Unable to get internet access from ISP modem
-
Hello,
I am new to Pfsense and need to know how to configure the Wan port on the router in order to communicate with the Comcast modem and provide internet access to the devices behind the firewall?
My current set up is as follows:
Lan port is on the 192.168.1.x and that is working great. PfSense DHCP and DNS resolver are enabled
Wan port was initially set up to default DHCPWhen that did not work on the Wan side, I changed the Wan configuration to a static public ip provided by the ISP. The IP has a totally different subnet.
DHCP, DNS and NAT are disabled on the Comcast modem.
The only interface I can access via web browser is the PfSense interface.
What do I need to do to get devices behind the pfsense internet access? My site is totally down now.
Thank you. -
@ama if its just a modem and not a gateway then you need to reboot it when you change out your old router with the new router. And it would be dhcp. Every single cable modem I have ever seen requires a power cycle when you change the device connected to it. Unless your doing a mac address clone on the new device your connecting to it.
If its a gateway, ie modem/router combo you would need to make sure its not the same network as your lan. For example if you have 192.168.1.x on both your wan and and your lan on pfsense - its not going to work too good ;)
-
@johnpoz Good morning,
Thank you for replying. Yes I understand that part. I connected a laptop directly to the comcast modem and used one of their provided static addresses. I was able to ping the gateway and get out to the internet. that ruled out issues with the ISP modem. I had the wan port and gateway set to the static Ips provided by comcast and that still did not allow the devices behind the firewall to reach the internet. Is there a default firewall rule that is preventing Lan devices from access to the internet through the firewall? If yes, does it not need to be removed or edited? -
@ama no out of the box pfsense lan rule is any any.. And would nat any traffic coming from your lan to whatever pfsense wan IP is..
So unless you modified this rule, or not using the default lan - new interfaces you create would have no rules on them.. Or messed with the automatic outbound nat. Pfsense should just work out of the box, as long as pfsense gets/has a valid IP on its wan that can talk to the internet, and doesn't overlap with the network you have on your lan interface of pfsense.
-
@johnpoz
Nope! did not mess with any rules. All is at default.
Wan is set to Static provided by ISP
Lan is set to private IP
I was unable to ping the gateway or any other site using the ping option. I browsed how to use PfSense ping and the first link pointed out needing to allow Ping on the firewall.
Added Firewall rule to allow ICMP ping on the PfSense router and that was the way out to the internet. I am back in Business. Is there a security concern with such a rule?
RFC 1918 is blocked and BOGON as well on the WAN rules. -
@ama said in Unable to get internet access from ISP modem:
first link pointed out needing to allow Ping on the firewall.
Out of the box pfsense would be able to ping anything outbound, there is no rule needed.. Now if your isp required the device to answer a ping coming into its wan before it would allow you to access the internet.. Then yes you would have to allow ping to the wan.. But this seems like an odd requirement..
Maybe your isp does not allow static IPs unless they answer ping?
Out of the box any traffic sourced from pfsense itself is allowed. Out of the box anything on the lan network is allowed.. You should for example be able to ping 8.8.8.8 out of the box with no rules needed to be added or allowed.
What specific rule did you create or edit?
As to allowing ping into your wan... I allow it.. Because I like monitoring I run from the public internet to check to see if it can get to my IP.. And if not alert me that my internet connection is down.
If your concerned with allowing ping into your wan - then limit it to the source IP or IPs that would be pinging you from your isp..
Here is my ping rule on wan
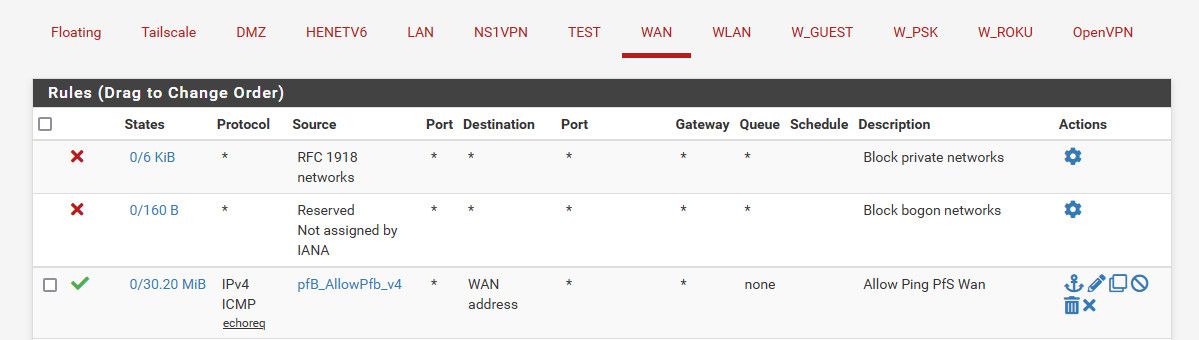
I limit it to specific IPs, US IPs are allowed, some lists of where other pings I want to allow might come from - status cake, uptime robot, etc. And its limited to only echo req, and not all icmp..
I use pfblocker to create the alias of geo Ips, and other lists that I allow.
-
@johnpoz
That would be my assumption too. This is an inherited situation and i am only discussing the tail end of it here. It was an out of the box router, installed Pfsense on then add tailscale for VPN access.
no rules modified at that time. when it was put on the network nothing would let up out until I added the ICMP rule to the firewall. The current rule is for IPV4 family, protocol ICMP (Echo Request), Source= any, destination= this firewall, -
@ama this firewall prob isn't a very explicit choice.. Wan address would be normally what you would use on your "wan" the "this firewall" is ALL ips on the firewall.. That is something you would normally use on a lan side interface where you want to block access to any pfsense IP after you have allowed what you want, normally before your any any rule on the bottom that allows internet.. This keeps say users on some network from accessing your web gui via the pfsense wan IP, etc.
As you move forward and tweaking your rules for your specific needs and wants. You might want to lock down the icmp rules to more limited space other than the "planet" ;) While sure you might want your isp to ping you.. Do you really want/need some IP in RU or China pinging your wan? I mean prob not a big security issue - but as you start to lock down stuff, why allow something you would never need..
-
@johnpoz
agreed!
The problem right now is losing the internet access if i disable this rule on the Wan. I am ways away from getting to know how the rule apply on PfSense. Just getting back online is the first step right now. Thank you for your support John!
I will let you know once I have a better grip on the rules.