Two subnets, virtual IP Address, with one gateway
-
Hello everyone,
I have a question about two subnets with one gateway.
Once the primary network, 172.17.17.1/24 and then the second network with Virtual IP Address 172.16.155.1/24. Access to the Internet via the gateway (172.16.155.1) works perfectly with the Virtual IP Address.
But now I want to prevent both networks from reaching each other, because that works now.
At what point the rule and what it must look like, I don't know exactly now and don't want to block all network traffic, because I'm connected via VPN myself...
The question is whether this is the right way or whether it should be solved via an OPT interface, where I have to assign the traffic route and, if necessary, a VLAN ID.
Thank you for your help in advance!
Ron -
@jogovogo said in Two subnets, virtual IP Address, with one gateway:
I have a question about two subnets with one gateway.
Once the primary network, 172.17.17.1/24 and then the second network with Virtual IP Address 172.16.155.1/24. Access to the Internet via the gateway (172.16.155.1) works perfectly with the Virtual IP Address.
You mean, both subnets are assigned to a single interface of pfSene, i.e. you have a single layer 2 for both?
and don't want to block all network traffic, because I'm connected via VPN myself...
Your VPN might not be concerned from rules you are adding to other interfaces.
-
Thank you for your answer yes, both networks are connected to the same interface.
The note with the VPN only serves that I access the web interface from the Pfsense from the outside.
The VPN access itself does not take place via Pfsense.The question is where do I set the "deny" rule for both subnets.
regards
ron -
@jogovogo said in Two subnets, virtual IP Address, with one gateway:
The question is where do I set the "deny" rule for both subnets.
On the interface tab as any other rule.
You can block access to any other private subnet. Best practice for doing this is to create an alias of type network and add all RFC 1918 ranges to it. Then add a block rule to the LAN interface and use this alias as destination. Put this rule above of the allow-any rule.
Note that the rules are probed from the top to the bottom of the rule set. So access to private destinations are blocked, but internet access is permitted.However to not block access to used services on pfSense itself, for instance if pfSense provides DNS for the internal subnets, you then need to create a pass rule for these services and place it above of the block rule, means at the topmost position.
For accessing the webGUI you should have enable the anti-lockout rule. So this rule is always on the very first place and cannot be moved down. -
Okay, I would have made it easy for myself now by simply banning the subnet among each other, if possible.
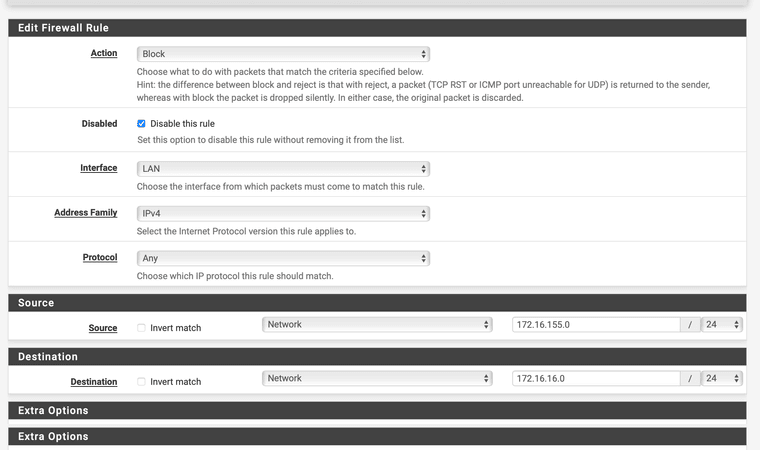
-
@jogovogo
Yes, you can do that, but makes no sense.
At source you can select "any", at destination simply use 172.16.0.0/12. There is no need to limit this anyhow at all.
Traffic between devices within the same subnet does not pass pfSense, hence the rule has no affect on it. -
@viragomann said in Two subnets, virtual IP Address, with one gateway:
@jogovogo
Yes, you can do that, but makes no sense.
At source you can select "any", at destination simply use 172.16.0.0/12. There is no need to limit this anyhow at all.
Traffic between devices within the same subnet does not pass pfSense, hence the rule has no affect on it.Okay, understandable, that has no effect, I hadn't even thought about it...
So it had to be right, didn't it?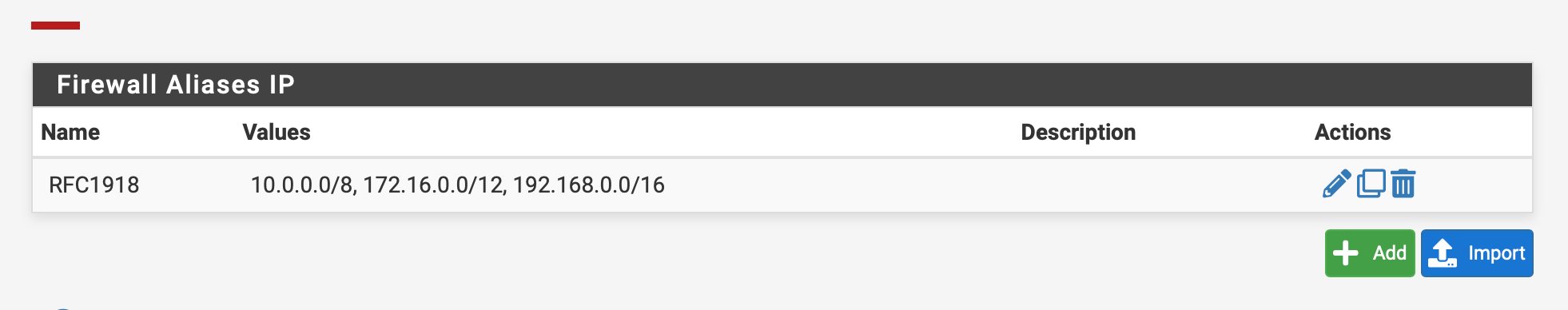
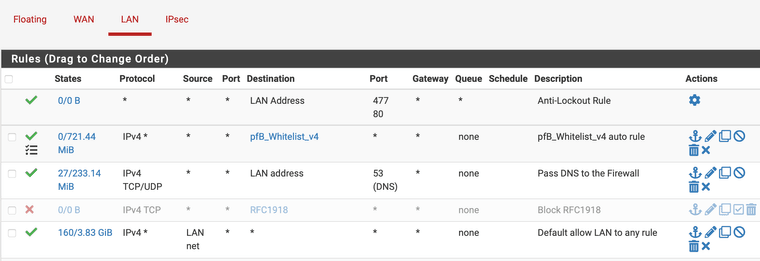 

 -
@jogovogo
You might want to block any protocol, not only TCP. Apart from this it seems well. -
The rule works perfectly. The problem is that it automatically deletes itself...
Do you have an idea if there is any management like autorule creation / delete.
regards
ron