Firewall blocking Synology MailPlus Server
-
Hi,
I'm trying to set up the Synology MailPlus server, but pfsense seems to be blocking outbound port 25.
I have tried creating a rule to allow port 25 but have obviously not done it correctly, as it is still blocked. How do I open port 25?
-
@aquinch
Is there an outbound NAT rule in place on pfSense for the NAS? -
-
@aquinch
Pretty nice. But without knowing the source subnets and the NAS IP, quite useless. -
-
@aquinch said in Firewall blocking Synology MailPlus Server:
but pfsense seems to be blocking outbound port 25.
Did you create a rule blocking anything outbound? Most ISP would block you from talking outbound on 25 to be honest. Unless you have a business sort of connection. The default out of the box rules on lan are any any.. There is no blocking in pfsense out the box for a client on pfsense lan talking to anything..
Are you running IPS?
Home users, other than sending spam don't normally need to talk outbound on 25..
What are you trying to do exactly? Are you wanting to use synology new notification sending via there servers? That wouldn't be using 25.. if it did, it would fail for many many users.. Because many isp block direct talking out 25 for their users.. To cut down on spam..
-
No, I don't have any rules blocking anything outbound. If my ISP were blocking the port, I believe the traceroute would show the connection passing the firewall and stopping at the ISP? But it seems to be stopping at pfsense.
I'm trying to create a mail server, and it communicates through port 25 with other servers. I'm not running any IPS. -
@aquinch said in Firewall blocking Synology MailPlus Server:
I'm trying to create a mail server, and it communicates through port 25 with other servers. I'm not running any IPS.
You can not send emails from residential internet anyway... it will be blocked almost everywhere.
-
@aquinch said in Firewall blocking Synology MailPlus Server:
, I believe the traceroute would show the connection passing the firewal
So your saying if you do a normal traceroute not calling out port, then it works showing you the next hop? What if you use say -p 80?
Sniff on your wan when you do your traceroute - do you see it send out? If your next hop is blocking, you wouldn't get an answer.. Doesn't mean pfsense blocked it.
-
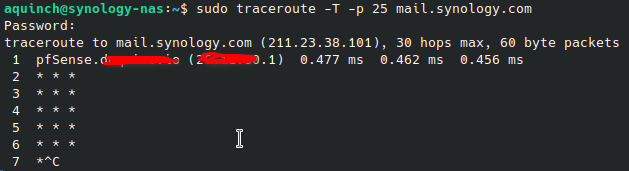
Running traceroute without the port I get this:

Maybe I don't know how to read traceroute properly, but I thought that the last hop was where the connection hit and stopped. So, if my ISP was the one blocking it, I would see it hitting the second hop at Optusnet. Which doesn't happen on port 25.
-
@aquinch the 2nd hop would be your isp, that first hop is your pfsense, next hop would be where you first hit your isp.
If they are blocking 25, then no you wouldn't get an answer, nor if they were blocking 25 would you get any answers past them, since they are blocking it..
if pfsense was blocking it would never leave pfsense wan, so just sniff on your pfsense wan to see if it went out.
But your isp blocking 25 would show exactly what your trace showed.. Nothing past pfsense..
https://networklessons.com/cisco/ccna-routing-switching-icnd1-100-105/traceroute
So I send a packet with ttl of 2, it would be answered at the 2nd hop.. But if they are blocking the port.. They could never answer because they never saw it, their firewall blocked it.. Then next hop 3, never goes anywhere past the 2nd hope because again they are blocking it.. So what you saw indicates a block right after pfsense.. If pfsense was blocking it would never enter pfsense to be answered.
So for example my isp doesn't block 25.. so your command.. from my client shows hops past pfsense and through my isp into the internet.
ash-4.4# traceroute -T -p 25 mail.synology.com traceroute to mail.synology.com (211.23.38.101), 30 hops max, 60 byte packets 1 sg4860.home.arpa (192.168.9.253) 0.566 ms 0.532 ms 0.516 ms 2 c3-0.rol-e6k1.nape.il.cable.rcn.net (209.122.32.1) 14.587 ms 7.544 ms 7.538 ms 3 static.rcn.com (216.80.79.9) 15.789 ms 16.144 ms 15.751 ms 4 hge0-0-0-1.core1.chgo.il.rcn.net (207.172.18.102) 44.661 ms hge0-0-0-0.core1.chgo.il.rcn.net (207.172.18.100) 44.642 ms 207.172.17.1 (207.172.17.1) 45.900 ms <snipped>Now I put in a block to 25 on pfsense.

ash-4.4# traceroute -T -p 25 mail.synology.com traceroute to mail.synology.com (211.23.38.101), 30 hops max, 60 byte packets 1 * * * 2 * * * 3 * * *But if I change that to an outbound block on my wan, so traffic can actually get to pfsense for it to answer with hey this ttl expired then..

ash-4.4# traceroute -T -p 25 mail.synology.com traceroute to mail.synology.com (211.23.38.101), 30 hops max, 60 byte packets 1 sg4860.home.arpa (192.168.9.253) 0.616 ms 0.603 ms 0.576 ms 2 * * * 3 * * * 4 * * *So unless you were doing a specific outbound block on your wan interface.. Your trace route is exactly what you would expect if your isp is blocking 25.. Which many of them do.. My old isp use too..
-
Hello!
Are you running the traceroute while shelled into your DS? I get flaky results running traceroute with the port option while shelled in.
You could try a different host and run putty/telnet...
telnet mail.synology.com 25
telnet mail.synology.com 587
...John

