Active IPsec tunnel between pfSense and OPNsense is active, suddenly reconnects with 0 bytes in phase 2
-
Re: Vpn Ipsec tunnel phase 2 show 0 bytes of data
We use a Netgate 1100 to connect a small branch office via IPSec to an OPNsense appliance at the HQ. Both are equipped with a static public IPv4. IPsec is configured in this way, that the branch opens the connection via VTI (routed) network.
By default, the IPsec tunnel is active and I can see traffic-counter through phase 2 counts data. A ping from one to the other side (and reverse) works as it should. Then there must be some kind of reconnection between both firewalls because we see that the tunnel remains up but in phase 2, 0 bytes are going through. If this happens, nothing goes through this tunnel - ping does not work in any direction.
This happens once a day. When we recognize this, we drop the connection at the HQ and data is going to the tunnel.
DPD is active on both sides. Because we use public IPs on both sides, we don't use NAT-T.
Does anybody have any suggestions to get this problem resolved?
Regards, Christian
-
The traffic counters show 0 in both directions? At both ends? Even when pinging from either end?
Are there any errors logged when it rekeys?
-
@cwo
Do you have any IPsec logs we can review? -
Hi. I need to collect them first. I will try it on Monday and post them here.
Regards, Christian
-
Hi. Yes, there is no traffic on both sides. I try to do some screenshots on Monday.
Regards,
Christian -
Even when initiated from either side?
If one side was doing something odd I might expect to at least see outbound packets on one side if traffic was initiated from that side.
If there's actually no traffic at all it sounds like maybe the routes are missing so it's not trying.
-
Sorry for the delay. The connection is initiated from pfSense (branch office)to OPN (hq). The OPN is only waiting for incoming requests. We use a certificate based authentication, not PSK.
Yesterday, I found the IPsec tunnel in this state:
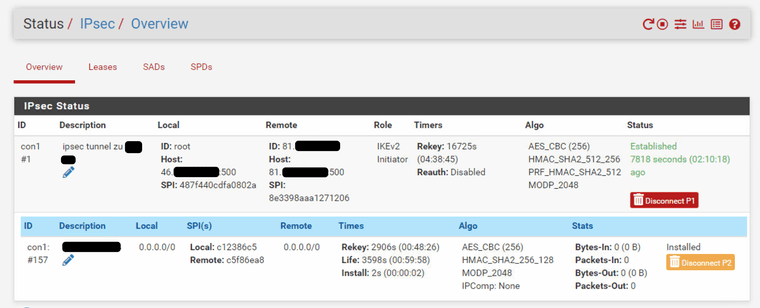
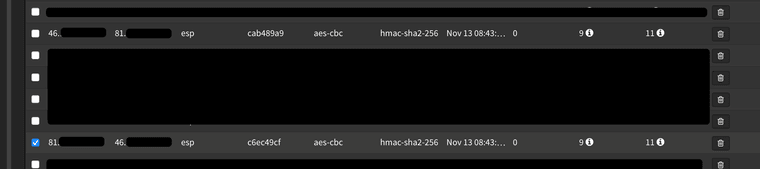
On the other side, I found that SPIs of "Phase 2" does not match on both sides:
After dropping the tunnel (restarting the service) on the pfSense side, it went back online but traffic flows only in one direction:
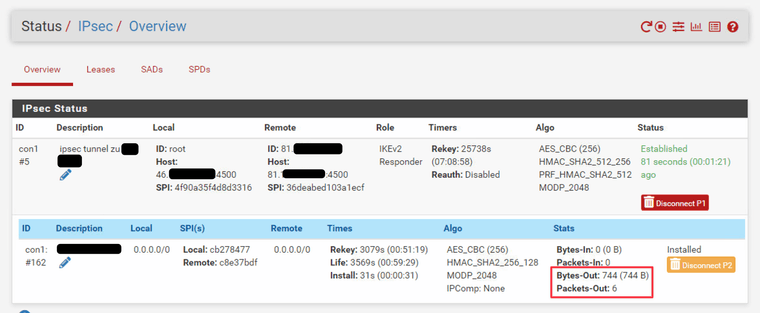
Then I did the same thing I do every day when this happens: I went on the OPN-side in the Phase 1, did a very small changed within the DPD (for example change the delay from default 10 seconds to 9 seconds) just to make a change and get the ability to "apply" the changes.
This seams to reset something and the traffic immediately starts running through the tunnel.
I will try to provide a pfSense ipsec-log but the log contain a lot of personalized information like IP addresses, certificate names of my company ... that needs to be truncated first.
Regards,
Christian
-
-
Nothing logged there really looks like a significant error.
In any of those intermediate states do the SPIs match?
Do you see routes at either end in any of those states?
-
Any time I've seen issues close to this it's because of collisions in the negotiation where both sides are rebuilding things at the same time and then can end up confused or broken in various ways.
I'm not sure what options you may have on the peer, but go over all the suggestions here in this doc:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/ipsec-duplicate-sa.html
-
@jimp
Thank you. This could explain it. I will follow the link and check the options :-)Regards, Christian
-
When I see this correctly, the SPNs does not match fully.
I always thought, that if the tunnel is up, DPD would handle the problem, if SPNs doesn't match?!? It is active on both sides.
I don't understand what you are meaning with "seeing routes"? I use a vti mode with static routes defined under System > Gateway. Looking at the tunnel status under
Status > IPsec
shows a "Local 0.0.0.0/0" and "Remote 0.0.0.0/0".
The gateway, defined within the Netgate, points to the Tunnel-IP from the OPN and vice versa. A route on each side points to the IP network on the other side.
I also disabled "Gateway Monitoring" and "Gateway Action".
Regards, Christian
-
DPD can still work even if the childSAs are mismatched so traffic doesn't actually pass.
Do you actually see routes present in the routing tables when it stops passing though? This feels like it could be missing routes that are replaced when you make any save to the tunnel.
-
Hi Stephen.
I give you a reply on this tomorrow (when the error happened again ;-))
Regards,
Christian