DNS suddenly broken [on some VLANs]
-
I wrote the following to Nord. Lets see how it goes.
I don't understand how this issue has taken as long as it has never mind a further 2 months never mind 5 days more. Networking may be a black art but it follows very simple rules. Can you clarify what the issue you are working on is.
From my understanding the issue I am having can only be caused by Nord intercepting my DNS queries as you say on your website. 'NordVPN native applications automatically use NordVPN's DNS servers when connected to VPN.' I read this as you intercept my DNS and direct it to your DNS servers. Can you confirm if this is true or not.
This makes me concerned that Nord are collecting this data as it is valuable to marketing people. Can you confirm that you are not collecting any DNS data.
I look forward to hearing from you.
-
@DaveP-0 if they say they are not intercepting, ask them why when you query 1.2.3.4 through their network you get an answer.. When 1.2.3.4 doesn't answer dns..
Do a simple test dig @1.2.3.4 www.google.com if you get an answer you were intercepted. Now it could be your own interception? Or redirection if you will.. But from the other thread(s) about this pretty sure someone did that test and got an answer, which is a smoking gun that dns was redirect somewhere, and if your not doing it and your routing your traffic through a vpn.. This screams they are doing it, unless the ISP of their exit IPs are doing it??
-
@johnpoz Thanks for that. I'll use that if they deny it. I'll keep everyone informed.
-
@johnpoz said in DNS suddenly broken [on some VLANs]:
if they say they are not intercepting, ask them why when you query 1.2.3.4 through their network you get an answer.. When 1.2.3.4 doesn't answer dns..
Do a simple test dig @1.2.3.4 www.google.com if you get an answer you were intercepted. Now it could be your own interception? Or redirection if you will..
While doing the dig @1.2.3.4, join a full packet capture on the VPN client interface, the one connected to Nord ?
This should dhow the DNS to 1.2.3.4 going out, and info coming back that 'someone' is answering ... -
Just got this reply ignoring all but one of my questions. I'll be replying to this one.
Thank you for your reply.
NordVPN strictly keeps no logs of your activity online.
That means we do not track the time or duration of the online session, and neither do we keep logs of IP addresses or servers used, websites visited or files downloaded.
In other words, none of your private data is logged or saved at any time.
Unfortunately, we are still experiencing some issues with custom DNS addresses, our developers are aware of the issue and are working to resolve it.
We would rather not give you an estimation when we do not actually have one for certain.
Let us know if you have any further questions in the mean time.
Please note that our support is available 24/7, you can always contact us via email or chat here!
Do not hesitate to drop us a message in case of any inquiries!
-
As per their last sentence I dropped them this.
Thank you for your response. I understood that Nord were not selling any data so it is good that you have confirmed that and I understand you do not want to give an eta on fixes.
I did note that you had not responded to my other questions so let me ask them slightly differently.
1 - Is Nord redirecting my DNS queries to the root servers and stopping me from performing my own root DNS searches?
2 - What exactly is issue with custom DNS addresses that you are taking so long to resolve?
-
I wrote to them again
I was expecting the security response for the issue so I'll let that go to save time.
You didn't answer all my questions though. I also asked if Nord is intercepting my DNS queries. All the tests I have done point to that
happening.Can you confirm if Nord intercepts my DNS queries or not.
They have just responded with;
Thank you for your reply.
To clarify, when you connect to the VPN server, our DNS are automatically assigned.
Feel free to contact us if there is anything else we can assist you with!
We offer customer support twenty-four hours a day, seven days a week.
The ticket will be re-opened automatically if you reply to this email.
Which is the best I'm going to get although it didn't answer the question. So they have an issue that they won't tell us about for security reasons. They kind of say they are assigning my DNS. They also say there is an issue with DNS and I can't do anything about it and have no idea when they will fix it. If they ever do.
So next question. I have PfSense set up to automagically send everything through Nord as per their configuration guide for PfSense.
How can I send my DNS queries through to my ISP instead who does allow me to use the root servers for resolving queries. I have no idea where to start. According to my system all items on port 53 are forwarded through the VPN.
