Use of Syslog-ng Package to see Bridge Mode AP syslog events on firewall.
-
Hello fellow Netgate community members,
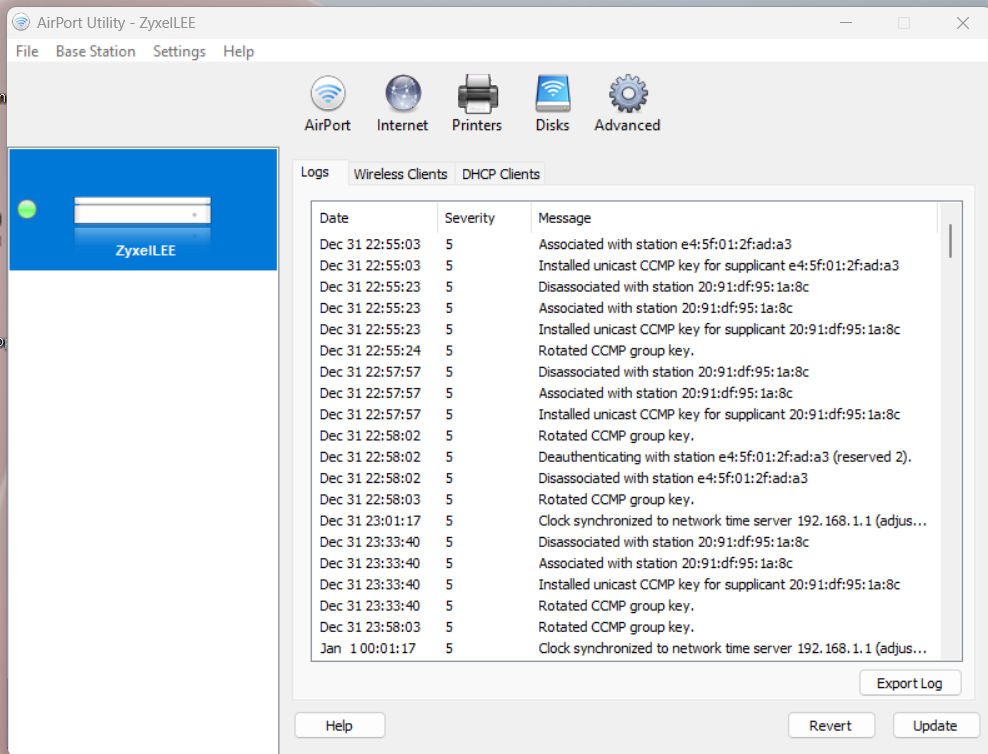
(Airport Extreme Logs, don't ask why it is named Zyxel :) )I wanted to share a quick how to guide to make your external AP system send syslog events to pfSense. You can setup pfSense to be a log server for syslog events. Keep in mind Airport Extreme logs only can be seen with some versions of Airport Utility, this causes issues with accessing them, as normally users can not see them with the version that is on Mac OSX, only with the older version and or the version that is made for Windows.
So here is how it's done.
