How to create an alias with my /56 DHCPv6-PD from ISP
-
Hi there,
So it's a simple enough question, is there a way to create an alias that will dynamically adjust to whatever my ISP assigns as prefix delegation?
And as a secondary related question, is there a way to create an alias that will combine multiple VLAN IPv6 subnets?
To explain a bit, I have 5 VLANs that track the interface of my WAN where my ISP gives me a /56 prefix. That prefix changes at every interface reset of any kind.
Those VLANs are:
- MAIN
- IoT
- Guest
- VPN
- Homelab
I want to create a firewall rule that blocks access from my IoT VLAN to all other VLANs. For IPv4 this is simple as you can create an alias with all the IPv4 subnets and just create a single rule to inverse match that alias.
But what about IPv6? So far I can only do one block rule per network, and do 3 rules like this. At the moment things look like this:
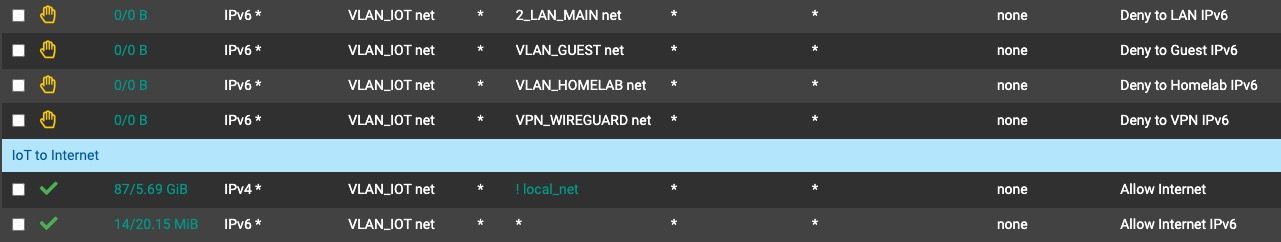
Is there a way to cleanup the IPv6 rules to look like the IPv4 one?
-
@IonutIT To answer the second part of your question: If you had an alias for all of the individual LAN networks, you could create an aggregate alias. pfSense allows nesting aliases.
However, the problem is indeed to get the dynamic aliases in the first place. I've ran into this problem myself and resorted to assigning both GUAs (tracked) for Internet access and ULAs (static) for local access.
-
Well that's disappointing. I kind of thought that the answer is "can't be done", but I just hoped someone just had a workaround somehow. I won't switch to ULA + NPt because that will make IPv6 basically useless as most devices will always prefer IPv4 over ULA IPv6.
Don't want to be rude or anything, but OPNsense had the ability to create network group aliases for interface networks for a long long time. Such a share this doesn't work in pfSense yet...
-
@IonutIT Frequent prefix changes is an unfavourable situation to begin with. Operating systems preferring IPv4 over IPv6 is also very annoying for local networks.
My go-to option nowadays is to use ULAs and GUAs simultaneously, which is thankfully well supported by IPv6.
-
But how are you doing firewall then? All rules will only apply to ULA and IPv4. Nothing will apply to GUA ranges.
-
@IonutIT said in How to create an alias with my /56 DHCPv6-PD from ISP:
I kind of thought that the answer is "can't be done", but I just hoped someone just had a workaround somehow.
I think, it can't be done. One thing you could try is creating an IPv6 rule, negating ULA traffic for now and defining the WAN gateway in there. Now every GUA-traffic is forced out to your WAN.
For the inner workings you could use ULAs and create ip-blocks to your liking.But it is not worth it. If your GUA prefix isn't static, use IPv6 as much as necessary and as little as possible.
-
@IonutIT Sorry for the long wait. I wanted to have something to report, so I've done a little experimenting these last few days. On another forum I often remind people to be careful with
*destination because that also includes other local networks which is usually not intended when they just want to allow internet access. I'm a bit embarrassed to admit that I've fallen into a similar trap myself with regards to IPv6.My baseline was this: I have an alias "Local_Networks" that includes the RFC1918 private IPv4 addresses as well as
fc00::/7. To allow internet access in a network, I would create a rule that with the inverse of the alias as the destination. But, as I realized thinking about your question, this also enables access to any local IPv6 endpoints that have a GUA, which is decidedly not intended! So I looked for a way to block connections to GUAs exiting any local networks. With a bit of trial and error and some inspiration from this Reddit post, I arrived at a solution that works for now:It requires two floating rules. The first one matches any IPv6 protocol exiting the WAN interface(s) with a destination of
2000::/3and tags it. The second one blocks any IPv6 traffic exiting any interface which does not have the tag assigned.This configuration has the desired effect of blocking any local connections to GUA endpoints while still allowing internet traffic with the mechanism described above. You don't have to worry about prefix changes or newly added interfaces other than WANs. However, a drawback of this solution is that now you also cannot explicitly allow local traffic to GUAs with interface rules even if you wanted to. Even with a
*-destination rule in one network I couldn't connect to a host in another network using its GUA. This is despite the floating rule not being quick, mind you. I will investigate this further and try to come up with a solution that fixes this flaw. But if you don't need this "feature", I think this setup is a good starting point. -
I'm just starting with IPV6 myself (my ISP enabled it about a week ago) but I think that the base need of a FW rule might be doable.
pfSense do support dynamic prefixes according to https://redmine.pfsense.org/issues/6626
If you add an inverted pass rule for IPv6 and the network ::0/56 for your IoT net I think it should allow anything outbound and deny everything going tp your /56 -
I was really excited by your comment and went and created an alias that points to ::/56 then created an inverted pass rule for this alias. Unfortunately it seemed that I could still access my other networks via IPv6, so something was weird.
But then I've switched from using the alias "::/56" to actually defining the network ::/56 in the firewall rule and it magically started working. So it seems that you're right you can block by using this.
Thank you, this has been very useful!