DHCP gateway not reachable once the lease has been given
-
Hi,
I have a weird problem DHCP/VLAN/Firewall.
So on the LAN interface ( igc0 ) I created 3 VLAN ( 10, 50 and 100).
Each VLAN interface have a static IP , then I activated DHCP on each interface ( VLAN10, VLAN50 [ 192.168.50.1 ] and VLAN100 [ 192.168.100.1 ] ).
Finally, I went in the firewall to create a rule for each VLAN interface that let pass any IPv4 packet with any protocol from any source to any destination.So, I stuggled with my switch for a long time but didn't find any issue.
My current test setup :
I'm connected directly to the netgate device with a laptop ( which has 2 VLAN interfaces)Both interfaces are connected and get lease from the dhcp server on netgate device:
nmcli device show vlan50 GENERAL.DEVICE: vlan50 GENERAL.TYPE: vlan GENERAL.HWADDR: 8C:16:45:BC:A8:26 GENERAL.MTU: 1500 GENERAL.STATE: 100 (connected) GENERAL.CONNECTION: VLAN50 GENERAL.CON-PATH: /org/freedesktop/NetworkManager/ActiveConnection/154 IP4.ADDRESS[1]: 192.168.50.2/26 IP4.GATEWAY: 192.168.50.1 IP4.ROUTE[1]: dst = 192.168.50.0/26, nh = 0.0.0.0, mt = 400 IP4.ROUTE[2]: dst = 0.0.0.0/0, nh = 192.168.50.1, mt = 20400 IP4.DNS[1]: 192.168.50.1 IP6.ADDRESS[1]: fe80::8e16:45ff:febc:a826/64 IP6.GATEWAY: -- IP6.ROUTE[1]: dst = fe80::/64, nh = ::, mt = 256nmcli device show vlan100 GENERAL.DEVICE: vlan100 GENERAL.TYPE: vlan GENERAL.HWADDR: 8C:16:45:BC:A8:26 GENERAL.MTU: 1500 GENERAL.STATE: 100 (connected) GENERAL.CONNECTION: VLAN100 GENERAL.CON-PATH: /org/freedesktop/NetworkManager/ActiveConnection/155 IP4.ADDRESS[1]: 192.168.100.2/26 IP4.GATEWAY: 192.168.100.1 IP4.ROUTE[1]: dst = 192.168.100.0/26, nh = 0.0.0.0, mt = 401 IP4.ROUTE[2]: dst = 0.0.0.0/0, nh = 192.168.100.1, mt = 20401 IP4.DNS[1]: 192.168.100.1 IP6.ADDRESS[1]: fe80::8e16:45ff:febc:a826/64 IP6.GATEWAY: -- IP6.ROUTE[1]: dst = fe80::/64, nh = ::, mt = 256now comes my problem.
Although I'm connected and have a dhcp lease on both interface, the IP4 gateway is unreachable ( 192.168.50.1 and 192.168.100.1) ...I must be missing something and I'm out of idea..
Any suggestion is welcome !!!
Thanks !!!
-
@Methraton did you enable block rfc1918 on these interfaces or bogon.. Have seen users do that quite often to be honest, way more than zero times you should see users do that.
Also have seen users create a tcp only rule vs an any rule because it defaults to tcp only when creating a rule.
So you have any floating rules that could be blocking, or new ethernet rules?
Do you see anything logged in pfsense firewall log when you try and ping pfsense IP from the device that got dhcp from pfsense.
-
@johnpoz thanks for the checklist !
