Port forwarding securely
-
Have a standard install of PFsense nothing fancy, 4 /24 networks each with a few PCs connected what do not talk to each other.
Need to port forward 3 ports for TCP/UDP to one of those /24 networks only.Googling has made me terrified of port forwarding so I asK:
How can I do this securely and mitigate as much risk to my home network possible?
If doing this how do I prevent attacks on the router management itself?
Is it imperative to lock down SSH before port forwarding ?
PFblocker/Snort of any use to help keep secure while port forwarding?Please let me know, thanks.
-
@srytryagn What are you forwarding to, a web server?
Forwarding port 443 for instance has nothing to do with SSH. If you mean, you need to forward an SSH port then just realize anything you expose to the Internet will have login attempts. Consider fail2ban on the server, or a VPN.
If you know the remote IP you can use that (or an alias) as the source in the NAT rule so only forward for selected IPs.
If you can limit access by country pfBlocker can be used to create country aliases...On the IPv4 tab use a Geo alias and then use that as the NAT rule source:
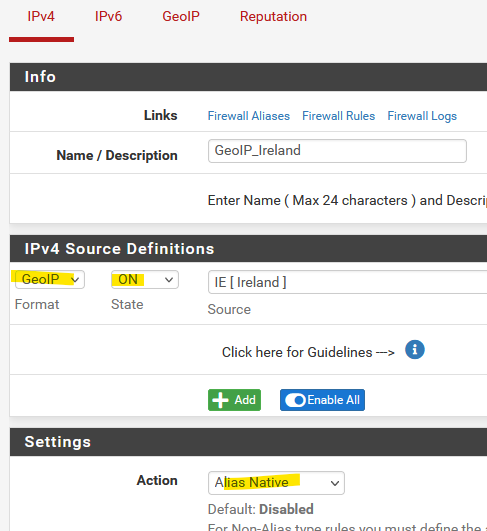
And yes you can use Suricata/Snort to protect a server...set it up on LAN, start out by not blocking so you can review your alerts. I recommend Suricata over Snort since it sounds like Snort may not exist forever on pfSense.
-
@srytryagn Thanks for helping they are ports in the 30k range and are for any TCP/UDP.
I want to reflect the open port traffic ONLY to one of my networks but NOT the others.
I will not know the IPs connecting, so I guess a VPN solution will not work either.I am concerned because it is my home network in particular
- My router getting reverse shelled into or infected with malware
- My PC connected to the reflected network having bad things happen to it
- The other networks having "bad things" also happen
The reason I ask is if I am probed by bots, since scans will show open ports, I want to make sure there is nothing vulnerable, which is why I ask about if necessary to lockdown SSH in the router or in that one PC which traffic is reflected to, or potentially all my host pcs.
I have little experience with Suricata and pfblocker, but if they help I can run them. If the PC requires ufw rules I can apply them.
Let me know what the best solution would be inline with my comments above please.
-
@srytryagn Unless you're forwarding ports to your router I don't see how that's a concern.
So the ports are forwarding for an SSH login? On one hand, it's up to your server(s) to maintain security. On the other hand if you're allowing others to log in to a server then you'd either need to trust them or limit their access. You can block access from that server to pfSense and/or your LAN network by firewall rules on that interface. Something like:
- allow from Network2 to This Firewall port 53 (for DNS)
- reject from Network2 to This Firewall
- reject from Network2 to LAN Subnets
- allow Network2 to any (allows to Internet and any other pfSense interface)
Of course you can't limit access from that server to any other device in Network2 because that traffic doesn't go through the router.
-
@srytryagn said in Port forwarding securely:
I will not know the IPs connecting, so I guess a VPN solution will not work either.
Why is that? You mean you don't know the people connecting, and you can not give them the login details for your vpn? What IP they come from for a vpn connection has nothing to do with vpn working.
Not sure what ports your wanting to open, but doesn't matter if you forward X to say 192.168.1.100.. And lets say that .100 box gets compromised and some bad actor gets full control over it. That does not mean he can access everything else on your network or the pfsense gui.
As long as the rules on pfsense prevent that .100 box from going to your other networks, or even its own gui the bad actor/software would be limited to what he can talk to on the 192.168.1 network..
This is why network segmentation is an advantage.. You could also just put this box you want to allow access from the internet to its own network. So no other devices on that network.. And if does need to talk to something else on your network you could limit that to specific ports and Ips of these other devices. So again even if the .100 box is compromised it would have limited access to what you allow on the rest of your network..
Also in reduction of attack surface thing - as shown by StevITS it would be possible to limit who can use your port forward to the country or countries you would have visitors from.. Even if you have no idea what actual IP or network they would be coming from. For example I expose my plex to the public internet via a port forward. But only IPs from the US and Morocco (have family there currently) can access it. Now this doesn't really make it more secure - but it does reduce the overall attack surface a bit..