Rule ID vs Tracking ID
-
Hi all
Can anyone clarify the difference between Rule ID and Tracking ID, also would be appreciable if anyone can explain the use cases of both.
Thanks in advance.
-
Which IDs do you mean exactly?
This rule for example:
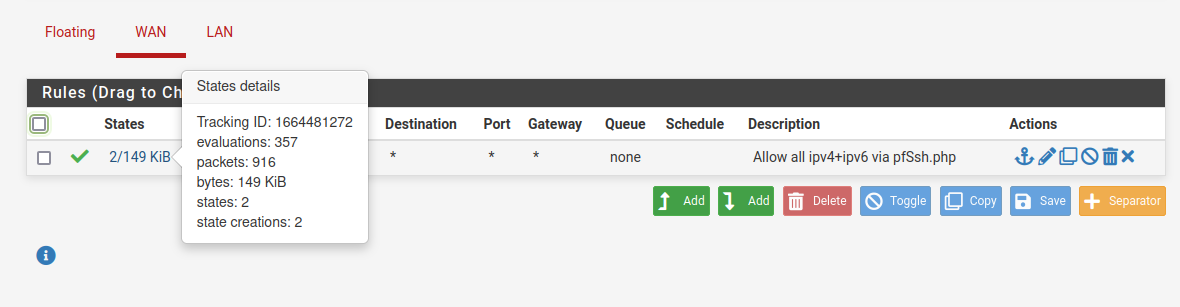
Appears in the ruleset (rules.debug) as:
pass in quick on $WAN reply-to ( em0 172.21.16.1 ) inet from any to any ridentifier 1664481272 keep state label "USER_RULE: Allow all ipv4+ipv6 via pfSsh.php" label "id:1664481272"And in the running rules as:
@86 pass in quick on em0 reply-to (em0 172.21.16.1) inet all flags S/SA keep state label "USER_RULE: Allow all ipv4+ipv6 via pfSsh.php" label "id:1664481272" ridentifier 1664481272 [ Evaluations: 230 Packets: 593 Bytes: 79110 States: 1 ] [ Inserted: uid 0 pid 20184 State Creations: 1 ] [ Last Active Time: Mon Jan 15 21:41:37 2024 ]And states created by it show as:
all tcp 172.21.16.184:22 <- 172.21.16.8:48666 ESTABLISHED:ESTABLISHED [2265314687 + 2147156224] wscale 7 [2857302096 + 65792] wscale 7 age 00:08:02, expires in 24:00:00, 328:354 pkts, 22905:64497 bytes, rule 86, log id: 0fa5a56500000000 creatorid: b766ae99 reply-to: 172.21.16.1@em0 origif: em0 -
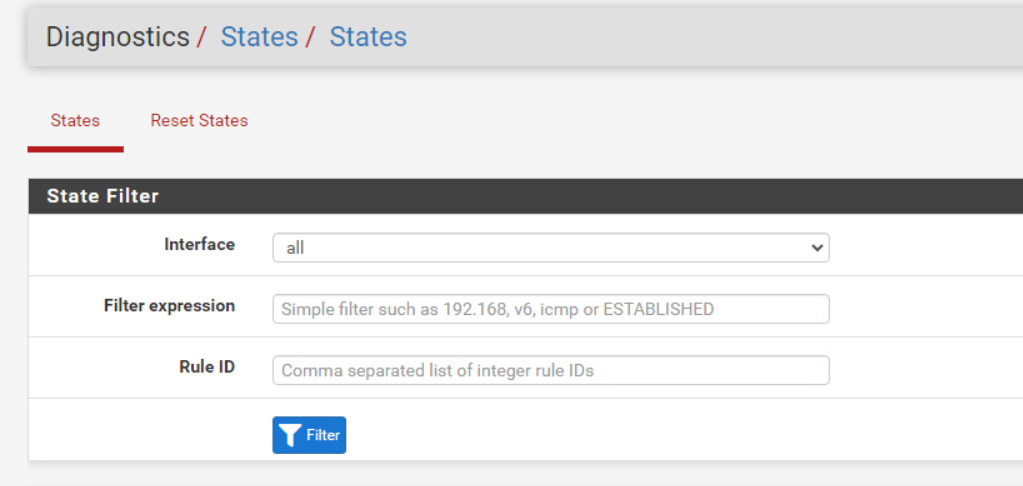
Hi @stephenw10 i refer this rule id on diagnostics tab
-
Ah Ok those are the rule numbers, so
@86in my example above. You'd enter86there. -
Hi @stephenw10 at least for me it´s not already 100% clear could you please explain it?
