Recipe for Pfsense becoming a static router for a /28 subnet
-
@frater I don´t understand now what you want. It is the same result when you do it with VIPs.
-
I can't bridge classless interfaces.
Tell me which interfaces I need to bridge given my last scenario!
I can create a logical interface with the name bridge on igc3 and give it a bogus IP IP 172.20.1.1/30
I can then bridge it with PPPPOE0 and connect foreign devices to igc3.If it works, it works.
I just can't test it now as I only have remote connections with pfsenses in that scenario and it's all production.And where do I tell it to route all traffic from those subnets directed to 20.0.0.1 to the Internet?
-
@frater said in Recipe for Pfsense becoming a static router for a /28 subnet:
igc1 -> lan1 192.168.188.1/24 (use NAT rules to use WAN IP 20.0.0.1)
igc2 -> lan2 192.168.168.1/24 (use NAT rules to use WAN IP 20.0.0.2)Rereading this again, you do want NAT for the internal interface but want it to use 20.0.0.2 instead of the default 20.0.0.1? (you wrote "do not want to use network translation" originally). That would be the outbound NAT mentioned in the first reply. Add the IPs as VIPs on the WAN/PPPOE connection, and add an outbound NAT rule to translate using that IP. Here's an outbound rule translating a 192.168.x.x network to a VIP Alias on WAN:
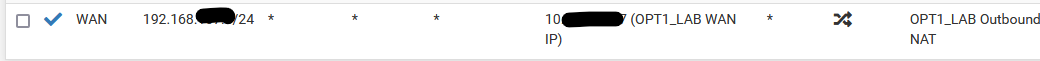
-
Rereading this again, you do want NAT for the internal interface but want it to use 20.0.0.2 instead of the default 20.0.0.1?No I do not want NAT.
I just gave that example to make clear that THAT scenario was no problem for me and I implemented quite often.
The 20.0.0.3~6 for foreign devices is my only problem.I want static routing
Even a simple Fritz!Box can do it.
Given a /30 subnet I have 2 IP's.
A Fritz!Box does NAT on 1 IP and a Cisco that is connected to the Fritz!Box has the 2nd IP and routes everything through the Fritz!Box. -
@frater No, surely not! The FB use one address and the provider router the other! You must have a GW to send traffic to the provider!
-
Surely YES
the router gets a /30 using PPPoE on a fibre connection
The 2nd IP is for the Cisco.The provider's gateway is outside the /30 network
The Cisco has a static IP on its WAN and has the FB as its gateway.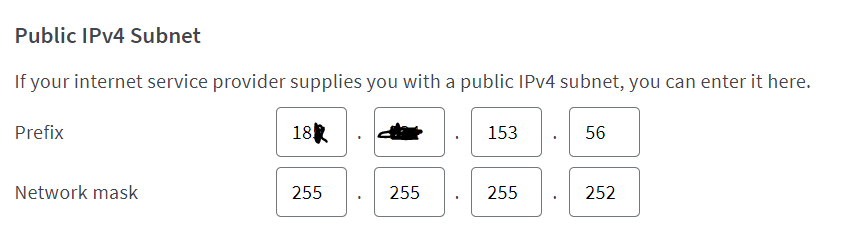
-
@frater Ok, I had a think failure. Sorry for that. But for what you want static routing?
-
In fact I'm not getting a /29 but will be getting a /27 network and I want to give more than 25 companies an Internet connection.
They all want a WAN IP without firewalling.The ISP gives me that subnet through PPPoE.
I will probably do it with a Mikrotik which needs a simple configuration to do this.I was wondering if I can do it with a Pfsense.
I also have a few places where I have a /29 subnet and Pfsense is a central router for a few companies (using VIP's)
I would like to be prepared if a company suddenly wants a WAN-IP and do his own firewalling.
I only have the subnet available on the PPPoE-interface. -
The simplest solution is to call your ISP and tell them "please I want my solution to be routed, not bridged" then they will give you a private network for the WAN side and route your network through that. Most providers can do that. Then you can configure 20.x.x.x on the "LAN side", just disable NAT altogether and you're set.
Otherwise. You should be able to bridge PPPOE and and eth interface and then set an IP address of that network in the bridge interface, then set other IP addresses on your devices with gateway your pfsense.
It sounds similar to what I have with OVH
OVH gives me a /29 and a gateway outside of that subnet.So on my WAN I configure my IP address as a /32, and then I add a route to the gateway (yes that is what I said, and a default) and then a default through the actual gateway
For example, I have:- Network: x.y.z.232/29
- Gateway: x.y.z.254
So I did this:
route add -host x.y.z.254 -iface em0 route add default x.y.z.254It's weird.... but it works
-
@andres-asm as a follow-up, while at the beginning what I did was bridge two virtual ethernet interfaces so I could give my internal VMs public IP addresses, I ended up switching to virtual IPs attached to the wan interface and 1:1 NAT.
But I get it, clients usually don't want to deal with NAT.