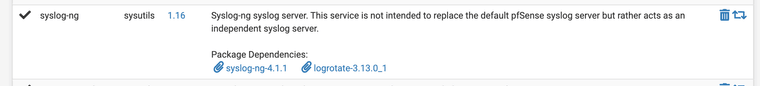
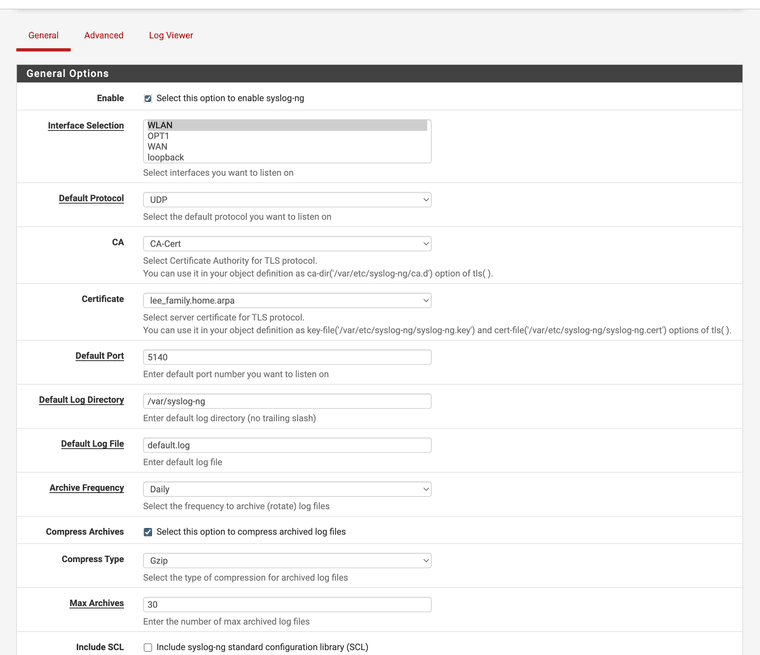
1. Install the Syslog-ng package
2. Configure your Airport Extreme (Vendor Dependent) to send syslog events over to your pfSense firewall IP address.
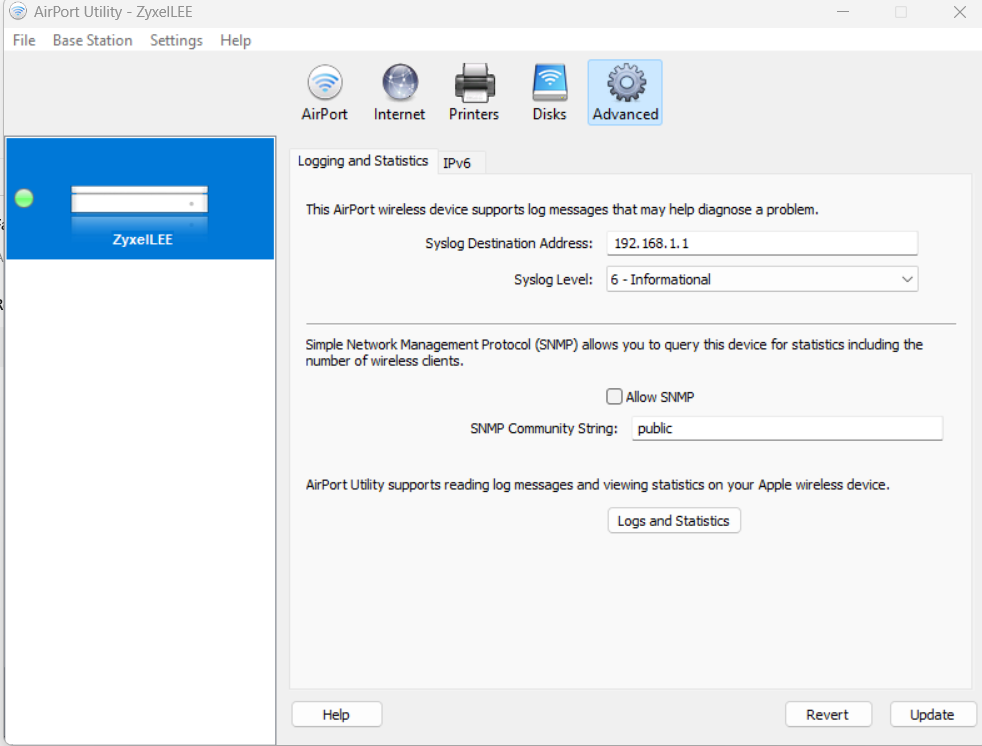
(This is easy just put in your firewalls ip address and set the syslog level you want)You can not configure the port on the Airport Extreme it is always UDP 514 so you need to do the port mapping to fix this
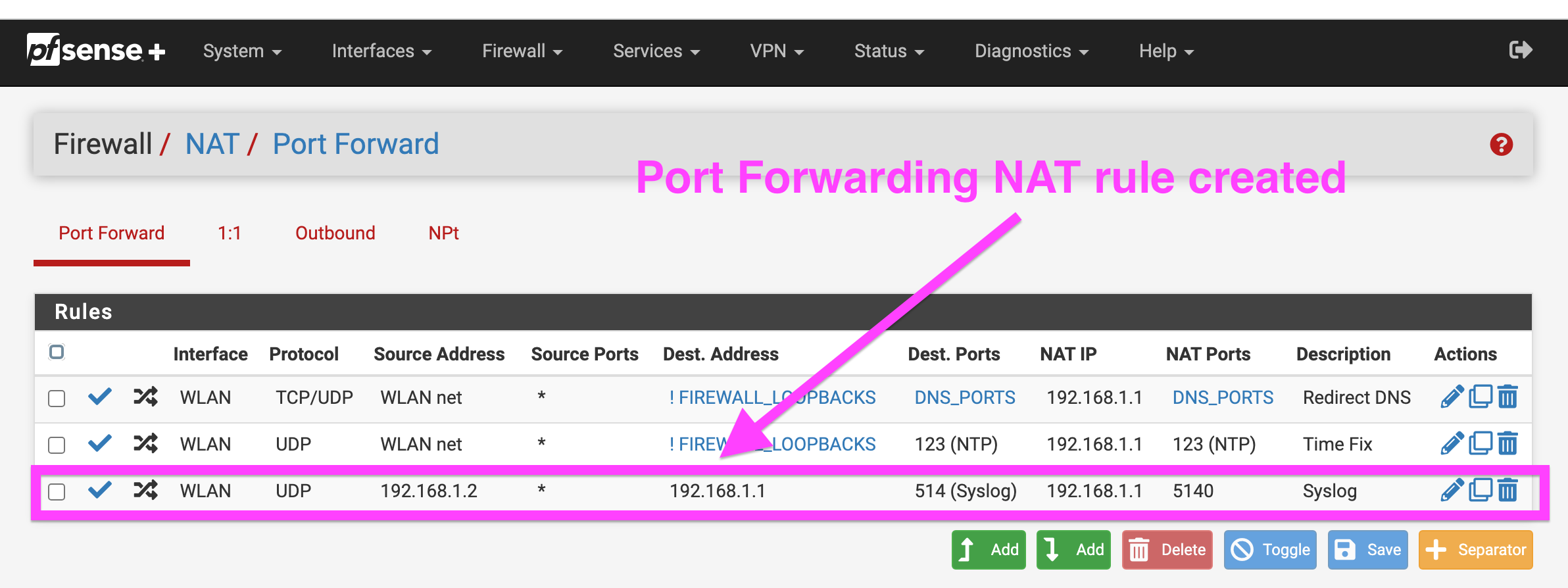
