DNS seems to be down
-
Hello,
After a recent reinstallation, I set in System -> General Setup -> 6 DNS's servers (Quad9, Cloudflare, Google) Only IPv4, not the IPv6 ones (For now), the IPv6 ones are set in the RA server.
In Services -> DHCP/v6 Server I have nothing set, it takes itself from the general (I think).The problem is the following, during a "Leak Test" it does not find any DNS server or it finds my own public IP. (I will attach pictures below)
What settings did I make wrong that it no longer works? At first it went without problems...


-
@root1ng bit of side note here, using multiple dns that don't provide the same results can lead to problematic situations.
When you list multiple NS like that you really have no idea which one might be used at any given time.. Your first one there 9.9.9.11 for sure is doing security filtering
https://www.quad9.net/support/faq/
Secure IPv4: 9.9.9.11 Provides: Security blocklistWhile your bottom ones there for googledns do not.. Or even if all the ones you list do some sort of filtering - is it the same filtering?
So if a non filtering NS is asked and resolves something that you might want to be blocked, that answer is now cached and anything on your network asking for that would get the cached response vs a filtered response.
If you want to use remote dns.. they should all respond the same - if you want filtering, only use from one service since its unlikely they all do the same exact filtering. If your not wanting filtering, don't include NS that do filtering.
To your leak.. Did you setup unbound to forward.. Placing NS in the general tab are really only for pfsense itself use.. Unless you setup unbound to forward.. So if a client asks pfsense (unbound) for dns it would just resolve - which yeah its going to show the IP unbound did the resolving from. if you want to hide your IP in a dns leak sort of test, you have to be forwarding.
And really the only thing pfsense itself would need dns for is check for updates, and grab packages available.. Or if you say click resolve on something in the firewall list for example. Also keep in mind that if pfsense does fall back to NS listed there, its not going to be doing dot, it would just be a in the clear query.. If you want to leverage dot in your dns, you need to be forwarding..
-
@johnpoz said in DNS seems to be down:
@root1ng bit of side note here, using multiple dns that don't provide the same results can lead to problematic situations.
When you list multiple NS like that you really have no idea which one might be used at any given time.. Your first one there 9.9.9.11 for sure is doing security filtering
https://www.quad9.net/support/faq/
Secure IPv4: 9.9.9.11 Provides: Security blocklistWhile your bottom ones there for googledns do not.. Or even if all the ones you list do some sort of filtering - is it the same filtering?
So if a non filtering NS is asked and resolves something that you might want to be blocked, that answer is now cached and anything on your network asking for that would get the cached response vs a filtered response.
If you want to use remote dns.. they should all respond the same - if you want filtering, only use from one service since its unlikely they all do the same exact filtering. If your not wanting filtering, don't include NS that do filtering.
To your leak.. Did you setup unbound to forward.. Placing NS in the general tab are really only for pfsense itself use.. Unless you setup unbound to forward.. So if a client asks pfsense (unbound) for dns it would just resolve - which yeah its going to show the IP unbound did the resolving from. if you want to hide your IP in a dns leak sort of test, you have to be forwarding.
And really the only thing pfsense itself would need dns for is check for updates, and grab packages available.. Or if you say click resolve on something in the firewall list for example. Also keep in mind that if pfsense does fall back to NS listed there, its not going to be doing dot, it would just be a in the clear query.. If you want to leverage dot in your dns, you need to be forwarding..
I know the difference between them and if I can use more than one at the same time, why not?
DNS Resolver is activated from the beginning and I didn't go to it, but I can't do it with DNS Forward, could you help me what and how to set it? Let's say that in this case I will only use 9.9.9.11 to understand how things are.
That is, if you could tell me what and where to set the optimal settings. -
@root1ng said in DNS seems to be down:
if I can use more than one at the same time, why not?
I thought I pretty much went over why its not a good idea to use different servers that might answer different based on filtering. You for sure can use any you want.. Just understand that filtering may or may not work.. One time you ask for something should be filtered and it is, some time later you ask for that same thing again and its not.. Seems pretty problematic to me - either I want filtering to work, or I don't want filtering.. Not sure I would pretty much leave it up to random chance if filtering works or doesn't work based upon who I forwarded dns to at any given time..
