No internet on LAN
-
Hi,
I'm brand new to pfSense, and I know this topic is brought up a lot. I have looked through this topic @stephenw10, which is similar to my setup, but the solution of explicitly setting my gateway didn't work.I have a virtualized setup, my building has a Spectrum business service wired to each apt, From the wall jack I am connected to the NIC associated with the isolated pfSense VM, 192.168.1.1, then from the NIC to my laptop, 192.168.1.100. I played around with adding rules and looking over the logs and the docs, but never got a connection from my laptop. no ping google. can ping pfSense VM. But when in the pfSense shell I can ping google. I have reverted all my settings to the system generated rules.
Please let me know where to start looking. Thanks!
-
@rakya said in No internet on LAN:
From the wall jack I am connected to the NIC associated with the isolated pfSense VM, 192.168.1.1, then from the NIC to my laptop, 192.168.1.100.
Unclear exactly which part of the connection you're referring to. It sounds like you might have a subnet conflict though. Is the WAN IP in a different subnet?
Steve
-
@rakya
when I filter the logs for traffic from my laptop, it shows it is blocked by "Default deny rule IPv4 (1000000103)", but that doesn't match the text in any of the Firewall or NAT rules I can see in the respective tabs.
Also I had briefly turned on logging for pass's . I was able to start a youtube video on my wifi then switch to the pfSense LAN, and I was able to finish the video buffering from the pfSense LAN. Would this be because the firewall saw it as an existing state? I will try that again when I am near my machine in a couple hours. and look through the logs more carefully@stephenw10 ,Thanks!
-
@rakya said in No internet on LAN:
Default deny rule IPv4 (1000000103)"
Post up your lan rules.. The default rule is an any any rule for anything coming from the lan net IP range..
The default deny rule is the rule that blocks stuff that is not allowed, its a hidden rule and on all interfaces. If traffic coming into your lan is not allowed by a rule, then yes it would be blocked by the default deny.
-
@stephenw10 I dont beleive so.
The way I understand it, I am basically creating a subnet, since the wall ethernet is configured as a LAN and I have pfsense configured to use it as a WAN
-
All traffic that is not explicitly passed in pfSense is blocked by the default block rules like that.
