Default Gateway & Policy Routing
-
Am i right to assume that the "Default gateway IPv4" setting within System -> Routing should be set to Automatic when trying to configure policy routing via a different gateway?
On a test box, i have it currently set to the WAN (isp) gateway but have noticed that i cannot route specific traffic over a WG tunnel to another pfsense box despite it being set to do so in the local FW rule. Am working remotely so I have not changed the gateway in case the connection drops.
Cheers!
-
@Popolou its possible you had an existing state, if you add a policy based rule by setting the gateway in a firewall rule. You need to make sure the previous states are removed, via either killing them or them timing out on their own before the new pbr rule would take effect.
-
@johnpoz Hi and thanks, yes cleared all states to/from the test IP once a config change is made. I haven't looked into changing the default gateway yet but tests so far always return SYN_SENT:CLOSED on the local side.
-
@Popolou does the state show your going out the gateway you set.. Maybe that gateway can't get to where your going or they are not answering from your source IP.
You don't have to change the default gateway, or change to auto for pbr to work.. I route traffic out a pbr now and then for testing vpn, etc. All that is required is to clear any existing states and then new traffic is routed out the gateway set in the rule.
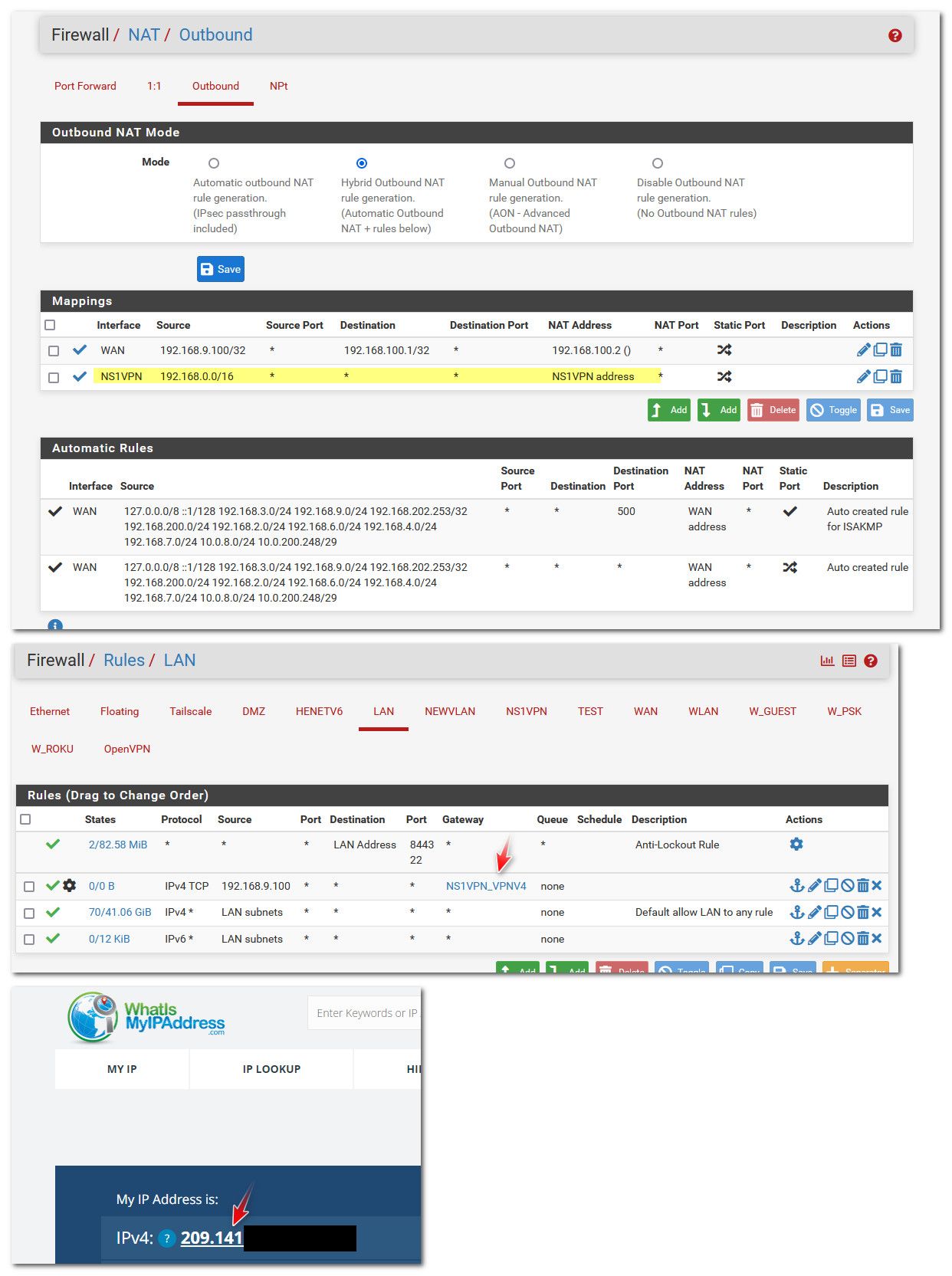
Make sure you have a outbound nat setup for your pbr..
edit: example - just enabled pbr for my PC..