Thanks in advance
-
If you want to filter the states by Rule ID you have to enter the rule numbers there.
You can see the rule numbers in the running ruleset by running:
pfctl -vvsr
For example:[23.09.1-RELEASE][root@7100.stevew.lan]/root: pfctl -vvsr @0 scrub from any to <vpn_networks:*> fragment no reassemble [ Evaluations: 39420 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @1 scrub from <vpn_networks:*> to any fragment no reassemble [ Evaluations: 39420 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @2 scrub on lagg0 inet all fragment reassemble [ Evaluations: 39420 Packets: 39368 Bytes: 310545 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @3 scrub on lagg0 inet6 all fragment reassemble [ Evaluations: 1 Packets: 1 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @4 scrub on ix2 inet all fragment reassemble [ Evaluations: 51 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @5 scrub on ix2 inet6 all fragment reassemble [ Evaluations: 2 Packets: 2 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @6 scrub on lagg1 inet all fragment reassemble [ Evaluations: 49 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @7 scrub on lagg1 inet6 all fragment reassemble [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @0 anchor "openvpn/*" all [ Evaluations: 813 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @1 anchor "ipsec/*" all [ Evaluations: 813 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @2 block drop in log quick inet from 169.254.0.0/16 to any label "Block IPv4 link-local" ridentifier 1000000101 [ Evaluations: 813 Packets: 12 Bytes: 1152 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: Tue Jan 16 15:19:53 2024 ] @3 block drop in log quick inet from any to 169.254.0.0/16 label "Block IPv4 link-local" ridentifier 1000000102 [ Evaluations: 23 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @4 block drop in log inet all label "Default deny rule IPv4" ridentifier 1000000103 [ Evaluations: 23 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @5 block drop out log inet all label "Default deny rule IPv4" ridentifier 1000000104 [ Evaluations: 800 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @6 block drop in log inet6 all label "Default deny rule IPv6" ridentifier 1000000105 [ Evaluations: 801 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @7 block drop out log inet6 all label "Default deny rule IPv6" ridentifier 1000000106 [ Evaluations: 778 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @8 pass quick inet6 proto ipv6-icmp all icmp6-type unreach keep state ridentifier 1000000107 [ Evaluations: 4 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @9 pass quick inet6 proto ipv6-icmp all icmp6-type toobig keep state ridentifier 1000000107 [ Evaluations: 4 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @10 pass quick inet6 proto ipv6-icmp all icmp6-type neighbrsol keep state ridentifier 1000000107 [ Evaluations: 4 Packets: 1 Bytes: 72 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @11 pass quick inet6 proto ipv6-icmp all icmp6-type neighbradv keep state ridentifier 1000000107 [ Evaluations: 3 Packets: 1 Bytes: 72 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 1 ] [ Last Active Time: N/A ] @12 pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type echorep keep state ridentifier 1000000108 [ Evaluations: 2 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @13 pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routersol keep state ridentifier 1000000108 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @14 pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routeradv keep state ridentifier 1000000108 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @15 pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbrsol keep state ridentifier 1000000108 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @16 pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbradv keep state ridentifier 1000000108 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @17 pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type echorep keep state ridentifier 1000000109 [ Evaluations: 1 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @18 pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routersol keep state ridentifier 1000000109 [ Evaluations: 1 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @19 pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routeradv keep state ridentifier 1000000109 [ Evaluations: 1 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @20 pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbrsol keep state ridentifier 1000000109 [ Evaluations: 1 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @21 pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbradv keep state ridentifier 1000000109 [ Evaluations: 1 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @22 pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type echoreq keep state ridentifier 1000000110 [ Evaluations: 1 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @23 pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routersol keep state ridentifier 1000000110 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @24 pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type routeradv keep state ridentifier 1000000110 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @25 pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbrsol keep state ridentifier 1000000110 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @26 pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type neighbradv keep state ridentifier 1000000110 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @27 pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type echoreq keep state ridentifier 1000000111 [ Evaluations: 1 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @28 pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type routersol keep state ridentifier 1000000111 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @29 pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type routeradv keep state ridentifier 1000000111 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @30 pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type neighbrsol keep state ridentifier 1000000111 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @31 pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type neighbradv keep state ridentifier 1000000111 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @32 pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type echoreq keep state ridentifier 1000000112 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @33 pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routersol keep state ridentifier 1000000112 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @34 pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type routeradv keep state ridentifier 1000000112 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @35 pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbrsol keep state ridentifier 1000000112 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @36 pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type neighbradv keep state ridentifier 1000000112 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @37 pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type echoreq keep state ridentifier 1000000113 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @38 pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type routersol keep state ridentifier 1000000113 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @39 pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type routeradv keep state ridentifier 1000000113 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @40 pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type neighbrsol keep state ridentifier 1000000113 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @41 pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type neighbradv keep state ridentifier 1000000113 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @42 block drop log quick inet proto tcp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000114 [ Evaluations: 799 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @43 block drop log quick inet proto udp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000114 [ Evaluations: 753 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @44 block drop log quick inet proto tcp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000115 [ Evaluations: 797 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @45 block drop log quick inet proto udp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000115 [ Evaluations: 753 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @46 block drop log quick inet6 proto tcp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000116 [ Evaluations: 799 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @47 block drop log quick inet6 proto udp from any port = 0 to any label "Block traffic from port 0" ridentifier 1000000116 [ Evaluations: 2 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @48 block drop log quick inet6 proto tcp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000117 [ Evaluations: 2 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @49 block drop log quick inet6 proto udp from any to any port = 0 label "Block traffic to port 0" ridentifier 1000000117 [ Evaluations: 2 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @50 block drop log quick from <snort2c:0> to any label "Block snort2c hosts" ridentifier 1000000118 [ Evaluations: 799 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @51 block drop log quick from any to <snort2c:0> label "Block snort2c hosts" ridentifier 1000000119 [ Evaluations: 799 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @52 block drop in log quick proto tcp from <sshguard:0> to (self:11) port = ssh label "sshguard" ridentifier 1000000301 [ Evaluations: 799 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @53 block drop in log quick proto tcp from <sshguard:0> to (self:11) port = https label "GUI Lockout" ridentifier 1000000351 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @54 block drop in log quick from <virusprot:0> to any label "virusprot overload table" ridentifier 1000000400 [ Evaluations: 23 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @55 pass in quick on lagg0 proto udp from any port = bootps to any port = bootpc keep state label "allow dhcp replies in WAN" ridentifier 1000000461 [ Evaluations: 23 Packets: 2 Bytes: 656 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 1 ] [ Last Active Time: Tue Jan 16 14:11:54 2024 ] @56 pass out quick on lagg0 proto udp from any port = bootpc to any port = bootps keep state