That means it's not matching the default pass rules which exist on LAN. Those normally catch traffic from anything in the LAN subnet so that traffic is either not from the LAN subnet or the default rules have been changed perhaps. Or maybe this is a new internal interface, not actually LAN?
What is the traffic in question?
What firewall rules do you have on that interface?
-
@johnpoz
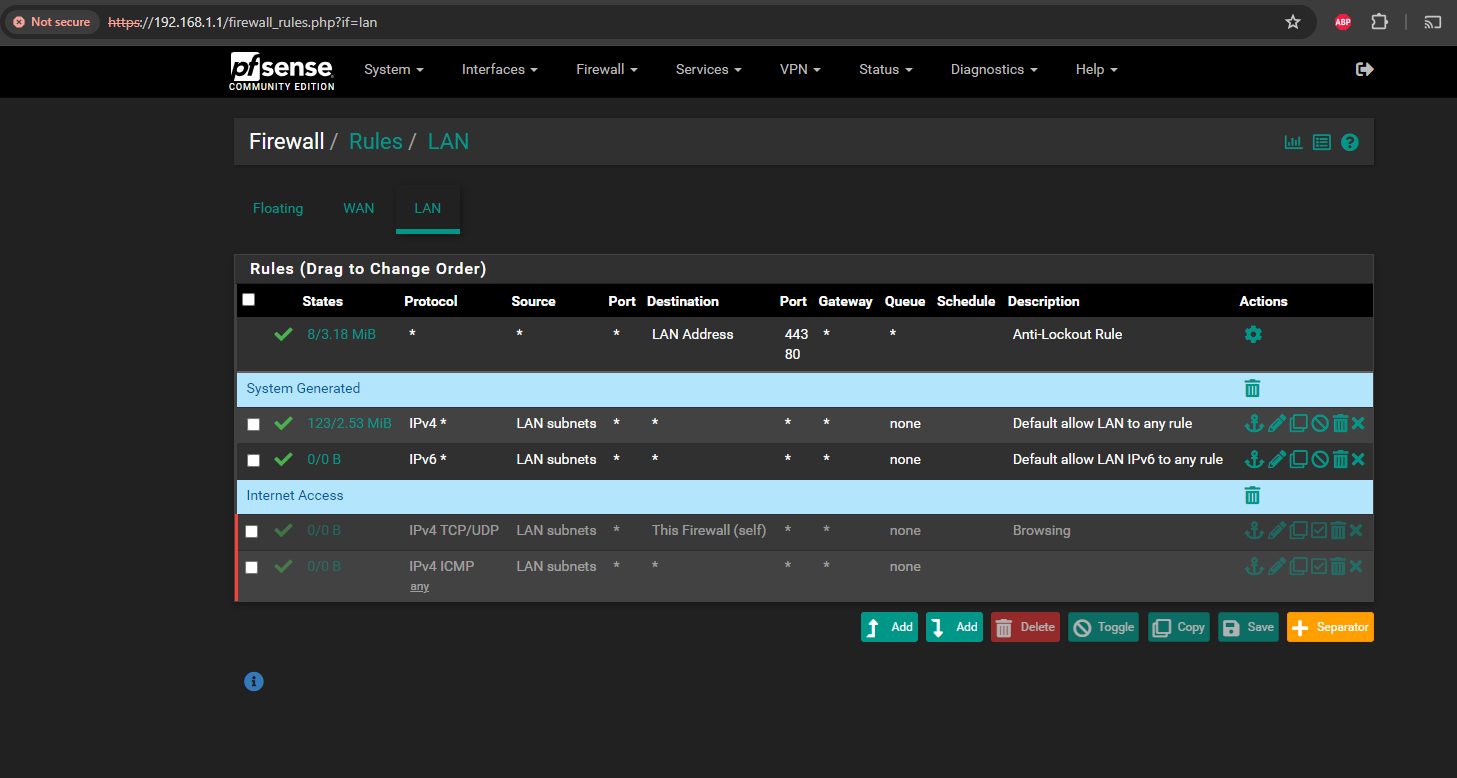
THe "Internet Access" ones were from a tutorial but they didnt work so I disabled them -
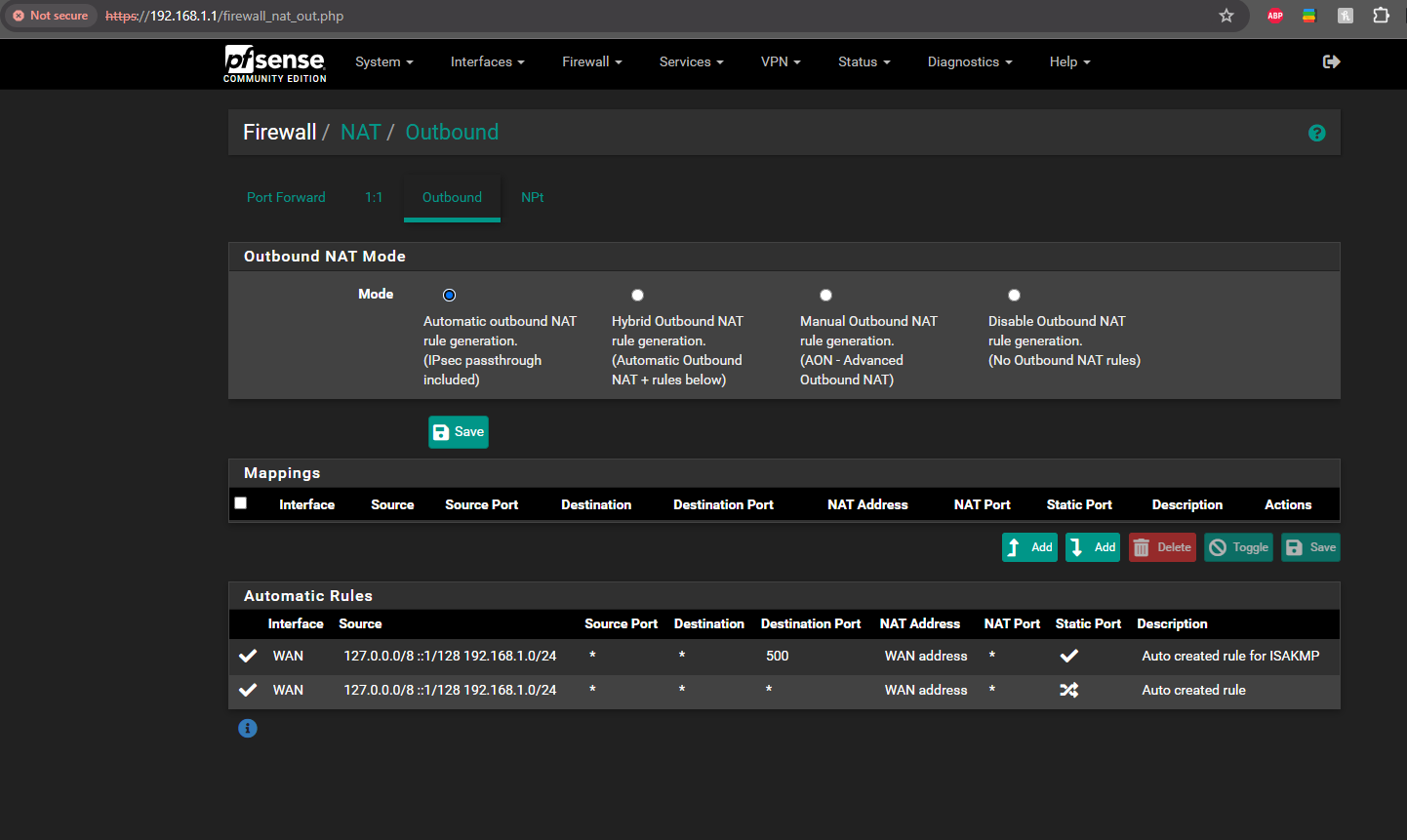
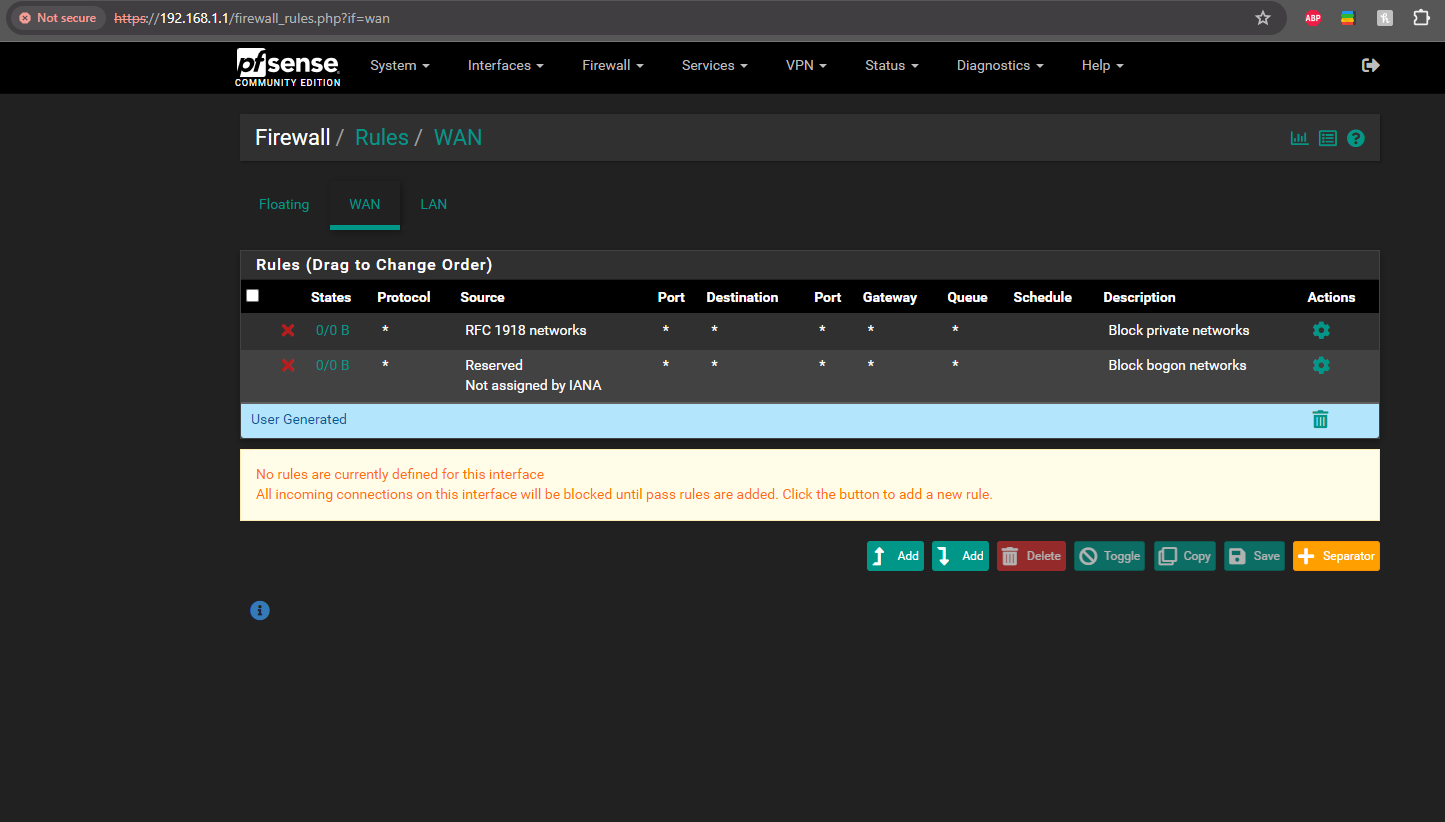
Als here are the WAN and NAT outbound rules.
I had played around with adding a pass rule in WAN, and looked over the docs, but came up empty so deleted it as part of reverting to system generated.
I am going AFK for abt 2 hours, thanks for your help so far!
-
@rakya so your rule on your lan is the default any any.. It currently shows you have a 123 states via that rule.. So it is allowing traffic..
if your saying you can not ping say 8.8.8.8 from a client on your lan network.. its not a firewall rule blocking it - unless you have rules in floating that would? But that would not be logged a default deny, that would be logged by the rule in floating that was blocking it.
There is nothing there that would prevent you from accessing the internet if pfsense has internet access via its wan.
But if your wan is the same network as your lan - that would be very problematic for sure.. What is the network on your wan.. Normally this would be some public IP 1.2.3.4 for example, if its a rfc1918 address that overlaps with your lan of 192.168.1/24 then yeah your going to have a bad day..
The only way something on your lan would be blocked by the default deny rule, is if its IP was not in the lan network.. For example if you had a device on your "lan" with and IP of say 192.168.2.x/16 while it could send traffic to pfsense on 192.168.1.1 to pfsense that IP is not part of the lan net and would not be allowed by the default rule, and would not be natted either..
-
Yup those rules look fine and they are opening and passing traffic.
What traffic is shown as blocked?
-
@johnpoz @stephenw10 So I am able to ping 8.8.8.8 from LAN client, still no google.com does that mean the issue is DNS?
Based on what was said abt a subnet conflict I moved my LAN IP to 192.168.0.1 (previously 192.168.1.1, which is also where my current router is, which will be converted into a switch/WAP if I am able to get pfSense working). Still not able to get through though. same ping behavior as before.
