SSL certs handling and HAproxy
-
Yes the destination on the pass rule should be the VIP. It would work fine using 'This Firewall' but best practice there is to make a rule as precise as possible.
-
Can someone share the specifics of this rule?
I'll test the single server first, and if that works, I'll then tackle the three web servers I've talked about.
-
It should looks something like:
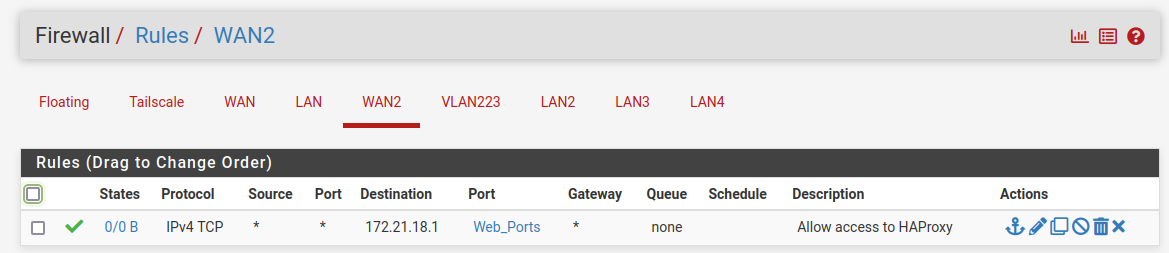
Where 172.21.18.1 is the VIP.
-
There is nothing in the rule creation page that offers any way of selecting a VIP.
Do I have to create another alias, just so I can use 'other'? -
Just select 'Address or Alias' and enter the IP.
-
This post is deleted! -
So here's my WAN rule;
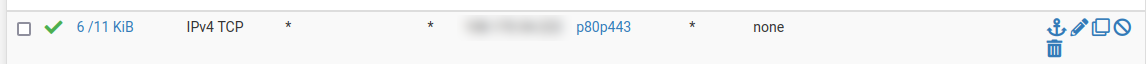
I seem to be reaching the firewall now but not the site. I say that because testing the SSL cert is now showing the days left of the cert on pfsense instead of the one on the web server.
I'm getting a
"Browser detected a potential security threat and did not continue to www.aaa.com because this website requires a secure connection"
No traffic is getting to the web server. I'm guessing that's the mess in the haproxy setup now. -
It's because by default the pfSense GUI listens on those ports. If you have not already you will need to change the port that runs on:
https://docs.netgate.com/pfsense/en/latest/config/advanced-admin.html#tcp-portAnd disable the webgui redirect rule there if you want to be able to connect on port 80 to HAProxy too.
-
I don't use standard ports for the GUI so that's not a problem.
I do however, have those standard ports in use on the primary IP which is why I'm using VIPs for web servers.Maybe I'm missing something in what you're saying?
-
BTW, I do now see Byes in and out in the haproxy status page for that web server.
Which also seems to confirm that the load balancing has never actually worked, even if some part of it definitely does. -
I might be close now.
I'm using a remote browser and I'm getting this;
has a security policy called HTTP Strict Transport Security (HSTS), which means that Tor Browser can only connect to it securely.
You can’t add an exception to visit this site.
The issue is most likely with the website, and there is nothing you can do to resolve it.I've disabled HSTS on the web server but still getting the warning.
Maybe now I have to look at the server but no one has answered some of the questions I've asked about the server.I've asked about how SSL should be set up on the server and especially if it's one that has virtualhosts.
Some talk about a self signed cert and some don't.
-
Can you connect using https? You are connecting to HAProxy so policy changes would have to be there. If you wanted to allow http connections which you probably don't. More likely you would add a redircet rule in HAProxy to redirect http requests to https.
But I would get it working using https directly first. -
Just for giggles, I swapped out the rule from NAT to WAN for the web servers and again, the traffic to each web server just died.

I had to re-anable the NAT rule again.Back to the single server I was testing, no, I cannot connect to it using http or https.
-
Isn't that a node without HAProxy though? Without anything to proxy the traffic you'd need the NAT to reach the servers.
So what error do you see when you try to connect through HAProxy?
Do you see firewall states opened for that traffic?
-
@stephenw10 said in SSL certs handling and HAproxy:
Isn't that a node without HAProxy though? Without anything to proxy the traffic you'd need the NAT to reach the servers.
Sorry, I'm not following this. A node without proxy?
