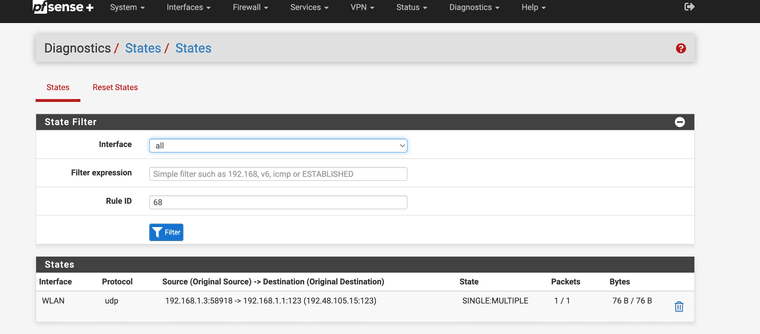
NTP issues NAT bypassed?
-
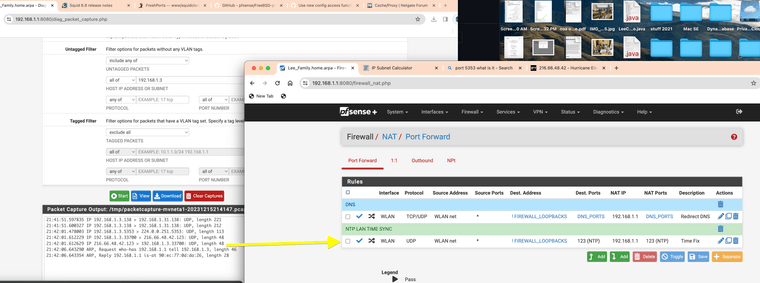
(NTP accessing other server outside of firewall bypassing rules)How is this possible? I have no open ports for anything but the NAT port 123 redirect.
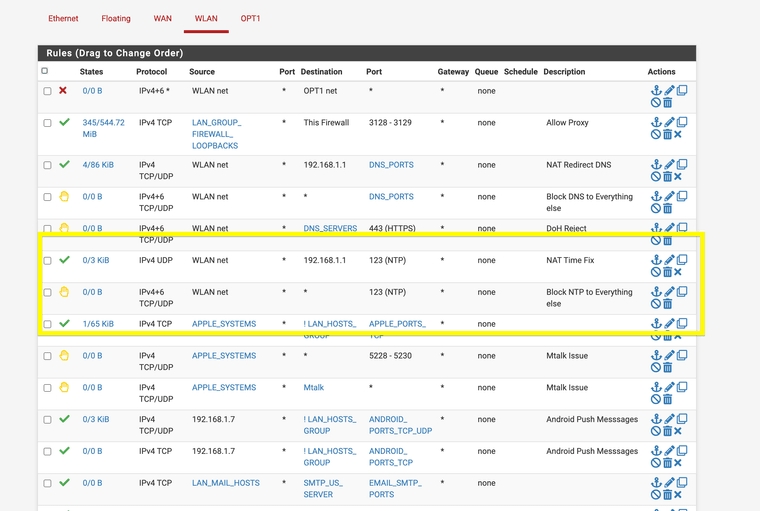
(rules that only allow access to port 123 with NAT)Is the access control lists not working anymore?
-
-
@JonathanLee
What makes you think, that NTP is bypassed?To detect this, you would have to sniff the traffic on the WAN interface, not on the inside interface.
-
@viragomann It is the 192.168.1.3 it should be getting an NTP from 192.168.1.1 inside the firewall right?
-
@JonathanLee
Your internal device is requesting NTP from a public IP. pfSense nats it to a local IP and translates the source in the respond packet back to the origin public IP, which the client was requesting.
This is necessary that the client accepts the response. But I guess, nothing goes to the outside here.