-
Yes sounds like a DNS issue now.
Make sure Unbound is running in Status > Services
Try resolving something in Diag > DNS Lookup.
-
@stephenw10 Unbound is running, and I found the following when doing the lookup
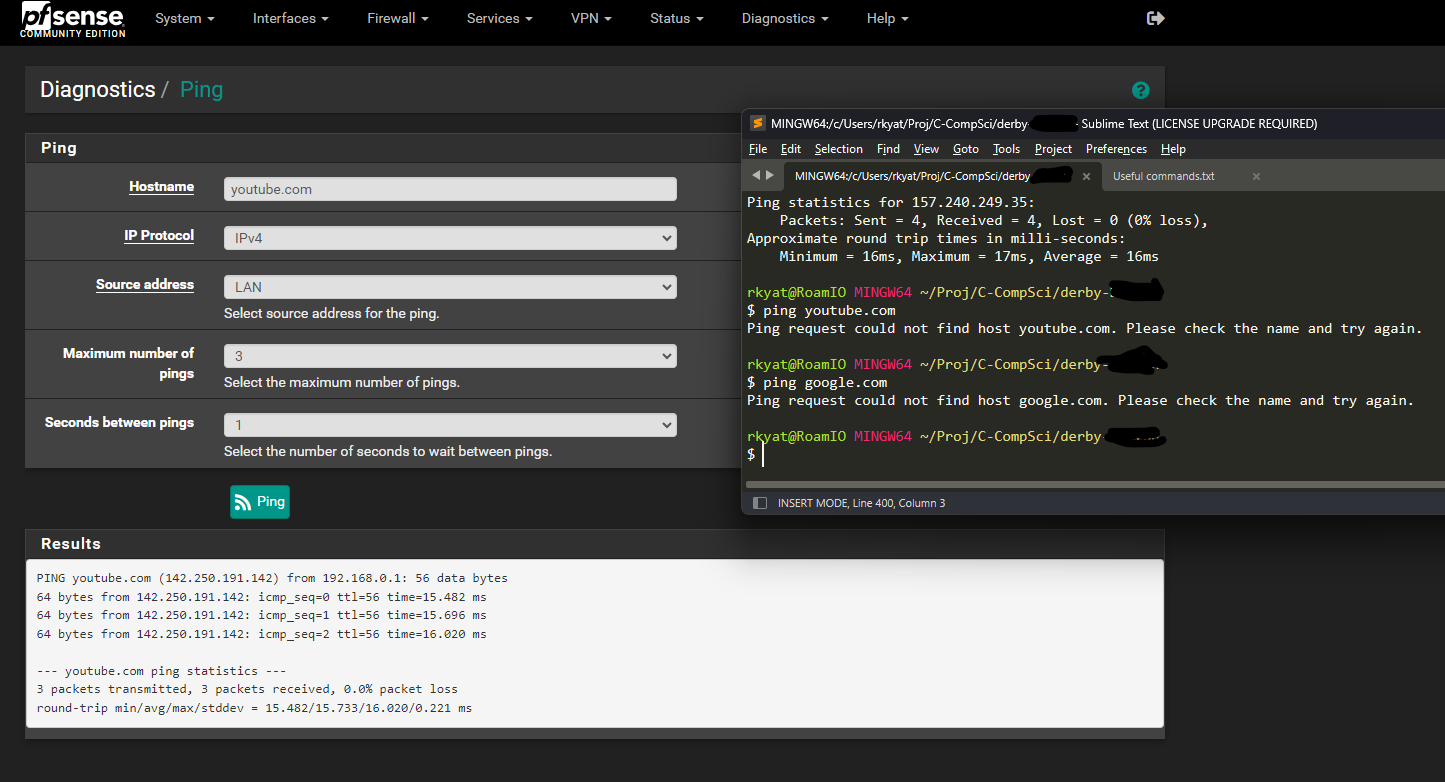
Somehow the issue is not present in the VMs LAN interface, but both my laptop and phone are unable to connect to the internet when hooked up to the VMs LAN -
@stephenw10 said in No internet on LAN:
Try resolving something in Diag > DNS Lookup.