I was told here that the NAT rule was the wrong one for haproxy, that I should create a wan rule which I did.
I've read that one I used a wan rule instead, the proxy would just know to handle traffic for that public IP.
The traffic keeps coming in, even while I'm messing around with these changes.So what error do you see when you try to connect through HAProxy?
I don't see any errors as I would post them. The traffic to the web servers simply stops, It doesn't get to the web servers once I'm using a wan rule.
Do you see firewall states opened for that traffic?
I didn't check so I'll do that next time I can disrupt the traffic.
-
@lewis said in SSL certs handling and HAproxy:
Just for giggles, I swapped out the rule from NAT to WAN for the web servers and again, the traffic to each web server just died.
I had to re-anable the NAT rule again.I assumed you did that on some other pfSense instance where HAProxy is not present?
To use HAProxy you must have firewall pass rules on WAN and you must not have any NAT rules.
@lewis said in SSL certs handling and HAproxy:
I don't see any errors as I would post them.
So the browser just timesout?
-
Some things are getting mixed up in the thread. That's why I suggested working on this one stand alone server first. Once I see how that is working, that will help me to understand how things need to be set up.
First, I'm only working on one firewall, not multiples in trying to solve this.
I have two different things going on.
1: I thought haproxy was handling the three web servers I've talked about and we've now found that this was not the case.
These servers have their own SSL certificates, not using ACME on the firewall.
When I swap from a NAT rule to a WAN rule, all traffic to all three servers stop.2: I've set up a test web server, just one server, to see if I can use the SSL certificate on pfsense instead of the web server, to learn about doing this using pfsense, ACME and haproxy.
In this case, I have ACME set up with a valid cert on pfsense and wanted to learn about this by having pfsense handle the ssl cert for the web server.
So far, nothing has worked. In this case, I've also shared images of the rules, setup etc.
The best I've been able to get in terms of reaching the web service is getting an error in the browser, complaining about HSTS which is odd because HSTS is disabled on the web server.This seems to imply that things are set up ok on pfsense but something on the web server is not.
-
That implies that you're hitting HAProxy with http and it's only configured for https.
Try connecting to to with https. Do you see the expected states opened in the firewall. Do you see the expected cert on the client?
-
@lewis
about the port he was talking about this settings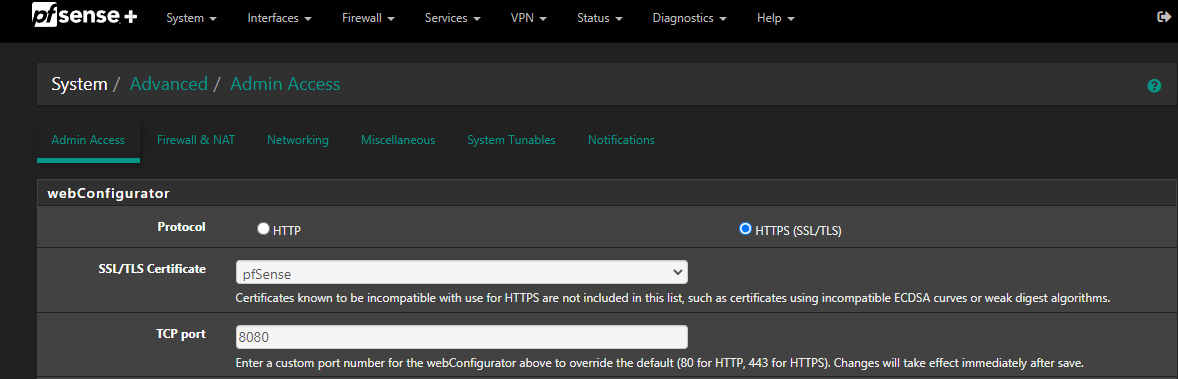
the default is 80 or 443 for https, if you don't chage this port the pfsense gui take control of the traffic instead of haproxy
if you saw the pfsense cert you are near the solution, change that setting and you should see the cert of haproxy
-
One thing I mentioned and will again is that the pfsense GUI is set to a custom port without an SSL certificate.
Nothing will hit the pfsense GUI other than if someone got the correct port set in the Advanced/Admin Access/TCP port settings.
That port is also blocked and allowed to only one or two IPs so no one can get to the GUI.Unless I'm missing something again?
Also, I double checked and there are no services on port 80 or 443 for the primary pfsense IP, all services are using ports with their own VIPs.