New Vlan and Default deny rule IPv4
-
Hi all,
I have had an interesting issue for a while. When I add a new Vlan on my pfsense, all traffic is going directly to the default deny rule.
It has happened a while after the 2.7.0 Upgrade
No matter what rules I setup or if I try to use the Easy rule function it is blocked by the Default deny.
I have 12 other VLANs that are working fine. I have gone through the settings to match working with non working, but no luck.
Also the incoming ISAKMP (500) for IPSEC tunneling has stopped working and is also blocked by the Default deny rule.
Is there any chance that the 2.7.1 will solve this ?
Thanks ! -
@ricbjo
When a new VLAN (new interface) is created on pfSense there is a default deny automatically applied. This doesnt happen on the default LAN interface when you install pfsense.
If you create a permit rule and the flow matches that rule than it wont be hit by the default deny.
Do you have screen shots you can share? -
@michmoor Hi !
Thanks, yes I have added rules for outgoing. The other 12 vlans are working fine.
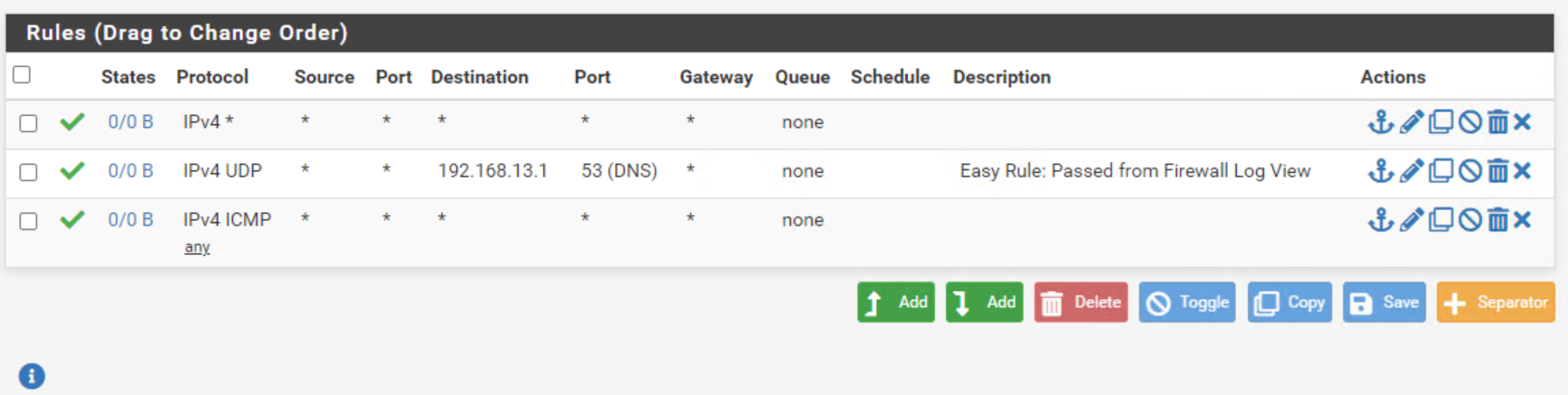
As you can see I have opened outbound.
Dns requests to my pfsense and some traffic to the outside is blocked by default deny rule. But I can browse the web and open the webgui of my pfsense. -
@ricbjo
Is this VLAN created under Interfaces / VLANs?
Is it mapped to the correct parent interface?
Is the managed switch you have connected to pfSense have the vlan created? Is the VLAN added (trunked) to the link to the pfsense?Your client machine, is it added to the correct vlan? If set for DHCP, is it pulling an IP address from pfsense (assuming pfsense is the dhcp server)
-
@michmoor Thank you so much for quick reply !