Do that^. It will show how all the configured DNS servers are responding.
-
This post is deleted! -
@stephenw10 Here is the lookup
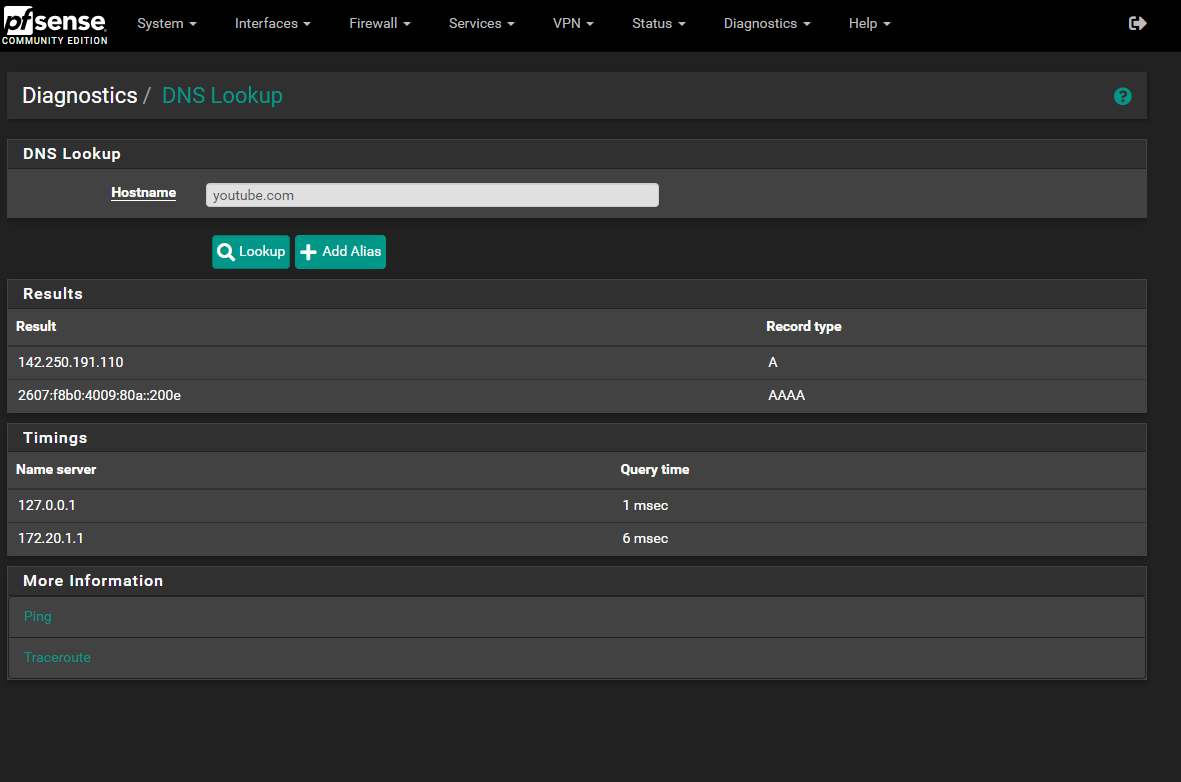
and I also did a traceroute
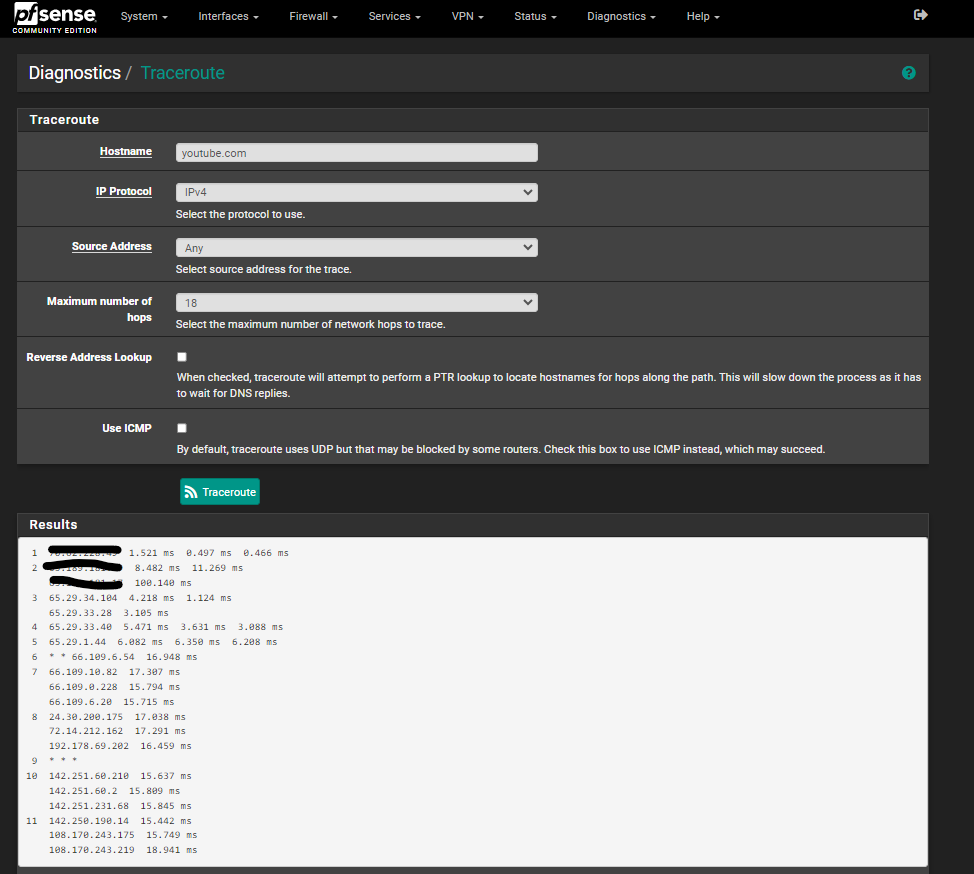
-
@rakya so what is not working.. You clearly can get to the internet if you can ping 8.8.8.8 and you can lookup something.. So what is not working?
-
DNS is failing on the LAN side client.
So check what the client is using for DNS. It would normally be passed the pfSense LAN IP to use via DHCP but that can be ignored/overridden on the client.
-
