How to setup HTTPS between my browser and my pfSense firewall?
-
Newbie here. I just installed a pfSense firewall, running v2.7.2. It works great! This is for my home office. I can aim my Google Chrome browser at 192.168.1.1 no problem, and logon, but the connection itself is simple HTTP, not HTTPS. How do configure the firewall & browser to use HTTPS? I'm sure this is simple every day topic, just don't know where to look. All help will be greatly appreciated.
-
@flugenblar SYSTEM -> ADVANCED -> ADMIN ACCESS
-
Yup that ^.
It should use https (and redirect http to https) by default though.
-
I've got it set to HTTPS and the SSL/TLS certificate is set to GUI Default (long number)... I didn't set that it was set by default, but I still see Not Secure in the URL box of my Chrome browser. Could Chrome by trying to warn me about a self-signed certificate? I think this is using a self-signed cert, maybe it's just saying it shoudn't be trusted?
-
Yes, it uses a self-signed cert by default.
-
@flugenblar said in How to setup HTTPS between my browser and my pfSense firewall?:
I think this is using a self-signed cert
If you didn't create your own cert with CA your browser trusts, then yeah its going to warn you.
here I created my own ca in pfsense, then issued certs from that CA, and my browser trusts my CA.. But still notifies me that hey we trust this but not a built in normal firefox CA
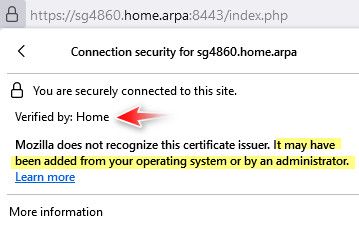
Another option would be use acme cert, then your browser wont bitch at you.. But you need to use a public domain. Which a cert you sign with your own ca you can use any fqdn you want, notice mine is using home.arpa the new recommended local domain. And you can add rfc1918 address space..
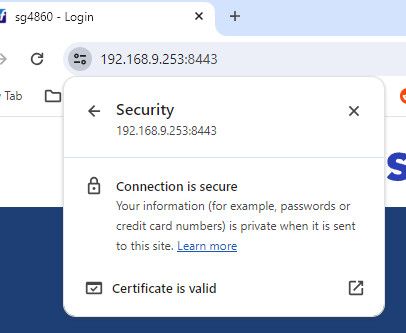
See I can access with IP and no warning..
here even in chrome
-
when I use Safari, I get a warning too. it says:
pfSense-65922812c2462
Self-signed root certificate
Expires: Saturday, February 1, 2025 at 6:48:15 PM Pacific Standard Time
! This certificate has not been verified by a third part...
Organization pfSense GUI default Self-signed Certificate
Common Name pfSense-65922812c2462
...so should I try to refresh the cert or get a new one or something? or just live with the warning? I mean, I setup the hardware and installed the image, so i do actually trust it... but...
-
@flugenblar browsers are most always going to complain about self signed certs.. If you want the warning to go away you going to have to create your own CA, issue cert and have your browser trust it.
or use domain and the acme (packet to use lets encrypt) to get a cert for for some domain to have your web gui use..
I have gone over how to create a CA and issue cert your browser will trust many times... Here is a old thread where I went over it
-
@johnpoz Thanks! that all makes sense. if i were doing this at work I'd be able to go to the team that issues certs and get one for this, but I'm at home and dont want to go through all that business. I might play with creating my own CA in pfSense. Not sure I care that much yet, but it's an interesting option.
-
@flugenblar yeah as long as your browser doesn't bug you every time about the self signed, its not an issue for sure.. Your still encrypting your traffic..
Its only a few seconds to setup, and once you setup a browser to trust you can issue signed certs for all your different things that might want to use a cert. switches, printers, your nas gui, my unifi controller software.. etc. etc.
Use to be better when the browsers also didn't complain about lifetime of cert, use to issue them for 10 years and never had to think about it again etc.. But now I think like 398 days is longest you can issue one for before browsers bitch at you about it.