Here is before IP.
You can see my outbound nat, and my new firewall rule.. And my IP changes to the vpn connections ip
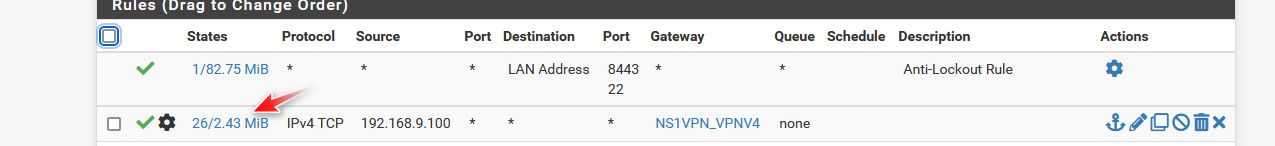
And notice that now that rule is showing traffic and and states.
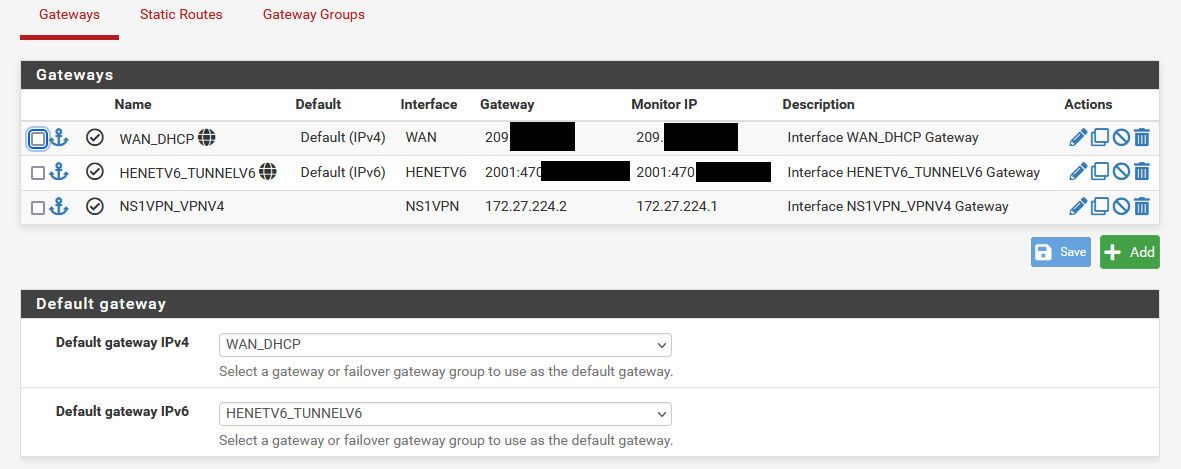
And can see my default gateway is set to my normal wan dhcp gateway
-
@johnpoz Thanks, i believe i'm following the same principle. There is an existing WG tunnel that allows all traffic between sites to pass unhindered (and works). There is also an outbound rule on the remote side to accept/permit traffic to pass through and over its own WAN. There is no outbound rule on the local side to force traffic over the WG tunnel since that already works.
I cannot see much more in the states other than the local side attempting to reach out to the remote network (am seeing packets and states) but there is no evidence on the remote side that it is getting this specific traffic. This leads me to think that there is still a block on the local pfsense instance. Running a pcap and i am seeing retransmissions on the local side but no traffic from that the test client on the remote side.
I'll keep testing!
-
Just to be clear setting the default gateway should not make any difference to policy based traffic. And in fact if you have additional gateways such as those for the WG tunnel you almost certainly want the default set to WAN. Otherwise in automatic it might set the default route to the WG tunnel.
Steve
-
Found some time and took another look at this and discovered that the WG tunnel between the two relevant hosts was missing the allowed IP of 0.0.0.0/0 to route over the WG tunnel to the internet from one WG host to another. A quick fix then...
Frustratingly, i remembered this same issue for another fault from long ago and recalled the key text from the official documentation that "....when sending packets, the list of allowed IPs behaves as a sort of routing table, and when receiving packets, the list of allowed IPs behaves as a sort of access control list." The differences are seldom drawn on in WG 'cheat sheets' but is essential for the routing - i suspect most people blindly following guides assumed it was only to force a default gateway for a WG host.