@root1ng said in DNS seems to be down:
but I can't do it with DNS Forward
What can't you do with a forward? Are you wanting to use dot? Or in the clear - its quite possible what your forwarding too doesn't do dot, or only does dot, etc. You have different servers in there.. I am not sure which ones of those support dot or not off the top of my head, etc.
@root1ng said in DNS seems to be down:
where to set the optimal settings
That is easy, pretty much out of the box - don't click on anything.. Out of the box just resolves, and this for most use cases should be optimal.. When you resolve dns would have to be down for the whole planet for it to fail.. When you forward - where you forward is down and you have no dns.
But if your going to forward, I would pick one service to forward too.. So you don't have issues with filtered or not filtered or filtered in a different way. if your going to forward I would disable dnssec - where you forward to is either going to be doing dnssec anyway or its not.. You telling unbound to do dnssec is more than likely just cause issue.
-
@johnpoz said in DNS seems to be down:
@root1ng said in DNS seems to be down:
if I can use more than one at the same time, why not?
I thought I pretty much went over why its not a good idea to use different servers that might answer different based on filtering. You for sure can use any you want.. Just understand that filtering may or may not work.. One time you ask for something should be filtered and it is, some time later you ask for that same thing again and its not.. Seems pretty problematic to me - either I want filtering to work, or I don't want filtering.. Not sure I would pretty much leave it up to random chance if filtering works or doesn't work based upon who I forwarded dns to at any given time..
@root1ng said in DNS seems to be down:
but I can't do it with DNS Forward
What can't you do with a forward? Are you wanting to use dot? Or in the clear - its quite possible what your forwarding too doesn't do dot, or only does dot, etc. You have different servers in there.. I am not sure which ones of those support dot or not off the top of my head, etc.
@root1ng said in DNS seems to be down:
where to set the optimal settings
That is easy, pretty much out of the box - don't click on anything.. Out of the box just resolves, and this for most use cases should be optimal.. When you resolve dns would have to be down for the whole planet for it to fail.. When you forward - where you forward is down and you have no dns.
But if your going to forward, I would pick one service to forward too.. So you don't have issues with filtered or not filtered or filtered in a different way. if your going to forward I would disable dnssec - where you forward to is either going to be doing dnssec anyway or its not.. You telling unbound to do dnssec is more than likely just cause issue.
Good, so to understand, at the moment how are the settings made, the DNS is more than likely not working because the network with dns set on the LAN ip (x.x.1.1) does not work on all TVs, and since and on devices connected by LAN, my public IP appears as DNS or nothing else, always, something is not working as it should.
I want to use it as follows, 9.9.9.11 + 149.112.112.11 + those for IPv6 I no longer put them here in System -> General + added hostname for DoT (the ones set here are for pfsense, correct?)
And further, I want all the devices (LAN, OPT's, WiFi, etc.) to use them and at the same time through TLS to be the "verification".I don't know what, how I did it, because at first after going through the wizard and setting 9.9.9.11 and 149.112.112.11 it worked fine on all devices... now it doesn't work at all. Something is stuck somewhere.
I don't know if you understand what I want to say and do.
-
@root1ng what are your settings in unbound? Did you set unbound to forward? Again what you set in general setup for dns is not going to be used by unbound unless you tell unbound to forward..
Unless unbound is not running, if its not running then dhcp would hand out what you have in general.. And not that unbound stopped or something. If you set unbound to not be enabled, then dhcp would hand out what you have there vs pfsense IP.. Which I assume is what your x.x.1.1 is (not sure why you think you need to hide an rfc1918 address? 192.168.1.1??
its noted in the docs
https://docs.netgate.com/pfsense/en/latest/services/dhcp/ipv4.html#servers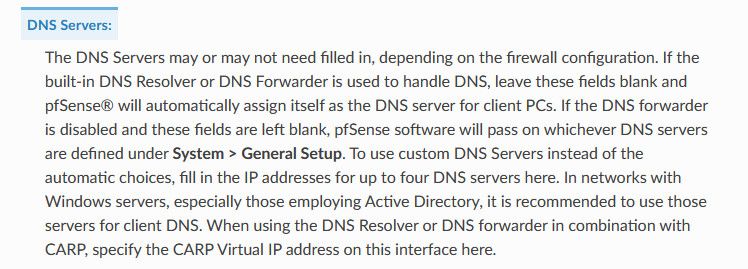
@root1ng said in DNS seems to be down:
And further, I want all the devices (LAN, OPT's, WiFi, etc.) to use them and at the same time through TLS to be the "verification".
