global IPV6 addresses are not routed into the LAN and to the client
-
I have the following problem.
I currently have 3 Internet connections WAN,
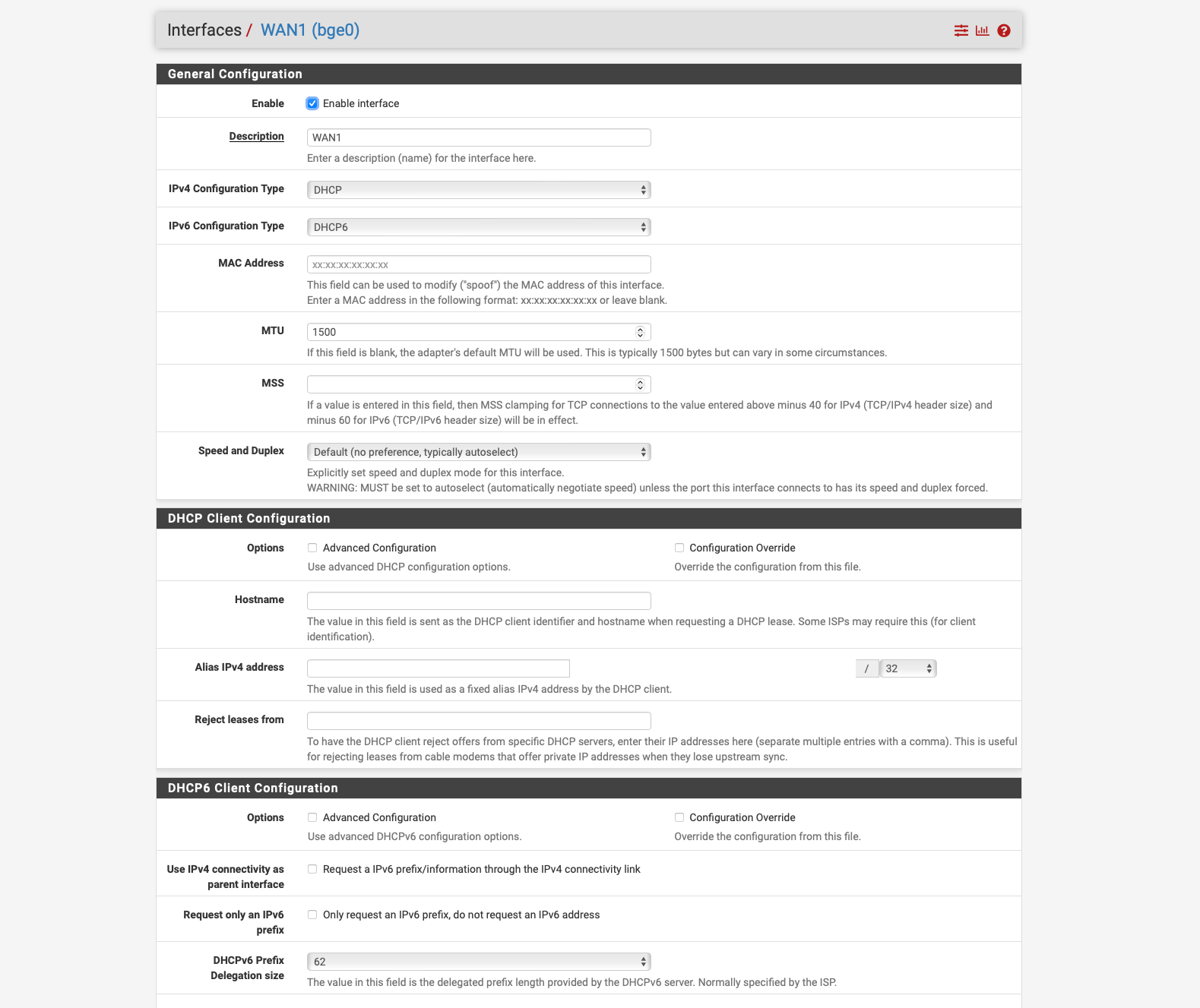
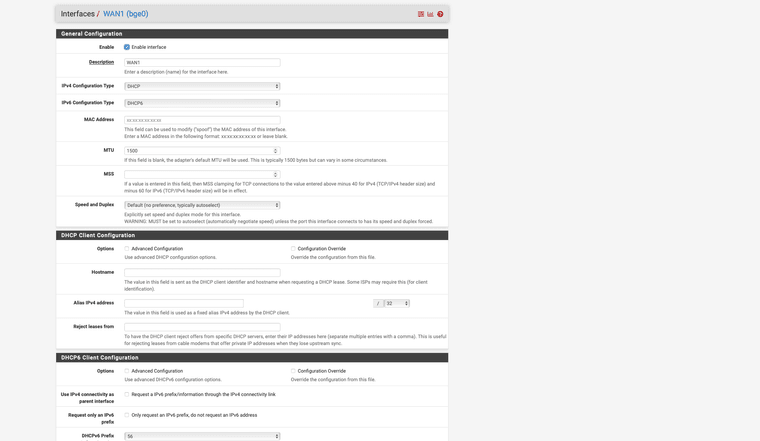
WAN 1 Cable internet Vodafone Germany 1000 Down 50 UP Static IPV4 and IPV6 per DHCPv4 and DHCPDv6 Native Dual Stack no DS Lite.