So the only rfc1918/bogon rules are only defined on my WAN interface, the VLAN rules are very very open (simplest is to show it here):
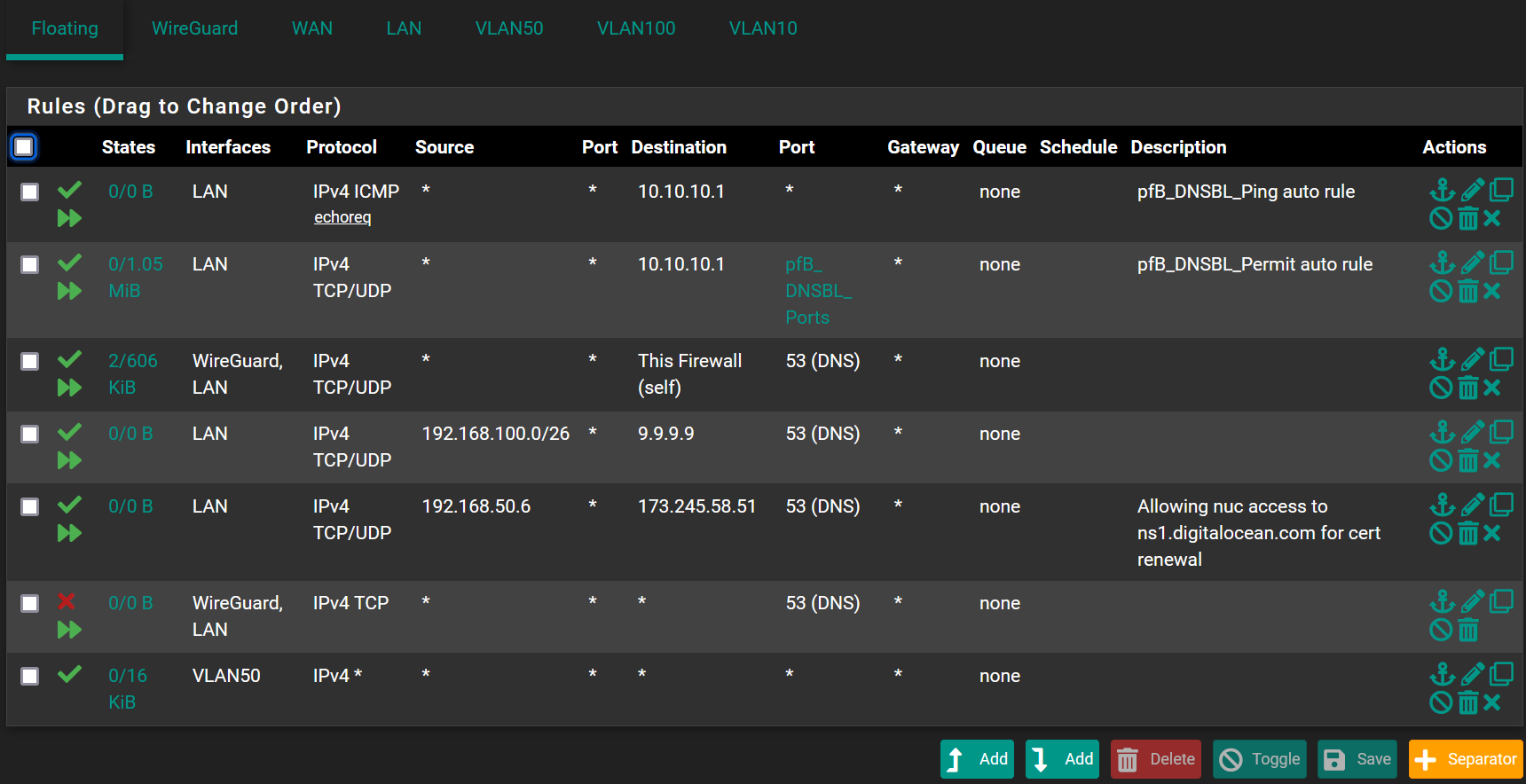
