Disabling DNS Rebinding Checks does alter domain overrides
-
@Bob-Dig said in Disabling DNS Rebinding Checks does alter domain overrides:
anything with domain overrides in the first place.
A domain override points the query for that domain to whatever you setup in the override - this is a forward, if the answer is rfc1918 it it would be a rebind.
If you want domain override to return rfc1918, then you need to setup the domain as private, or disable rebind. When you setup a domain override, it sets the domain as private for you.
You can check that by looking in the /var/unbound/unbound.conf file
Here I setup a domain override for example.com - see in the conf how now set to private and non secure, ie no dnssec.
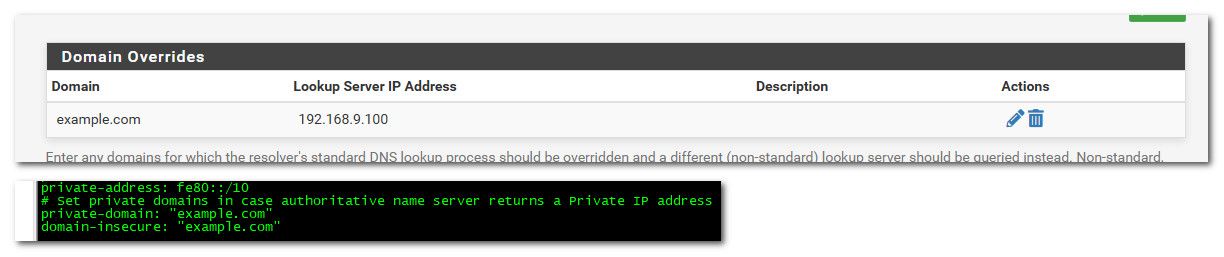
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
domain as private, or disable rebind.
Hi @johnpoz ,
disabling rebind (checks) does make the problem for me, it doesn't solve it.
And I think I know why now because I checked the config file like you said.
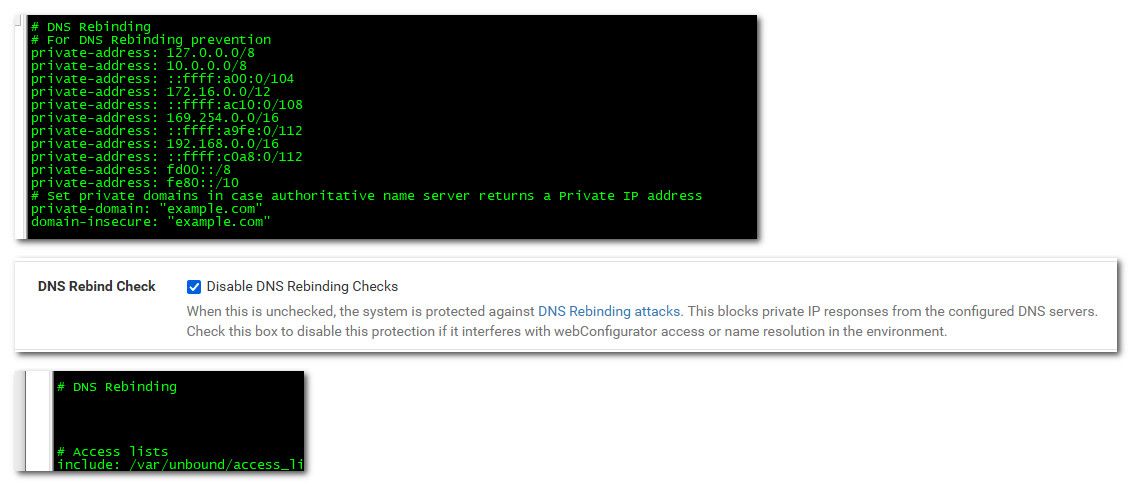
If I disable rebind (checks) the config is missing private-domain and domain-insecure.
In my mind, it shouldn't delete private-domain although I don't know anything about unbound's inner workings. There might be other differences in the config I haven't sighted. For me this looks like a bug, reason has been given in the first post. -
@Bob-Dig If you disable rebind in the advanced options in pfsense.. Then the whole rebind section listing what IP ranges are "rebind" should go away..
have you tried restarting unbound once you have made a change, like turning off rebind protection? Just because the conf changed, doesn't always mean that unbound restarted and used the new conf.
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
have you tried restarting unbound once you have made a change, like turning off rebind protection?
Yes, I did. And
# Set private domains in case authoritative name server returns a Private IP addressis also missing. But I think this is essential for Domain Overrides to work correctly. It shouldn't get deleted when turning off dns rebind checks. I will file a bug report, at least you haven't give me any reason to not do it.

