nothing on pfSense (Plus or CE) sets any sort of
SOCKS5value with cURL. We do set a proxy configuration when one is configured for upstream (System > Advanced, Misc tab) but it is notSOCKS5. -
Thank you @jimp for your appreciate and risolutive replay.
Just a question: what doesThis is the version in 23.09
mean?
Here is the output of curl -V on a standard 2.7.0 release of psSense CE:
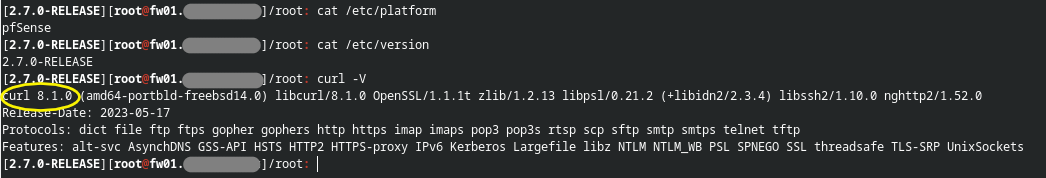
The output shows curl version is 8.1.0.
Just my curiosity
-
2.7.0 is older, it wouldn't have it there. But as the other points mentioned, it's not a concern.
[23.09-RELEASE][root@ruby.lab.jimp.pw]/root: cat /etc/version 23.09-RELEASE [23.09-RELEASE][root@ruby.lab.jimp.pw]/root: curl -V curl 8.4.0 (amd64-portbld-freebsd14.0) libcurl/8.4.0 OpenSSL/3.0.12 zlib/1.2.13 libpsl/0.21.2 (+libidn2/2.3.4) libssh2/1.11.0 nghttp2/1.55.1 Release-Date: 2023-10-11 Protocols: dict file ftp ftps gopher gophers http https imap imaps pop3 pop3s rtsp scp sftp smtp smtps telnet tftp Features: alt-svc AsynchDNS GSS-API HSTS HTTP2 HTTPS-proxy IPv6 Kerberos Largefile libz NTLM NTLM_WB PSL SPNEGO SSL threadsafe TLS-SRP UnixSocketsThere is a CE 2.7.1 release coming that has cURL 8.4.0 as well, there should be RC images to test soon (maybe even today).
-
Confirmed: fixed in 2.7.1
[2.7.1-RELEASE][root@xxx.yyy.zzz]/root: cat /etc/version 2.7.1-RELEASE [2.7.1-RELEASE][root@xxx.yyy.zzz]/root: curl -V curl 8.4.0 (amd64-portbld-freebsd14.0) libcurl/8.4.0 OpenSSL/3.0.12 zlib/1.2.13 libpsl/0.21.2 (+libidn2/2.3.4) libssh2/1.11.0 nghttp2/1.57.0 Release-Date: 2023-10-11 Protocols: dict file ftp ftps gopher gophers http https imap imaps pop3 pop3s rtsp scp sftp smtp smtps telnet tftp Features: alt-svc AsynchDNS GSS-API HSTS HTTP2 HTTPS-proxy IPv6 Kerberos Largefile libz NTLM NTLM_WB PSL SPNEGO SSL threadsafe TLS-SRP UnixSockets -
@fireodo my son's Nintendo switch was running cURL all day on the network, I had to move it to it's own lan away from everything