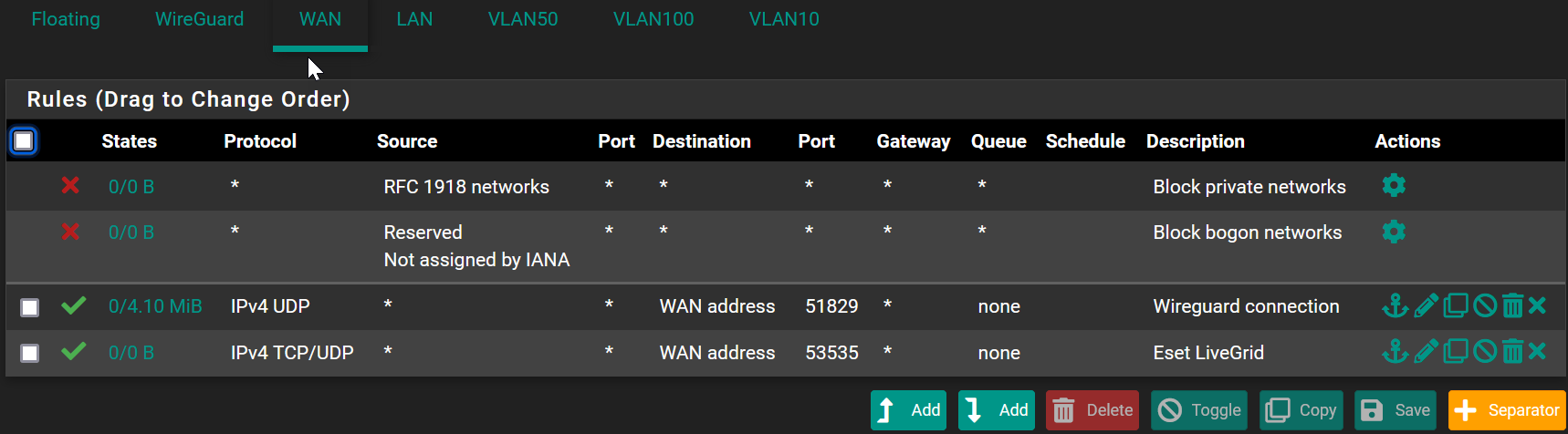
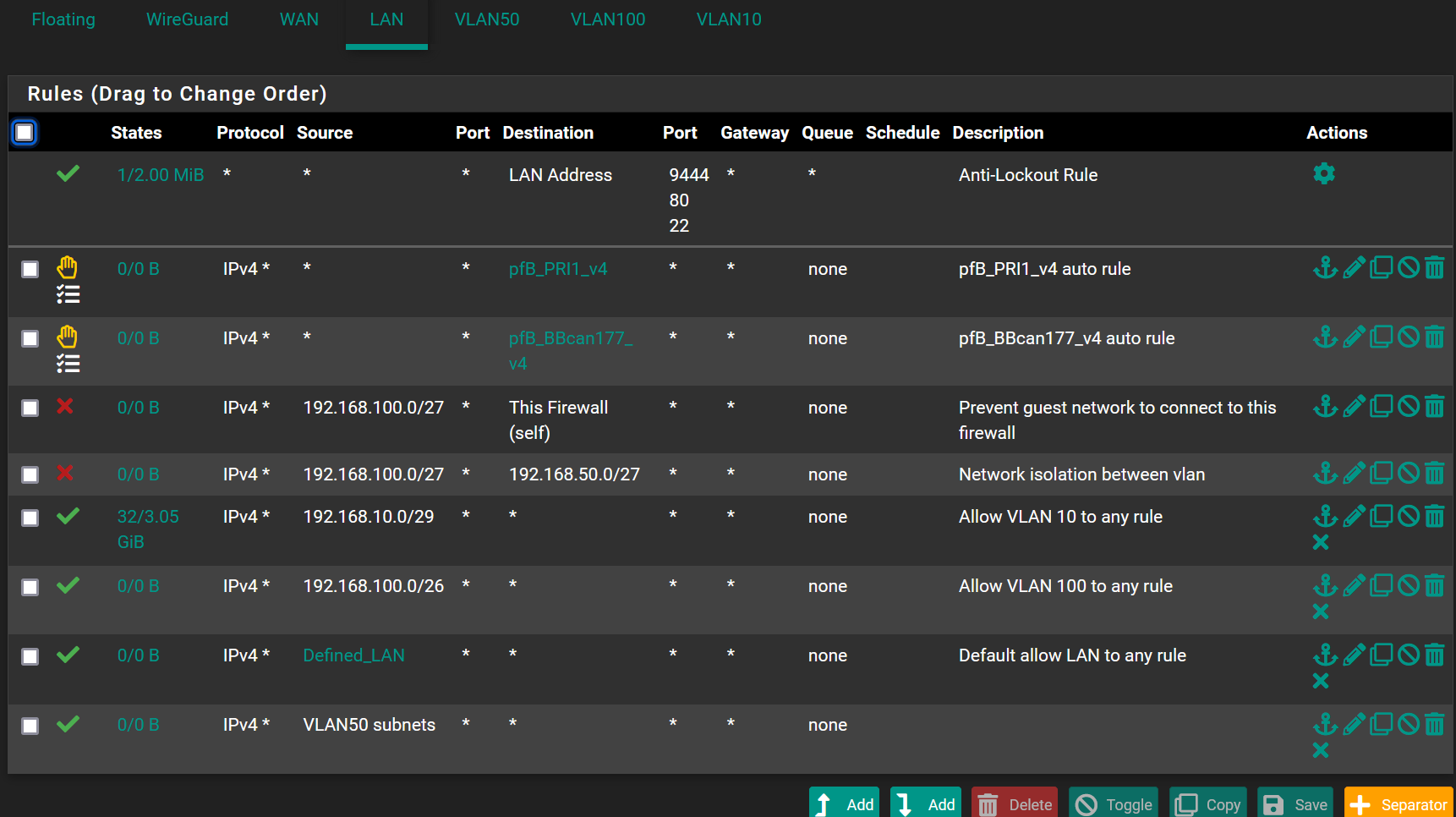
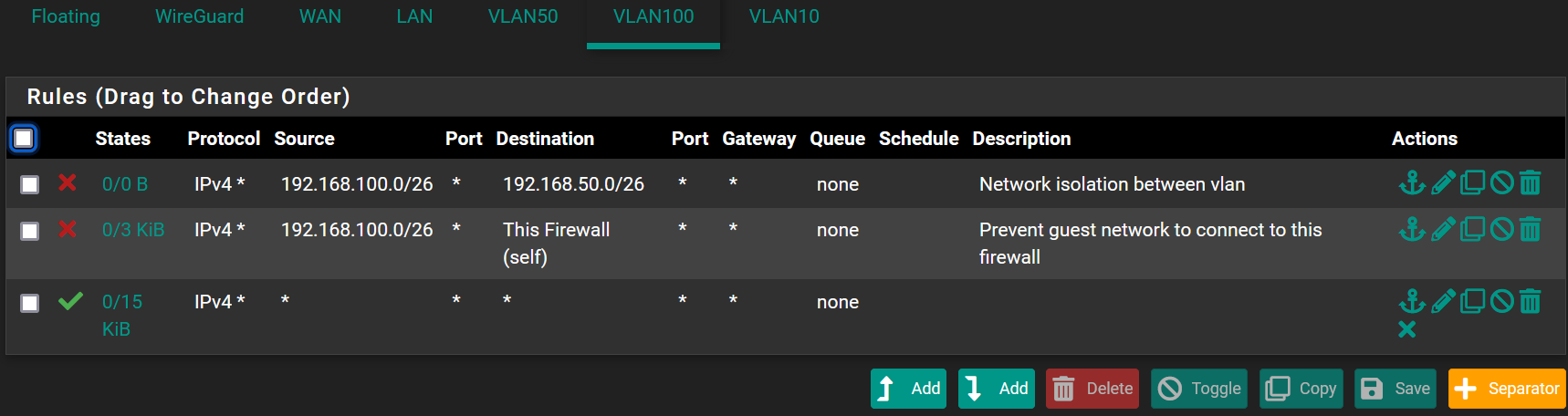
and I can't see anything relevant in the system logs....
