OPENVPN Client View IPSEC site-to-site
-
Good afternoon,
We're currently facing a challenge within our company that requires attention. We operate across four units in Brazil, each equipped with PFSENSE, while the main unit also features PFSENSE. The main unit connects to the other PFSENSE units via IPSEC site-to-site.
Our main unit hosts critical infrastructure such as production servers, file servers, ticketing software, and workflow tools. To facilitate remote work, we've set up an OPENVPN server in this unit, allowing employees to access resources remotely.
Additionally, we've configured an IPSEC connection to our Cloud server and another IPSEC connection to our primary Firewall, which is PFSENSE. It's imperative that remote employees using OPENVPN can access these IPSEC connections, particularly our Cloud server.
Key information:
PFSENSE version: 2.7.0 LAN of PFSENSE: 192.168.140.0/23 LAN of OPENVPN: 20.20.20.0/23 TCP/port: 1194 Mode: Remote Access (SSL/TLS + User Auth) LAN of Cloud: 172.19.0.0/24IPSEC CONNECTION CONFIGURATION:
Phase 1 (P1):IKEv2 Exchange Key Version Remote Gateway: Public IP of the Cloud Mutual PSK Authentication Method Encryption Algorithm: AES 256-bit Hash Algorithm: SHA256 (2048 bit) Lifetime: 20800Phase 2 (P2):
ESP Protocol Encryption Algorithm: AES 256-bit Hash Algorithm: SHA256 PFS Key Group: 14 (2048) Lifetime: 3600We've created an OPENVPN permission rule allowing all traffic from and to all destinations. No NAT rules have been applied to the output, and no static routes have been configured.
We have two public IPs and one LAN.
Please advise on how we can enable OPENVPN users to access these IPSEC connections seamlessly.
Thank you.
-
@BRQ_michael said in OPENVPN Client View IPSEC site-to-site:
LAN of OPENVPN: 20.20.20.0/23 TCP/port: 1194 Mode: Remote Access (SSL/TLS + User Auth)
You configured a public address range for the OpenVPN tunnel pool?
That's not recommended at all.In the OpenVPN server settings you have to add 172.19.0.0/24 (LAN of Cloud) to the "Local Networks" to push the route for this subnet to the clients.
In the IPSec settings you have to add a phase 2 to connect the remote network with the VPN tunnel network.
So at main:
local network: VPN tunnel network
remote network: 172.19.0.0/24And on the cloud node also add p2 with swapped networks of course.
-
@viragomann
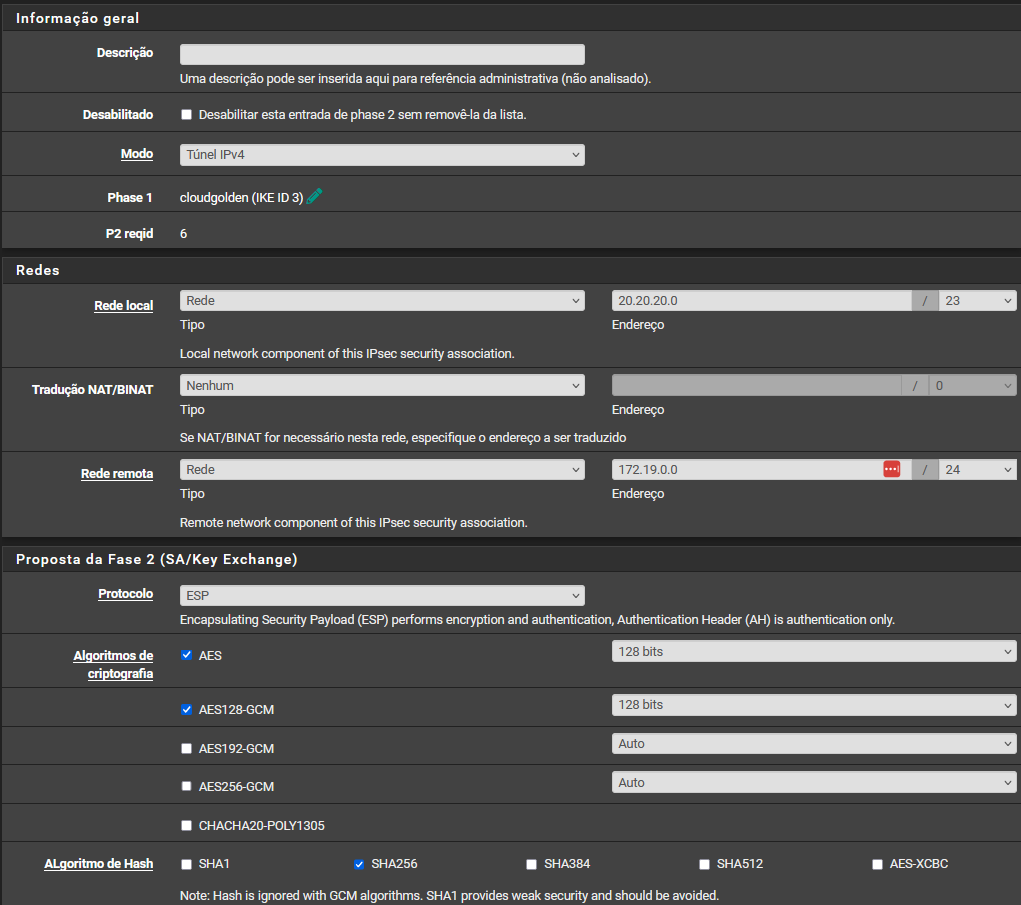
I even added the LAN network of my CLOUD "172.19.0.0/24" in Local Networks on my OPENVPN Server, and the IPSEC tunnel is already done this way, closing P1 and P2 to the Cloud, including on the other side of the tunnel, in CLOUD, I also added a LAN network on P2 which is 20.20.20.0/23, apart from my LAN which was also 192.168.140.0/23, the IPSEC connection works when I'm on my network, normally, but when I'm an OPENVPN client no. I recently saw a topic like this from 2014 where the person explains this, but on the other side of the IPSEC is an EDGE Firewall, and the configuration of this firewall is provided by CLOUD specialists, I don't have access to it but it should be simple, right? just add the CLOUD network to local networks and add the IP 20.20.20.0/23 to P2 of my IPSEC on the other Firewall.
Attached are the settings made.
In the link below are the settings of my OPENVPN Server and the IPSEC connection.https://drive.google.com/drive/folders/1Jv_Lq9mXWe-oQMrNmnVYMVPeIG2Ig2w9?usp=drive_link
-
I managed to make it work, I had to configure phase2 this way to see the other side of ipsec
-
@BRQ_michael said in OPENVPN Client View IPSEC site-to-site:
on the other side of the IPSEC is an EDGE Firewall, and the configuration of this firewall is provided by CLOUD specialists, I don't have access to it
You would need to add the P2 policy carrying the OpenVPN traffic at both ends of the IPSec tunnel for it to establish.
You should see it in the IPSec status. -
@stephenw10 It worked, friend, thank you very much, I had to configure phase2 as the image I sent last