-
@DaveP-0 Just go to Services > DNS Resolver and set the outgoing network interface(s) for unbound to only your WAN, and tick the
Strict Outgoing Network Interface Bindingcheck box:
A shame that they're punting on a real explanation, but also rather expected as you say. Although it is somewhat curious that they seem to acknowledge that there is as issue as opposed to just saying everything's working as it should. It will be interesting to see whether there are any further developments. I plan to periodically attempt to turn off forwarding mode and check whether it starts working again at some point. I'll be sure to report back here if it does.
-
@DaveP-0 said in DNS suddenly broken [on some VLANs]:
To clarify, when you connect to the VPN server, our DNS are automatically assigned.
Nope that is not what they are doing - they are intercepting.. And the big brains running that outfit didn't think it through that interception is easy to spot and will break shit like dnssec, which is one of the things dnssec is suppose to do, validate your talking to the actual authoritative ns.. Which when your intercepting clearly your not..
Using their "app" ok assign your dns away.. But if I am routing traffic through your vpn - you shouldn't freaking touch it..
Why anyone sends their traffic through these money grabbing scare mongers is beyond me.. The whole VPN service scam that blew up over night is just horse shit all the way down.. They don't give too shits about your privacy or your security.. All they are after is a drop dead simple way to get people to send them money for doing nothing..
The only value they provide is the ability to circumvent geo IP restrictions.. And most of the services are starting to block the big boys.. So that money tree is going away..
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
V viragomann referenced this topic on
-
P panzerscope referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
Hi Everyone, It looks like I also have the same issue.
I have setup multiple VPN clients on my pfsense firewall. Using DNS Resolver as a resolver, and only selected the "VPN Interface" in the "Outgoing Network Interfaces". This setup has been working fine for years (Since I have set this up, for more than 6 years). The DNS issue started on 3rd March, 2024. I was scratching my head.
Got the DNS temporary fixed by selecting "WAS" in "Outgoing Network Interfaces".
Hopefully they fix this issue soon. -
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
I debated whether to open a new topic for this, but as it's possibly related I figured I'd try resurrecting this thread first.
So it seems pretty clear that Nord had decided to never not hijack DNS :) Which is whatever, but unbound in forwarding mode through the VPN client iterfaces works. However, I recently realized that I'm constantly logging (apparent) blocked inbound connections from the Quad9 DNS servers to the VPN client interfaces:
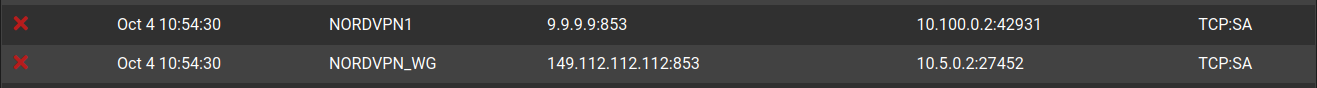
Is it clear to anyone that this is somehow an artifact of Nord's hijacking? My expectation, I think, would be:
- unbound forwards to 9.9.9.9 and/or 149.112.112.112 via one of my two VPN client interfaces.
- The Nord server intercepts the DNS request and routes it to its own DNS servers instead (or maybe its own recursive resolver)
So I wouldn't think the request would ever actually even reach a Quad9 server, but then why would I be seeing blocked inbound connections from them?
Now astute observers may ask: if Nord is intercepting all DNS anyway, why don't I just set my system DNS servers to which unbound will forward to be Nord's DNS servers? Well, I've found that if I do that, I run into problems with streaming services like Netflix (even for clients that I policy route to avoid the VPN for most traffic, I often still have them use the pfSense box as their DNS server so that is goes through pfBlockerNG).
So there is some substantive difference between forwarding to Nord's DNS servers via not Nord's DNS servers that I do not grasp.
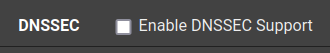
I should also note that I have tried with and without "Use SSL/TLS for outgoing DNS Queries to Forwarding Servers" enabled. DNSSEC is disabled since I'm in forwarding mode. Oh and also, even when I set Nord's DNS servers as the system DNS servers to forward to, I then see blocked inbound connection attempts from them.
