Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?
-
@viragomann -- I wanted to add a detail that the VPN provider is issuing private IP addresses (ie: 10.X.X) but I imagine that is commonplace with every kind of VPN provider at this stage. Is there a rule I am missing?
I tried a block all rule on the VPN interface to see if I could get any kind of logging, and there was nothing even in the firewall block logs.
-
@techboot
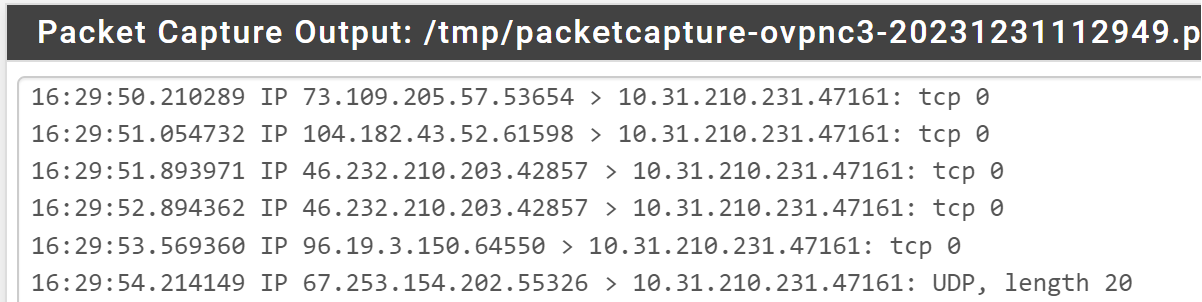
You're using a different destination port now, as allowed in the NAT rule?Don't know, what kind of connection this is. It basically looks fine, but not any packet has a payload. So maybe it's just "keep alive" communication.
@techbooties said in Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?:
I wanted to add a detail that the VPN provider is issuing private IP addresses (ie: 10.X.X) but I imagine that is commonplace with every kind of VPN provider at this stage.
Changed the forum username?
No, it's not normal to masquerade the source IP.
And I was expecting to see a public IP. -
I must have created a second account and didn't realize Google had an account linked and stored the other. Sorry for this confusion. I will clean up the duplicate account, but don't want to delete it mid-thread.
Yes, I changed the port number from the VPN provider... it's a static port, with the option to release and request a new one if needed.
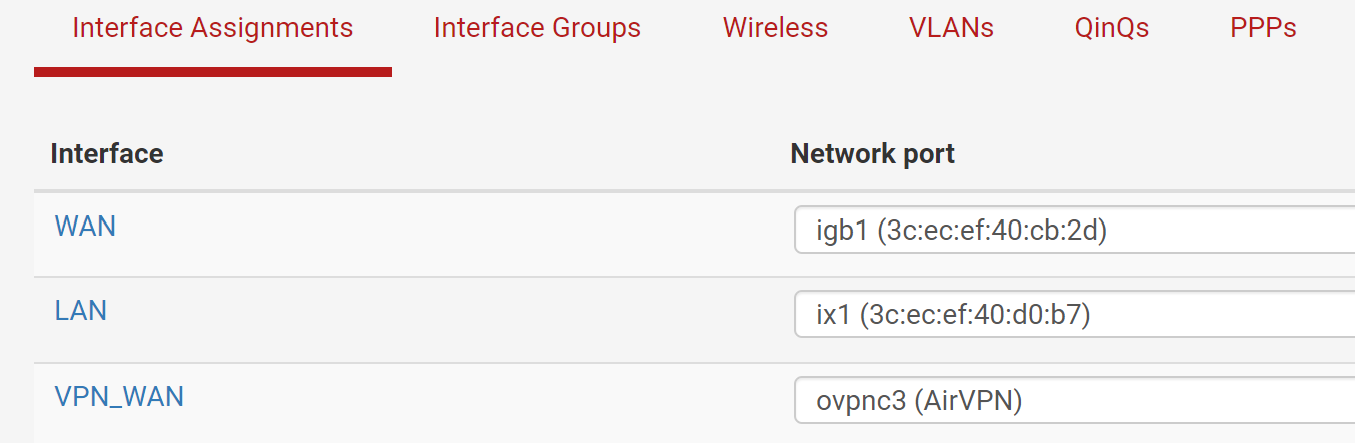
So basically VPN provider (AirVPN) has public IP -> private IP with assigned port to route towards it (mine, when connected with the client) -> pfsense -> local machine
So my running theory now is that since I am being assigned a 10.x IP by the VPN provider upon connection to them, there is something I am missing fundamentally in my config?