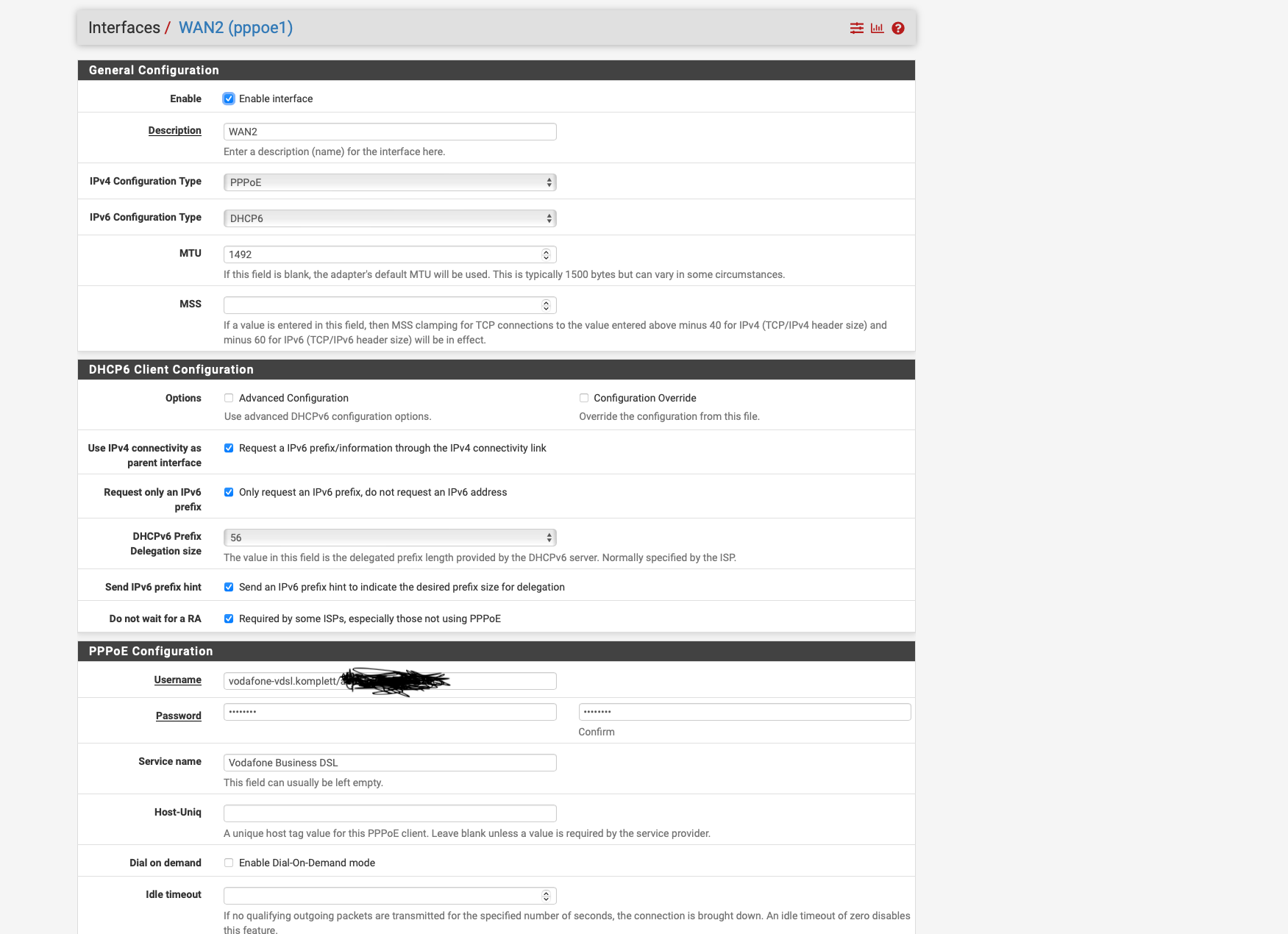
WAN 2 VDSL 175 down 46 UP Native Dual Stuck per PPPOE with VLAN TAG 7 no DS Lite
Mobile 4G /5G only Public IPV4 without Static IP only DHCP.
