secureboot, uart0, AES-NI CPU Crypto, QAT Crypto, Hardware crypto, Kernel PTI, MDS Mitigation (four queries)
-
[1]
I used below for PFSense community addition:https://storage-asset.msi.com/excelSku/us/mini-pcs/Cubi%20N%20ADL%20S-055BUS.pdf (Cubi N ADL S-055BUS)
with 3200MHz 16 GB RAM and nvMe M2 SSD 500 GB.[2]
FreeBSD (on which PFSense is based) does not support secure boot.
First I was not able to disable the secure boot. It was there in BIOS, but not clickable.
I installed Ubuntu server on this box, then in bios secure boot disable was clickable in BIOS, no idea how installing ubuntu server on the box made it clickable in bios.
I disabled secureboot and followed intstructions to installed pfsense available publically.[3]
Now I faced this message while boot/intallation. It did not even reach the place where we say install it.
The message was:
atkbd0: [GIANT-LOCKED]
atrtc0: <At realtime clock> at port 0x70 irq 8 on isa0
atrtc0: Warning: Couldn't map I/O.
atrtc0: registered as a time-of-day clock, resolution 1.000000s
Event timer "RTC" frequency 32768 Hz quality 0
uart0: <16550 or compatible> at port 0x3f8 irq 4 flags 0x10 on isa0
here it halted.
I found help from opnsense forms with similar messages.
The steps where
a) start again the machine.
b) first time when pfsense screen comes, quicly press tab to stop autoboot.
c) press 3 to enter loader shell prompt.
d)type line below then press enter:
unset hint.uart.0.at
e)type line below then press enter:
unset hint.uart.1.at
f)type line below then press enter:
boot
g) everytime on boot loader (b above) follow (c to f above) in the future. [important]
h) follow normal publically available instartuction to install pfsense.
i) when pfsense is fully installed, and you are on a screen which has message like your wan is on this port, lan is on this url etc, with 1 to 16 pointers, options like logout, pfTop, assign interfaces, and so on: press 8 to enter shell.
here type:
ee /boot/device.hintsA screen will appear with multiple lines. use keyboard down keys to navigate down to line:hint.uart.0.at (more text)
infront of this line type "#"
it should look like
#hint.uart.0.at (more text)
use keyboard down keys to navigate down to line:hint.uart.1.at (more text)
infront of this line type "#"
it should look like
#hint.uart.1.at (more text)press escape key.
a popup comes where select file operations ( i think it was pressing c)
then select the operation by pressing corresponding key which says save.press escape key again.
