step-ca private CA with pfSense
-
Hello,
I've recently set up a step-ca server within my home lab. I plan to automate all my certificates within my private network using ACME, but I haven't reached that point. Right now, I'm just manually requesting certs from the CA and installing them for each service. The certs are working correctly as I get the lock icon in my Firefox browser for each https service.
I want to setup pfSense's webGUI and OpenVPN to use certificates from my private step-ca server. My understanding of this process is as follows:
- Install the CA's root fingerprint within the server
- Use certificates issued by the CA within your server
I see that the GUI provides an option to import an existing Certificate Authority. Should this just be my root certificate from my step-ca server?
The configuration instructions for step-ca direct installing the root fingerprint rather than the root certificate. What is the difference between the two? Is there anyway for me to import the root fingerprint into pfSense?
Here is the GUI for importing an existing Certificate Authrotiy into pfSense
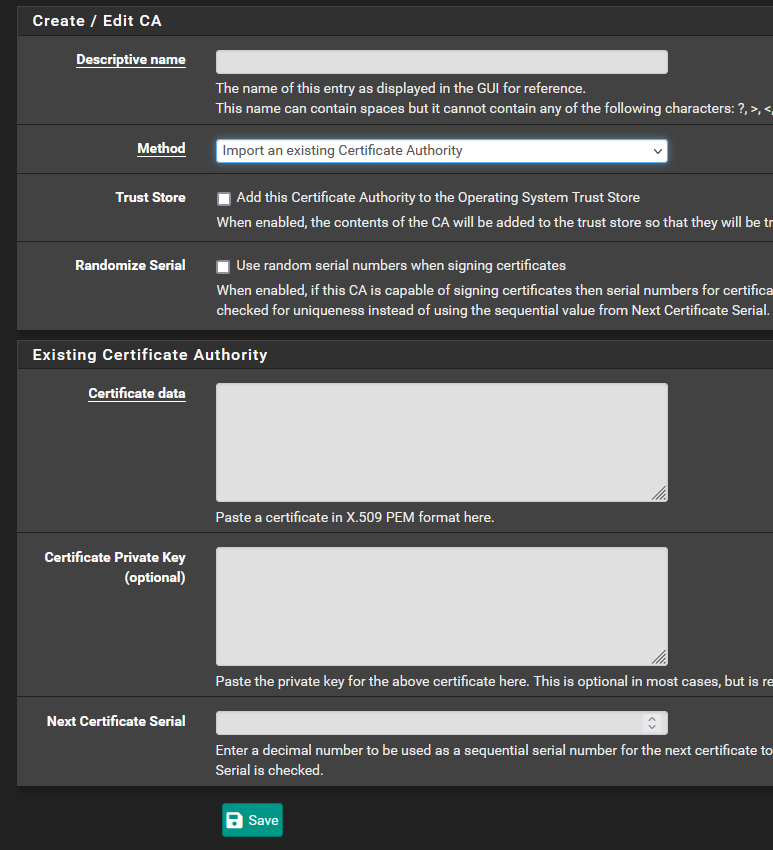
I'm really doing this as more of an educational journey. I'm trying to learn about PKI as i find it rather cool.
How exactly would Certificate Signing Requests fit into my setup?
What exactly is a certificate signing request, and would pfSense signing requests to my CA to keep renewing its certificates? Any information or explanation would be appreciated.