-
-
@techboot
This whole thread is already pretty confusing. In the screenshot above on the VPN interface, I can see public source IP. But then you say, the provider replaces it with a private one (masquerading)...To get a step beyond, do a simple test, please:
Add an outbound NAT rule for the incoming traffic:
Interface: LAN
source: any
destination: <server IP>/32
translation: interface addressCheck if you get access from outside.
-
To clarify when you say "server ip" do you want the public ip as seen in the screenshot or the assigned internal IP via Masquerading?
-
@techboot
It's local IP.Edit:
also flush the states after adding the rule. -
No change. To confirm:
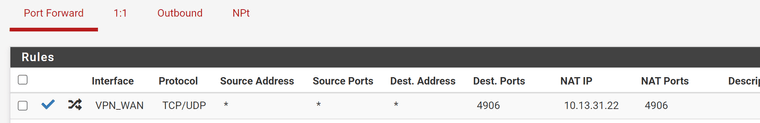
NAT:
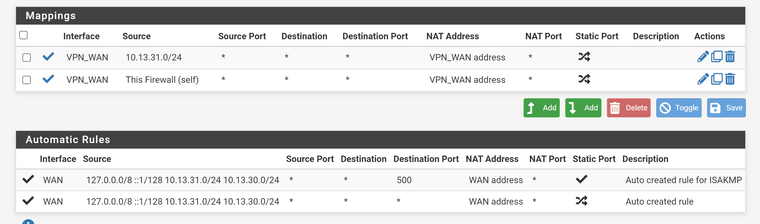
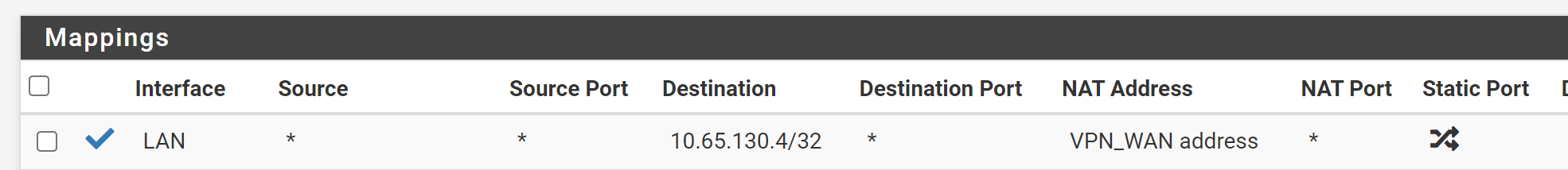
Outbound NAT:
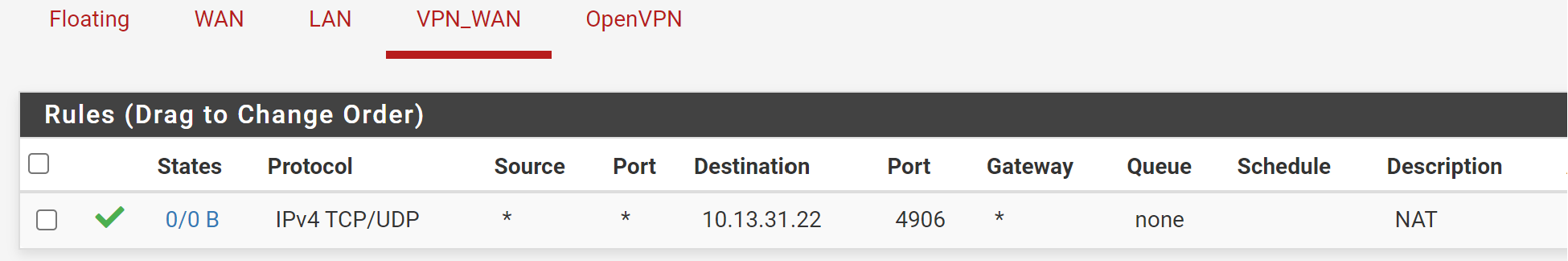
Rules (VPN Interface)
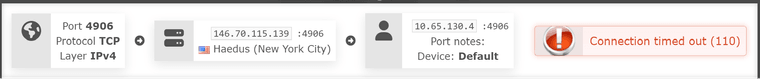
VPN Provider Port Check Tool: (Note, telnet to the public IP from an outside IP (ie: an Azure VPS, yields the same result)
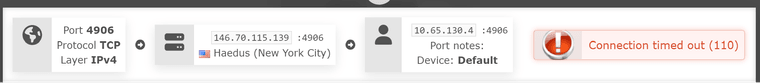
--
In an effort to maybe make this easier, should I delete this thread and re-make it? I will remove all of the rules, NAT, etc.. reboot for good measure and start over with all of the details / information in one post based on your feedback and comments thus far?
