IPSEC site to site Openvpn site to site
-
Good morning,
I need help I don't know what to do
I have a firewall connected point to point by ipsec to a paloalto
works fine even openvpn clients connect correctly and can access ipsec
I have the problem with other sites that are connected with openvpn point to point
If I launch a ping from the client firewall and select OpenVPN client it responds but if I launch from the LAN it does not work
If I make a tracer it is sent fine but I don't know something :(
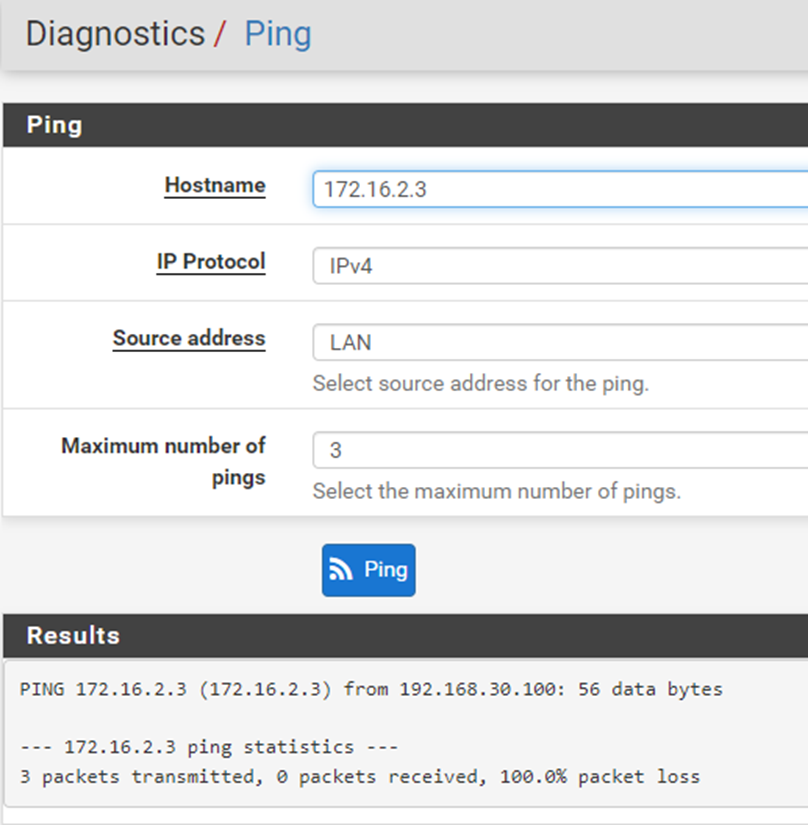
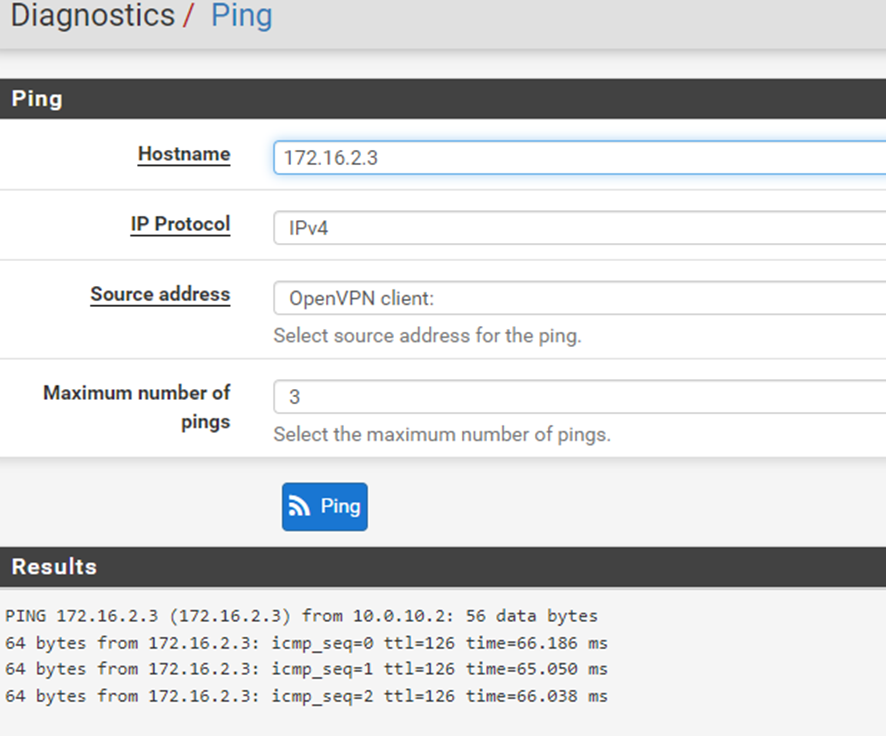
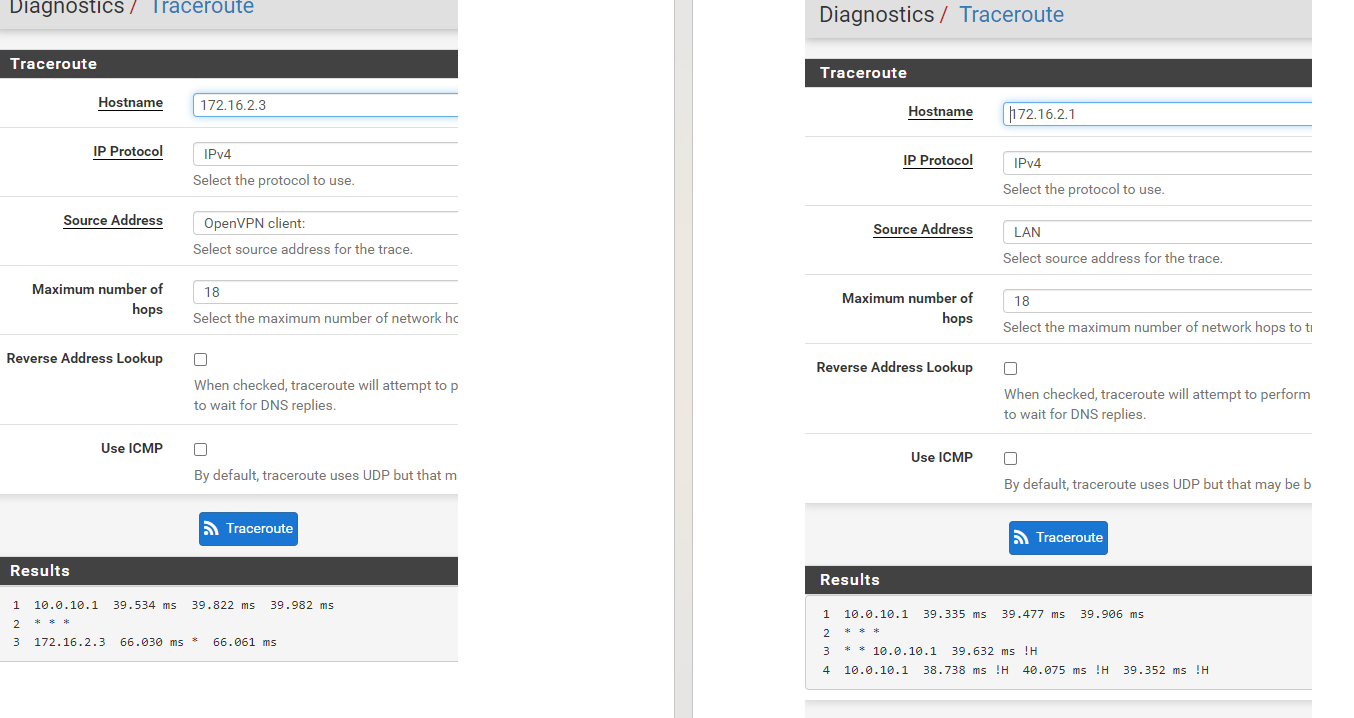
-
@jba
Did you configure a CSO for this client on the server and is it applied without issues?
To check this, set the log level to 4 on the server and reestablish the connection. -
I have configured the IPs on the OpenVPN client, I don't know what you mean by the level and the CSO
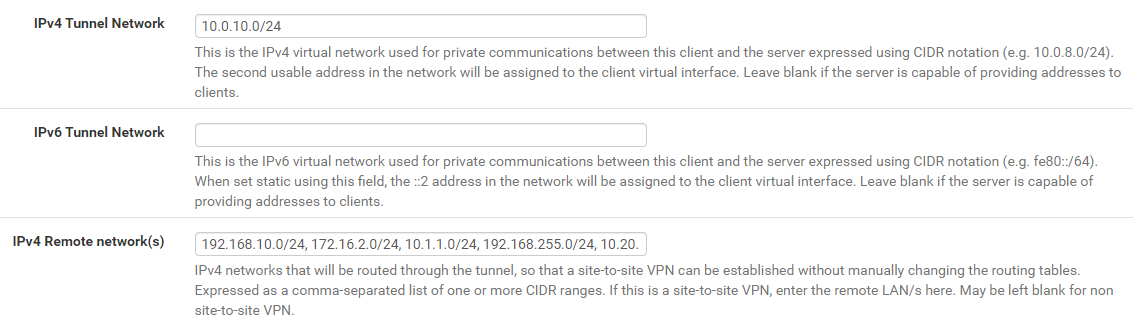
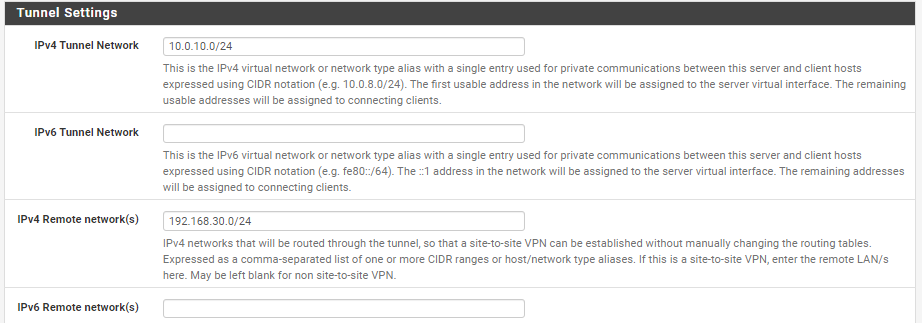
Server OpenVPN
excuse my ignorance, Thanks for helping me
-
@jba
VPN > OpenVPN > Client Specific Overrides
It is necessary to route traffic to the clients side local network. -
Hello again I can't get it to work
I put the configuration on the vpn override client firewall or on the server side
the common name I put the cn of the certificate
Do I have to specify in advanced? or configure Tunnel Settings
I try it but it doesn't work for me :(
Thank you
-
@jba
The CSO has to be configured on the server, as I mentioned already.In the CSO at "tunnel network" you have to state an IP out of the servers tunnel pool, e.g. 10.0.10.23/24.
And down at "Remote Networks" you have to enter the client side networks as well as you have in the server settings.If this is all correct check the log to see if the CSO is applied properly.
-
Thanks for the support viragomann,
in the end it worked for me by going to IPsec to phase 2 and adding the IP range of the client's LANThanks for everything
-
@jba
Glade that you got it working.
You're right, all subnets you want to connect across the IPSec need to be stated in a phase 2 as well.