Authentication fails when multiple different ldap source (server, bind user and users database) are configured
-
Hello everyone,
I'm looking for feedback about bug #15060
This is my scenario:- brand new pfSense+ system deployed as AWS AMI (AMI ID: ami-0e1a56989ef6d9eb2, AMI Name: pfSense-plus-ec2-23.09-RELEASE-amd64 23-d6a66a49-ceec-4a27-ad5b-ea8a3eb55b15) with singe ENI and a EIP
- 2 different ldap source configured in 2 different Authentication Servers:
- Authentication Server #1 is an AWS Managed Microsoft AD, a NLB with a TLS Listener with certificate signed by our internal CA is configured in order to get LDAPS (see this AWS blog post for details)
- Authentication Server #2 is the Okta LDAP interface of our preview tenant
- LDAPS is in place for both Authentication Servers
- Search scope, Authentication containers, Bind credentials, User naming attribute and Group Object Class differ between the 2 Authentication Servers
Steps to reproduce the issue:
- configure Authentication Server #1
- Authentication Server #1 configuration successfully tested with Diagnostic > Authentication
- configure Authentication Server #2
- Authentication Server #2 configuration successfully tested with Diagnostic > Authentication
- testing again Authentication Server #1 with Diagnostic > Authentication will fail with error "Could not bind to LDAP server Authentication Server #1"
- delete Authentication Server #2
- testing again Authentication Server #1 with Diagnostic -> Authentication will succeed
The issue is reboot resistant.
I suspect the following
- pfSense+ system is somewhere messing up Bind Credentials and/or Certificate validation
- issue is agnostic to database engine
I'm unable to run test without TLS/SSL configuration because of the scenario: could anyone reproduce the issue, maybe without LDAPS configuration also in order to understand the root cause?
Thanks
-
Update: I run Packet capture and it seems a random failure on CA verification on both Authentication Server:

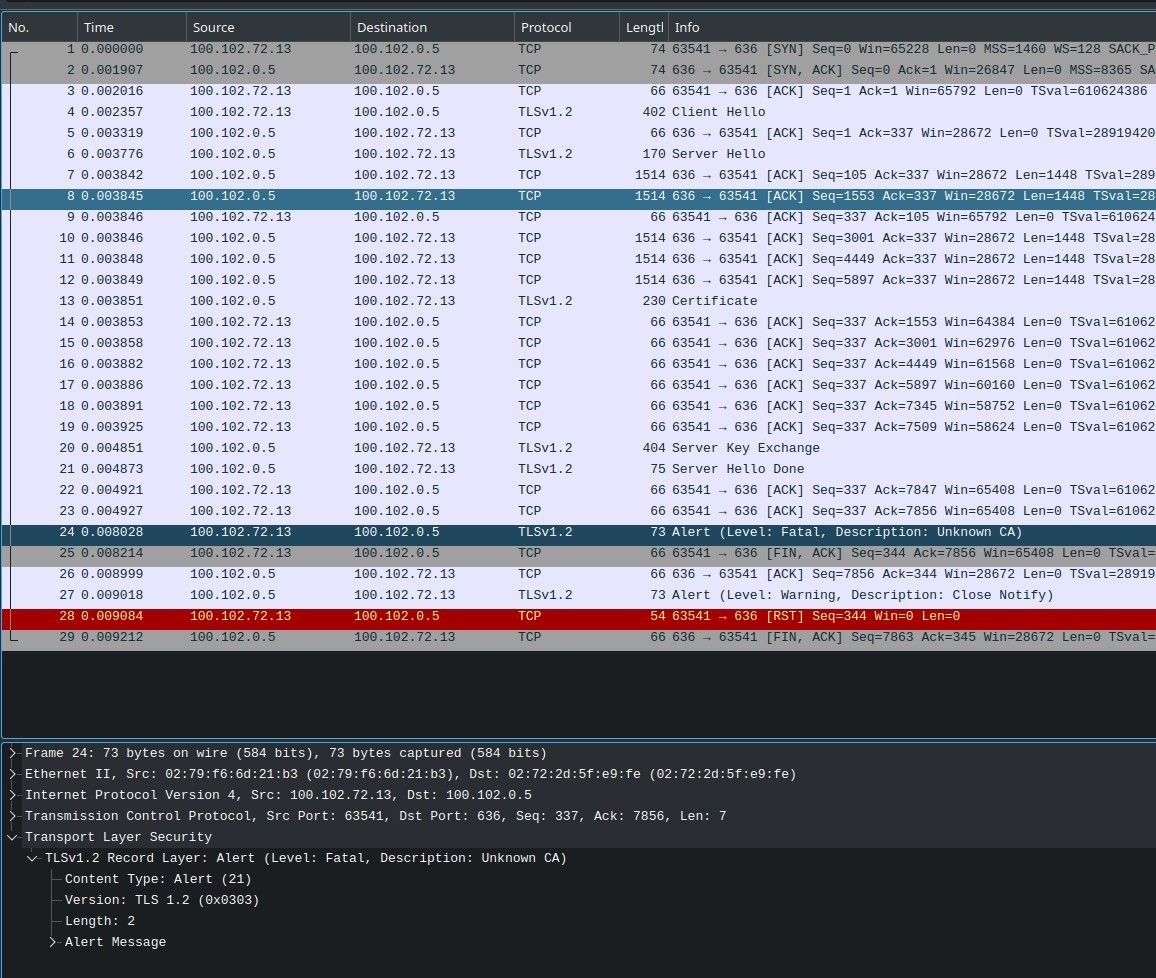
-
Can we assume each of them works correctly if the other is disabled?
-
@stephenw10 I didn't find any options in System/User Manager/Authentication Servers to keep them both configured but one enabled and one disabled.
I confirm that they both work if there is only one configured at time
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.