Captive Portal, Ruckus hotspot setup and POST request to a return URL question
-
@stephenw10
A guest SSID is not working because Ruckus blocks the access to the private networks and also if I set a rule for accepting the pfsense IP and put it on top, Ruckus is still blocking. I set up a normal SSID and created the rules for blocking internal IPs except the pfSense IP then I will get the captive portal login page, can login with a voucher, and get internet access. I first try it with a guest SSID, then with a Hotspot/WISPr, first without the login page, second with the auth redirection URL POST issue. I will ask the Ruckus people why rules for the guest SSID is not working. -
Sounds like 'guest ssid' implies some special setup in Ruckus world. But I'd expect just any additional SSID that can be tied to a VLAN would work.
-
@stephenw10
yes, this is what I have done now. It is working with a regular SSID with VLAN tag.
There is a default check box for guest SSIDs to avoid traffic/access between clients. I assume that this is the reason why I could not get access to the pfSense captive portal even with setup a rule for it.
The Ruckus world is sometimes special. I have used now the unleashed version for testing.
The unleashed version is the cheaper one without a licence needed.
I had implemented this setup together with the pfSense captive portal in the past for two hotels with the licenced version of the Ruckus access points plus a ZoneDirector controller. This was no problem at all.
This behavior could also be related to the current firmware version. Doesn't matter, it is working now.
Thank you for your time. -
@getcom said in Captive Portal, Ruckus hotspot setup and POST request to a return URL question:
There is a default check box for guest SSIDs to avoid traffic/access between clients.
That would normally only prevent access between wireless clients and not between wireless clients and wired hosts.
-
Hello. I am trying to configure captive portal on pfsense with Ruckus AP in the back end. I am struggling how to modify the authentication response. Can somedody help me, please? How should I modify the noauth.html with proper POST response for Ruckus to accept authenticated client? Where do these responses go?
https://${RuckusUnleashedFQDN}:9998/login
username=${USERNAME}
