Squid and ACLs
-
Hello fellow Netgate community members,
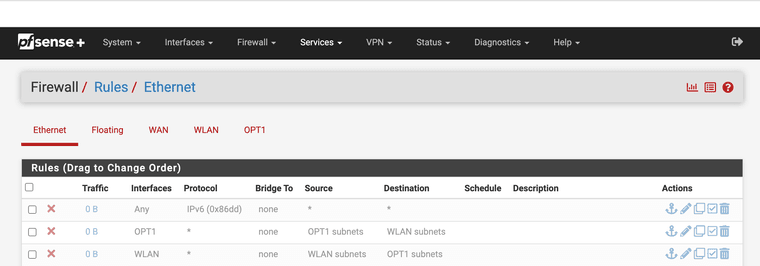
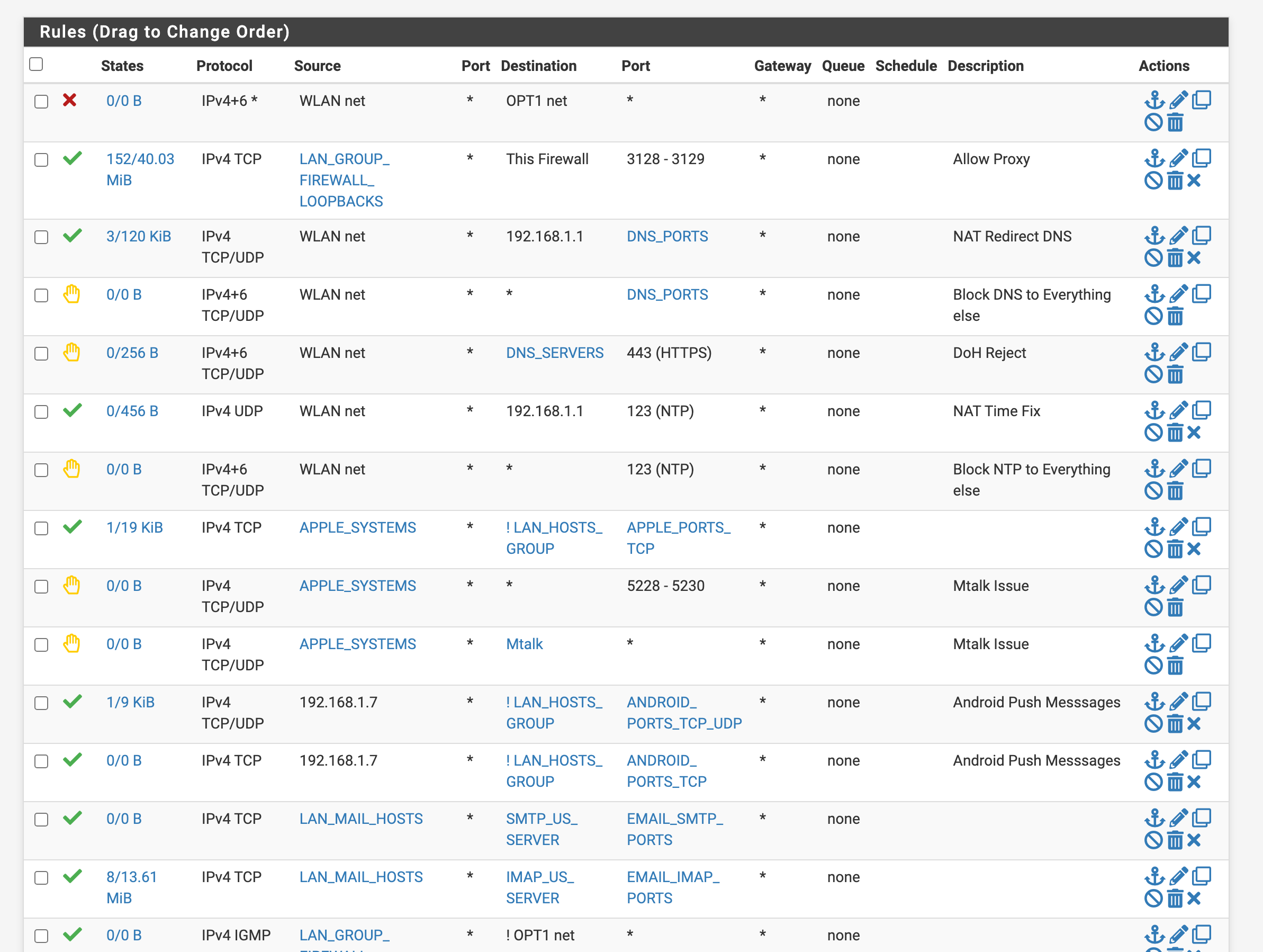
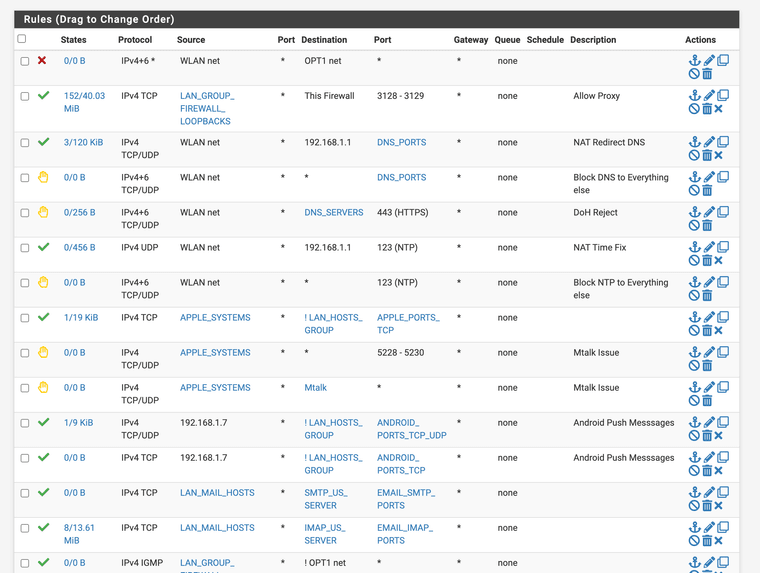
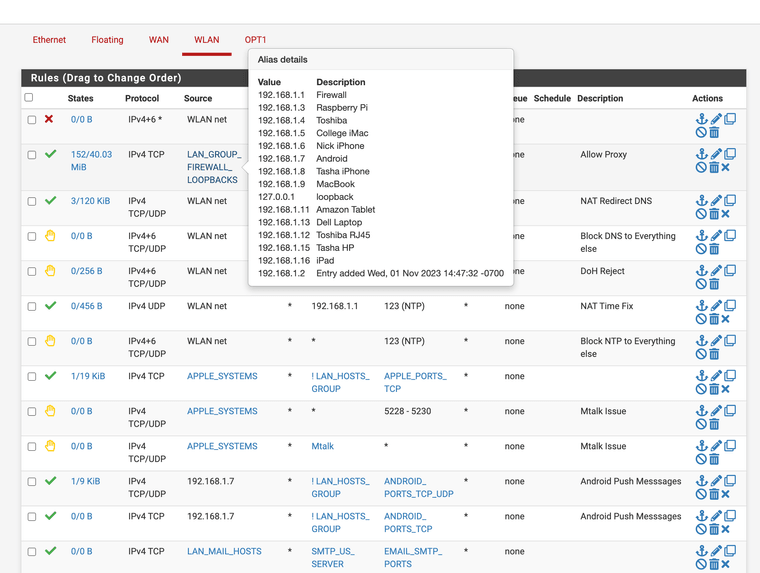
Can you help?I am running Squid, in my firewall logs I see oftentimes a default block from the firewall 192.168.1.1:3128 to lan side devices like 192.168.1.5. Should I implement a rule to approve 192.168.1.1:3128 to all lan subnet or all lan devices the default block rules still show items and the rule never shows states established. This has gone on for years. This default block is a Netgate rule I didn't create it or can see it. I have no issues with it's functionality with the proxy working and access with rules below however on a update to 23.09.01 on fresh firmware and a new SSD, I loose GUI access until I use pfctl -d. What is wrong with my rules? I do not want to implement a any any rule that defeats the purpose of a firewall. Can anyone that has worked with Squid on loopback and interface let me know? Opt1 does not use Squid only WLAN.
I have a separate SSD for 23.09.01 and my config locks me out.
What rule should be on the access control lists to resolve this? TCP-A is always blocked here.
Should I set the Squid package to bypass private addresses? If I do that I can't monitor the loop backs for issues.
Please also do not respond with Squid is depreciated. I am never going to remove it or even upgrade pfSense past a version that does not support it.
