Limit web access for DMZ
-
Yup I would probably try to use ASNs there. It does rely on someone keeping them up to date though, which doesn't always happen.
A lot of companies have public lists of subnets they use and I'm pretty sure MS is one of them. Those are usually accurate. You can add them as a table alias or point pfBlocker at them to do it.
-
I appreciate @SteveITS and @stephenw10 for the feedback.
So INTUIT does have their own ASN so i can craft an IP permit around that.
MSFT is a bit more challenging but the solution is going to have to be to allow the ASN as well. I do prefer control internet access by domain as its more granular. If i use pfBlocker its all or nothing, right? Cant be specific on an interface.In the future, the ASN piece will be harder. I notice lots of companies use AWS. If I go ahead and permit Amazon I might as well remove the IP block list then. Unless theres something i can do that im not thinking of.
@SteveITS What do you have against WSUS? I think sysadmins use SCCM or something these days.
-
@michmoor said in Limit web access for DMZ:
If i use pfBlocker its all or nothing, right? Cant be specific on an interface.
You can use pfBlocker to generate aliases from list urls or ASNs. Then apply them in rules on whichever interfaces you want.
-
@stephenw10 said in Limit web access for DMZ:
You can use pfBlocker to generate aliases from list urls
hmm...how do i generate aliases from list urls? In pfBlocker?!?
i dont think ive ever done that.edit: You mean IPv4 Custom_Lists ?
-
Yes if you have a hosted list of IPs or subnets you can add that url as a custom list item. Like:
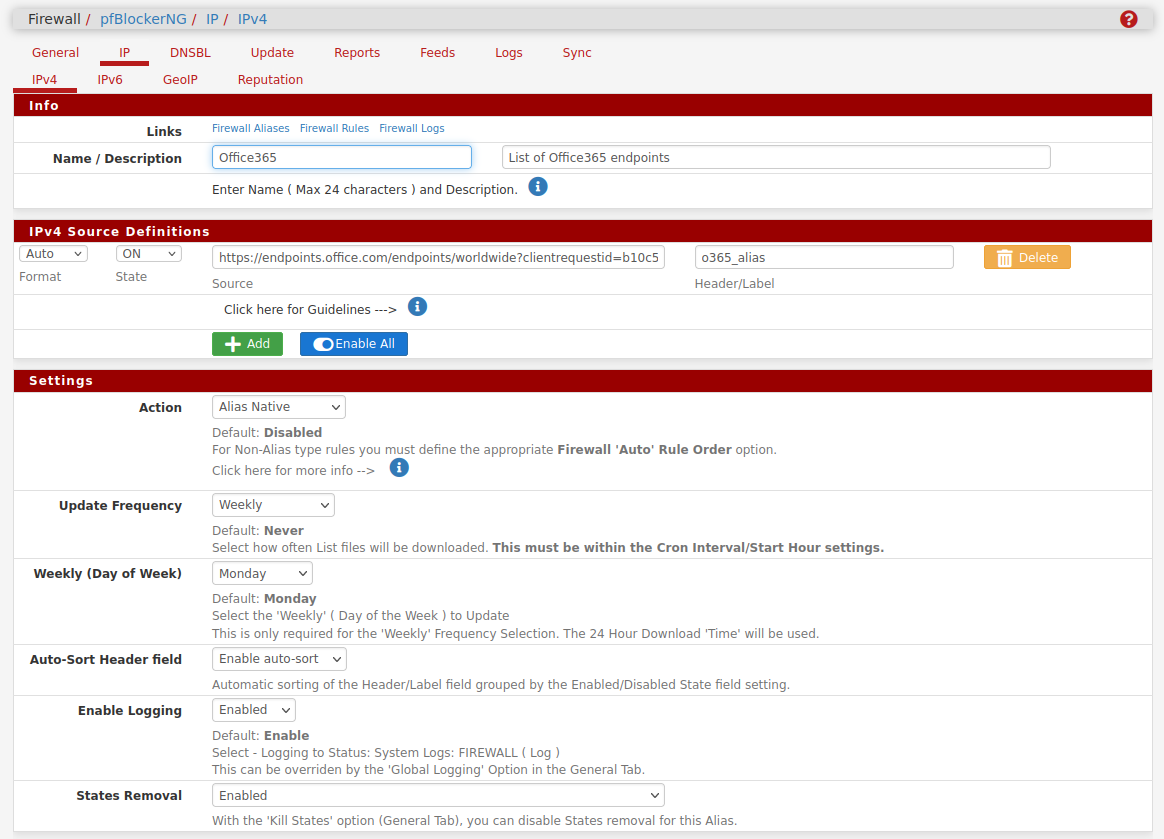
-
@michmoor said in Limit web access for DMZ:
What do you have against WSUS?