3. Create a NAT rule for your AP (mine is 192.168.1.2) to map the default syslog port 514 over to the port that Syslog-ng uses 5140
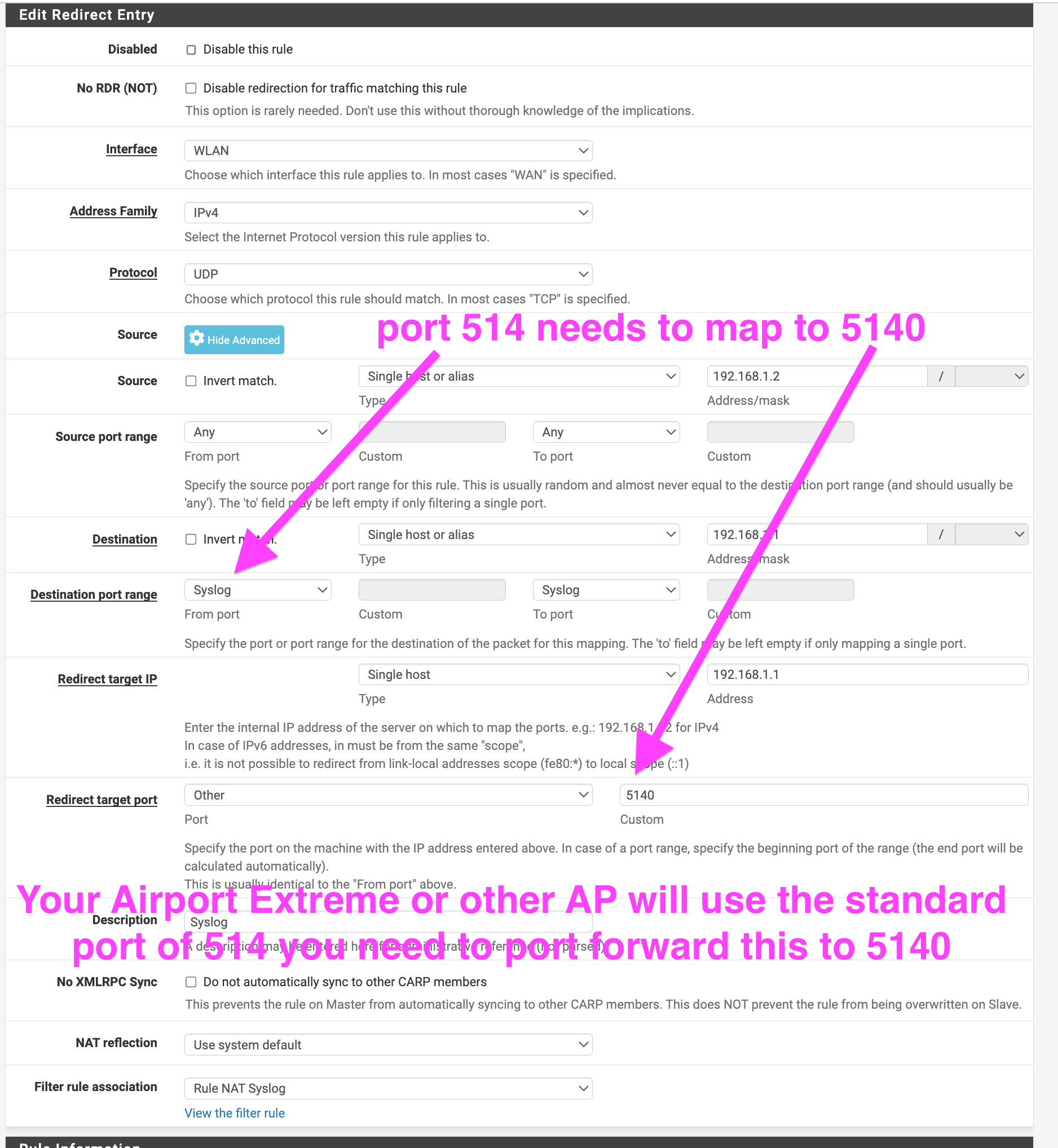
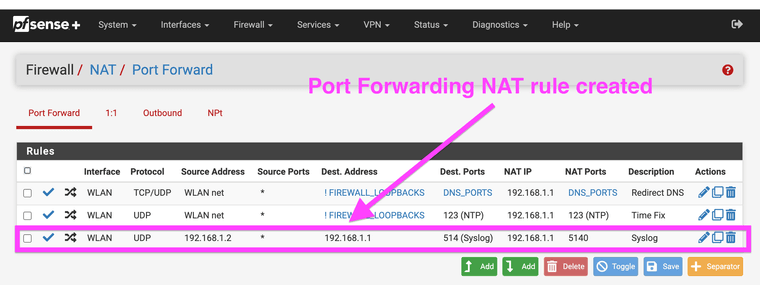
(Again use the Windows Airport Extreme software it still allows you access to the syslog configuration options)
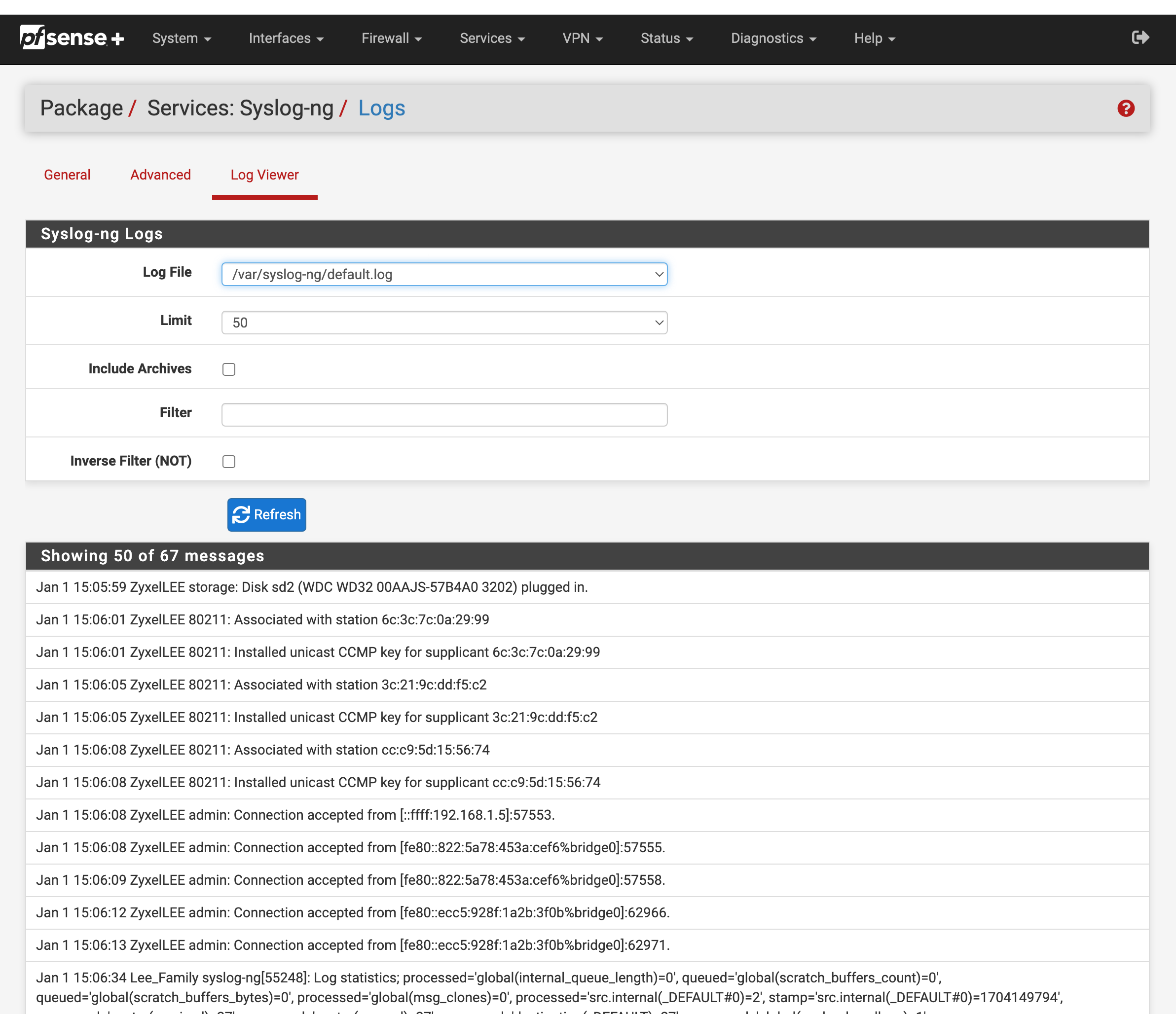
4. Enable your Syslog-ng package for your interface the ap resides on.
Now... Drum roll.....
Bingo!! You got all your logs in pfSense without ever having to log into your Airport specific software to see them. You can see who accesses the NAS, shows connected.
