DNS and NTP intercept for multiple interfaces
-
I have 3 vlans + LAN defined in my config.
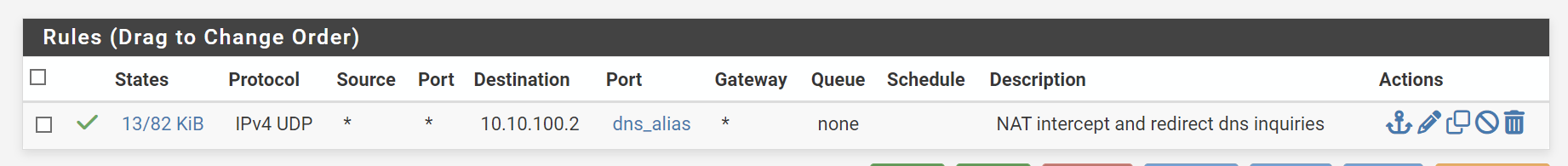
DNS intercept works well with the port forwarding rule below. I will be adding the same for NTP intercept.
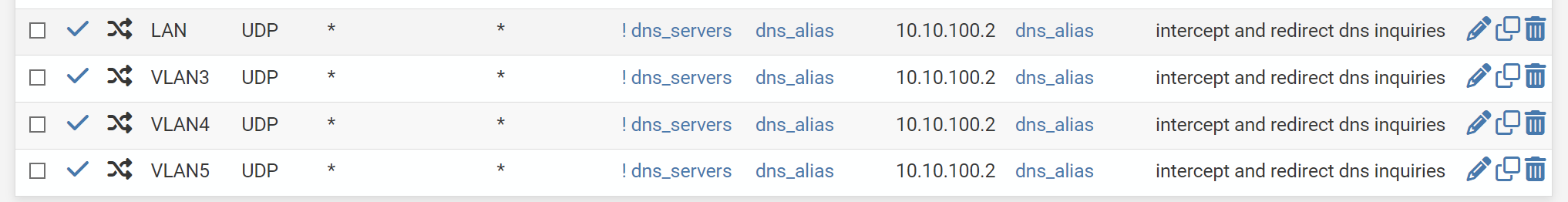
My question, is there a way of consolidating the rule to cover multiple interfaces rather than having separate intercept rules for each interface?
Dns_servers is alias for 10.10.100.2 and 10.10.1.1. That should probably just be 10.10.100.2 as each interface has it's own unique ip (ie 10.10.3.1, 10.10.4.1, 10.10.5.1 for vlans3..5 respectively). Dns alias is ports alias for ports 53 and 853.
-
@GPz1100 Create an interfacegroup of those interfaces and place the rule on the interfacegroup.
-
@keyser Aha! I was wondering if such an alias existed. Thanks, will try that.
-
@keyser That did indeed do the trick.
It appears I can also get rid of the floating firewall rule to allow dns server access (it's on a different vlan/subnet altogether than everything else).
floating rule
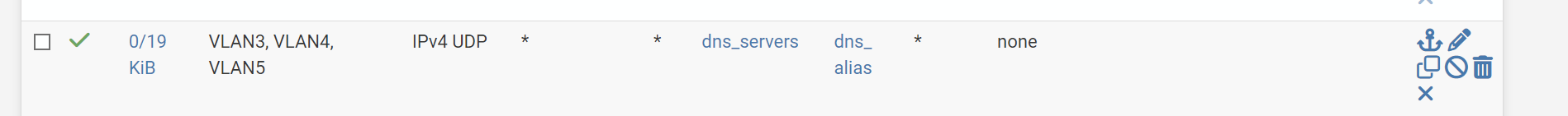
Since NAT rules are executed before floating rules, traffic never reaches the above rule.
NAT/port forward
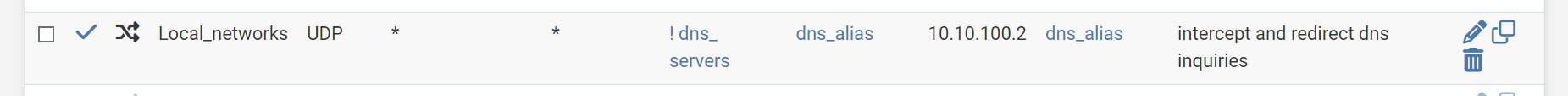
This creates firewall rule below for the Local_networks "interface".