Glad to provide more configuration details upon request, just hoping someone may have a better/any interpretation of exactly what's going on here. Thank you!
-
Some:thought :
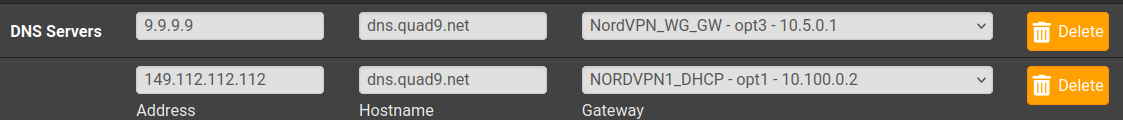
9.9.9.9:853 ... are you sure ? Checked that with quad 9 setup guidelines ?
Because you use 853, which means DNS over TLS (so, side note : TCP only) you wouldn't be using 9.9.9.9 but its host name = dns9.quad9.net.
On one side : dns9.quad9.net will resolve to 9.9.9.9, and this DNS server will use a certificate stating that it is "dns9.quad9.net" so unbound knows that it talks to dns9.quad9.net over a secured connection, just like .... https !
I don't think Nord can intercept that one, as unbound would know about it.This :
Is your pfSense blocking on your side :
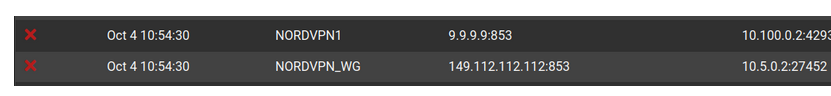
pfSense can't show blocks that happen on Nords side.
@TheNarc said in DNS suddenly broken [on some VLANs]:
Well, I've found that if I do that, I run into problems with streaming services like Netflix
If I was Netflix, I would block any DNS requests coming from known DNS servers like the ones coming from Nord.
Netflix want to know your real IP.
Netfklix hates VPNs (and does everything to make live hard on people using a VPN ^^ for the obvious reasons )Btw : the lines above are very IMHO of course.
I'm not 'Netflix'.There is no need to tunnel Netflix traffic over a VPN. The info is known, not really 'private' and all the traffic goes already over a TLS connection.
@TheNarc said in DNS suddenly broken [on some VLANs]:
"Use SSL/TLS for outgoing DNS Queries to Forwarding Servers"
Which also means you have to use destination port 853, which is the assigned port for DNS over TLS.
@TheNarc said in DNS suddenly broken [on some VLANs]:
system DNS servers to forward to, I then see blocked inbound connection attempts from them
Who is blocking here ? (see above ^^ )
@TheNarc said in DNS suddenly broken [on some VLANs]:
The Nord server intercepts the DNS request and routes it to its own DNS servers instead (or maybe its own recursive resolver)
Exact.
The 'normal' TCP and UDP destination port 53 traffic "any destination IP" will do, they will intercept.
And as no one has said the contrary so the same old song applies : because your DNS data is worth $$ to them, it goes out to the highest bidder.Btw : when you forward to a DNS server like 9.9.9.9, this means that your very last traffic that was 'visible' on the Internet is now encrypted under TLS.
The rest was already TLS (mail, web, apps, whatever).
So, for that, no need to use a VPN.Last but not least : when you forward, you lose DNSSEC.
Me, imho, prefer, by far, DNSSEC. -
@Gertjan Thanks for the quick reply.
9.9.9.9:853 ... are you sure ? Checked that with quad 9 setup guidelines ?
