Netgate SG-2100 pfSense 32GB Router & Firewall and a Sercomm Model: LTE2122GR router
-
It depends exactly what those devices are doing currently.
Which of them is NATing? What subnets are in use?
I assume there is some physical separation between the router and your house? Because the 4G router need to be placed for better signal?
Potentially the 2100 could be at either side.
Steve
-
Thanks for your reply Steve. Currently, without the SG-2100 installed, the router is assigning IP addresses. I'm not sure about subnets, I just have them set to the usual 255.255.255.0, perhaps that's not what you mean...
Good point about having the SG-2100 pfSense network connected after the receiving Ubiquiti NanoStation M5 in the house. That would keep the existing WAN setup coming in which would simplify things.
Yes the router is connected to an antenna in the garage (I am in the countryside).
So if I try this all I should have to do is configure pfSense. Does it matter how I have the WAN configured or is the standard IP setup okay?
Thanks for your help.
-
Ok so it sounds like there is only one subnet in use if host devices in the house get their IP addresses directly from the 4G router.
That implies the wireless link is purely layer 2, it just passes the traffic?
Ideally you want only one NAT translation so only one private subnet in use. So with two routers in the chain you would want to put one of them in bridge mode of some sort. That may not be possible. And your 4G carrier may be using CG-NAT anyway. But however it's configured you need to avoid a subnet conflict. pfSense uses 192.168.1.X/24 by default, if the 4G router is also using that subnet on its LAN then one of them must be changed.
-
Thanks for the info Steve, much appreciated. I will read up more on what you have said. Could you point me in the right direction of the best guide to configure pfSense or area on here for someone new to this?
-
Aside from changing the subnet to avoid a conflict it should 'just work' using the default config. I'd recommend running it in a basic config like that for a while before adding anything more complex.
Asking questions here is as good a place an any though.
-
Hi Steve. So I have the SG-2100 reset and I was thinking of changing the subnet to a 10.0.0.0 config but I would like to install surfshark VPN in the pfSense so perhaps it would be better to do that first as it may need a specific type of subnet for the LAN? Also Will it be possible for me to still gain access to administer the router and repeaters on the 192.168.1.x WAN subnet while connected to the SG-2100 or would I have to plug in directly to do that?
Thanks again for your help, much appreciated.
-
The LAN subnet you choose would have to not conflict with an OpenVPN tunnel subnet but that's unlikely. There are a lot to choose from in the 10.0.0.0/8 address space. Try 10.100.1.1/24 as LAN
Yes you will still be able to reach the management interfaces of other devices in the 192.168.1.0/24 subnet from the pfSense LAN.
-
Hi Steve. So I have the SG-2100 installed with the latest pfsense. I set up the LAN network as suggested. I had a problem accessing web pages so thought to manually configure the DNS in the router and that has done the trick. If fact web pages seem to be much more responsive which is great. Now to look into the VPN.
This seems to be a powerful little box that can do lots of different things. I used my own domain when doing the basic instal does that mean you could actually host a webpage or is it just a domain name for the local network?
Thanks again.
-
It's just for the local network. You can't host web servers in pfSense itself.
Steve
-
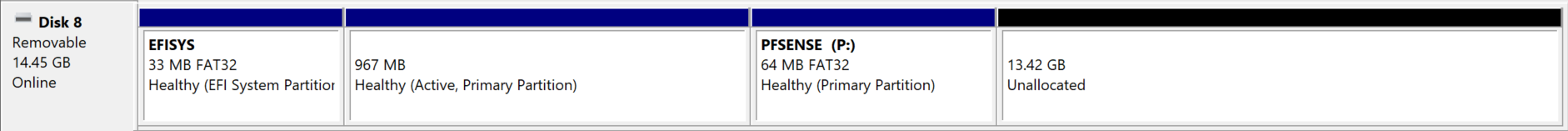
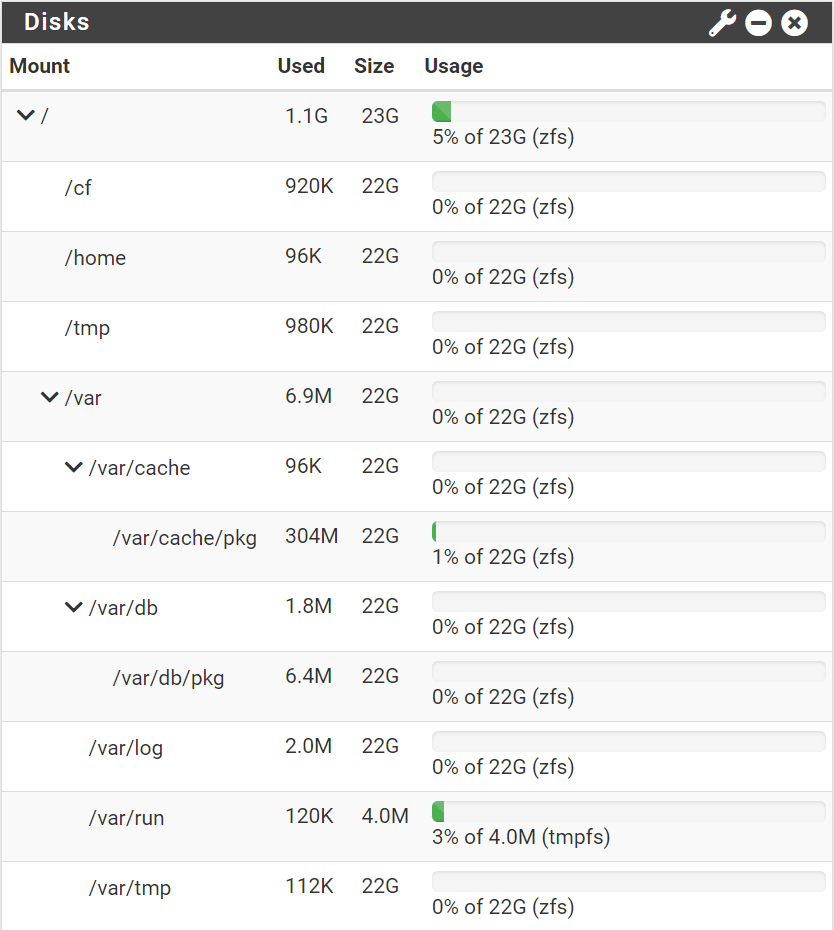
Hi Steve. I was checking is Disk Management and in the pfSense dashboard and I'm not sure if the full 32GB is being used correctly.....
-
You probably have some space used by ZFS Boot Environment snapshots. Check System > Boot Environments