I would like to configure / have partially configured the following.
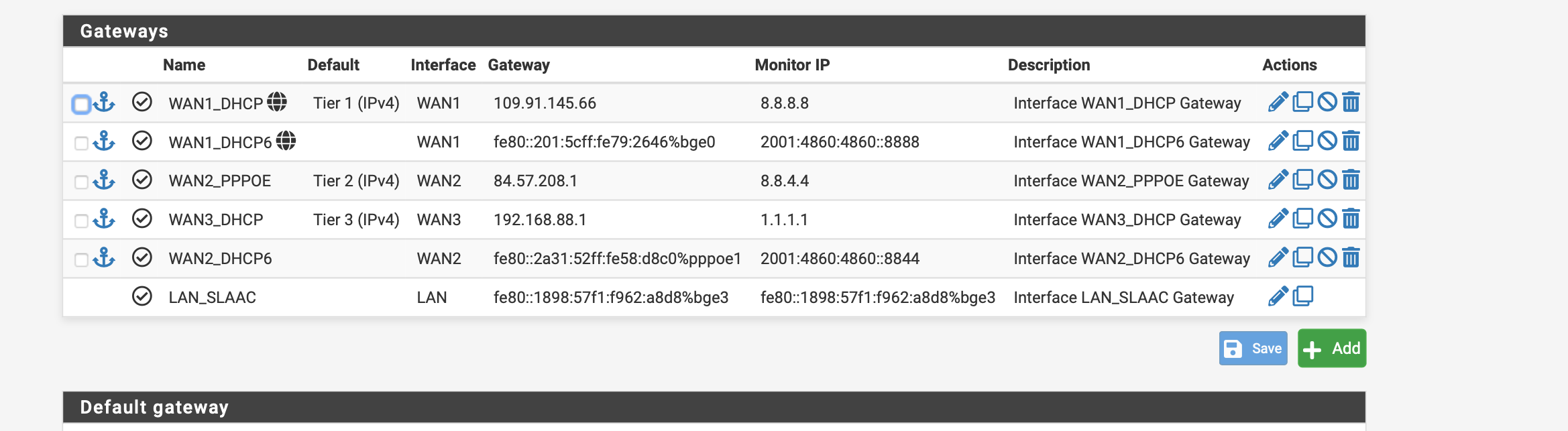
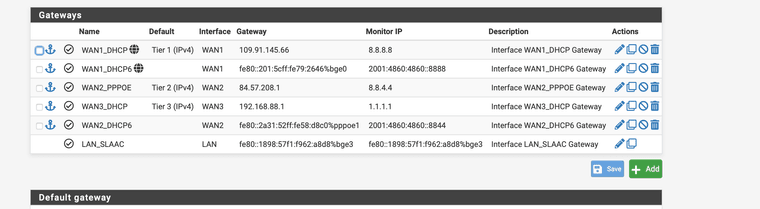
I would like to use WAN 1 as tier 1 I have configured this way I would like to use VDSL as tier 2 already configured.