This is only asking about access control lists issues for the version that still supports the package.
-
@JonathanLee said in Squid and ACLs:
am never going to remove it or even upgrade pfSense past a version that does not support it.
Do you have the System_Patches package installed? I know there were some security updates in 23.09.1 that i 'think' have been pushed in the sysetm patches package.
-
@michmoor last night on the 23.09.01 SSD it showed no updates only my NTP custom patches. I removed the patches and same issue I had to do pfctl -d to access GUI. It's weird, I also had my old separators in a row listed on opt1 I deleted them all but same result, pfctl -d is the only way I could access GUI. TAC support suggests I add a any any rule to see if that fixes it, I will play with it more tonight when I can do change it without interrupting everything.
I sent them the system status file and they keep seeing the 192.168.1.1:3128 getting blocked to lan side the TCP-A logs for the default Netgate block rule. Like my old post remember that? They said it's weird it works for 23.05.01 but my config file doesn't for 23.09.01. I can access GUI until I put the config down.
It's fused the technology to my ARM processor but when my config DNA gets pushed down I am locked out.
-
@JonathanLee I just want to make sure you at least get the security patches on your 23.05 instance considering you are staying on that version going forward.
-
@michmoor yes I have every patch on 23.05.01 it's a huge list
-
I think the problem is the first rule.
You are getting proxied to the GUI.If you are using transparent proxy, bypass the destination IP of the firewall.