-
There are few entries in there but only one of any size is "default" Base version: 23.09 / Space: 3.31G
Would it be worth restoring via a recovery image or do you think this is normal? I thought there would have been more space available on the 32GB.
Thanks.
-
The size shown there is not the size used on disk by the snap. It's an issue without an easy fix but we are looking at it.
Remove any snaps you don't need there and see how it affects the available disk space. -
Hi Steve.
I have a Surfshark VPN account. I'm wondering if the VPNs available within pfSense are free or do I need my Surfshark account to be used by one of the options (pictured) within pfSense?

I'm a bit confused. I'd like to be able to have a VPN running within pfSense so that I don't have to turn on and off in my PC all the time.
Also when I do eventually have a VPN set up in pfSense, I take it you can turn on and off from within pfSense in the same way you can locally?
Thanks.
-
The VPNs listed in pfSense are just types of VPN. You still need to configure a server for it to connect to. That could be Surfshark and you would need an account with them to get a login.
-
Hi Steve, Surfshark will allow me to set up the VPN using either WireGuard, OpenVPN or IKEv2. It seems that OpenVPN is the preferred. Would you agree?
Also could you recommend a pfSense+ VPN configuration guide? I'm having a bit of trouble finding a basic walkthrough.
I found this one specifically from Surfshark which seems like the right thing to do but some of the options mentioned within are not available in my pfsense+ :
"Then navigate to System > Cert. Manager > CAs." - does this mean System\Certificates\Certificates ?
https://support.surfshark.com/hc/en-us/articles/360010789259-How-to-set-up-pfSense-2-4-4-with-Surfshark
Thanks.
-
OpenVPN is the most tested and most flexible.
No that line is for adding the Surfshark CA cert. You'd have to add it using the CA tab there so System > Certificates > Authorities.
-
That's working.
I was wondering: can I have multiple clients setup for different server locations and if so is there a quick way to change between them or is the easiest thing to just open up the existing client and add a different Server host or address as this would be the only information that would be changing in the config (as far as I can remember)?
Thanks for your help again Steve.
-
Yes you can as long as the clients use different tunnel subnets and gateway IPs. That can be a problem with some VPN providers.
-
"different tunnel subnets"
Each Surfshark server location is on a different subnet, at least they all start with a different three digit prefix in their addresses - is that what you mean?
My current config does not actually use a specific IP but rather the host name specific to the server region I am connecting to.
You can chose to use a specific IP from their servers rather than using the host name but as each location that I will be connecting to has it's own subnet (I think) I am assuming sticking to hostnames instead of IPs will be okay for configuring multiple VPN interfaces within pfSense?
When you say gateway are you referring to:
When I set up the "description" in: Interfaces > Interface Assignments and add Surfshark VPN interface.
Are you saying that I should create a different "description" for each VPN connection so that each IPv4 rule (within: Firewall > Rules > LAN) can choose a different "Gateway" that relates to the specific VPN interface selected/server location configured above?
I read a post saying:
"One simple way I've done it is with firewall rules. So if I had 4 VPN servers configured, I'd have 4 rules for my interface. 3 rules stay disabled, 1 rule stays enabled. The enabled rule is the VPN Server I route traffic to. The gateway for each rule is set to a different VPN server location.
If I want to hop servers, I just disable the current rule and enable the rule to the new gateway."