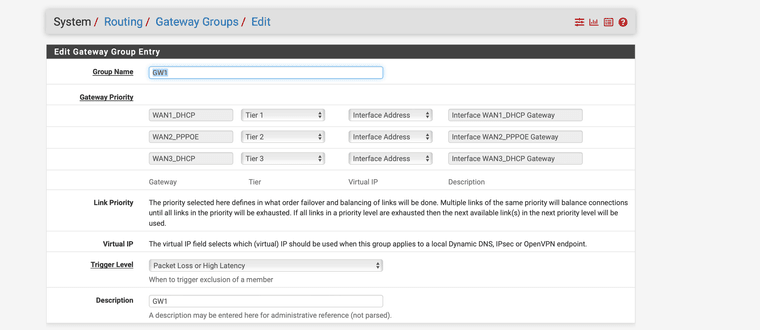
I would like to use WAN 3 as tier 3.I have created a gateway group and added the DNS server and the DNS resolver.
Furthermore, I have added the Google DNS IPV4 and IPV6 as ping where the link should be recognised as down by packet loss.
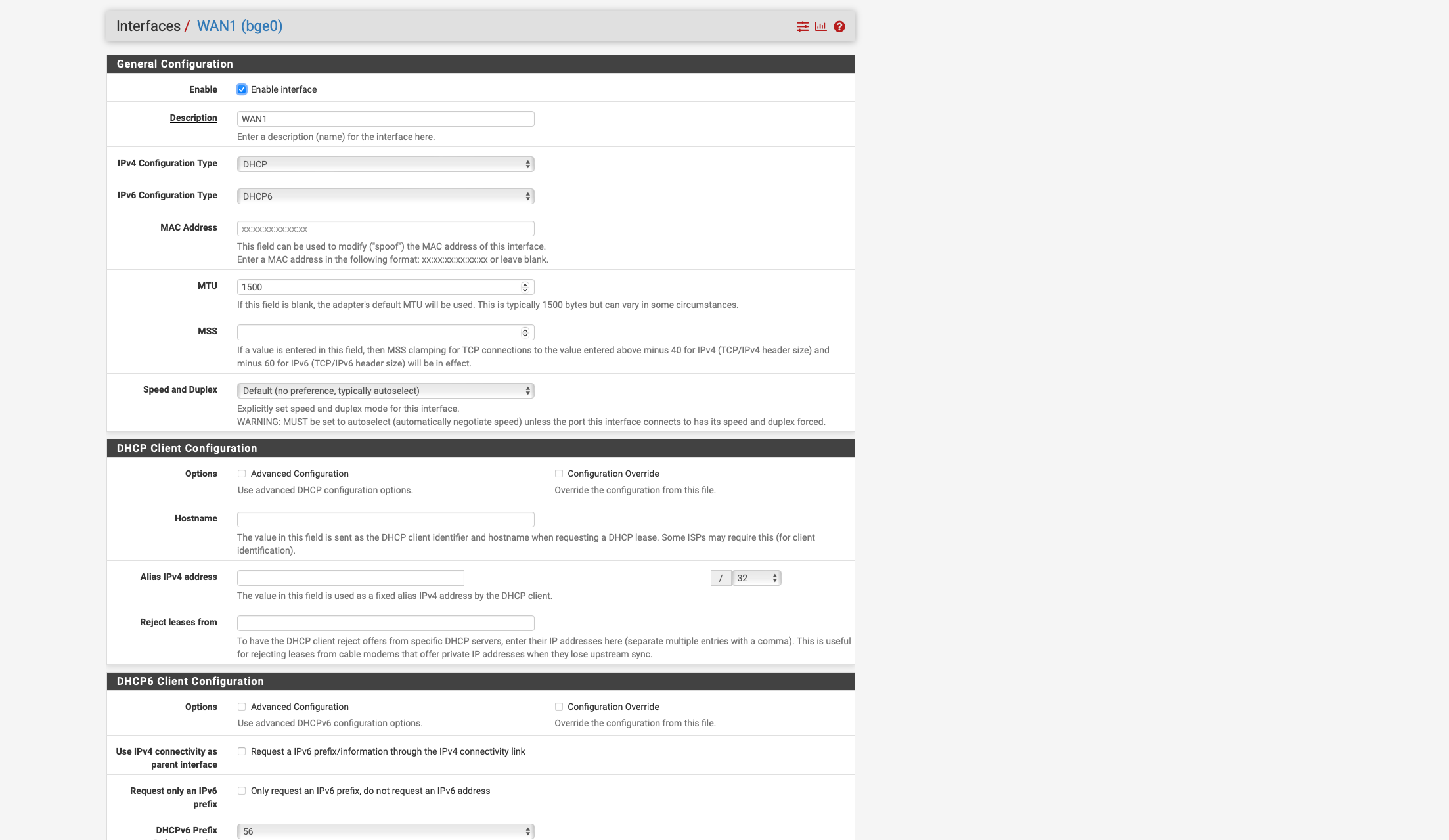