-
@techboot said in Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?:
NAT:
And the mess goes on...
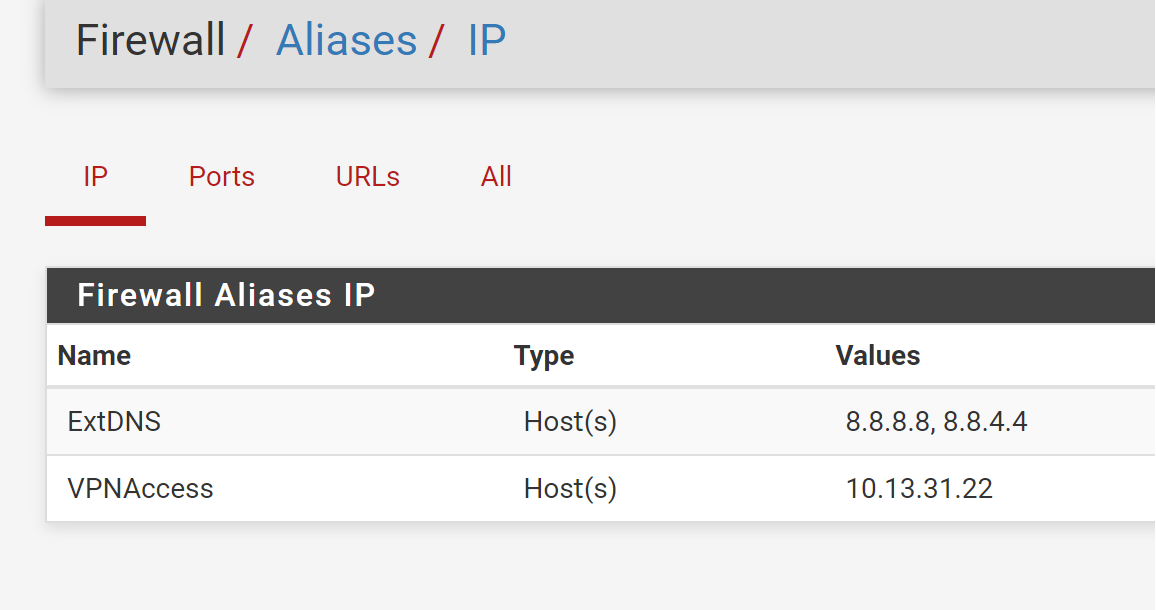
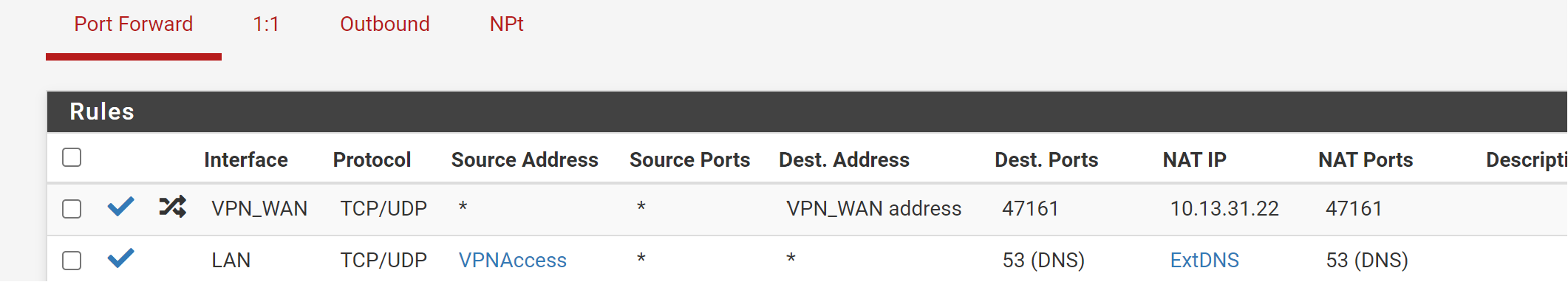
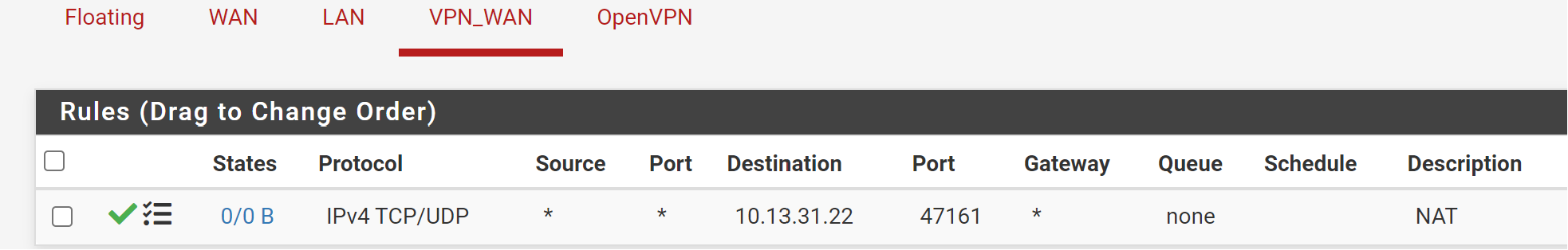
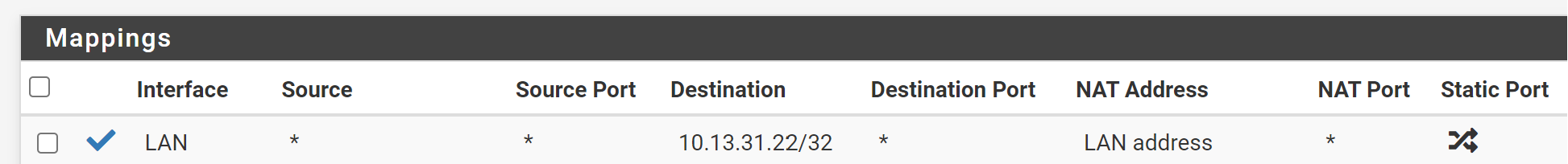
10.13.31.22 is your VPN interface address. The NAT IP has to be your internal server IP!Also you should limit the destination IP. Your may set it to the interface address.
-
-
@techboot
Ah ya. So you need to edit the outbound NAT rule and correct the destination IP. -
Cleared States.