If you are using explicit proxy, bypass the IP of the firewall or the entire network 192.168.1.0/24, you can do it through the browser (do not proxy for these networks), or through a .pac file.So, when you use pfctl -d, the first rule gets disabled and you restore access.
-
@mcury I have it manually set to bypass proxy for 192.168.1.1 on lan side devices. I did have that issue until I did that but I never added that to the bypass it on the poxy itself inside the firewall. Thanks I didn't think about that, I will test tonight. What's weird why does this work for 23.05.01?
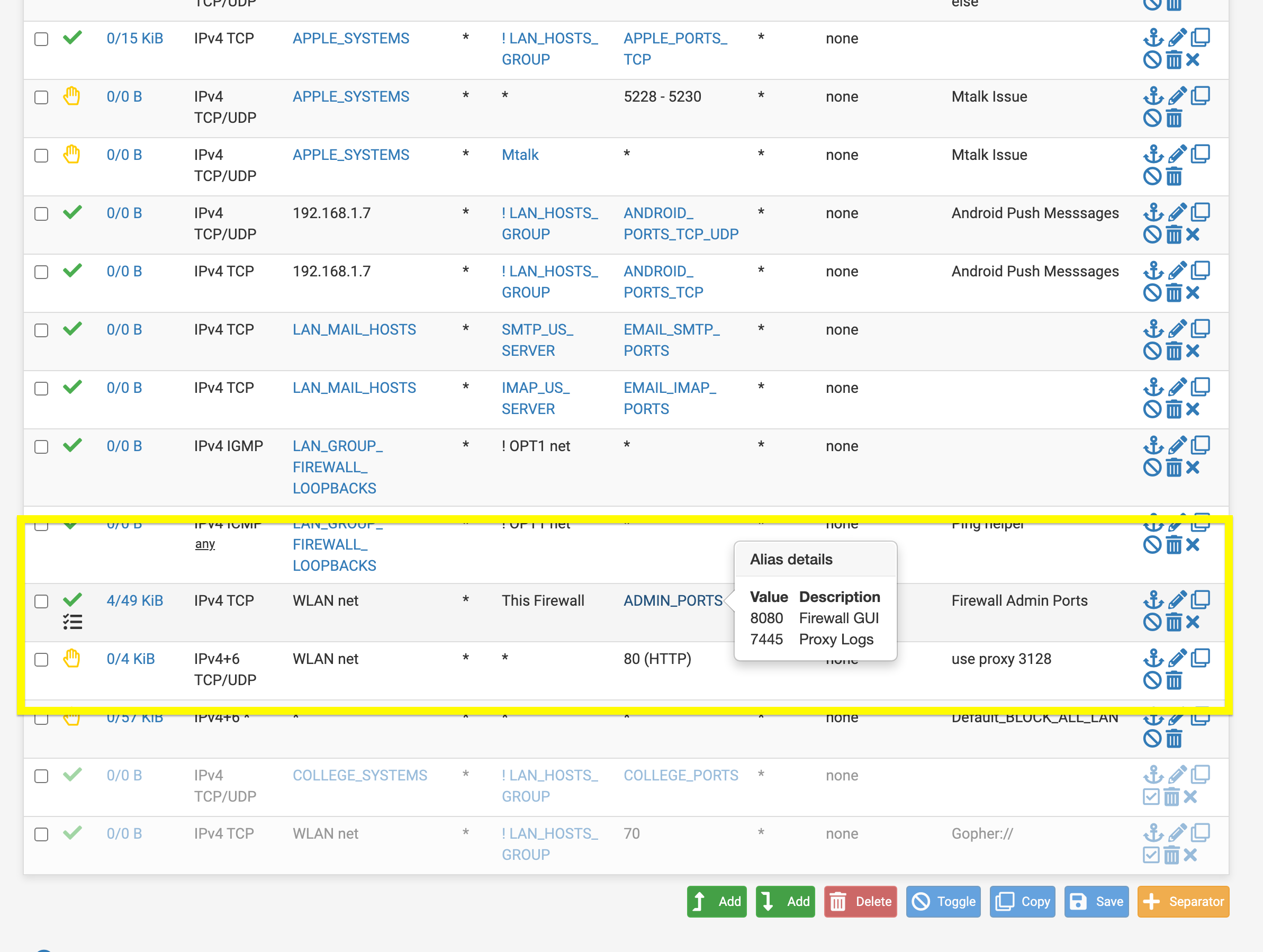
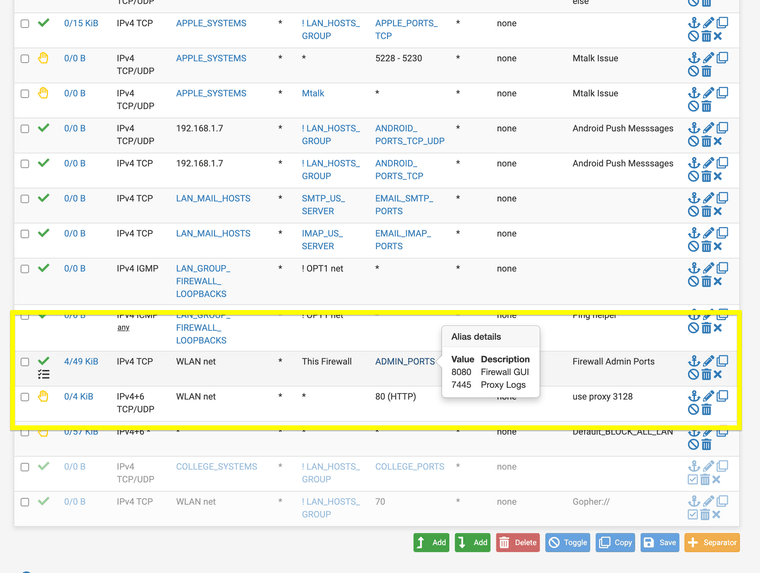
TAC wants me to move my 8080 rule to the top next tonight.
I have to swap out my "everything bagel" 🥯 SSD and put the 23.09.01 SSD back in to test it.
Everything bagel is the software where everything works perfectly for everyone in our house.
-
@JonathanLee said in Squid and ACLs:
Thanks I didn't think about that
I'm 99% sure that it will solve that issue.
@JonathanLee said in Squid and ACLs:
What's weird why does this work for 23.05.01?
I really can't tell, but what I can say is that I got into similar problems in the past.
I'm searching for the topic here, but it is very very old.. It was jimp who gave me the tip to fix that at that time.. -
@JonathanLee said in Squid and ACLs:
TAC wants me to move my 8080 rule to the top next tonight.
That is a good idea, but if I'm right, that alone won't help.
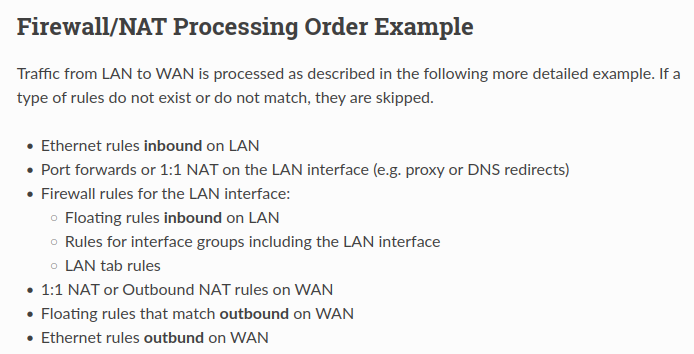
As I see it, you are getting intercepted by the proxy while going to the pfsense's GUI.Also note that NAT is processed first than a firewall rule in the pipeline.. So, if I'm right, moving that rule won't solve the problem..