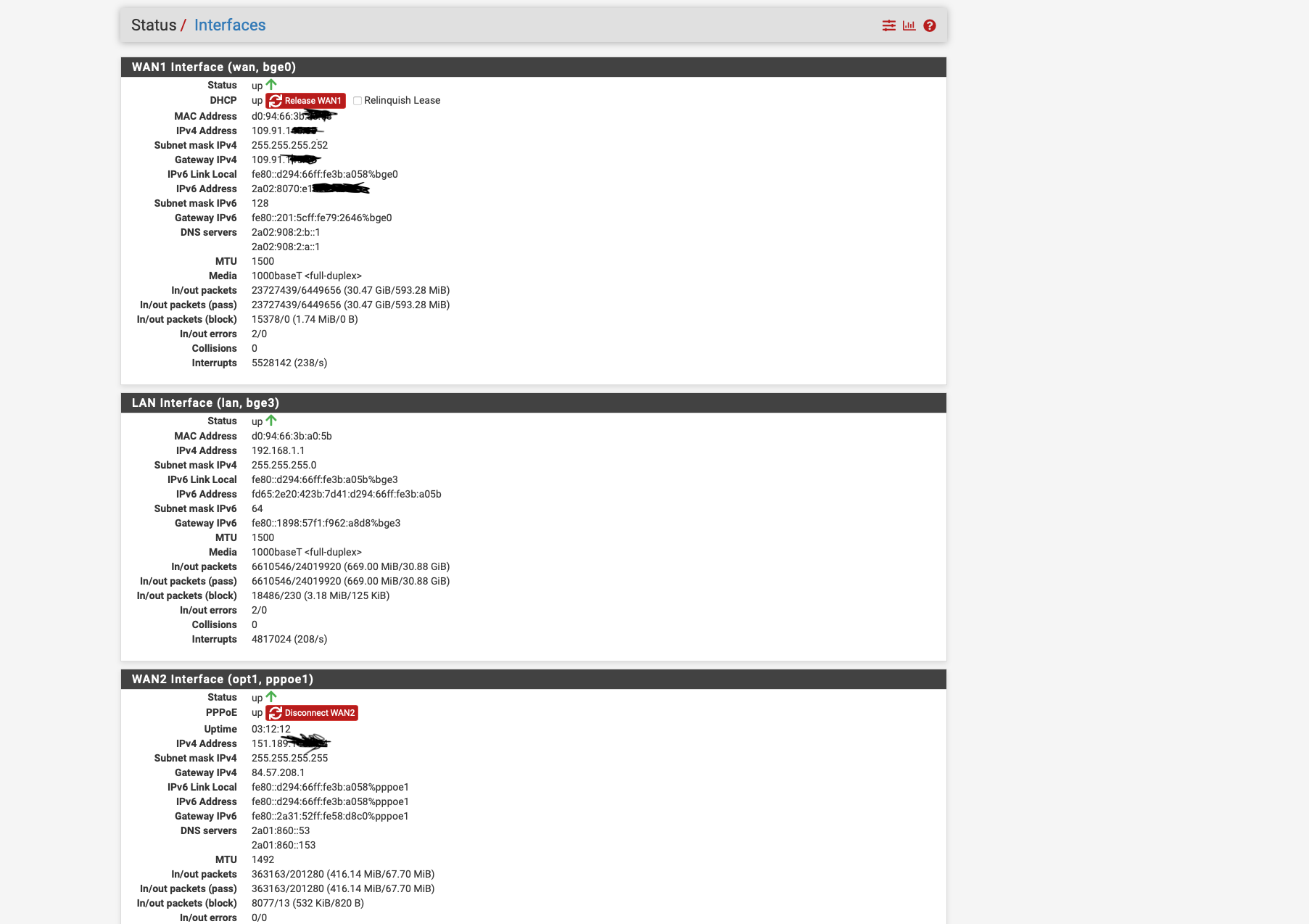
Currently I have the problem that I only get a LINK Local FE80 address assigned by VDSL via PPPOE and I don't know exactly why actually the PFsense should retrieve the /56 prefix via Autoconf via DHCPDv6 and assign a Global IPV6 address and actually on LAN routes so that the clients have IPV4 and V6.
