Port forwarding to OpenVPN tunnel
-
Hi everyone,
I have to create a port forwarding from my public IP address WAN to a openvpn client computer where there is an HTTP webserver.The OpenVPN server inside pfsense works and I see the client connected, its address is 10.0.8.2.
I tried to simply add a NAT to thatvpn tunnel address and open a TCP testing port 8080:
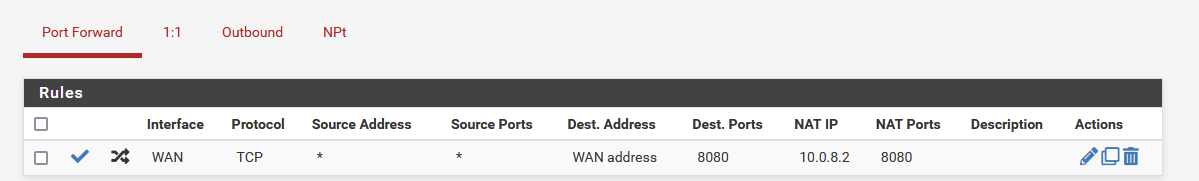
I tried from pfsense shell to telnet 10.0.8.2 to 8080 port and it works. I see HTTP replies.
However from the public ip address it is not working, I checked the firewall logs and the rule works, I see the connection from public ip to openvpn is passed.
What I'm missing? I thought it can be an asymmetric routing, maybe the vpn client (http server) replies using the wrong interface and not throught the vpn, but how can I detect it? What else can I do?
Many thanks.
-
@tobiascapin1
You have to masquerade the outgoing traffic on the VPN interface, otherwise the remote computer will send responses to it's default gateway.Alternatively you can route all upstream traffic of the remote client over the VPN.
-
@viragomann Thanks for your reply.
I would avoid to route all trafic beacuse it will stress the vpn server and increase the bandwith for nothing.How can I masquerade the outgoing traffic on VPN interface?
Is there a way to translate the source ip for those NATted packets to a source ip inside the vpn tunnel?
So the VPN client should not use the default gw but routes those replies to the tunnel. Am I wrong?Thank you for your help.
-
@tobiascapin1 said in Port forwarding to OpenVPN tunnel:
How can I masquerade the outgoing traffic on VPN interface?
Is there a way to translate the source ip for those NATted packets to a source ip inside the vpn tunnel?
So the VPN client should not use the default gw but routes those replies to the tunnel. Am I wrong?Yes, this is what masquerading is doing.
You have go to Firewall > NAT > Outbound and enable the hybrid mode if it is in automatic.
The add a rule:
interface: OpenVPN or maybe you have assigned a certain one to the instance
protocol: TCP or what you need
source: any
destination: network > 10.0.8.2/32
translation: interface address -
@viragomann great! Many thanks for your help.
I thought this translation was implicit for a NAT, but probably it is not. -
@tobiascapin1
No, that would be undesired in most cases and first of all, could be a security issue. So it's a no-go on real firewalls.
With masquerading, the destination device is not able to determine the true source IP of an access packet. Instead it only sees the interface IP of the device doing the NAT, in most cases the directly connected one.
So this is also a method to circumvent security settings and get trust to the accessing connection. -
@viragomann
oh yes, good point. I was confused by the fact that many times the NAT device is also the default gateway, so the masquerade is not needed. But it is not my case with openvpn.Many thanks again for explanation and support.