rate limiting / policer
-
Hello everyone,
Looking to see if my application here is sound when applying limiters.
Part of DoS protection i need to liit icmp and tcp traffic to the firewall. Basically rate limiting.
Ive configured limiters to help me with this. Each limiters is set to 1Mbps
I then created a floating rule and have it match on all interfaces except WAN in the In Direction. My thinking is that to protect the and test this rule from the inside first before I apply it to the WAN side as we do allow icmp. Is this correct so far?
My next step is i would of apply a limiter to each of my different service ports - I am in Fintech so ports need to be open from the Internet but we do tighten it down to whitelist source IPs of clients.
So for example clients hitting my NAT at x.x.x.x/32 on port 1840 will be limited to 20Mbps.
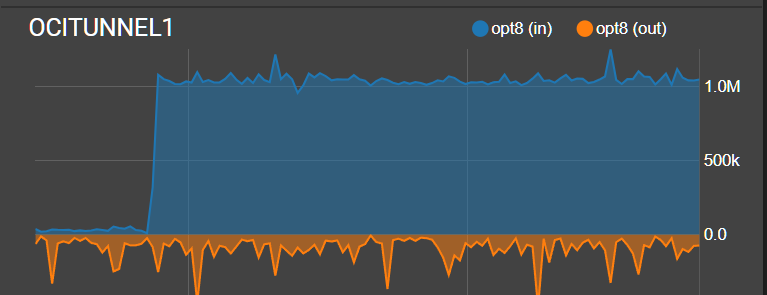
Does of any this seem reasonable or doable? Do I have the Floating Rules direction accurate? I dont think it matters to much as the 1Mbps ICMP limit is the same regardless of direction.edit: using hping3 on my Ubuntu box i can validate that the 1Mbps icmp flood protection i put in is working.
-
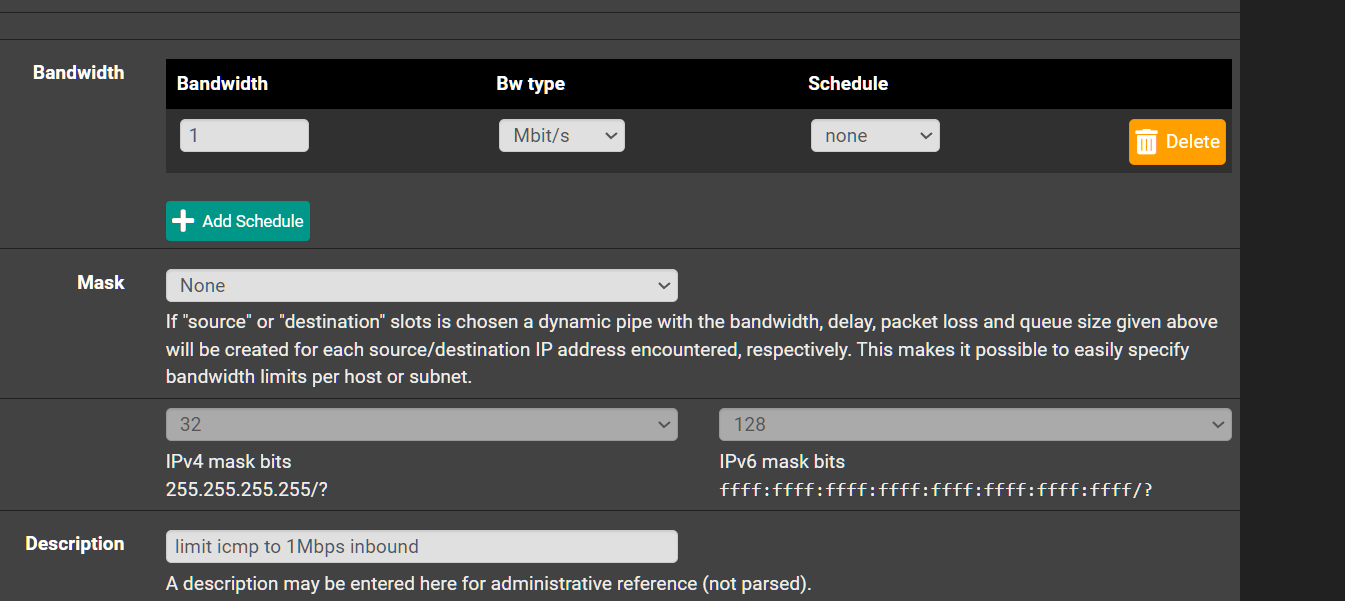
Should I use a Mask??
-
@michmoor Inbound I’m not terribly effective at DoS because the traffic has already filled your pipe before it gets to pfSense. Is it necessary to respond to pings at all?
A mask can be used to have multiple queues/limits, so for example each LAN IP is limited to 1 Mbps, as opposed to all sharing 1 Mbps.
-
@SteveITS
The goal is not to prevent an ddos attack rather to limit resource consumption of the firewall. For pings it still needs to create state in the table as it’s allowed. CPU utilization will be high so just reducing the impact and still making the firewall usable is the goal. It’s not just about WAN. We have LAN traversing other interfaces such as DMZ. Firewall can’t function if it’s hammered on the WAN. .Plus policing it to a low level gives us enough time to investigate and work with our upstream -
I would probably try to set actual states limits on the rule rather than using Limiters. So set a maximum number of states and/or maximum source IPs:
https://docs.netgate.com/pfsense/en/latest/firewall/configure.html#maximum-state-entries-this-rule-can-create
That wouldn't prevent a single host sending a ping flood though. -
@stephenw10
Is there a way to see what the CPS is for a rule? -
@michmoor I was just going to write that
 .
.re: floating rules direction, look at the state table. It's not always immediately obvious, for instance "download from web server" is an inbound connection on port 443 and the reply uses that, it's not an outbound direction.
What I usually do is run the wizard, pick one of high/medium/low and then copy and/or change the IPs to fit the actual needs. (or in our case now I just copy from another router).
re: rule data, the firewall rule will have the number of currently open states in the left column.
-
@SteveITS said in rate limiting / policer:
What I usually do is run the wizard, pick one of high/medium/low an
You mean the Shaper wizard, right?
@SteveITS said in rate limiting / policer:
re: rule data, the firewall rule will have the number of currently open states in the left column.
Yep thats a good way to figure out the open connections now. Give maybe a 10% overhead
-
The shaping wizard only creates AltQ based shaping. You could add Limiters to the match rules it creates but it probably doesn't make much sense for this if you're Limiters at least.
-
@michmoor said in rate limiting / policer:
Shaper wizard
Yeah sorry, low on coffee. Same general idea though...
LAN outbound to *:443 limit 10 Mbps is one pipe.
LAN outbound to *:443 limit 10 Mbps with a mask of /32 is one 10 Mbps pipe per device.
"When a limiter is set for Source Address or Destination Address, the pipe bandwidth limit will be applied on a per-IP address basis or a subnet basis, depending on the masking bits, using the direction chosen in the masking."