@stephenw10 I did a
ipconfig/allon my laptop and it seems to be saying the pfSense LAN IP is correctly set as the DHCP, and DNS provider, but i am still unable to ping google.com
@johnpoz in addition to being unable to ping google.com, i cannot browse the web, that is why I had believed that DNS was the issue, but am now unsure again... everything seems to be working great from within the VM, but the 2 clients I have tried are unable to navigate to anything except the webconfigurator. I will try a different ethernet cable.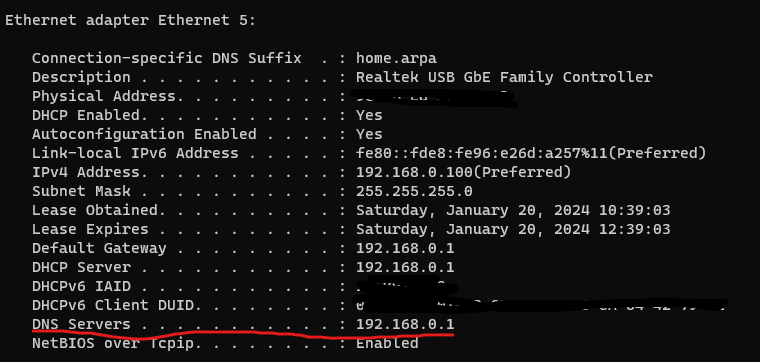
-
switching cables made no difference