password=${PASSWORD}
client_mac=${client_mac}
uip=${uip}
url=${RETURN_URL} -
@sash11 said in Captive Portal, Ruckus hotspot setup and POST request to a return URL question:
Hello. I am trying to configure captive portal on pfsense with Ruckus AP in the back end. I am struggling how to modify the authentication response. Can somedody help me, please? How should I modify the noauth.html with proper POST response for Ruckus to accept authenticated client? Where do these responses go?
https://${RuckusUnleashedFQDN}:9998/login
username=${USERNAME}
password=${PASSWORD}
client_mac=${client_mac}
uip=${uip}
url=${RETURN_URL}This was also my fault. What you want to do is not working.
You do not need to setup anything special on Ruckus.
Just create a new ESSID without authentication in Ruckus unleashed and add a VLAN to this.
Then create this VLAN on pfSense, setup a DHCP server, add this VLAN to your managed switches, setup the ports where the Ruckus APs are connected to trunk ports, join the VLAN on this ports. Rest is done in pfSense in the Captive Portal section without anything special except that you use the configured VLAN as interface.
If you need screenshots then I can do that next few days.Ralf
-
@getcom
The config out of the box does not seem to work. Ruckus ends up blocking all traffic but the local subnet, since clients are not authorized. Here is how I have it configured:
Ruckus Unleashed side: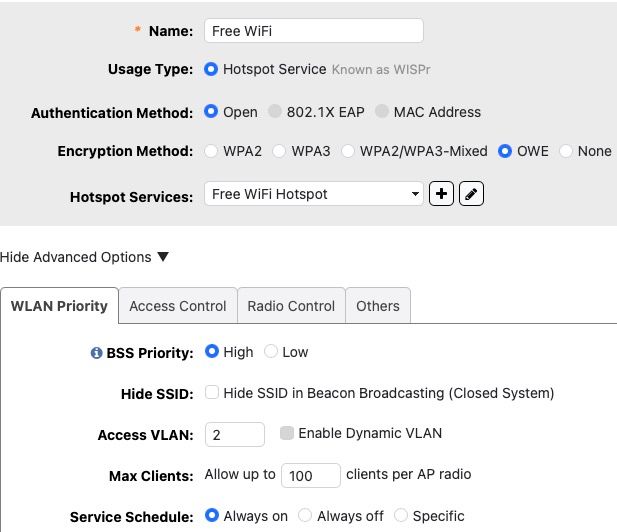
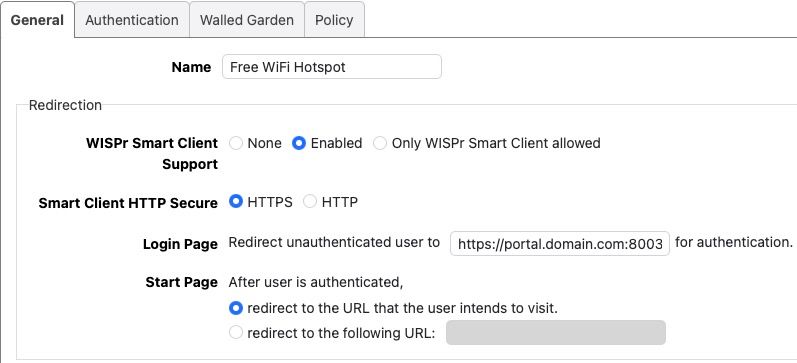
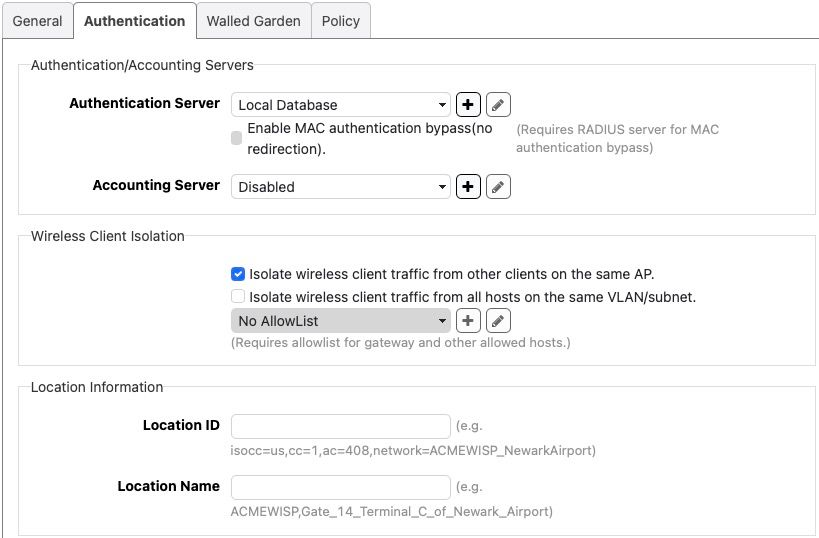
Pfsense side:
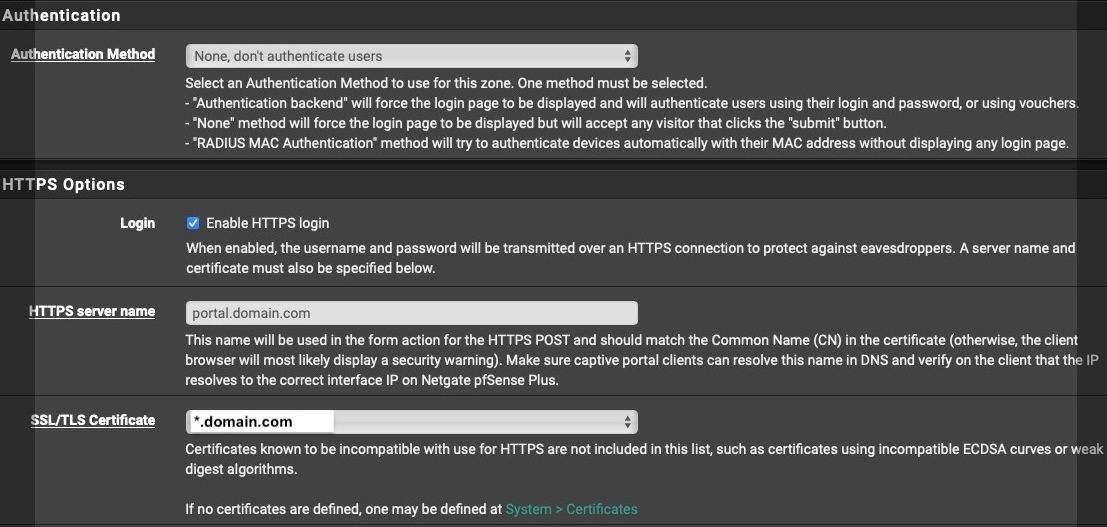
Client is not authorized in unleashed:

The work around I am using now is to allow everything to pass in pre authorization in walled garden. But I would like to have it working properly if possible....
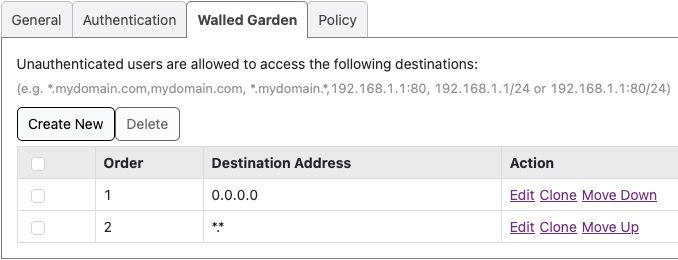
-
Hmm, you seem to be trying to run two captive portals there. I'm no sure why you're trying to run CP in pfSense if the AP is already redirecting traffic. or conversely why the AP is redirceting traffic if pfSense is running CP, it should just pass all traffic to pfSense.
-
@stephenw10
If I choose hotspot wifi type on AP, I have to use external portal. It can be any external portal. It just happens that pfsense has one already built-in, so I am trying to use that.