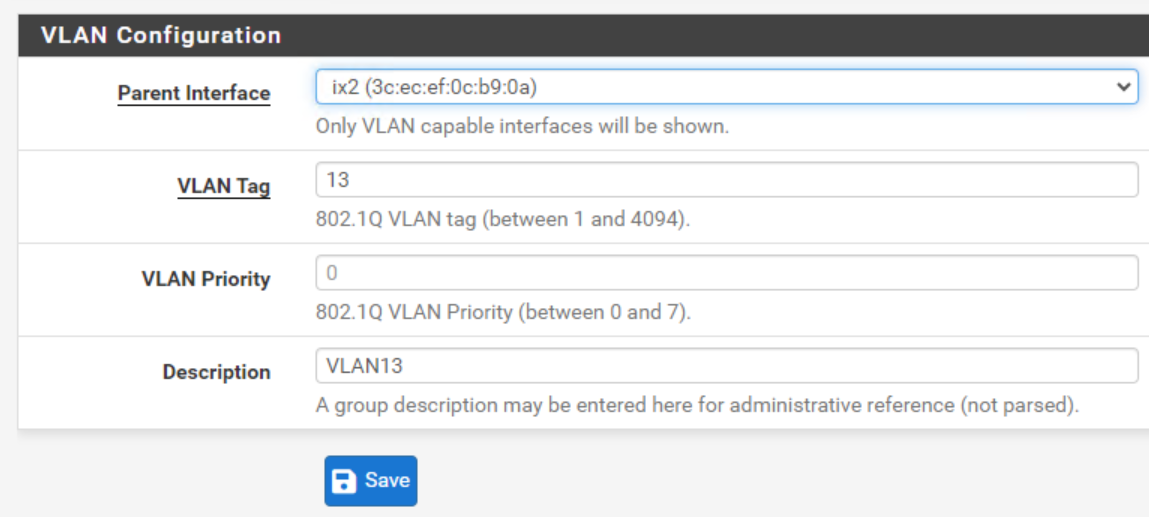
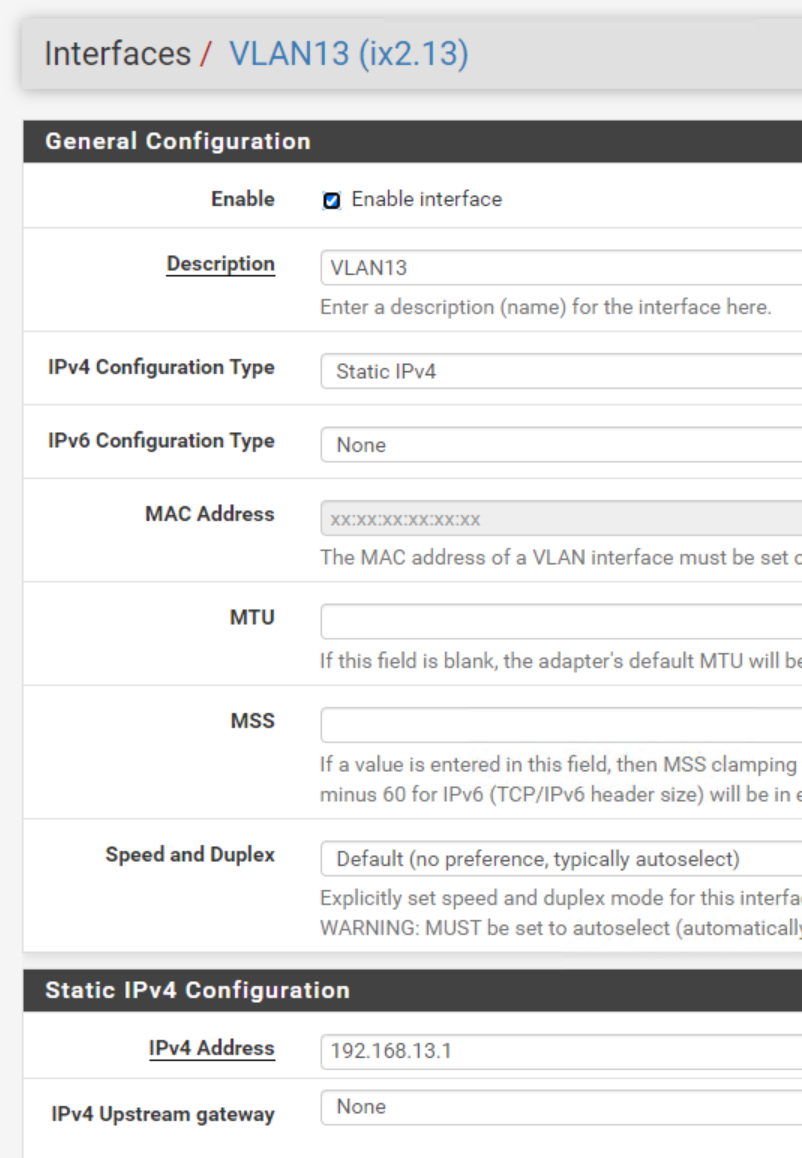
The client is using static IP.