I'm not sure I understand the question here. As far as I can tell I have it configured properly:
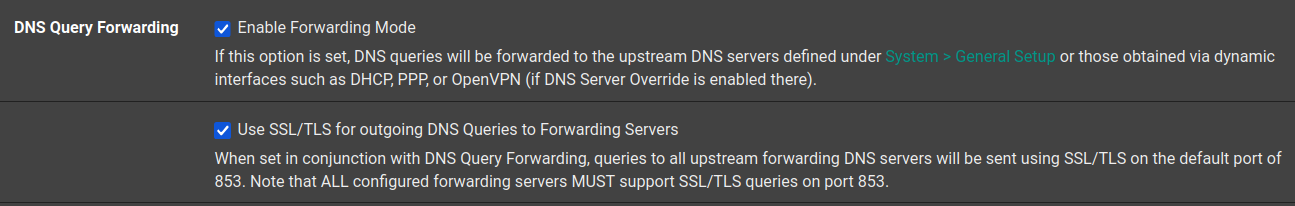
Is your pfSense blocking on your side :
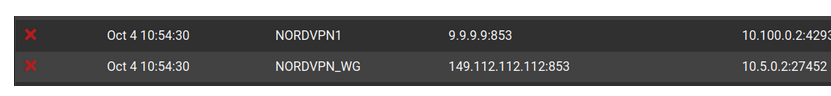
pfSense can't show blocks that happen on Nords side.
I understand this, and that it's me blocking these inbound connections from the Quad9 servers. What I don't understand is why I'm getting inbound connections from the Quad9 servers. If my outbound queries to the Quad9 servers via Nord are indeed being hijacked by Nord, then the queries should never even reach the Quad9 servers, so why would they be reaching back out?
If I was Netflix, I would block any DNS requests coming from known DNS servers like the ones coming from Nord.
Netflix want to know your real IP.
Netfklix hates VPNs (and does everything to make live hard on people using a VPN ^^ for the obvious reasons )Absolutely :) Makes perfect sense, but again, if Nord is hijacking no matter what I set my system DNS servers to, then I would expect to see the same behavior (i.e. Netflix is unhappy) no matter what I set my system DNS servers to. But I don't . . . Netflix is only unhappy if I set my system DNS servers to Nord's DNS servers, but it works if I set them to the Quad9 servers. So that coupled with the point from above makes me think that I don't really understand exactly what Nord is doing with DNS traffic, and that they're at least not hijacking it all in exactly the same way.
There is no need to tunnel Netflix traffic over a VPN. The info is known, not really 'private' and all the traffic goes already over a TLS connection.
Yeah, on LAN hosts using Netflix I policy route to avoid going through Nord for non-DNS traffic. But their DNS queries still hit pfSense directly, and in turn go to unbound and (as it's configured now) out the Nord client gateways.
Last but not least : when you forward, you lose DNSSEC.
True, but the origin of this long thread was a change on Nord's side that outright blocks connections to the root servers. So if you set Nord client gateways as the outgoing interfaces for unbound, you're forced to use forwarding mode.
But even then, it seems there is odd behavior. Again, mostly what I'm wondering is why are the Quad9 servers making inbound connection attempts to my Nord interfaces (which to your point I (pfSense) am then blocking)? If all my DNS queries that go out via my Nord connection are intercepted by Nord and re-routed to their own DNS servers or resolvers, then the Quad9 servers should never see those queries, and therefore should not be making any inbound connection attempts to me.
So maybe that (partially, at least) answers my own question, if just by virtue of seeing these blocked inbound connection attempts from the Quad9 servers indicates that Nord is not in fact hijacking all DNS queries. That may also explain your point about "how could forwarding with DNS over TLS be working if Nord was hijacking?".
But supposing they're not hijacking, and are just dutifully forwarding my DNS queries to the Quad9 servers. It still doesn't make obvious sense to me why I would be seeing inbound connection attempts from the Quad9 servers. Wouldn't their responses to my queries just be part of the flow already established by my outbound queries to them, not completely distinct inbound connections?
-
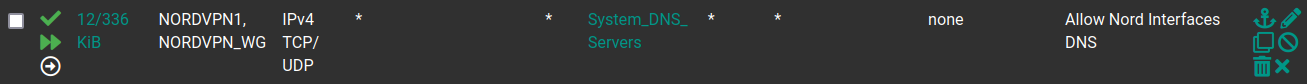
Reporting back. Creating a "quick" floating firewall allowing outbound access from my Nord interfaces to my System DNS servers seems to have gotten rid of these blocked inbound connections. It's not clear to me why, but maybe it will be to someone else . . .