-
@Bob-Dig no that whole section should go away if you turn off rebind protection. Those IP ranges are what tell unbound its a rebind.. if there is no networks in there, then it wouldn't be considered a rebind.
Give me a bit, let me have another cup of coffee and I will setup an actual domain override that will work and simple enough to tell if rebind is working or not..
edit: ok, something is going on.. Its not the rebind thing.. But looks to be related to dnssec.. But there is not dnssec anything on the host overrides I put in my upstream pfsense. I can get it to work if I set the domain to not secure.. Or if I disable dnssec on the downstream pfsense.
Ok this might need more coffee, or better yet a couple of Micheladas ;)
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
Give me a bit, let me have another cup of coffee and I will setup an actual domain override that will work and simple enough to tell if rebind is working or not..
I actually don't know what rebind means. I only know that Domain Overrides don't work for me anymore if rebind checks is disabled.
But I have other options set as well in the advanced settings, so yeah, please check when you are comfortable.
My uneducated guess is, while it is ok that the following is gone
# For DNS Rebinding preventionthe following should stay
# Set private domains in case authoritative name server returns a Private IP addressbut it is also gone and domain overrides don't work anymore.
-
@Bob-Dig see my edit
A rebind is if you ask a dns for something and it returns a rfc1918, when it shouldn't.. Normally the only time you should get back rfc1918 for a fqdn, is if the resource is local.. If your asking some other dns, like if you forward to some other dns - it shouldn't be a rfc1918..
edit:
Normally with dnssec - if there is no dnssec setup on the domain, then shouldn't matter.. Hmmm example.com is a actual valid domain.. So wonder if its signed with dnssec, and the host override is failing because of that.Are you really using example.com - or some other domain?
Just looked and yeah example.com does have dnssec enabled - so yeah that would explain why its failing unless set the domain to non secure.. What domain are you actually using? Send it to me PM if you don't want to make public.
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
What domain are you actually using? Send it to me PM if you don't want to make public.
Mine should have dnssec too. But I don't see why this matters here, it was working fine, while dns rebind was in check.

PM inbound. -
@Bob-Dig said in Disabling DNS Rebinding Checks does alter domain overrides:
while dns rebind was in check
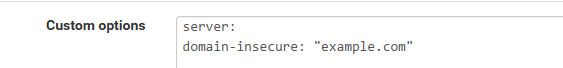
because when you have rebind enabled, and then add a domain override it auto addess that its not secure and to not worry about dnssec.
When you disable rebind it doesn't add anything because your not doing a rebind, but it would then be doing dnssec.
See the custom option I setup to say hey example.com doesn't have to pass dnssec..
So either leave rebind on, which should be fine. It is a good thing to do rebind checking. Or either completely turn off dnssec (bad to do) or set the specific domain to be ok with not passing dnssec checks.
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
because when you have rebind enabled, and then add a domain override it auto addess that its not secure and to not worry about dnssec.
When you disable rebind it doesn't add anything because your not doing a rebind, but it would then be doing dnssec.
Ok, thanks for clarifying that. But the more ideal outcome would be that if I disable rebind check, that it still doesn't check for dnssec for a domain override, right? Now the question is, is it doable or is unbound not capable to that solution. But your right, the easiest thing to do for me is to enable dns rebind check. I will have to give my email server a different dns server then because of reasons.
-
@Bob-Dig said in Disabling DNS Rebinding Checks does alter domain overrides:
if I disable rebind check, that it still doesn't check for dnssec for a domain override
Yeah guess that could be an option set, that if rebind is disabled completely to still add the non secure setting for domain overrides.. But its easy enough to do with just custom setting.
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
But its easy enough to do with just custom setting.
I am GUI addicted and pfSense is a GUI in the first place. I will leave it up to netgate what to do with my report. Thanks again for looking into it.
-
@Bob-Dig you can set the custom setting in the gui..
To be honest not sure if I like that it auto adds anything, what if I don't want to disable rebind on where I am forwarding too? I think it should require to choose that I want to disable rebind or dnssec.. Maybe they could add some checkboxes when you add the domain override..
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
To be honest not sure if I like that it auto adds anything, what if I don't want to disable rebind on where I am forwarding too? I think it should require to choose that I want to disable rebind or dnssec..
For DNSSEC it is clear. As soon as you use a domain override, you want DNSSEC to be disabled for that, right? And this was the problem here, so the solution seems easy: Do still set private domains in the config even if dns rebind check is disabled.
-
@johnpoz said in Disabling DNS Rebinding Checks does alter domain overrides:
@Bob-Dig you can set the custom setting in the gui..
Na...

-
@Bob-Dig said in Disabling DNS Rebinding Checks does alter domain overrides:
you want DNSSEC to be disabled for that, right?
Not necessarily.. If where you are forwarding does actually do dnssec then no you wouldn't want to disable it.