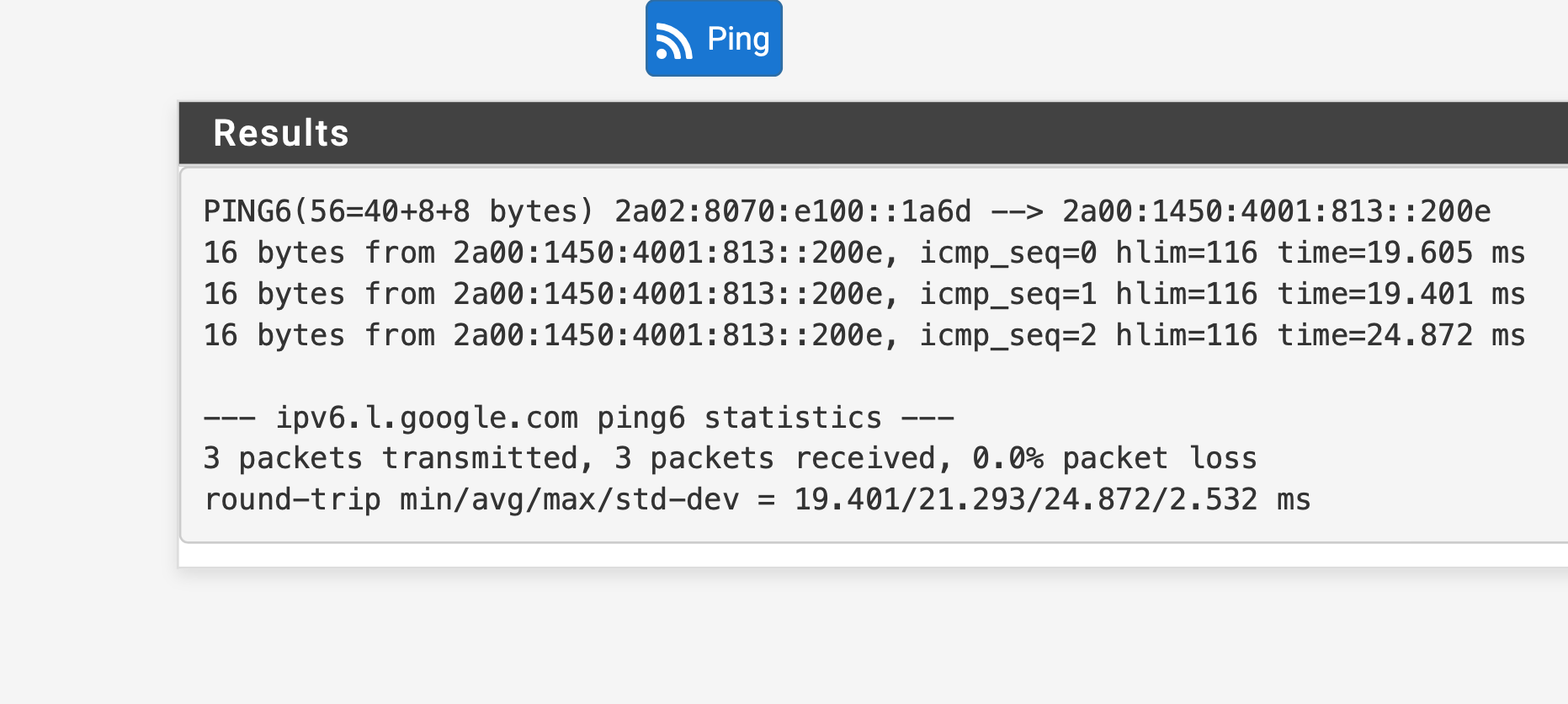
ping to ipv6.google.com works via gui.The second problem is that I neither get the Global IPV6 addresses from the Cable internet connection on LAN nor from the VDSL.
See screen shots I think I have almost everything correct but I seem to be missing something and need help.
as you can see on the screen shot where you can see the interfaces status, WAN 1 did not request a 56 prefix but again a 128 prefix like during installation.
-
@Globaltrader312 Don't do NAT for the Firewall itself, don't do NAT for IPv6 in general.
