Outbound NAT - Potential RFC violation?
-
@adude42069 not sure what you read that the user ports "Ports in the User Ports range (1024-49151)" can not be used for nat? Those ports are just available for registering a service with IANA, unlike the dynamic ports 49152-65535.
Maybe I missed it, but not aware that user ports should not be used for nat..
Here is a state I took at random, one that is in the user range vs the dynamic range - it works fine. And off the top of my head not sure what device that is, but different OS can and do use ports outside the dynamic range
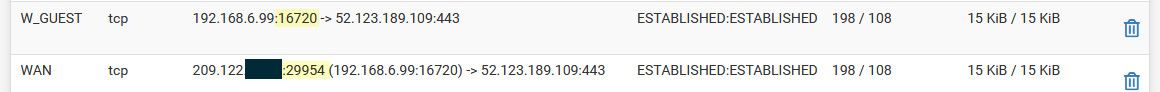
edit: just looked and that 6.99 IP is my work surface running windows 11. I sure did not adjust anything on it and its using user range as its source port in that connection.
Just looked on my windows 10 machine, and the range of source ports it can use is
C:\Windows\System32>netsh int ipv4 show dynamicport tcp Protocol tcp Dynamic Port Range --------------------------------- Start Port : 1024 Number of Ports : 64511 -
Well it is not good practice to not follow the IANA guidline, as stated in the RFC.
As per 8.1.2
"Ports in the Dynamic Ports range (49152-65535) have been specifically set aside for local and dynamic use and cannot be assigned through IANA."User ports are and may be registered to some services, that's why the dynamic range exists, as per my understanding. Some services do use relatively high port ranges (for ex. Plex with 32400).
"Assigned ports both System and User ports SHOULD NOT be used without or prior to IANA registration."
https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtmlAbout the windows port configuration, the default port range is 49152 - 65535
https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/default-dynamic-port-range-tcpip-changNo clue why it is not the case on your device. I also set up a VM with a fresh install of Windows 10 Pro, the port ranges match the standard (49152 - 65535)
Yes, it also works to use other ranges, but it is not best practice and therefore "dirty" in a certain way. That's also the reason I proposed a configurable option, so that you can go outside of the IANA/Best practice range if desired, instead of a hardcoded setting.
-
@adude42069 said in Outbound NAT - Potential RFC violation?:
cannot be assigned through IANA."
Again not assigned, doesn't say you can not use them..
You shouldn't create an application that uses port X, whithout assigning it.. Using the port as a source port to talk to some website is not using it in some application you created that listens on port X..
Ports range (1024-49151) are user ports.. And yes they can be used for source ports.. But you should say right an application that uses port say 10015 without registering it with IANA
https://www.speedguide.net/port.php?port=10015
And I agree with adhering to RFCs - but your confusing using a user port, and assigning it to some application. User port range can the dynamic range, higher up can not be assigned to an application.. But the whole range user and dynamic can be used in nats, and or as source ports when talking to some service.
-
Hmm okay, i'm still unsure though, as you could quite commonly open higher ports services to the internet, like 8080, 8443, 32400
These also could be used as ephemeral ports even though they got legitimate services running on them. Would this not create a conflict? Besides, why are OS using smaller ephemeral port ranges followig IANA recommendation?
I'm not saying you're wrong, I'm trying to understand why IANA best practice does not apply in a WAN scenario (besides WAN not usually transporting a lot of higher port services) or if I'm understanding the RFC the wrong way.
It made sense from a logical standpoint to only use a reserved port range that is made for the intended (epheremal) use, instead of using the "right range" plus another that is kinda also right but has quite a few registered services in it.
After all, when using IPv6, which does not go through NAT, the OS setting applies and its default setting is the IANA recommended range.
You could also say NAT is a crutch that is only created/used because of limited IPv4 addresses, which will not be needed in the future as IPv6 adoption increases, that would be technically true.
-
@adude42069 said in Outbound NAT - Potential RFC violation?:
8080, 8443, 32400
Those are in the user space.. And registered.. Its quite possible that talking to 32400 plex, the source port could be 32400 - its kind of just random chance.