label "allow dhcp client out WAN" ridentifier 1000000462 [ Evaluations: 784 Packets: 4 Bytes: 1312 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 2 ] [ Last Active Time: Tue Jan 16 15:59:01 2024 ] @57 block drop in log on ! lagg0 inet from 172.21.16.0/24 to any ridentifier 1000001470 [ Evaluations: 796 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @58 block drop in log inet from 172.21.16.120 to any ridentifier 1000001470 [ Evaluations: 782 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @59 block drop in log on lagg0 inet6 from fe80::2e0:edff:fe86:a68c to any ridentifier 1000001470 [ Evaluations: 22 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @60 block drop in log on ! ix2 inet from 192.168.88.0/24 to any ridentifier 1000002520 [ Evaluations: 22 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @61 block drop in log inet from 192.168.88.1 to any ridentifier 1000002520 [ Evaluations: 22 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @62 block drop in log on ix2 inet6 from fe80::208:a2ff:fe0e:a593 to any ridentifier 1000002520 [ Evaluations: 22 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @63 pass in quick on ix2 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000002541 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @64 pass in quick on ix2 inet proto udp from any port = bootpc to 192.168.88.1 port = bootps keep state label "allow access to DHCP server" ridentifier 1000002542 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @65 pass out quick on ix2 inet proto udp from 192.168.88.1 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000002543 [ Evaluations: 774 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @66 pass in on lo0 inet all flags S/SA keep state label "pass IPv4 loopback" ridentifier 1000004661 [ Evaluations: 794 Packets: 23 Bytes: 2226 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 11 ] [ Last Active Time: Tue Jan 16 13:59:27 2024 ] @67 pass out on lo0 inet all flags S/SA keep state label "pass IPv4 loopback" ridentifier 1000004662 [ Evaluations: 24 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @68 pass in on lo0 inet6 all flags S/SA keep state label "pass IPv6 loopback" ridentifier 1000004663 [ Evaluations: 26 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @69 pass out on lo0 inet6 all flags S/SA keep state label "pass IPv6 loopback" ridentifier 1000004664 [ Evaluations: 12 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @70 pass out inet all flags S/SA keep state allow-opts label "let out anything IPv4 from firewall host itself" ridentifier 1000004665 [ Evaluations: 796 Packets: 92 Bytes: 23856 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 13 ] [ Last Active Time: Tue Jan 16 15:41:40 2024 ] @71 pass out inet6 all flags S/SA keep state allow-opts label "let out anything IPv6 from firewall host itself" ridentifier 1000004666 [ Evaluations: 774 Packets: 2 Bytes: 172 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @72 pass out route-to (lagg0 172.21.16.1) inet from 172.21.16.120 to ! 172.21.16.0/24 flags S/SA keep state allow-opts label "let out anything from firewall host itself" ridentifier 1000004761 [ Evaluations: 774 Packets: 2338 Bytes: 448008 States: 3 ] [ Inserted: uid 0 pid 46270 State Creations: 743 ] [ Last Active Time: Tue Jan 16 16:37:23 2024 ] @73 pass in quick on ix2 proto tcp from any to (ix2:2) port = https flags S/SA keep state label "anti-lockout rule" ridentifier 10002 [ Evaluations: 796 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @74 pass in quick on ix2 proto tcp from any to (ix2:2) port = http flags S/SA keep state label "anti-lockout rule" ridentifier 10002 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @75 pass in quick on ix2 proto tcp from any to (ix2:2) port = ssh flags S/SA keep state label "anti-lockout rule" ridentifier 10002 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @76 anchor "userrules/*" all [ Evaluations: 796 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @77 pass in quick on lagg0 reply-to (lagg0 172.21.16.1) inet all flags S/SA keep state label "USER_RULE: Allow all ipv4+ipv6 via pfSsh.php" label "id:1533055761" ridentifier 1533055761 [ Evaluations: 796 Packets: 40 Bytes: 25177 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 10 ] [ Last Active Time: Tue Jan 16 16:04:08 2024 ] @78 pass in quick on lagg0 inet6 all flags S/SA keep state label "USER_RULE: Allow all ipv4+ipv6 via pfSsh.php" label "id:1533055761" ridentifier 1533055761 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @79 pass in quick on lagg0 reply-to (lagg0 172.21.16.1) inet proto icmp from <WAN__NETWORK:1> to 172.21.16.120 keep state label "USER_RULE: Allow ping" label "id:1559646116" ridentifier 1559646116 [ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @80 pass in quick on ix2 inet from <LAN__NETWORK:1> to any flags S/SA keep state label "USER_RULE: Default allow LAN to any rule" label "id:0100000101" ridentifier 100000101 [ Evaluations: 26 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ] @81 anchor "tftp-proxy/*" all [ Evaluations: 786 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 46270 State Creations: 0 ] [ Last Active Time: N/A ]From the Firewall > Rules page in the GUI you can click on the state column for each individual rule and it will automatically fill in the RuleID in the state table filtering.
Steve