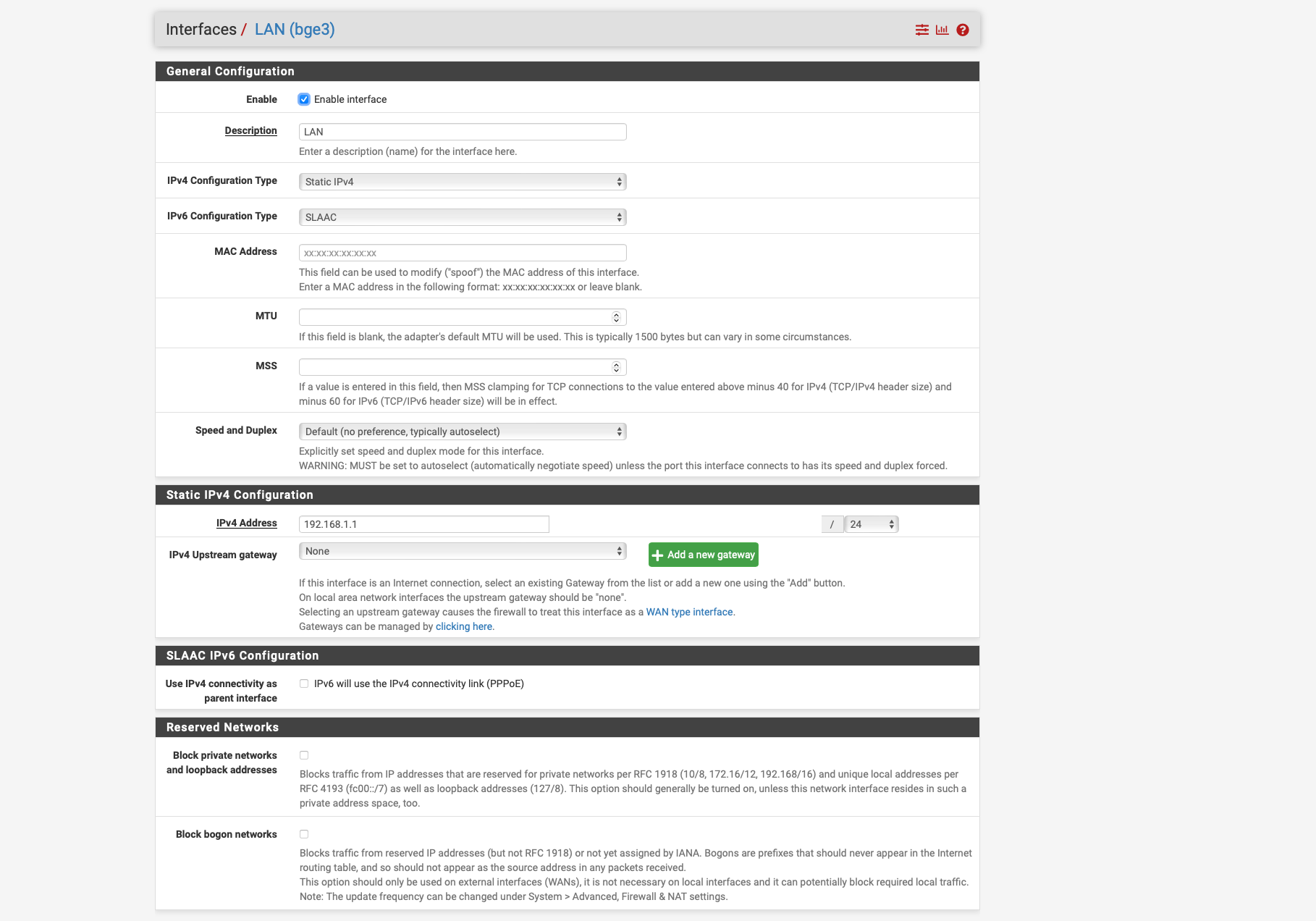
IPv6 on the LAN interface has to be set to Track, not SLAAC. -
@Bob-Dig
tried it with Track interface, but I can only select either WAN 1 or WAN 2 as the parent interface, and that didn't work either, which is why I selected SLAAC for testing, but unfortunately that didn't work either.
it has to work so that when WAN 1 goes down I can then use the IPv& prefix from the DSL including IPV4 and vice versa when WAN 1 is UP again.
