Tailscale and Multi-WAN
-
Hi!
Is there a way to route Tailscale traffic over a secondary WAN connection? Has anyone done this and can point me into the right direction?
I have tried setting a different gateway group in firewall rules and also playing with static routes, but haven't solved this yet.
If there is an easy way to set a different gateway, it would be great. Because of my limited upload speed, I got a second WAN connection for offsite backups. Site-to-Site VPN with Tailscale is easy to set up and the router on the remote site only supports outdated/slow IPsec algorithms, so Tailscale would be preferred, but the traffic would need to go over the second WAN connection.
-
@andreas_e Did you ever find a way to do this? I am looking for the same solution.
-
@egates Kinda.
After hours of watching Christian McDonald's videos about WireGuard + Tailscale, I just gave up because it is not easily doable to bind WireGuard to a specific interface. I switched back to IPSec (and OpenVPN in one scenario) which gives me more control over which interface to use.
-
@andreas_e Have you tried to create a policy rule for the Tailscale subnet router?
Simply create a LAN rule using the LAN IP (not the Tailscale IP) of the server running Tailscale.
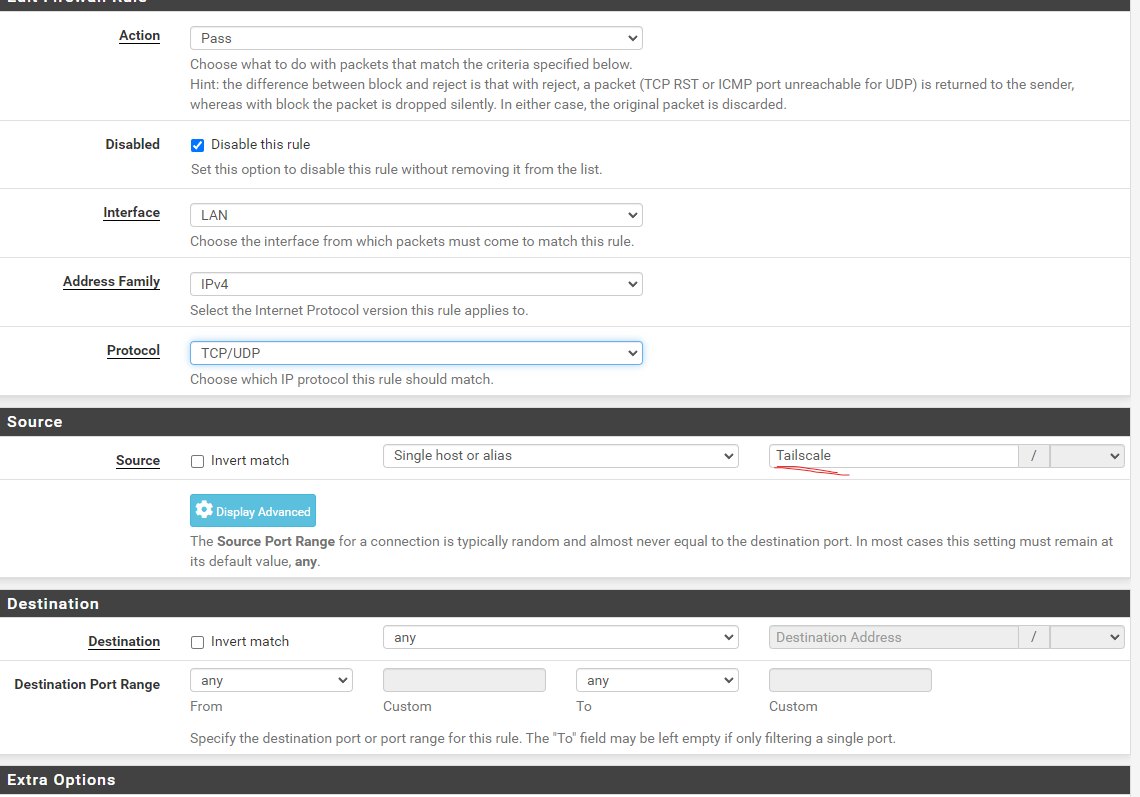
Then expand the Advanced section and select your second WAN under Gateway.
That's it, now all traffic to that entire node, including the Tailscale tunnel, will go via the second WAN.
-
@andreas_e I just realized you are probably running Tailscale on pfsense, which is a different situation altogether...
So what I suggested was based on having Tailscale installed on a separate machine, like a VM or a Raspberry Pi, and set up as a "Subnet Router". Then it is the IP of that machine which you set as the host (Alias) in the FW rule as shown in the picture above.
All you need to do is to define and approve your subnet route for the pfsense LAN.
I have tested towards our summer house where we have a second WAN (LTE) as failover, and can verify that it does indeed work...
-
I ended up setting up a tailscale LXC on proxmox to achieve this. Thanks for the suggestion @Gblenn!
-
@egates Cool, glad that you got it working!