Those are common services. But there is nothing saying 32400 as source can't talk to 32400 as destination.
And what source port will devices use when using IPv6..
C:\Windows\System32>netsh int ipv6 show dynamicport tcp Protocol tcp Dynamic Port Range --------------------------------- Start Port : 1024 Number of Ports : 64511If a client can use it as source port when talking say 32400, why can you not nat the connection using some other source part also in the user port range..
Yeah when IPv6 is wide used, nat can go away.. But we are many many years away from that to be honest.. IPv4 isn't going away any time soon.
-
sorry to repeat myself, but your windows dynamic port configuration is not standard. Neither for IPv4 nor IPv6.
In a standard configuration, IPv6 clients would not use 32400 because it is not in the default range of 49152-65535
See:
https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/default-dynamic-port-range-tcpip-chang"If a client can use it as source port when talking say 32400, why can you not nat the connection using some other source part also in the user port range"
-> This would not happen with windows standard settings, as the default range starts at 49152.
In the end, this does not break function, it's just less elegant of a solution, I guess. It also seems to be common practice to have NAT this way instead of only the IANA reserved range for ephemeral ports.
"Those are in the user space.. And registered.."
That would imply that NAT does know what ports are registered so it does not use them, right? Or am I misunderstanding?
You mean, NAT knows what ports not to use from NAT inbound rules, correct? -
@adude42069 dude you are so overthinking this... No it doesn't know what services are registered, because it doesn't matter..
The rfc your looking at is
Internet Assigned Numbers Authority (IANA) Procedures for the Management of the Service Name and Transport Protocol Port Number Registry
Why do you think that has anything to do with what Ephemeral Ports and using them in nat, or what ports are used for source port when you talk to a service on some port?
https://en.wikipedia.org/wiki/Ephemeral_port
If you want to read RFCs - here is one you should take a gander at ;)
https://datatracker.ietf.org/doc/html/rfc6056#section-3.2
3.2. Ephemeral Port Number Range As mentioned in Section 2.1, the dynamic ports consist of the range 49152-65535. **However, ephemeral port selection algorithms should use the whole range 1024-65535.** Ephemeral port selection algorithms **SHOULD use the largest possible port range**, since this reduces the chances of an off-path attacker of guessing the selected port numbers. -
@johnpoz said in Outbound NAT - Potential RFC violation?:
@adude42069 dude you are so overthinking this... No it doesn't know what services are registered, because it doesn't matter..
Well, you're probably right. As stated in first post, I'm not sure if this is common practice or not
The rfc your looking at is
Internet Assigned Numbers Authority (IANA) Procedures for the Management of the Service Name and Transport Protocol Port Number Registry
Why do you think that has anything to do with what Ephemeral Ports and using them in nat, or what ports are used for source port when you talk to a service on some port?
https://en.wikipedia.org/wiki/Ephemeral_port
If you want to read RFCs - here is one you should take a gander at ;)
https://datatracker.ietf.org/doc/html/rfc6056#section-3.2
3.2. Ephemeral Port Number Range As mentioned in Section 2.1, the dynamic ports consist of the range 49152-65535. **However, ephemeral port selection algorithms should use the whole range 1024-65535.** Ephemeral port selection algorithms **SHOULD use the largest possible port range**, since this reduces the chances of an off-path attacker of guessing the selected port numbers.did not know about this RFC, but it seems more relevant than RFC6335, also, the dynamic port range corresponds to what is usually done (even though OSes like Windows do use a smaller range, starting at 49152 unless configured differently)
Thank you for providing the more correct information.
-
@adude42069 np - yeah your rfc you linked to is specific for the registration of service ;) And yeah you can not register services to use the high dynamic ports.
If nat routers were limited to just those dynamic ports.. They would be very limited to how many sessions they could actually handle to be honest..
-
@adude42069 Don't confuse random, ephemeral source ports (which is the scope here with the random port translations in outbound NAT) with destination ports on which services are listening for connections (Which is the scope of IANA registration).