If I choose Guest type of wifi network, I can utilize built-in portal on Ruckus AP. But nowhere I am using two CP at the same time. -
Well disable that 'smart client' redirect stuff then. No redirect of any of the pfSense details should be required. It should just pass traffic at layer 2 and pfSense does all the authentication/login.
-
This is the correct setup on Ruckus:
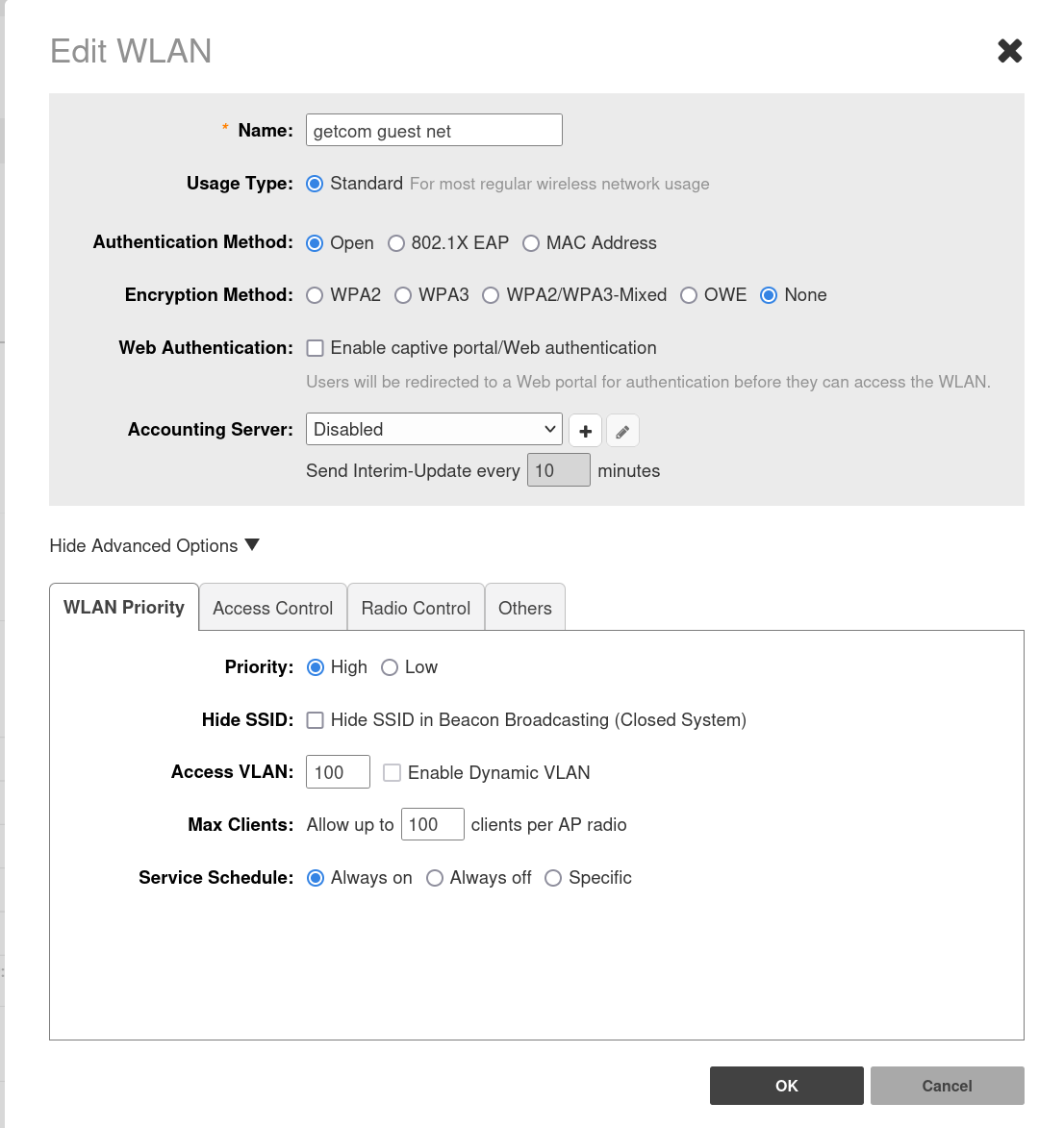
Just setup a standard WiFi with VLAN XXX, then add this VLAN to your switches, change the switch ports of your Ruckus APs from "access" to "trunk" and join the ports as tagged VLAN.
Next setup is on the pfSense site: add this VLAN, setup an interface for this VLAN, setup DHCP on this interface, add a Captive Portal for this interface.
In Captive Portal check follwing:- Reset waiting period
- Preserve users database
- Reauthenticate Users
- Local Authentication Privileges
- Login
Add a HTTPS server name, e.g. guestlogin.yoursite.tld and add a host override in DNS resolver with IP of your VLAN interface.
Choose your certificate (we are using letsencrypt).Done. It is working then.
Next would be a custom login site...
-
@getcom
Thank you! That worked!