Edit:
Found the link, it wasn't jimp, memory failed me..
https://forum.netgate.com/topic/110072/squid-dnsbl-problemEdit2 :
Oh, it would be easier to just change the firewall management port, choose any port that is not being used by any services in the firewall and not being intercepted by the transparent proxy.
-
@mcury thanks for the information
-
@mcury is port 8080 used by something else? My GUI is currently set to port 8080.
-
@JonathanLee said in Squid and ACLs:
@mcury is port 8080 used by something else? My GUI is currently set to port 8080.
No, not by default.
But some websites use that port, so it is usual to see users include that port in the allowed ports in the Squid settings.If its not there, then, I don't think this is the problem.
Just to be clear, my suspicious is that the NAT that transparent proxy creates is intercepting that port when you are accessing the GUI, and sending it to the proxy 3128.
-
@mcury I got it. It should also work to add bypass 192.168.1.1:8080 on the Squid bypass settings right

-
@JonathanLee said in Squid and ACLs:
It should also work to add bypass 192.168.1.1:8080 on the Squid bypass settings right

Yes, just bypass connections to destination 192.168.1.1.
Usually, most of the times if not always, you don't want to proxy connections to local networks, so I would bypass everything to:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16As far as I remember, you said a few weeks ago when we were trying to fix your Nintendo Switch problem, that you use both modes, transparent and explicit.