I have checked the trunk more than once :-)
I'm able to ping from the pfsense to the client (verified the ARP with the expected remote mac). I'm also able to ping between other clients. And also accessing the webgui of the pfsense.
Https seem to be allowed to pass. -
@ricbjo said in New Vlan and Default deny rule IPv4:
I'm able to ping from the pfsense to the client (verified the ARP with the expected remote mac). I'm also able to ping between other clients. And also accessing the webgui of the pfsense.
Https seem to be allowed to pass.Based on your screenshot of your firewall rules, no traffic is matching any of the rules which indicates to me a misconfiguration somewhere.
You are saying you are able to ping your gateway - 192.168.13.1?Can you also post your client IPv4 information
-
@michmoor Hi, No I cannot ping from the client to the gateway(pfsense) but from the pfsense I can ping the clients.
I agree, something is most likely misconfigured. But I haven't been able to find where.
Looking at the arp cache, the client finds the pfsense and the firewall log say Deny:

Client ipconfig
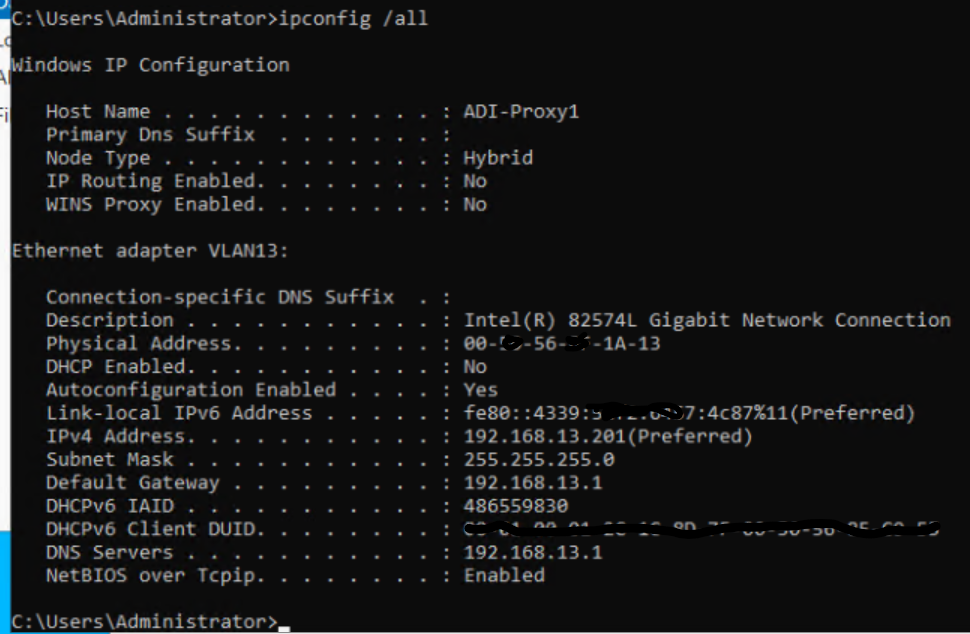
-
@ricbjo Do you have floating rules? This seems like a floating rule being hit which would make sense as thats first and then interface rules.