Thanks !!
-
@Methraton on your vlan 100 your blocking access to anything on the 192.168.50 network, So no that vlan100 would not be able to start a conversation to anything in that network.
And you blocking access to every IP on the firewall, so no you wouldn't be able to ping pfsense IP address on the 192.168.100 or any other IP of pfsense.
Unless the device on the vlan100 was using some external dns, it wouldn't be able to ask pfsense for dns either with those rules.. So Its not going to be able to go to www.google.com even unless it was using something external to resolve www.google.com
Rules are evaluated top down, first rule to trigger wins, as traffic enters the interface from the network its attached too.
edit: these rules look pointless.. What is the network on your LAN, sure isn't 192.168.100 or 192.168.50? That traffic would never be source into pfsense lan.. Is your lan network 192.168.100/27 ?? how would that be source of traffic into the lan interface? Going to anything on the firewall or the 192.168.50/27 network??
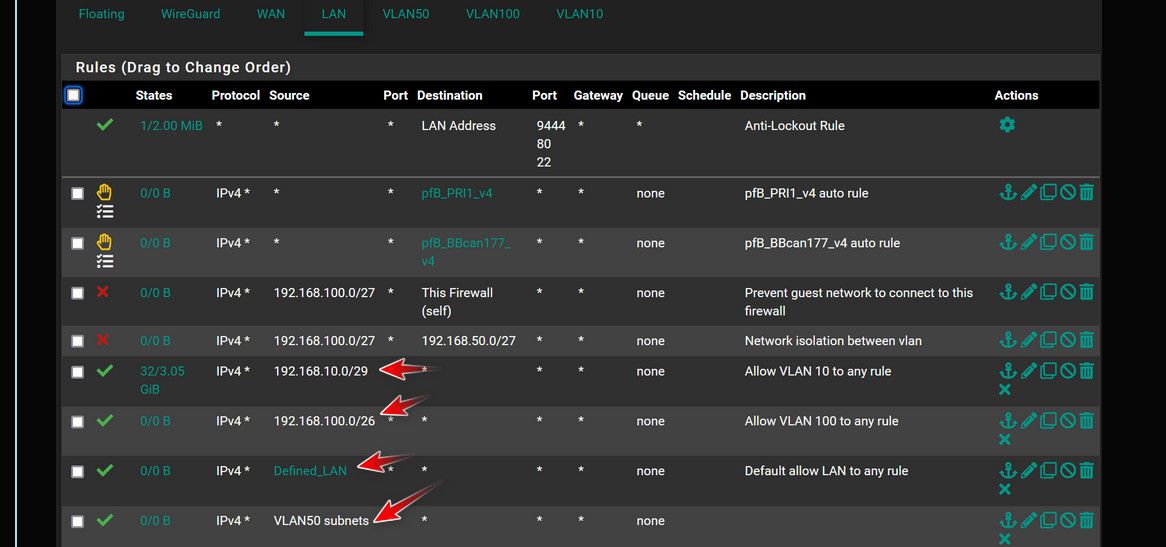
The only traffic that would be source inbound into the lan interface, is the lan subnet.. What network do you have on LAN, that is the only thing that could be source into the lan interface. Unless you were using lan as a transit/connector network - and if that was the cause you wouldn't create vlan interfaces on pfsense..
To be honest the whole thing looks a mess, all those rules on floating only make for complexity.. If you don't want vlan X to go so some where, or you want to allow it to do something - put the rule on the interface not floating..