Longstanding FreeRADIUS EAP-TLS security bug on validating client certificate common name
-
I figured a screenshot would be easiest:
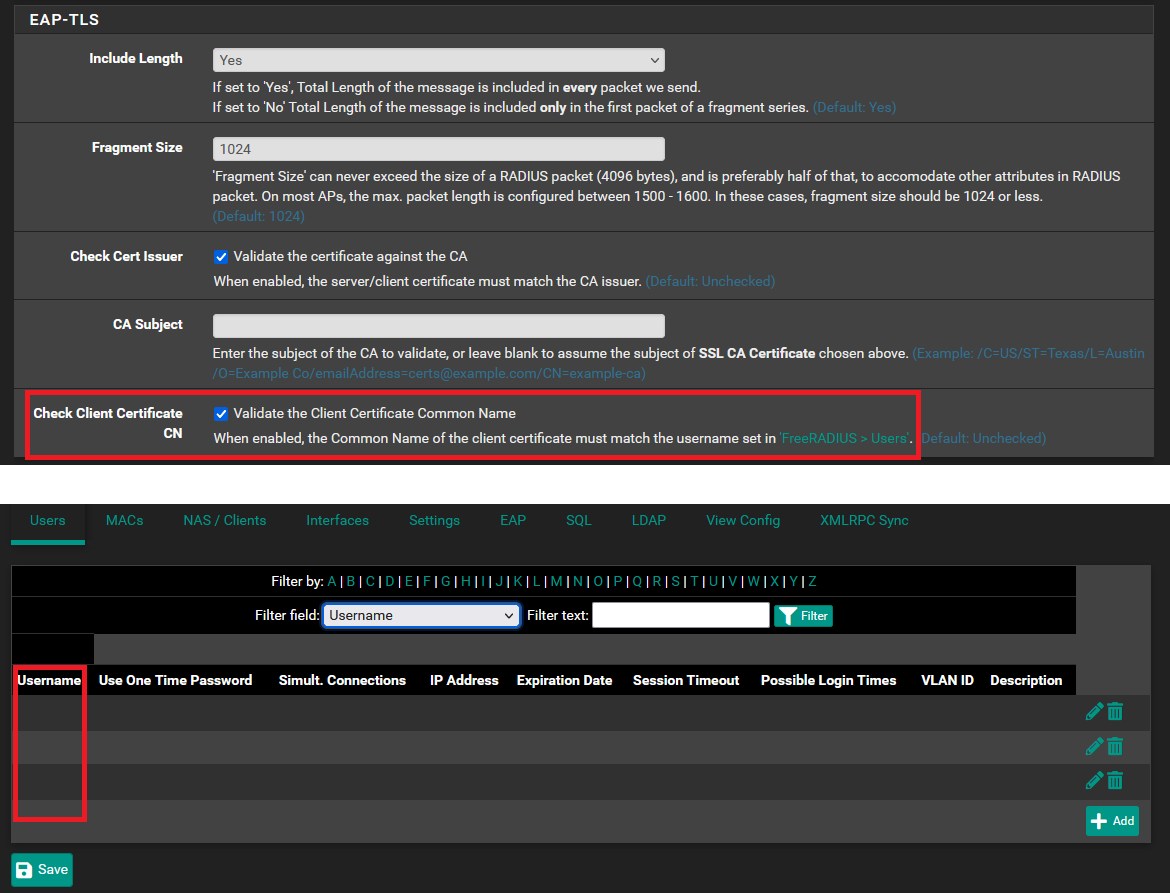
Basically, the "Validate the Client Certificate Common Name" checkbox in the EAP-TLS section does nothing. I can delete all users (or rename the username field to gibberish), and wireless devices can still connect to the WLAN. I presume that no validation/comparison is done to see if the Common Name that the client presents == the Username listed in "Users" in the FreeRADIUS package.
Thank you for your time.
-
Also seeing this bug, anyone know if theres any updates on this?
Edit: Looks like this is also known about here:
https://redmine.pfsense.org/issues/11054 -
@jamesg246 said in Longstanding FreeRADIUS EAP-TLS security bug on validating client certificate common name:
Also seeing this bug, anyone know if theres any updates on this?
Edit: Looks like this is also known about here:
https://redmine.pfsense.org/issues/11054I haven't seen any updates both in this thread and on the Redmine ticket. I linked the Redmine issue in the first line of the original post, btw.
Also updated the Redmine issue showing it is still broken in 2.7.2 with FreeRADIUS package 0.15.10_1.
I hope the screenshot makes it clear to understand the behavior we're talking about that is broken. It's sorta hard to follow in the bug report.
-
@Finger79 I remember running into this when they fixed it, but I did notice recently not working again.
I recall when they fixed it, because I was working without local users to validate the cn again, and then it broke.. Then I created them and working... But some recent thing I was doing I didn't have a user created and it worked..
I will try and add my 2 cents to the redmine, because I do believe it is currently not working again.. I have no users, have cn set to be check - and they auth, so clearly its not validating because there is nothing to validate against, etc..
its currently not working in 23.09.1, I was just going to wait to see what 24.03 brings.. Since its not really a big concern for me.. But I can see where it could be..
edit: so don't forget will put this here.. See I don't have a johnsphone user, and cn set to validate.. But it still auths just fine

-
F Finger79 referenced this topic on
-
Has this been fixed? I have the same problem in 24.03 and 0.15.10_2
-
@sltadm said in Longstanding FreeRADIUS EAP-TLS security bug on validating client certificate common name:
Has this been fixed? I have the same problem in 24.03 and 0.15.10_2
Nope, hasn't even been acknowledged. It's a minor security vulnerability.
The Redmine bug report is linked in this thread.
-
@Finger79 Thx for the info.
-
Can this security vulnerability get some love please?
-
Confirmed still an issue as of May 2025 with pfSense CE 2.8.0 and FreeRADIUS package version 0.15.14
I also updated the Redmine bugtracker: https://redmine.pfsense.org/issues/11054
Can this security vulnerability please get some attention? Wi-Fi supplicants are able to join an 802.1x WPA2-Enterprise network without the username in the client certificate validated at all.