press the option which says exit editor ( i think it was a)now type "exit" to exit shell
press option 6 to restart,
j) if step i above is followed correctly, during future restarts, steps b to i above can be forgotten for future.
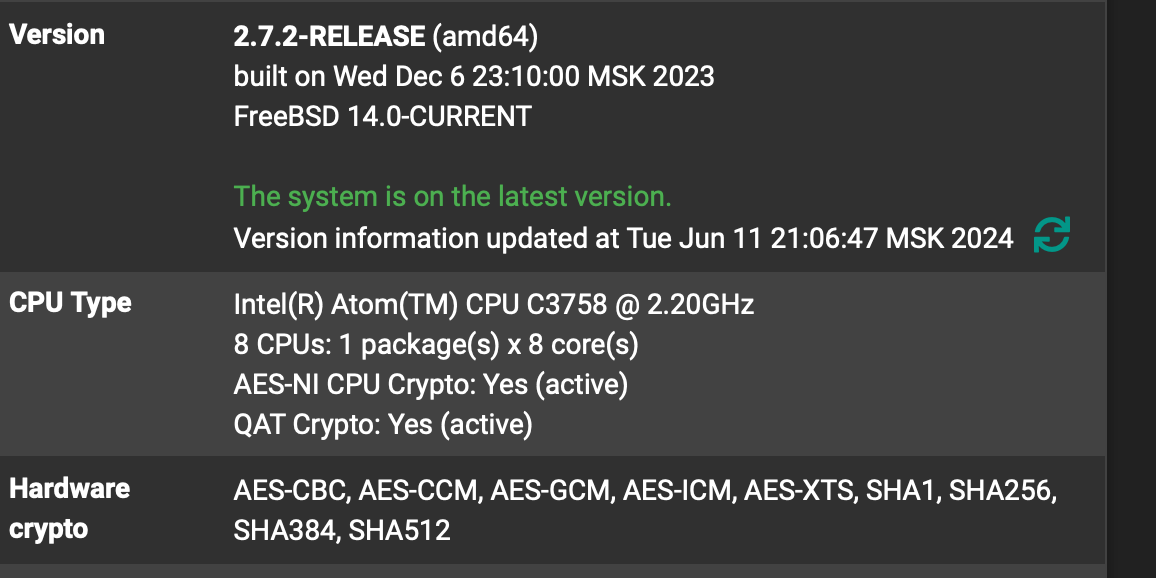
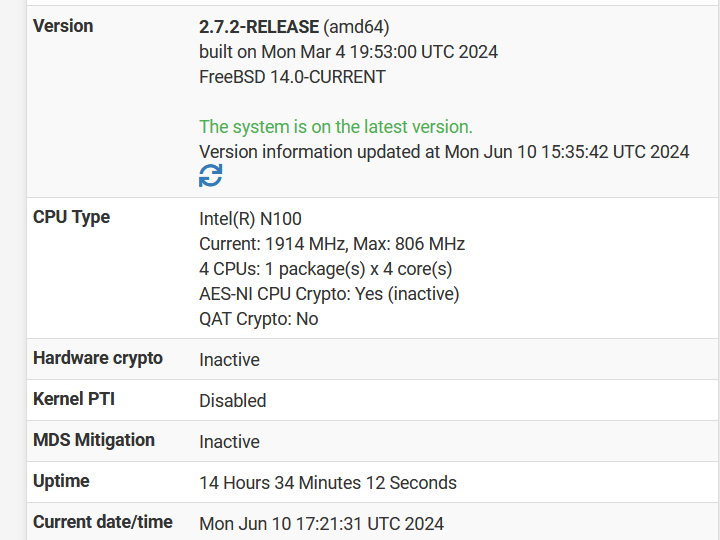
[4] My home screen of pfSense Web GUI says for system information
Version 2.7.2-RELEASE (amd64)
built on Mon Mar 4 19:53:00 UTC 2024
FreeBSD 14.0-CURRENTThe system is on the latest version.
Version information updated at Mon Jun 10 15:35:42 UTC 2024CPU Type
Intel(R) N100
Current: 1813 MHz, Max: 806 MHz
4 CPUs: 1 package(s) x 4 core(s)
AES-NI CPU Crypto: Yes (inactive)
QAT Crypto: NoHardware crypto Inactive
Kernel PTI Disabled
MDS Mitigation Inactive
Uptime 14 Hours 27 Minutes 55 Seconds
Current date/time
Mon Jun 10 17:15:14 UTC 2024
[5] now after we are same point, I come up with my queries and comments.
a) how hard it could be to implement secureboot in freeBSD?
b) what was on uart0 [point three above] which had to be disabled for pfSense to work?
c) AES-NI CPU Crypto, QAT Crypto, Hardware crypto, Kernel PTI, MDS Mitigation being disabled. Does it sounds ok?
d) I wanted to say pfSense (or any similar firewall like OPNSENSE) is being implemented, used and praised worldwide, and very basic security features are being ignored in the usage?
What we want to achieve here?Please help me to find answer to [5] a to d
-
Briefly:
a) https://freebsdfoundation.org/freebsd-uefi-secure-boot/. So non-trivial!
b) I'd guess bad ACPI tables or other hardware descriptors since other N100 platform devices do not require such a workaround. Check the boot log. Try booting in verbose mode.
You probably want to add those as disable hints in loader.conf.local because device.hints will be overwritten at upgrade.c) That's as expected. PTI is disabled because the N100 doesn't require it. You could enable MDS but on a hardware appliance like pfSense the attach surface is next to zero in most cases.
d) Not sure what your question is here?
Steve
-
@dotgate
I'll add a little on my own
c) there is no problem activating these options (if the device allows it)https://docs.netgate.com/pfsense/en/latest/hardware/cryptographic-accelerators.html
https://man.freebsd.org/cgi/man.cgi?qathowever, version 2.7.2 does not include the core modules of the QAT driver
(Intel QuickAssist Technology (QAT) [Plus only])But, if you build your Freebsd 14.0 kernel on any test device, you can download this driver manually into the PF kernel (by copying several files)