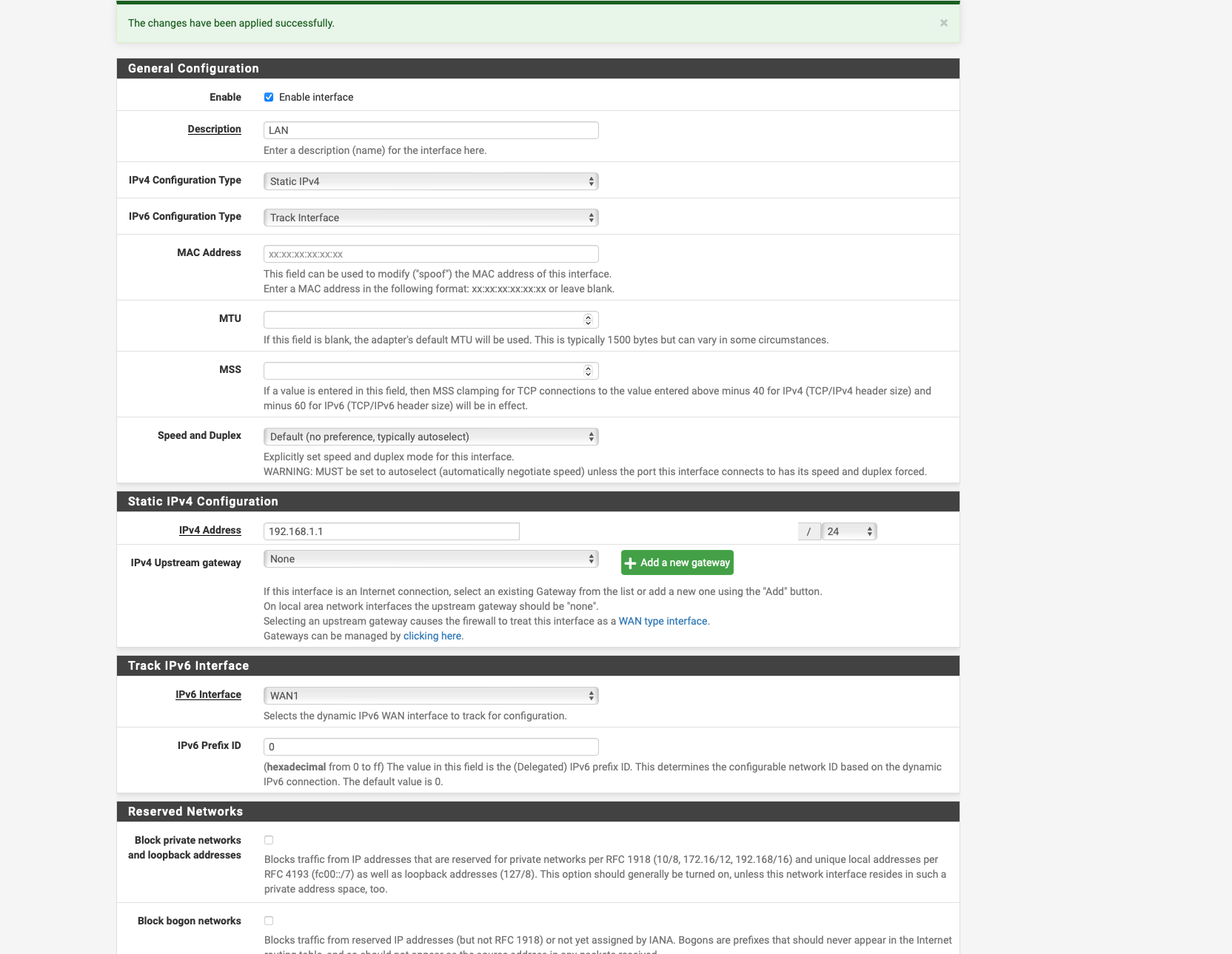
I have now set it to Track interface see screen shot and selected WAN 1 as the parent interface.
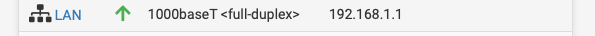
now LAN only shows the local 192 address but no more IPV6 neither local nor global
-
@Globaltrader312 I have now also removed the firewall rules under NAT