Whenever I saw it, a client we acquired had installed Small Business Server which had it by default. Various issues of the top of my head: C: partition from OEM too small for the large database, no one had auto-approved updates (so no updates ever installed), auto-approving categories downloads all updates (ref C: partition), database often gets corrupted if not cleaned, various third-party scripts to clean out/repair the database, etc. In summary most small businesses are way better served by just using Windows Update directly. Or letting us control updates for them as their MSP. :)
re: DNS, it's a bit error prone, but give the server its own pfSense router to talk to the Internet? No issue with asymmetric routing if there are no inbound connections...?
-
@stephenw10
Yep that actually may work.
Is there any support or way i can include wildcard domains like *.windowsupdate.com ? -
No, that url just points to a hosted list of IPs. pfBlocker pulls that list and creates a table alias from it. Then I can use that in rules.
There aren't any domains or fqdns there.
You'd need to use something in DNS-BL or in Unbound directly to filter a wildcard domain like that.
-
Ahh ok i was actually here in pfblocker. I thought thats what you mean but both solutions work.
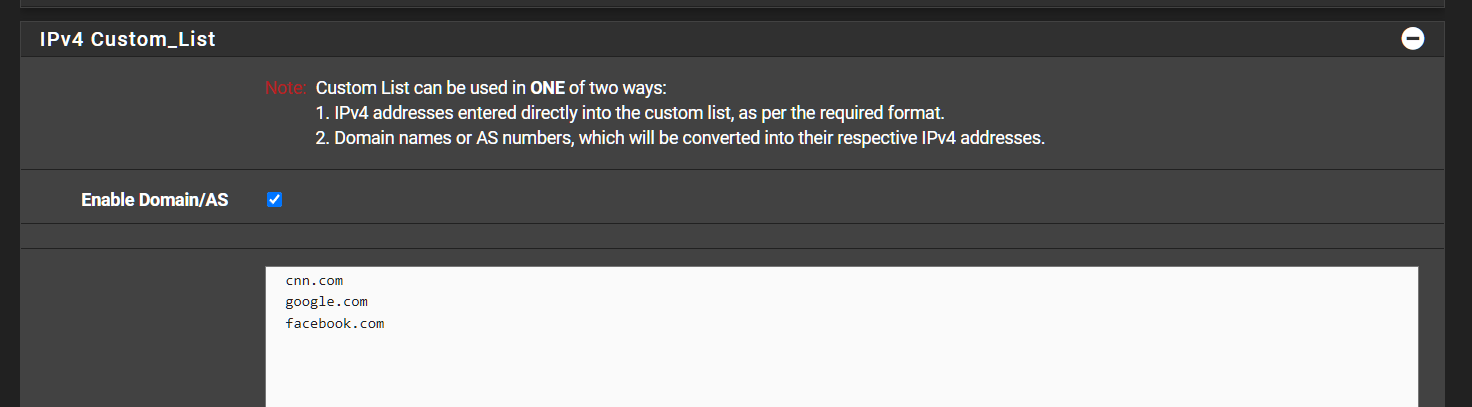
For that wildcard blocking then @SteveITS suggestion of unbound views might be the ticket.
-
Just want to say I appreciate the replies. There is documentation from the vendor on URLs and IPs to whitelist so that’s a win. IPs and Ports