Here is the GUI for creating a Certificate Signing Request
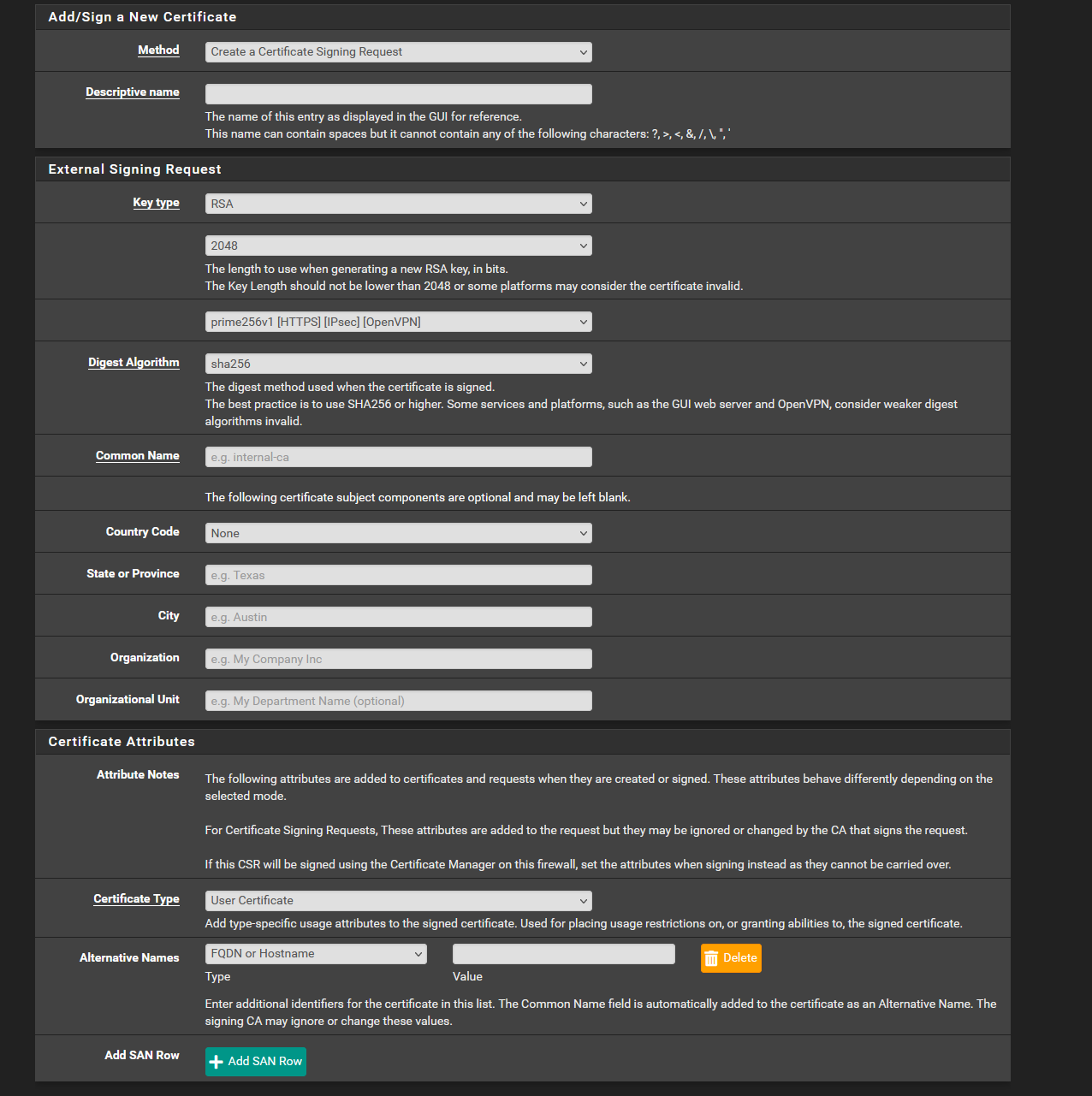
-
You don't need to import the CA for for clients accessing pfSense to see it as valid. That would only be required for pfSense itself to trust other resources it's connecting to.
Additionally if those certs are signed by something globally recognised then pfSense would see them as valid anyway just as firefox does on a client.Consider also that using global root CA signed certs for OpenVPN can actually reduce security. A client will authenticate any server cert signed by that CA. Though it would still fail to connect.
Steve
-
@stephenw10 I still have more questions. I access pfSense through a browser that is on my network. To secure the connection between my browser on my PC and pfSense's webGUI I need to configure a certificate issued by my CA inside pfSense? My browser still has (Error code: SEC_ERROR_UNKNOWN_ISSUER) when I access pfSense's webGUI. This is not a globally recognized CA this is a private CA running within my local network.
https://smallstep.com/certificates/
My current understanding of setting up certificate authentication is as follows:
- Certificate Authority generates the root certificate
- Root certificate or Root fingerprint needs to be upload and installed on each individual server that trusts the CA
- Each server then needs to be issued a certificate from the CA.
- Each service within the server needs to be configured to use that certificate issued by the CA.
- After this if you have the root fingerprint or root certificate installed on your client you will trust all certificates issued by the CA.
I'm still looking for specific advice on configuration.
What is the difference between a root certificate and a root fingerprint? Can I paste my CA's root fingerprint directly into the 'certificate data' field? Then just upload a certificate that my CA issues into pfSense.
How should I handle Certificate Signing Requests in pfSense? After generating a CSR in pfSense, what is the correct process to get it signed by my private CA and correctly installed?
Is having a certificate signed equivalent to being issued a certificate by the CA?