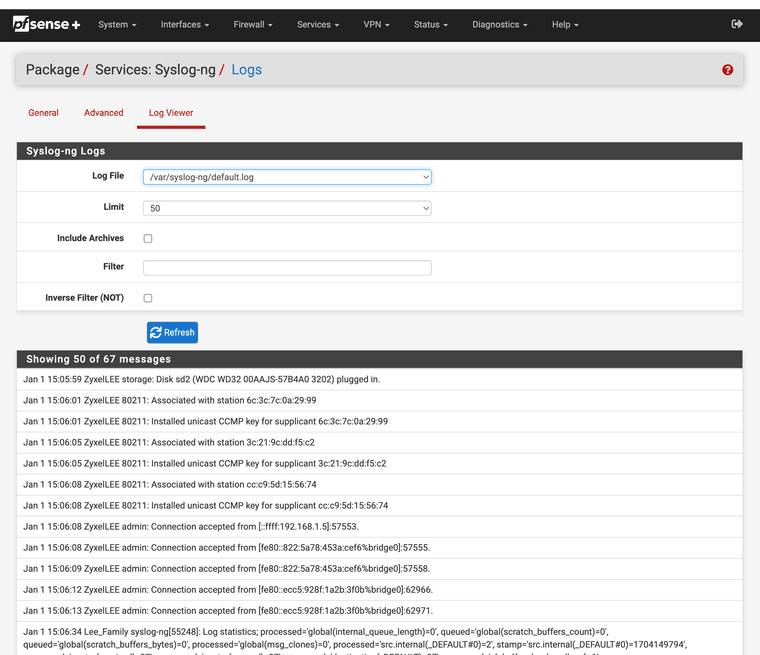
This also will work with other AP systems that have the ability to forward syslog events, some may even allow you to use a custom port, again if they only let you use 514 just port forward it.
Now you can set up remote access to your NAS drives running on your Airport Extreme and see who connects and track whats going on.
-
I know what your thinking, Big deal, I got logs in pfSense,
But here the issue is, most often you will be running your AP in bridge mode and having pfSense hand out the DHCP addresses, and if your in bridge mode not much info on whats connecting to the NAS internally behind the firewall is ever seen on the firewall logs. This gives you a level of visibility not normally seen within pfSense unless it is configured. Again if you can do it with one AP you can do it with an alias for many APs on a bigger network. This gives you more information into possibile mac spoofing and unauthorized access. If you use remote access and Dynamic DNS for your network, you can see the firewall logs and the AP logs as well.