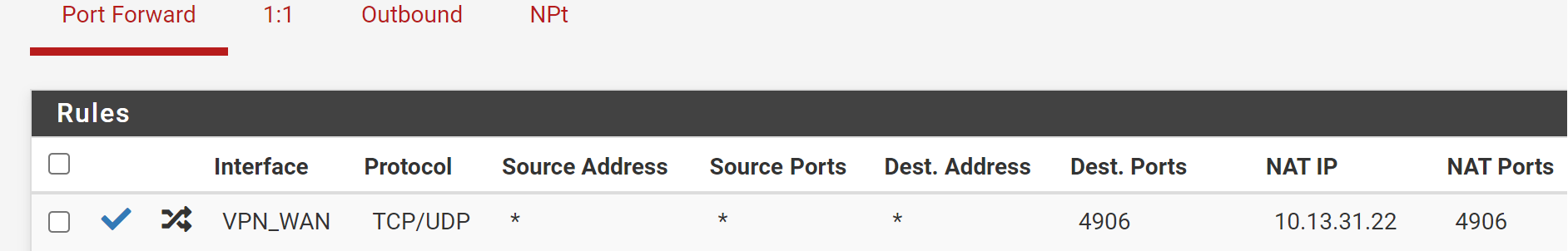
--
--
I am confused what you mean by limit the destination IP and limit to the interface address. I assume you mean on the port forward tab?
-
@techboot said in Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?:
I assume you mean on the port forward tab?
Yes.
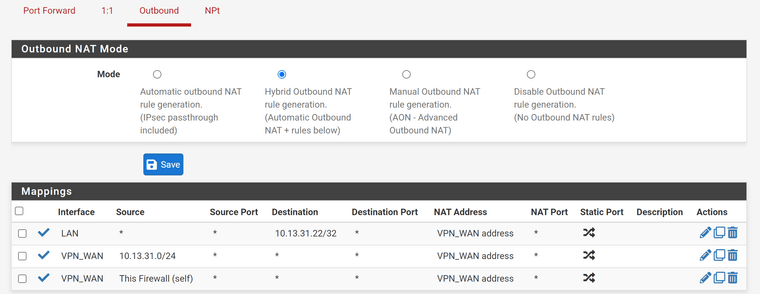
In the LAN outbound NAT rule correct the translation to interface address, please, which is the default setting.
-
I think I have now gone and confused myself in all of this. Thank you for bearing with me.
Like this?