So, you need to make sure that you bypass these networks for both methods.
For transparent mode, you need to include those networks in Squid configuration, or if you created the NAT manually, include those networks there, you can use that reverse destination alias as previously mentioned in that thread.
For explicit mode, you would need to set it in the browser settings, or through the PAC file.
-
Thanks I got the PAC file working. I bet 23.05.01 had some default Netgate proxy rules that 23.09 doesn't include.
-
@JonathanLee said in Squid and ACLs:
Thanks I got the PAC file working. I bet 23.05.01 had some default Netgate proxy rules that 23.09 doesn't include.
hm..
 could be but I don't think so.
could be but I don't think so. -
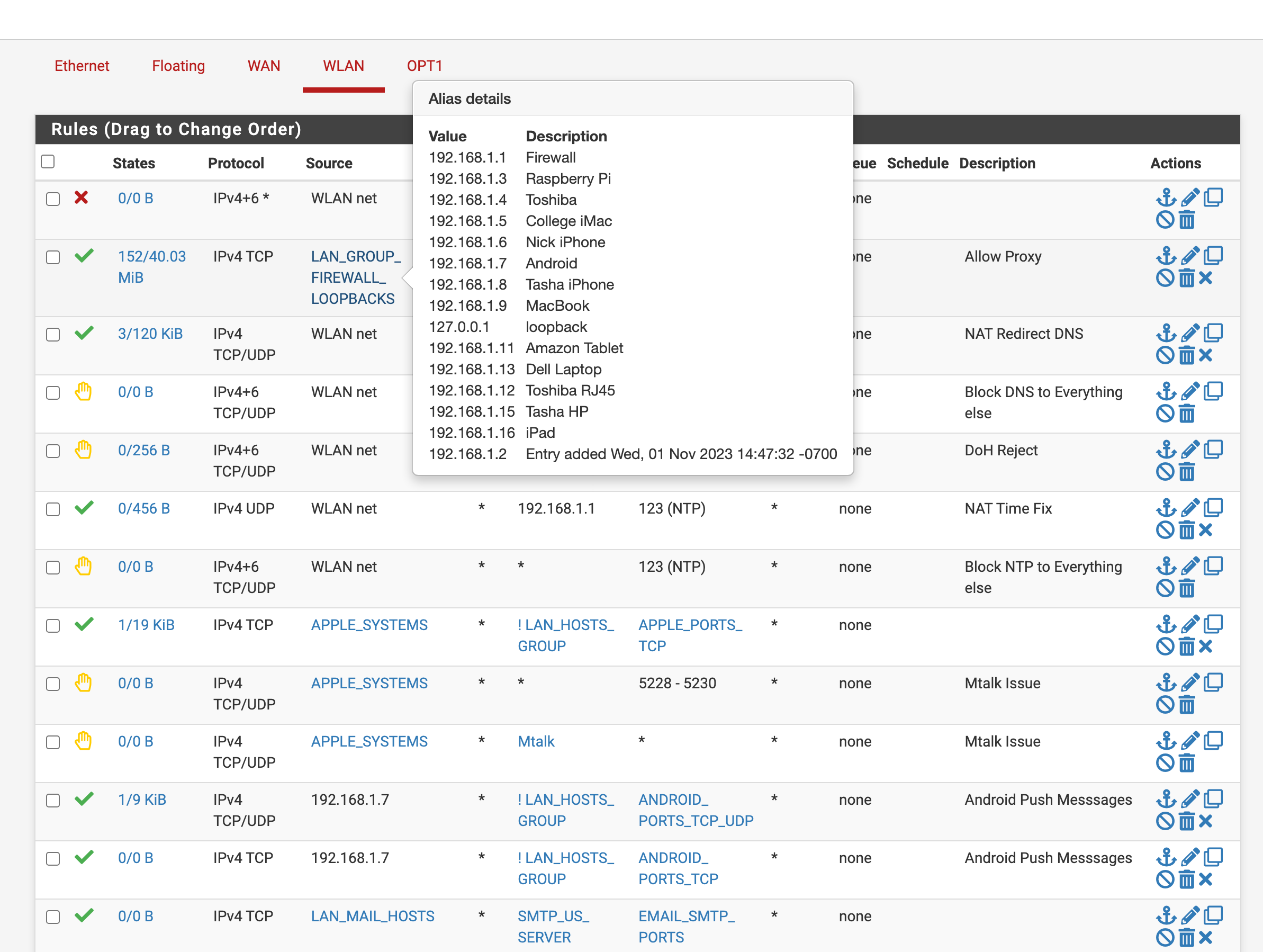
It was this old separators that were deleted however still listed in the 23.05.01 config.xml file.
It mixed up every rule on the config.xml side and left it looking correct on the GUI side. I just deleted them and it fixed it for my 23.09.01
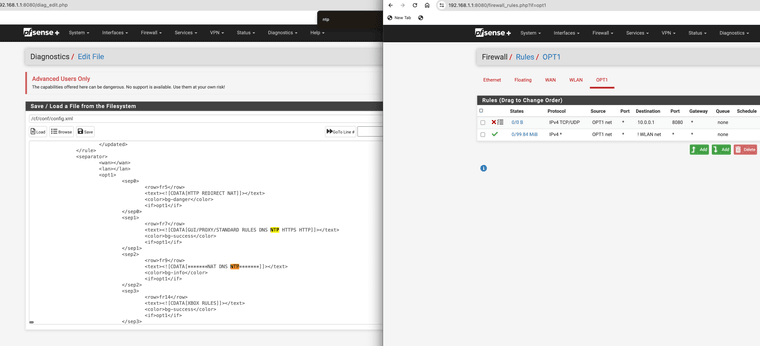
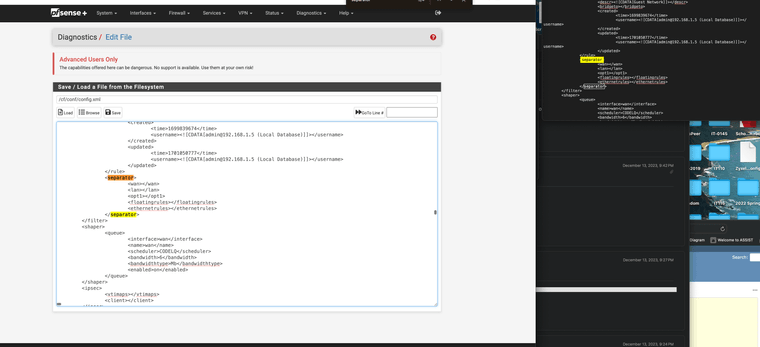
-
@JonathanLee said in Squid and ACLs:
It was this old separators that were deleted however still listed in the 23.05.01 config.xml file.
It mixed up every rule on the config.xml side and left it looking correct on the GUI side. I just deleted them and it fixed it for my 23.09.01


Oh, that certainly wasn't a easy shot, good work =)
-
@mcury I also had to disable some ethernet rules that all the sudden showed a lot of activity