-
-
@michmoor Only the pfBlock and it doesn't seem to have any traffic logged on them. I haven't really started using it.
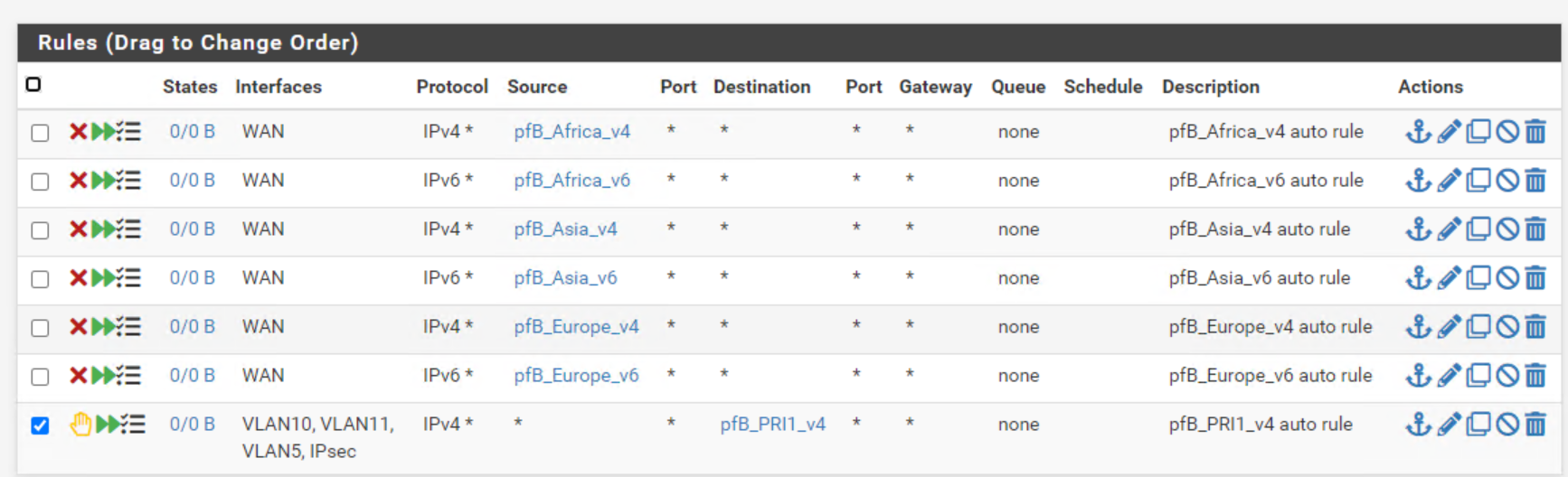
I'm planning on doing a restart.
-
@SteveITS Did a reload, no errors and no difference. And one of my issues is that incoming ISAKMP and that was one of the earlier things I set up.
-
@SteveITS Sorry, there was an error:
-There were error(s) loading the rules: /tmp/rules.debug:35: cannot define table bogonsv6: Cannot allocate memory - The line in question reads [35]: table <bogonsv6> persist file "/etc/bogonsv6"Sincde I don't use IPv6 (wich I think this relates to) I ignored it.
-
@ricbjo
Very strange. Can we try a system reload ? -
@ricbjo In the pfSense system options on the firewall page ensure your max table size is at least 2 million and raise as necessary.
-
Thanks so much!!
I updated to the 2.7.1 version with reboot and now it seem to be working. :-) -
@SteveITS For future reference... I also had to raise the max table size and that made the rule loading error go away. Also when adding new rules today, they were not applied until I had raised the max table size and reloaded.