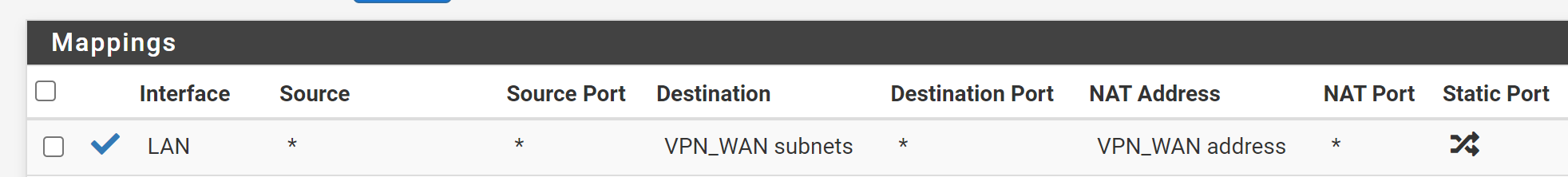
-
@techboot
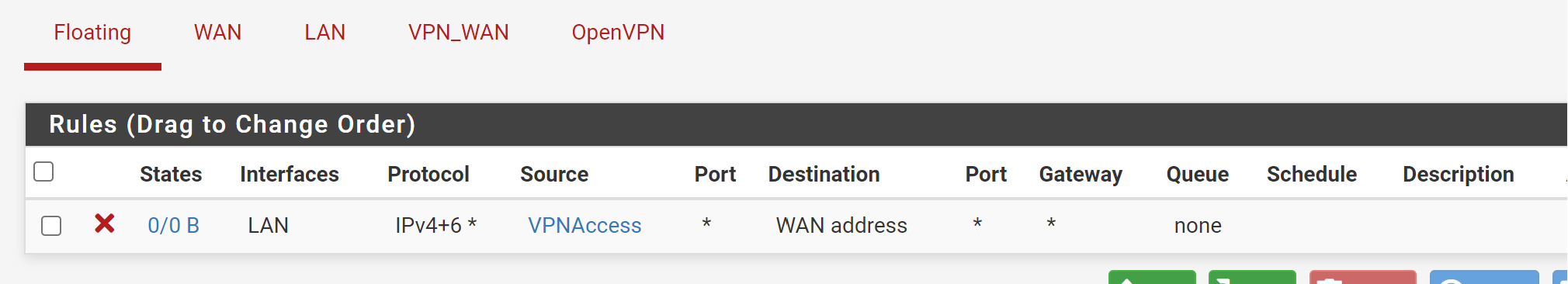
destination: internal server IP with /32 mask
translation: LAN address -
-
Question on this...
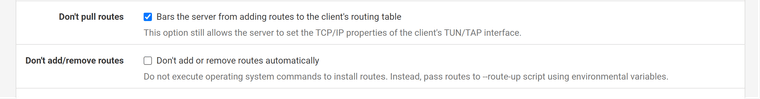
These are my current OpenVPN Client (towards the VPN Provider) Settings... I was under the impression that I wanted the "Dont Pull Routes" checkbox selected, since that would otherwise set the default gateway for the whole router towards the VPN provider.
In my case, I want to only route specific IP's out via the VPN, which DOES currently work.
Could this actually be some of my port forward issues?
Edit: this is the documentation pertain to port forwarding from the VPN provider: https://airvpn.org/faq/port_forwarding/
-
@techboot said in Port Forwarding w/ OpenVPN Tunnel - What am I doing wrong?:
These are my current OpenVPN Client (towards the VPN Provider) Settings... I was under the impression that I wanted the "Dont Pull Routes" checkbox selected, since that would otherwise set the default gateway for the whole router towards the VPN provider.
That's correct. You don't need routes, since you do policy routing for outbound traffic.
Edit: this is the documentation pertain to port forwarding from the VPN provider: https://airvpn.org/faq/port_forwarding/
There is nothing mentioned, that the provider does masquerading as you stated above.
If he doesn't masquerading you need to enable reply-to for proper reply-routing.For a quick test if this is the issue, remove the "Don't pull routes" check, ensure that the VPN is shown as default gateway in Status > Gateway, then test the access.
-
Will try shortly.
To clarify, this is the only information that shows how they (provider's port check tool) works.
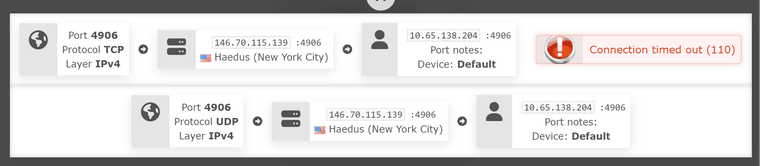
To me, that's public -> pfsense (as VPN client 10.65.138.204) -> LAN client (10.13.31.22)
-
@techboot
I don't expect, that the provider knows your LAN clients IP.