Clients are rarely going to support dot, they might do doh.. But I am not aware off the top of my head any sort of clients that actually support dot out of the box sort of thing..
If you want your clients dns to be via dot to some outside service.. Then you need to point your clients to pfsense IP, you need to setup unbound to forward using tls (dot)..
And to be honest these days their is no guarantee your clients will even pay attention to your settings.. There are more and more things doing doh without any user intervention or acknowledgment. And its harder and harder to block because it hides in your normal ssl (443) traffic..
-
@johnpoz said in DNS seems to be down:
@root1ng what are your settings in unbound? Did you set unbound to forward? Again what you set in general setup for dns is not going to be used by unbound unless you tell unbound to forward..
Unless unbound is not running, if its not running then dhcp would hand out what you have in general.. And not that unbound stopped or something. If you set unbound to not be enabled, then dhcp would hand out what you have there vs pfsense IP.. Which I assume is what your x.x.1.1 is (not sure why you think you need to hide an rfc1918 address? 192.168.1.1??
its noted in the docs
https://docs.netgate.com/pfsense/en/latest/services/dhcp/ipv4.html#servers
@root1ng said in DNS seems to be down:
And further, I want all the devices (LAN, OPT's, WiFi, etc.) to use them and at the same time through TLS to be the "verification".
Clients are rarely going to support dot, they might do doh.. But I am not aware off the top of my head any sort of clients that actually support dot out of the box sort of thing..
If you want your clients dns to be via dot to some outside service.. Then you need to point your clients to pfsense IP, you need to setup unbound to forward using tls (dot)..
And to be honest these days their is no guarantee your clients will even pay attention to your settings.. There are more and more things doing doh without any user intervention or acknowledgment. And its harder and harder to block because it hides in your normal ssl (443) traffic..
DNS Resolver is started from the first boot, it has no setting made by me, DNS Forwarder is turned off (I think from the beginning), what should be set for them?
Edit: With DNS Resolver disabled, the internet doesn't work at all apparently :))
-
@root1ng said in DNS seems to be down:
Edit: With DNS Resolver disabled, the internet doesn't work at all apparently :))
Well duh... Did your clients update their dhcp after you disabled it? Did you restart dhcp server so it would know that unbound was disabled.. And hand the clients the IPs from the general tab..
If your are not forwarding in unbound, then no the dns you put in general would not be used by clients asking unbound for www.something.com..
If you want to forward to dns using dot (tls) then set it up to do that.
https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html
-
@johnpoz said in DNS seems to be down:
@root1ng said in DNS seems to be down:
Edit: With DNS Resolver disabled, the internet doesn't work at all apparently :))
Well duh... Did your clients update their dhcp after you disabled it? Did you restart dhcp server so it would know that unbound was disabled.. And hand the clients the IPs from the general tab..
If your are not forwarding in unbound, then no the dns you put in general would not be used by clients asking unbound for www.something.com..
If you want to forward to dns using dot (tls) then set it up to do that.
https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html
Yes, I forgot to restart the DHCP server after modifying the DNS resolver, it seems to work, yes. But I would still use TLS, so I will try to figure it out.
I saw that the DNS for IPv4 and he took them from System -> General, the IPv6 ones are also set but he did not associate them (the dhcpv6 server is not running, because I don't need it) why?
-
@root1ng said in DNS seems to be down:
But I would still use TLS
No its not going to use dot if you just hand a client some NS ip from your general tab via dhcp.
-
@johnpoz said in DNS seems to be down:
@root1ng said in DNS seems to be down:
But I would still use TLS
No its not going to use dot if you just hand a client some NS ip from your general tab via dhcp.
No, I will set DNS over TLS by what you told me above
-
I did it, everything works as it should now, thank you!